A user reports that after a recent software deployment to upgrade the Testing application, they can no longer use it. However, other employees can successfully
use the Testing program.
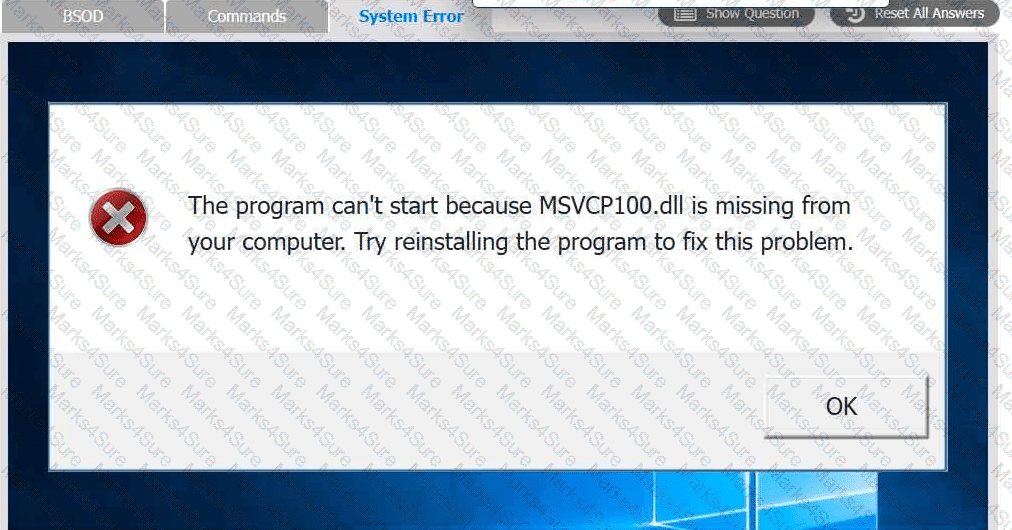
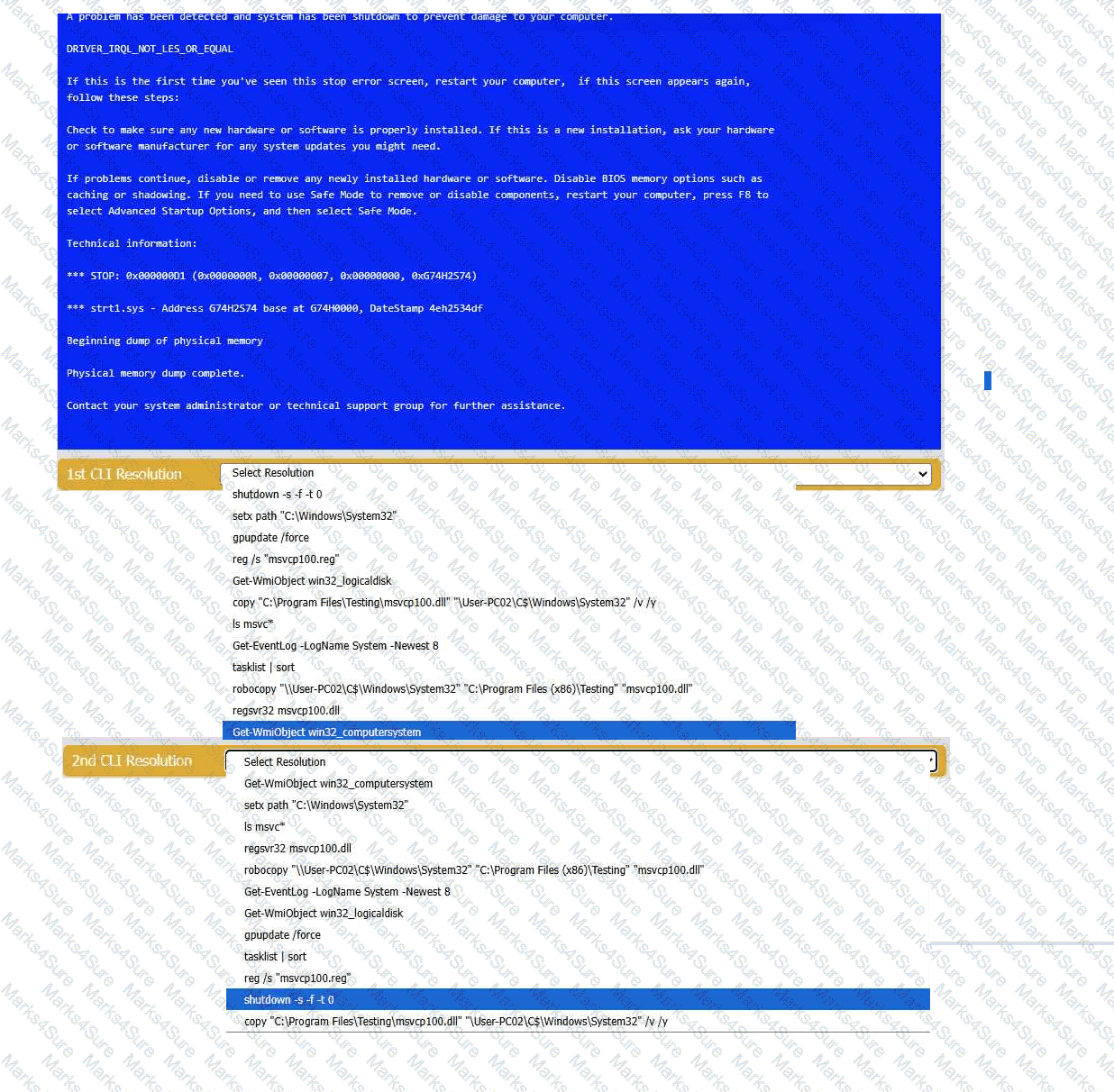
INSTRUCTIONS
Review the information in each tab to verify the results of the deployment and resolve
any issues discovered by selecting the:
· First command to resolve the issue
· Second command to resolve the issue
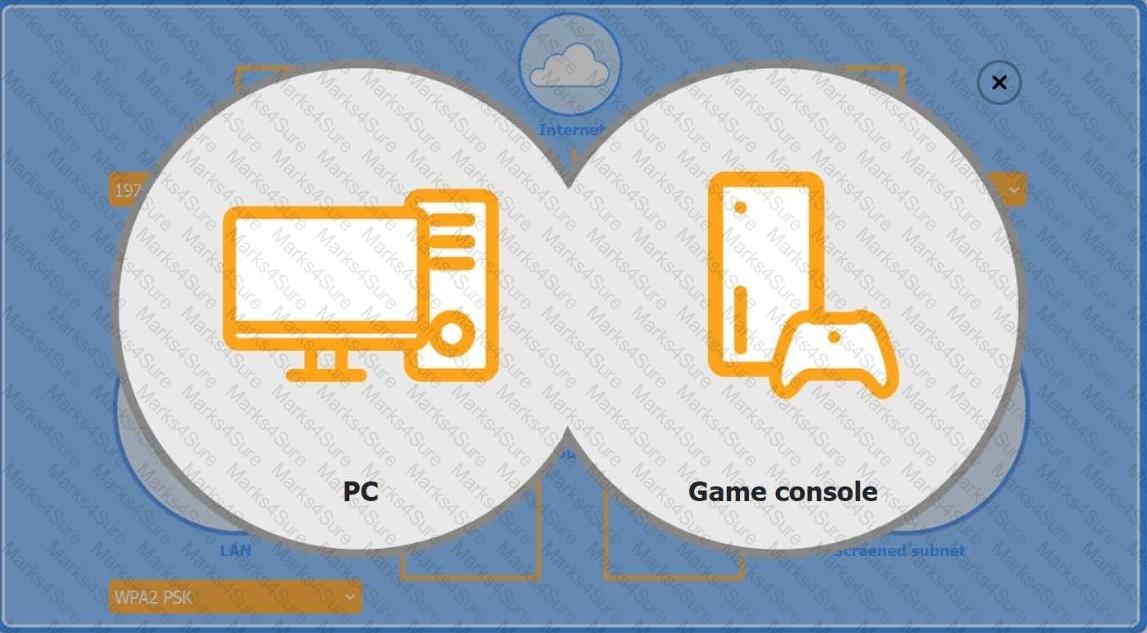
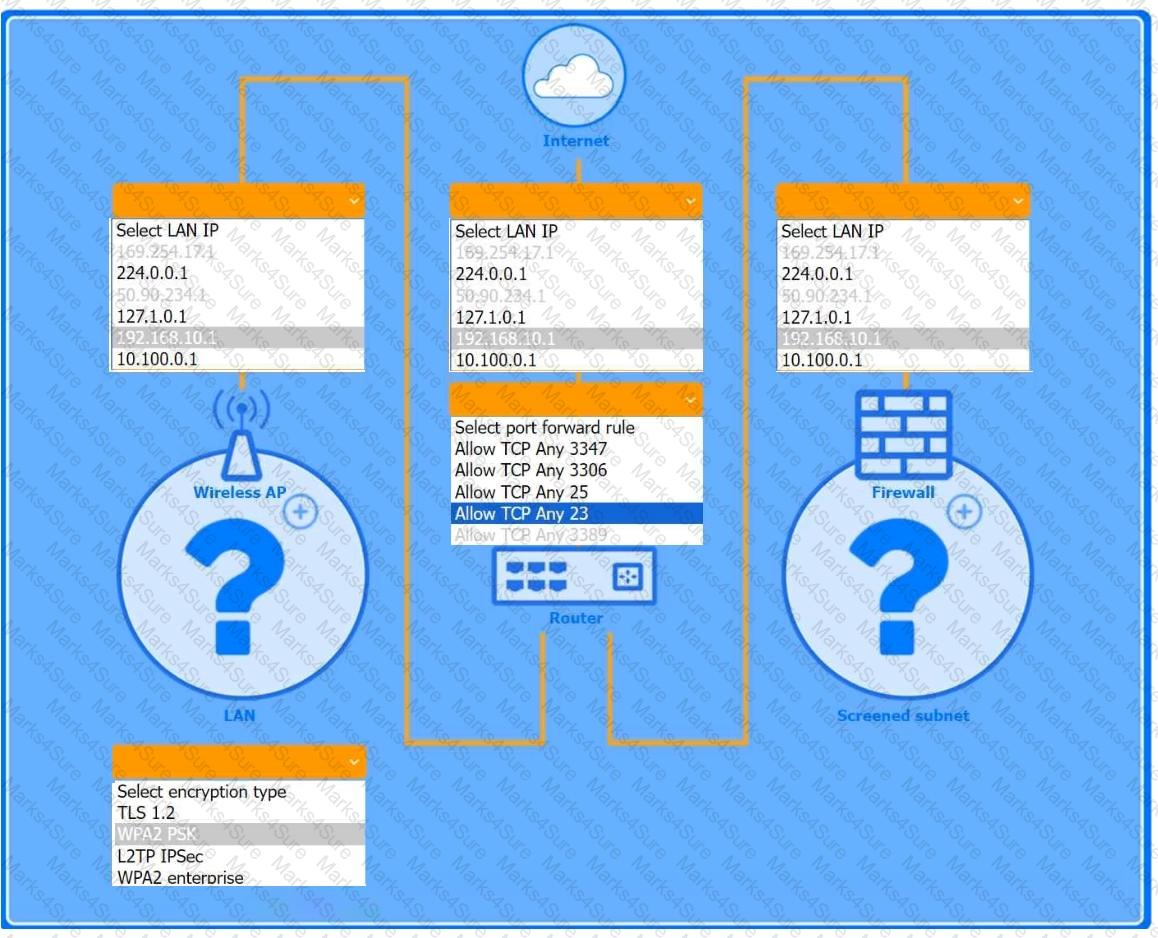
You are configuring a home network for a customer. The customer has requested the ability to access a Windows PC remotely, and needs all chat and optional functions to work in their game console.
INSTRUCTIONS
Use the drop-down menus to complete the network configuration for the customer. Each option may only be used once, and not all options will be used.
Then, click the + sign to place each device in its appropriate location.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
Wireless AP LAN
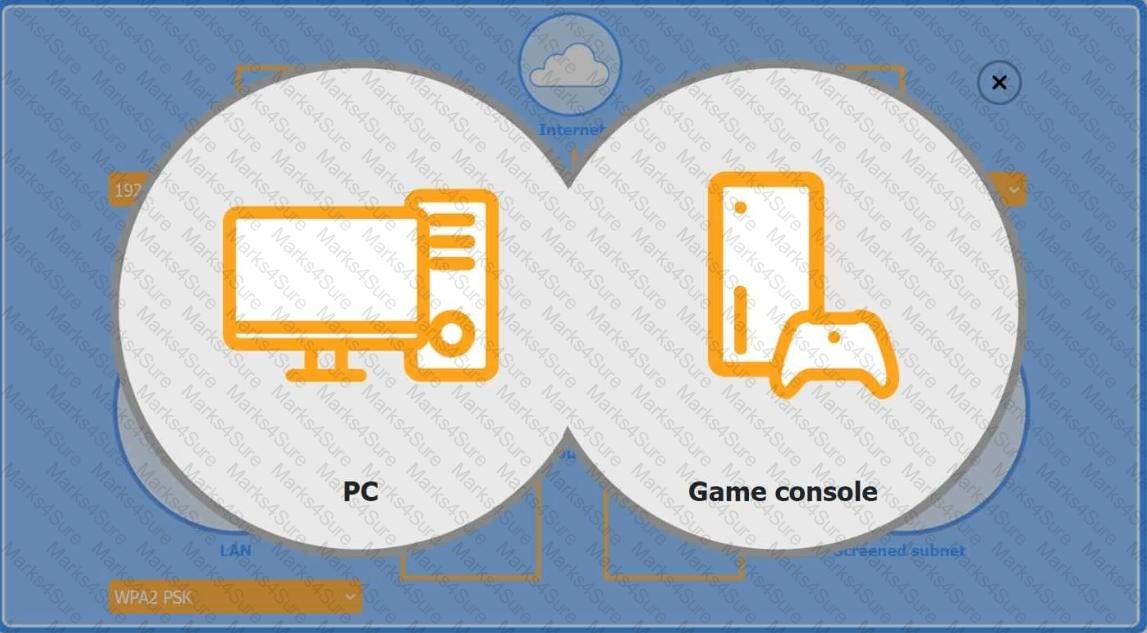
Firewall Screened Subnet
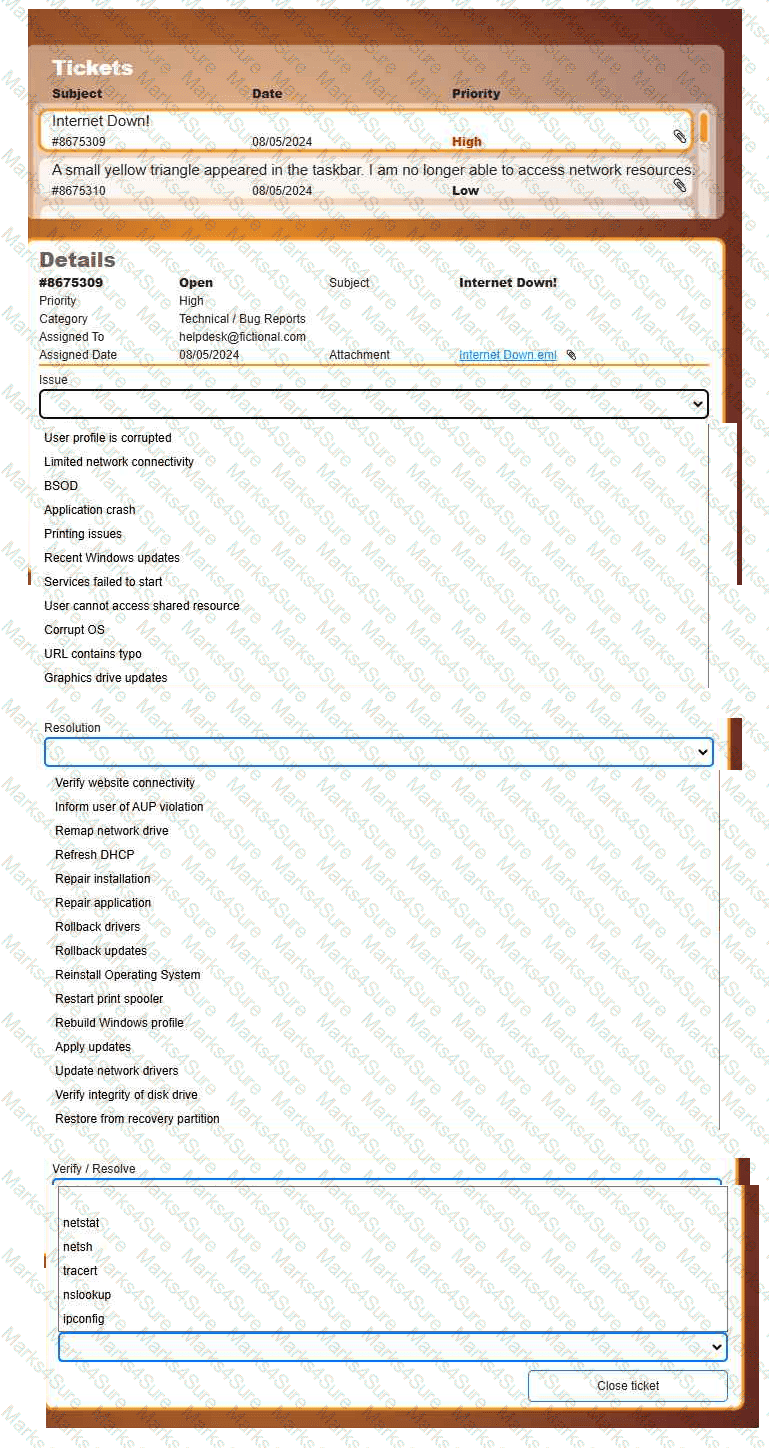
Welcome to your first day as a Fictional Company, LLC helpdesk employee. Please work the tickets in your helpdesk ticket queue.
INSTRUCTIONS
Click on individual tickets to see the ticket details, and view applicable attachments to
determine the problem.
Select the appropriate issue from the 'Issue' drop-down menu. Then, select the most
efficient resolution from the 'Resolution' drop-down menu. Finally, select the proper
command or verification to remediate or confirm your fix of the issue from the
'Verify/Resolve' drop-down menu.
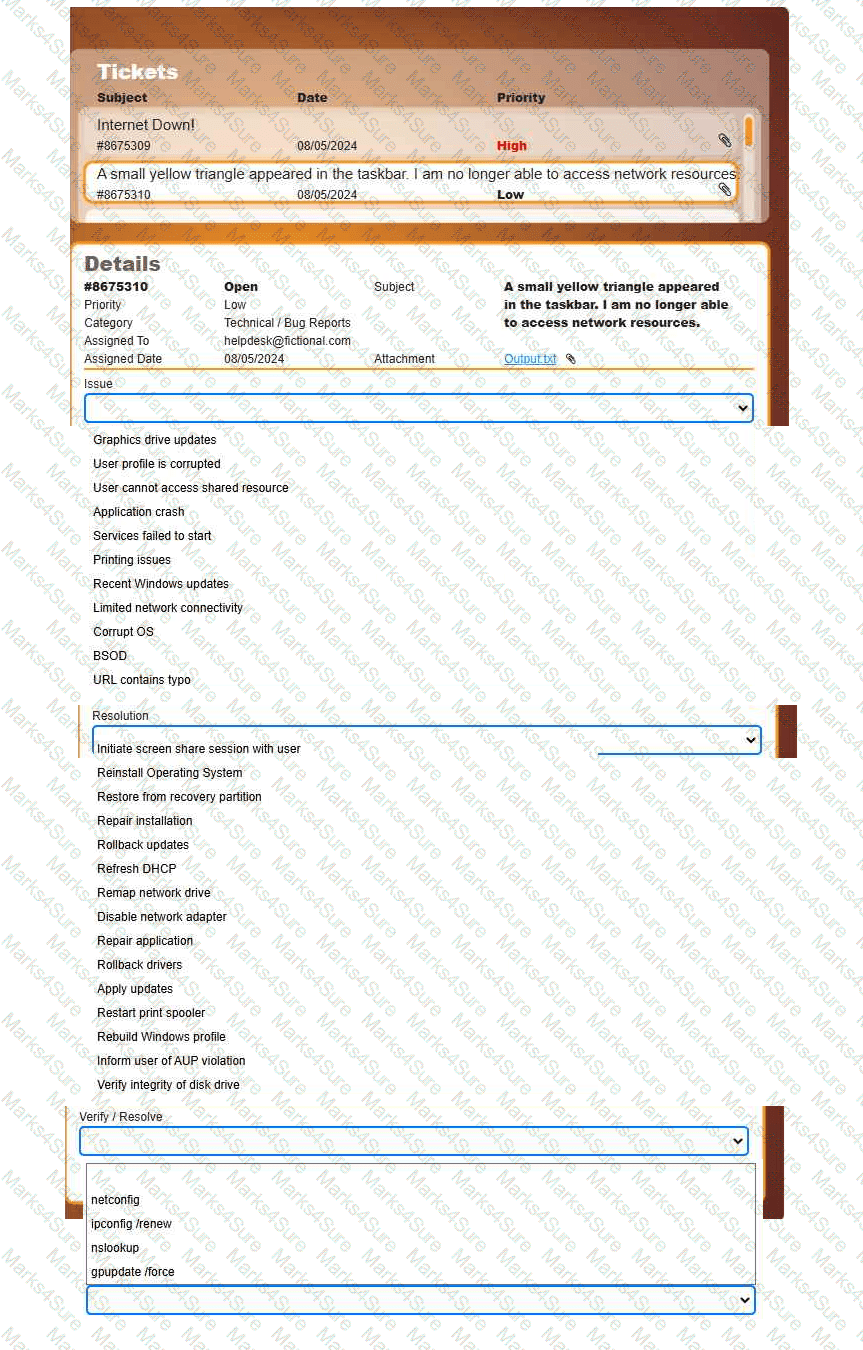
Welcome to your first day as a Fictional Company, LLC helpdesk employee. Please work the tickets in your helpdesk ticket queue.
INSTRUCTIONS
Click on individual tickets to see the ticket details, and view applicable attachments to
determine the problem.
Select the appropriate issue from the 'Issue' drop-down menu. Then, select the most
efficient resolution from the 'Resolution' drop-down menu. Finally, select the proper
command or verification to remediate or confirm your fix of the issue from the
'Verify/Resolve' drop-down menu.
Which of the following must be followed during incident response to ensure the collected evidence is properly handled and accounted for?
A technician needs to change hibernation settings on a Windows computer via a batch file. Domain policies are unavailable. Which is the best method?
A technician installs VPN client software that has a software bug from the vendor. After the vendor releases an update to the software, the technician attempts to reinstall the software but keeps getting an error message that the network adapter for the VPN already exists. Which of the following should the technician do next to mitigate this issue?
A user is trying to install a preferred word processor on their work laptop, but the installation fails each time. Which of the following is most likely the cause of this failure?
An end user is unable to access the intranet. A technician needs to confirm whether the Windows web server is online and functioning. Which of the following default remote access technologies would the technician most likely use to remotely connect to the server?
A user is trying to install a preferred word processor on their work laptop, but the installation fails each time. Which of the following is most likely the cause of this failure?
A help desk technician recently installed an SSH client on a workstation in order to access remote servers. What does this enable?
A senior administrator asks a help desk technician to run a set of commands on a remote network switch. After running the commands, the technician needs to collect the output and provide it to the administrator. Which of the following should the technician use to fulfill the administrator's request?
Technicians are failing to document user contact information, device asset tags, and a clear description of each issue in the ticketing system. What should the help desk management implement?
A Microsoft OS laptop user frequently forgets their password. Which alternative login method should a technician enable?
A company would like to deploy baseline images to new computers as they are started up on the network. Which of the following boot processes should the company use for this task?
A technician is installing a cloud-based productivity suite and gets an error saying the installation is unavailable. What should be tried first?
An engineer notices that many websites prompt users to input login and payment details. The engineer wants to require the browser to encrypt communications. Which of the following best helps to protect sensitive data?
A user receives a new personal computer but is unable to run an application. An error displays saying that .NET Framework 3.5 is required and not found. Which of the following actions is the best way to resolve this issue?
Thousands of compromised machines are attempting to make fake purchases from an online store. Which of the following is taking place?
A user decides to switch to Windows from Linux and is trying to migrate data using an external USB hard disk. However, when the user connects the cable to the Windows machine, an error message appears stating the device must be formatted before it can be used. The hard disk works as expected when connected to the Linux machine. Which of the following should the user do to resolve this issue?
After a technician upgrades the RAM on a user's workstation, the system shows a “No boot device found” message. Which of the following is most likely the cause?
A company wants to prevent unauthorized physical access to its mobile devices. Which of the following should the company do? (Select two).
Which of the following Microsoft Windows versions would most likely be installed on a server?
A Microsoft OS laptop user frequently forgets their password. Which alternative login method should a technician enable?
A customer’s computer does not have an active connection to the network. A technician goes through a few troubleshooting steps but is unable to resolve the issue. The technician has exhausted their knowledge. The customer expresses frustration at the time taken to resolve this issue. Which of the following should the technician do?
What is the next step a technician should take after completing malware cleanup?
A user logs in daily and cannot print a report. Help desk fixes it each day, but the issue recurs. What should be done so the issue doesn’t recur? (Select two)
A user notices that their smartphone's data usage has increased significantly even when the device is not in use. The phone feels warm, and its battery drains quickly. Which of the following should the user do to address this issue?
A user cannot upload files to corporate servers from their mobile device when outside the office, but uploads work fine in-office. What should a technician do to determine the root cause?
An end user wants to have a sales printer added to their computer. The printer is on the domain. Which of the following is the best method for the technician to add the printer?
A user wants to dispose of a failed hard drive in a way that ensures the data is unrecoverable. Which of the following is the best at-home method?
A technician needs to download and install a new web browser on a desktop. Which attribute should be used to verify the installer's authenticity?
Which of the following is used to apply corporate restrictions on an Apple device?