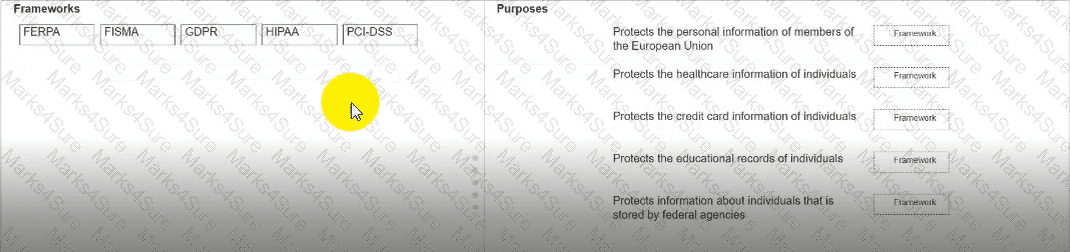
Move each framework from the list on the left to the correct purpose on the right.
Note: You will receive partial credit for each correct answer.
You are collecting data after a suspected intrusion on the local LAN.
You need to capture incoming IP packets to a file for an investigator to analyze.
Which two tools should you use?(Choose 2.)
Move each NIST Incident Response Lifecycle phase from the list on the left to the correct description on the right.
Note: You will receive partial credit for each correct answer.

A remote worker is visiting a branch office to attend face-to-face meetings. The worker tries to associate their company laptop with the branch wireless access point (WAP) but is unable to do so.
What is a possible cause?
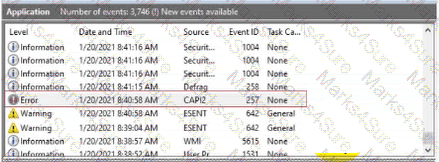
You are reviewing the Application log on a Windows computer. You see an event with an error-level message as shown.
What can you determine about the application that generated the event message?
Your manager asks you to review the output of some vulnerability scans and report anything that may require escalation.
Which two findings should you report for further investigation as potential security vulnerabilities?(Choose 2.)
You need a software solution that performs the following tasks:
Compiles network data
Logs information from many sources
Provides orchestration in the form of case management
Automates incident response workflows
What product should you use?
You need to design your company’s password policy to adhere to the National Institute of Standards and Technology (NIST) guidelines for user password security.
What is the minimum password length that you should require to be consistent with the NIST guidelines?
A restaurant installs a second wireless router that only employees can use.
Which statement describes how to securely configure the new router?
You work for a hospital that stores electronic protected health information (ePHI) in an online portal. Authorized employees can use their mobile devices to access patient ePHI.
You need to ensure that employees’ mobile devices comply with HIPAA regulations.
Which safeguard should you develop and implement?
A client cannot connect to the corporate web server. You discover a large number of half-open TCP connections to the server.
What should you do?
The company web server collects information through a form. The form is accessed by using port 80. The form content is transferred to an encrypted database for storage. You are investigating a complaint that the form content has been compromised.
What is the cause of the security breach?