Which two elements of the incident response process are stated in NIST Special Publication 800-61 r2? (Choose two.)
Which evasion method involves performing actions slower than normal to prevent detection?
An engineer is sharing folders and files with different departments and got this error: "No such file or directory". What must the engineer verify next?
Which element is included in an incident response plan as stated m NIST SP800-617
Which evasion technique is indicated when an intrusion detection system begins receiving an abnormally high volume of scanning from numerous sources?
Which technology on a host is used to isolate a running application from other applications?
An engineer is investigating a case of the unauthorized usage of the “Tcpdump” tool. The analysis revealed that a malicious insider attempted to sniff traffic on a specific interface. What type of information did the malicious insider attempt to obtain?
Refer to the exhibit.
During the analysis of a suspicious scanning activity incident, an analyst discovered multiple local TCP connection events Which technology provided these logs?
Refer to the exhibit.
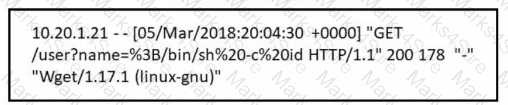
Which attack is being attempted against a web application?
A company encountered a breach on its web servers using IIS 7 5 Dunng the investigation, an engineer discovered that an attacker read and altered the data on a secure communication using TLS 1 2 and intercepted sensitive information by downgrading a connection to export-grade cryptography. The engineer must mitigate similar incidents in the future and ensure that clients and servers always negotiate with the most secure protocol versions and cryptographic parameters. Which action does the engineer recommend?
What are two differences between tampered disk images and untampered disk images'? (Choose two.)
What is the practice of giving employees only those permissions necessary to perform their specific role within an organization?
An engineer received a flood of phishing emails from HR with the source address HRjacobm@companycom. What is the threat actor in this scenario?
Refer to the exhibit.
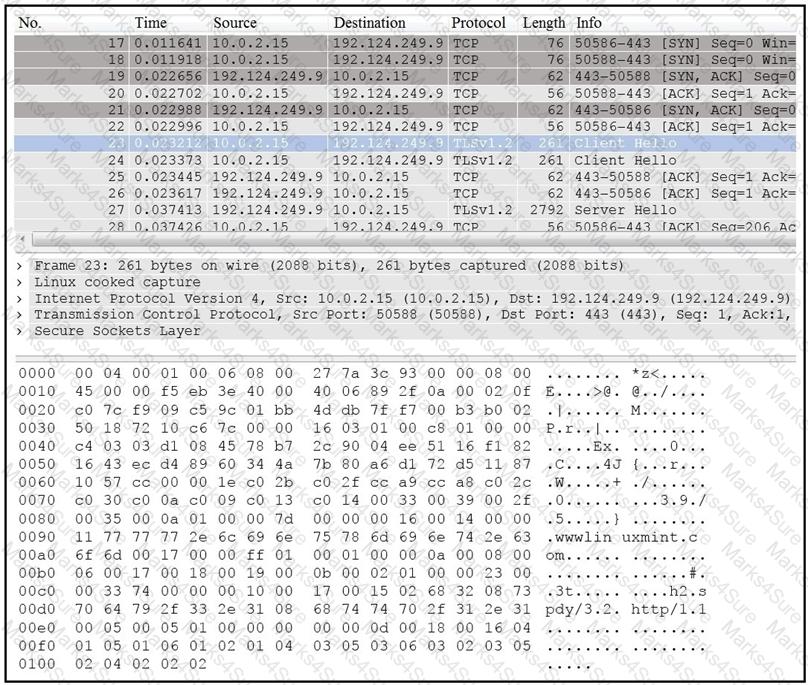
Drag and drop the element name from the left onto the correct piece of the PCAP file on the right.
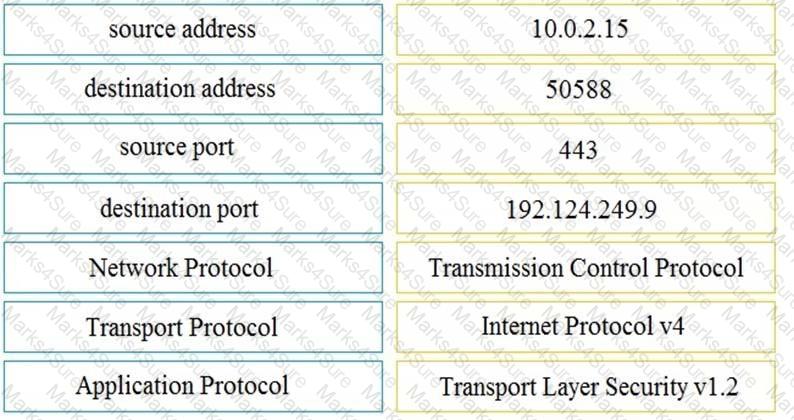
Which technology should be used to implement a solution that makes routing decisions based on HTTP header, uniform resource identifier, and SSL session ID attributes?
Refer to the exhibit.

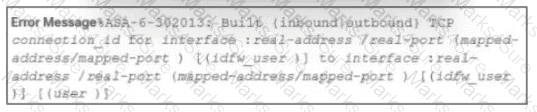
An analyst received this alert from the Cisco ASA device, and numerous activity logs were produced. How should this type of evidence be categorized?
Which difficulty occurs when log messages are compared from two devices separated by a Layer 3 device that performs Network Address Translation?
What are two differences in how tampered and untampered disk images affect a security incident? (Choose two.)
Which step in the incident response process researches an attacking host through logs in a SIEM?
Refer to the exhibit.
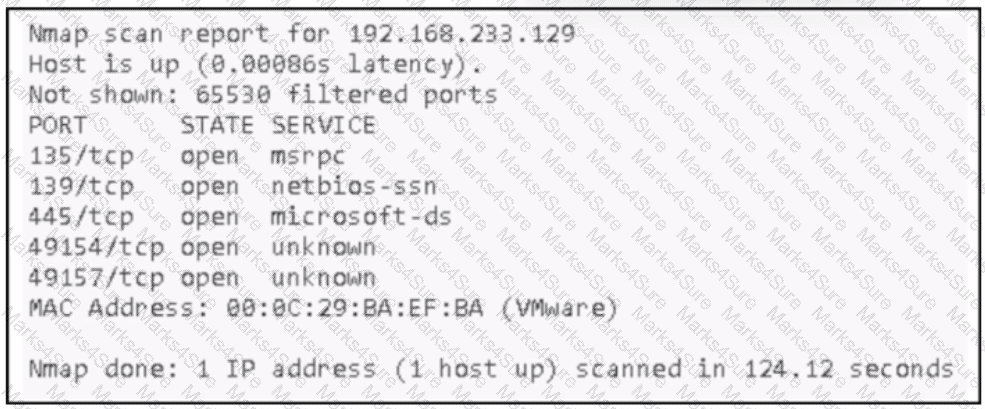
An attacker Infiltrated an organization's network and ran a scan to advance with the lateral movement technique. Which two elements from the scan assist the attacker? (Choose two.)
A network engineer noticed in the NetFlow report that internal hosts are sending many DNS requests to external DNS servers A SOC analyst checked the endpoints and discovered that they are infected and became part of the botnet Endpoints are sending multiple DNS requests but with spoofed IP addresses of valid external sources What kind of attack are infected endpoints involved in1?

Refer to the exhibit. An engineer must use a 5-tuple approach to isolate a compromised host in a grouped set of logs.
Which data must the engineer use?
An engineer received an alert affecting the degraded performance of a critical server. Analysis showed a heavy CPU and memory load. What is the next step the engineer should take to investigate this resource usage?
An engineer must analyze a security event from last month. The engineer has access to a .pcap file collected via traffic mirroring and NetFlow data. The engineer must perform checks quickly on a busy network segment without prior knowledge of the incident details. Which source of data should be used for analysis?
How does the approach of a behavioral detection system to identifying security threats compare to that of a rule-based detection system?
Which type of attack occurs when an attacker is successful in eavesdropping on a conversation between two IP phones?
What is the difference between inline traffic interrogation and traffic mirroring?
Refer to the exhibit.
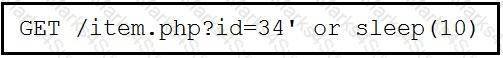
This request was sent to a web application server driven by a database. Which type of web server attack is represented?
Which SOC metric represents the time to stop the incident from causing further damage to systems or data?
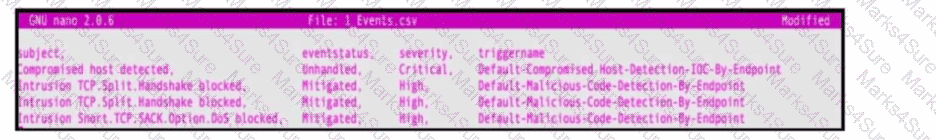
Refer to the exhibit. An engineer must map these events to the source technology that generated the event logs. To which technology do the generated logs belong?
What are two differences and benefits of packet filtering, stateful firewalling, and deep packet inspections? (Choose two.)
What is the impact of false negative alerts when compared to true negative alerts?
Drag and drop the definition from the left onto the phase on the right to classify intrusion events according to the Cyber Kill Chain model.
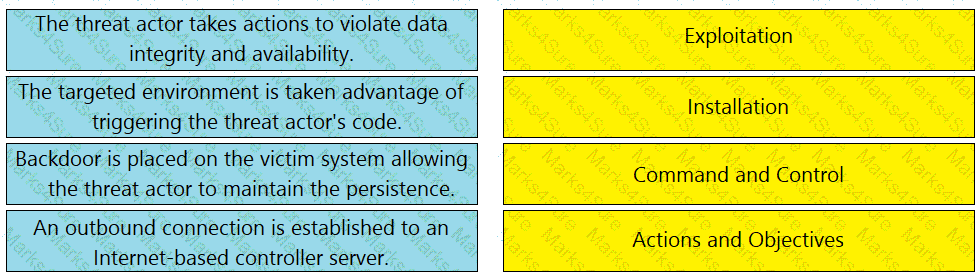
Refer to exhibit.
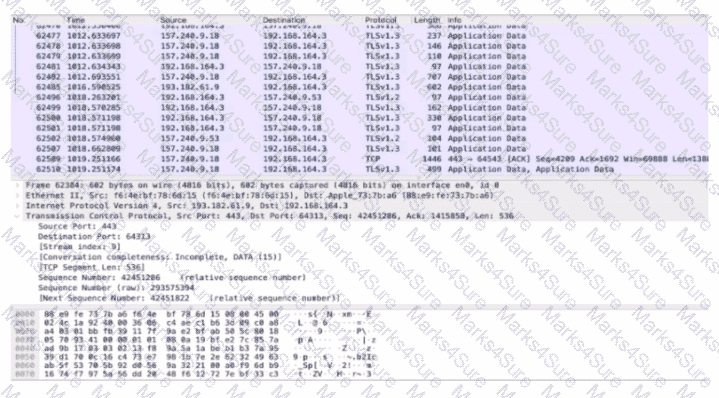
An analyst performs the analysis of the pcap file to detect the suspicious activity. What challenges did the analyst face in terms of data visibility?
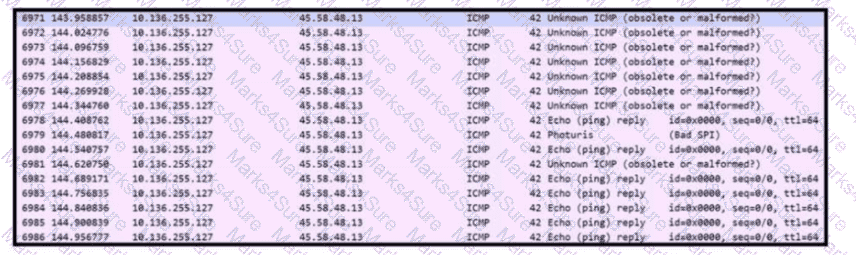
Refer to the exhibit. An engineer received a ticket to analyze unusual network traffic. What is occurring?
Which technology assures that the information transferred from point A to point B is unaltered and authentic?
An engineer must compare NIST vs ISO frameworks The engineer deeded to compare as readable documentation and also to watch a comparison video review. Using Windows 10 OS. the engineer started a browser and searched for a NIST document and then opened a new tab in the same browser and searched for an ISO document for comparison
The engineer tried to watch the video, but there 'was an audio problem with OS so the engineer had to troubleshoot it At first the engineer started CMD and looked fee a driver path then locked for a corresponding registry in the registry editor The engineer enabled "Audiosrv" in task manager and put it on auto start and the problem was solved Which two components of the OS did the engineer touch? (Choose two)
An investigator is examining a copy of an ISO file that is stored in CDFS format. What type of evidence is this file?
What is a difference between rule-based and role-based access control mechanisms?
While viewing packet capture data, an analyst sees that one IP is sending and receiving traffic for multiple devices by modifying the IP header.
Which technology makes this behavior possible?
A system administrator is ensuring that specific registry information is accurate.
Which type of configuration information does the HKEY_LOCAL_MACHINE hive contain?
An analyst discovers that a legitimate security alert has been dismissed. Which signature caused this impact on network traffic?
A vulnerability analyst is performing the monthly scan data review Output data is very big and getting bigger each month The analyst decides to create a more efficient process to complete the task on time All false positives and true positives are excluded from the results The remaining findings will be assigned to a technical team for further remediation What is the result of such activity?
What is the difference between inline traffic interrogation (TAPS) and traffic mirroring (SPAN)?
In digital communications, which method is recommended for securely exchanging public keys between users T0n2262144790 and D4n4126220794?
A security analyst notices a sudden surge of incoming traffic and detects unknown packets from unknown senders After further investigation, the analyst learns that customers claim that they cannot access company servers According to NIST SP800-61, in which phase of the incident response process is the analyst?
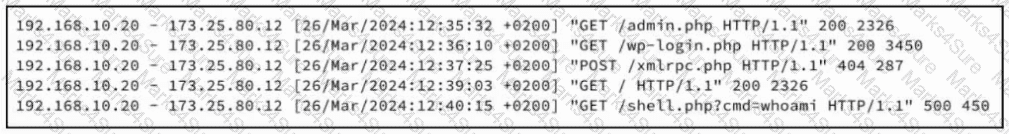
Refer to the exhibit. A security analyst examines Apache web server logs and notices the entries. Which security concern is occurring?
An analyst received an alert on their desktop computer showing that an attack was successful on the host. After investigating, the analyst discovered that no mitigation action occurred during the attack. What is the reason for this discrepancy?
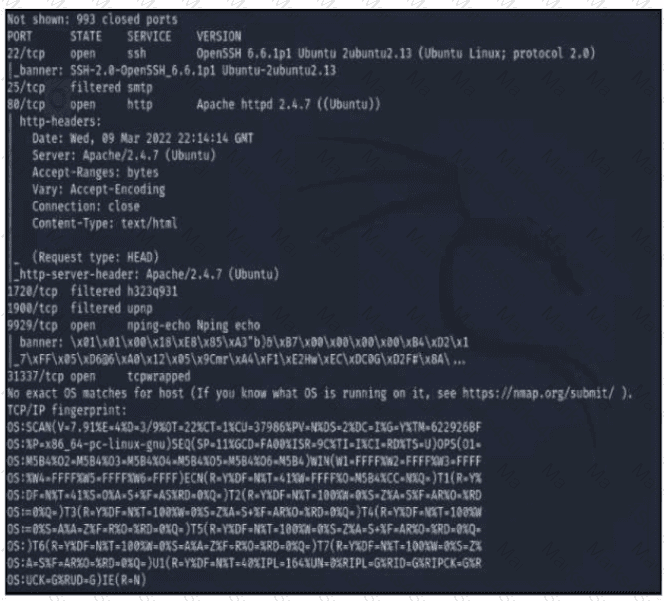
Refer to the exhibit A penetration tester runs the Nmap scan against the company server to uncover possible vulnerabilities and exploit them Which two elements can the penetration tester identity from the scan results? (Choose two.)
A security expert is working on a copy of the evidence, an ISO file that is saved in CDFS format. Which type of evidence is this file?
An engineer must gather data for monitoring purposes from different network devices. The engineer needs to collect events from the local network and use that information for packet sniffing. The solution must create an exact copy of traffic and provide full fidelity. Which solution should the engineer use?
Which type of attack involves sending input commands to a web server to access data?
A company is using several network applications that require high availability and responsiveness, such that milliseconds of latency on network traffic is not acceptable. An engineer needs to analyze the network and identify ways to improve traffic movement to minimize delays. Which information must the engineer obtain for this analysis?
Which metric should be used when evaluating the effectiveness and scope of a Security Operations Center?
Which classification of cross-site scripting attack executes the payload without storing it for repeated use?
What is the key difference between mandatory access control (MAC) and discretionary access control (DAC)?
An engineer is working on a ticket for an incident from the incident management team A week ago. an external web application was targeted by a DDoS attack Server resources were exhausted and after two hours it crashed. An engineer was able to identify the attacker and technique used Three hours after the attack, the server was restored and the engineer recommended implementing mitigation by Blackhole filtering and transferred the incident ticket back to the IR team According to NIST SP800-61, at which phase of the incident response did the engineer finish work?
Refer to the exhibit.
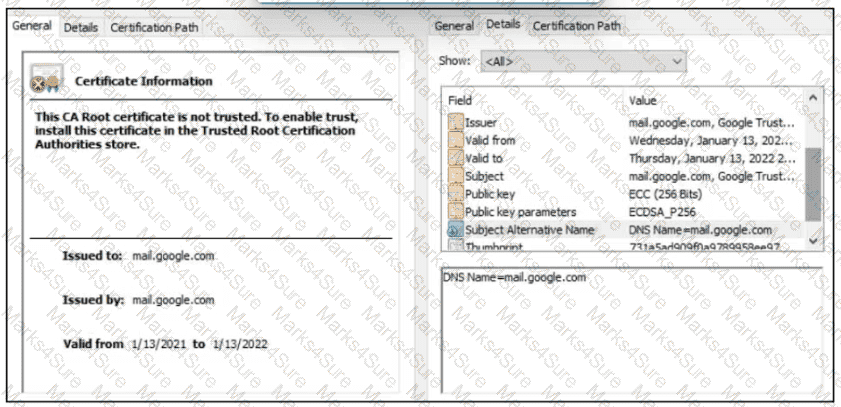
A company employee is connecting to mail google.com from an endpoint device. The website is loaded but with an error. What is occurring?
The security team has detected an ongoing spam campaign targeting the organization. The team's approach is to push back the cyber kill chain and mitigate ongoing incidents. At which phase of the cyber kill chain should the security team mitigate this type of attack?
What is a key difference between a tampered and an untampered disk image during a forensic investigation?
A security consultant must change the identity access management model fof their organization The new approach will put responsibility on the owner, who will decide whichusers will have access to which resources Which low-cost model must be used for this purpose?
An analyst is using the SIEM platform and must extract a custom property from a Cisco device and capture the phrase, "File: Clean." Which regex must the analyst import?
A user reports that a mobile application is working very slowly. A DDoS detection tool reports high-volume traffic. During which phase does the CSIRT ensure that the incident does not continue and confirm that the organization has taken the required actions?
Which type of attack uses a botnet to reflect requests off of an NTP server to overwhelm a target?
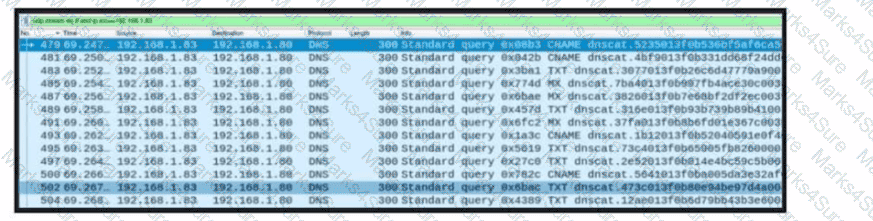
Refer to the exhibit. A network engineer received a report that a host is communicating with unknown domains on the internet. The network engineer collected packet capture but could not determine the technique or the payload used. What technique is the attacker using?
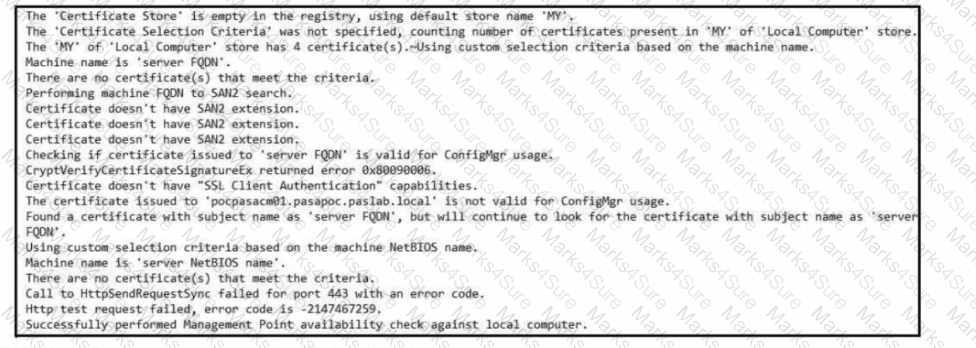
Refer to the exhibit. Which set of actions must an engineer perform to identify and fix this issue?
Which two pieces of information are collected from the IPv4 protocol header? (Choose two.)
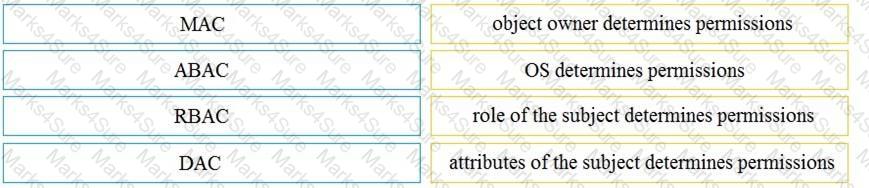
Drag and drop the access control models from the left onto the correct descriptions on the right.
Which type of data consists of connection level, application-specific records generated from network traffic?
Which metric in CVSS indicates an attack that takes a destination bank account number and replaces it with a different bank account number?
Which system monitors local system operation and local network access for violations of a security policy?
Refer to the exhibit.
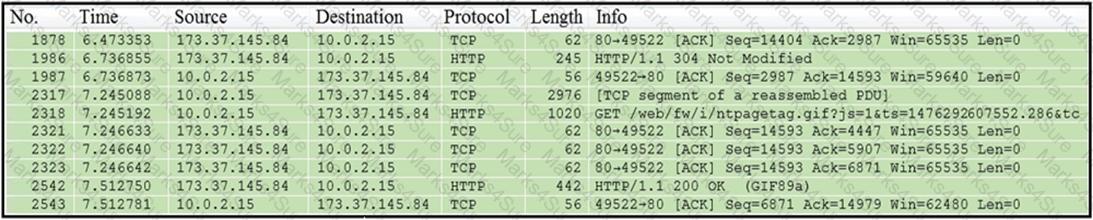
Which packet contains a file that is extractable within Wireshark?
A suspicious user opened a connection from a compromised host inside an organization. Traffic was going through a router and the network administrator was able to identify this flow. The admin was following 5-tuple to collect needed data. Which information was gathered based on this approach?
Which management concept best describes developing, operating, maintaining, upgrading, and disposing of all resources?
During which phase of the forensic process are tools and techniques used to extract information from the collected data?
Refer to the exhibit
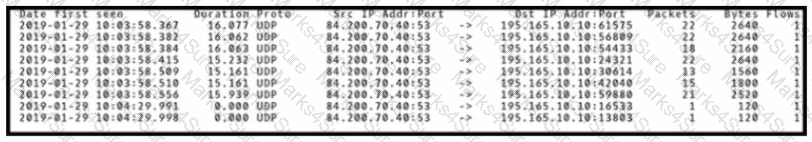
An engineer is analyzing DNS response packets that are larger than expected The engineer looks closer and notices a lack of appropriate DNS queries What is occurring?
Refer to the exhibit.
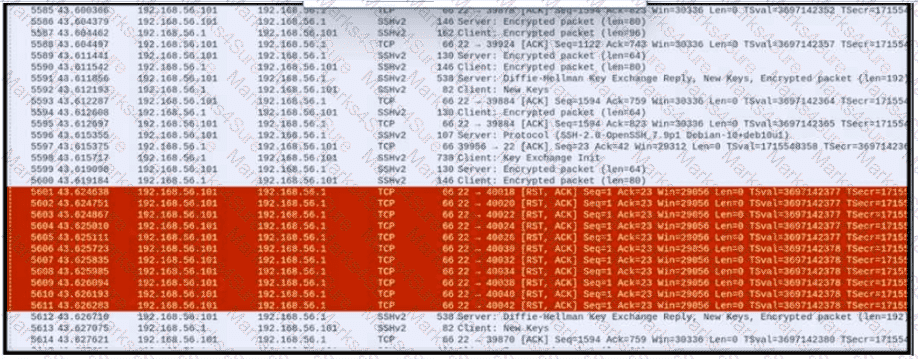
An engineer is analyzing a PCAP file after a recent breach An engineer identified that the attacker used an aggressive ARP scan to scan the hosts and found web and SSH servers. Further analysis showed several SSH Server Banner and Key Exchange Initiations. The engineer cannot see the exact data being transmitted over an encrypted channel and cannot identify how the attacker gained access How did the attacker gain access?
A user received a malicious attachment but did not run it. Which category classifies the intrusion?
A software development company develops high-end technology for the customer that will go through the HIPAA audit program. The technology will be hosted in the cloud, and the healthcare, employee names, and contact information will be stored on two separate logically isolated private cloud services. The patents and inventions will be hosted on a separate encrypted database. A compliance team is asked to analyze the cloud infrastructure and architecture to identify the protected data. Which two types of protected data should be identified? (Choose two.)
What describes the impact of false-positive alerts compared to false-negative alerts?
Drag and drop the technologies from the left onto the data types the technologies provide on the right.

When communicating via TLS, the client initiates the handshake to the server and the server responds back with its certificate for identification.
Which information is available on the server certificate?
Developers must implement tasks on remote Windows environments. They decided to use scripts for enterprise applications through PowerShell. Why does the functionality not work?