Which two file types can be sent to WildFire for analysis if a firewall has only a standard subscription service? (Choosetwo.)
For which firewall feature should you create forward trust and forward untrust certificates?
Which statement describes a function provided by an Interface Management Profile?
Which three interface types can control or shape network traffic? (Choose three.)
Because a firewall examines every packet in a session, a firewall can detect application ________?
If a DNS sinkhole is configured, any sinkhole actions indicating a potentially infected host are recorded in which log type?
On a firewall that has 32 Ethernet ports and is configured with a dynamic IP and port (DIPP) NAT oversubscription rate of2x, what is the maximum number of concurrent sessions supportedby each available IP address?
Which condition must exist before a firewall's inband interface can process traffic?
Which action in a File Blocking Security Profile results in theuser being prompted to verify afile transfer?
Besides selecting the Heartbeat Backup option when creating an ActivePassive
HA Pair, which of the following also prevents "SplitBrain"?
As the Palo Alto Networks administrator, you have enabled Application Block pages. Afterward, some users do not receive web-based feedback for all denied applications. Why would this be?
InPAN-OS 8.0which of the available choices serves as an alert warning by defining patterns of suspicious traffic and network anomalies that may indicate a host has been compromised?
What built-in administrator role allows all rights except for the creation of administrative accounts and virtual systems?
Select the implicit rules that are applied to traffic that fails to match any administratordefined Security Policies. (Choose all rules that are correct.)
Which of the following represents HTTP traffic events that can be used to identify potential Botnets?
Which of the following statements is NOT True regarding a Decryption Mirror interface?
A local/enterprise PKI system is required to deploy outbound forward proxy SSL decryption capabilities.
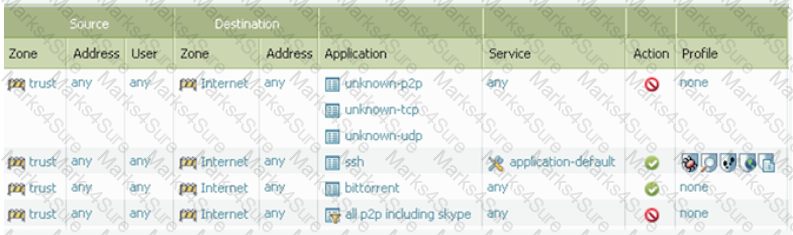
Taking into account only the information in the screenshot above, answer the following question. Which applications will be allowed on their standard ports? (Select all correct answers.)
As the Palo Alto Networks administrator responsible for User Identification, you are looking for the simplest method of mapping network users that do not sign into LDAP. Which information source would allow reliable User ID mapping for these users, requiring the least amount of configuration?