A security operations team is transitioning from alert-driven investigations to a mature threat hunting program. The team wants to focus on detecting adversaries who intentionally evade signature-based tools and traditional SIEM alerts by using legitimate credentials and native system utilities. Which hunting focus best supports this objective?
The CISO must improve the threat-hunting strategy to strengthen the organization's security posture and better prepare against sophisticated threats. Which aspect of the Threat Hunting Maturity Model can significantly enhance an organization's ability to address challenges outlined in the Pyramid of Pain?
Which hunting technique is MOST effective for detecting stealthy data exfiltration over standard web protocols?
After completing a threat hunt that uncovered previously undetected credential abuse, the SOC wants to ensure long-term improvement in detection and response capabilities. Which action BEST represents the final and most critical phase of the threat hunting lifecycle?
Refer to the exhibit.
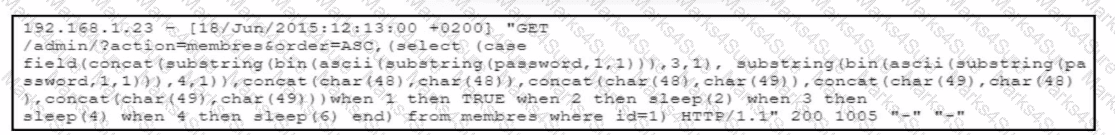
The cybersecurity team at a company detects an ongoing attack directed at the web server that hosts the company website. The team analyzes the logs of the web application firewall and discovers several HTTP requests encoded in Base64. The team decodes the payloads and retrieves the HTTP requests. What did the attackers use to exploit the server?
While investigating multiple incidents using Cisco telemetry, analysts notice that attackers consistently use valid credentials, avoid malware, and rely on remote management protocols. Why is this information valuable for attribution?
A threat hunter is asked to model how an attacker could abuse cloud identity misconfigurations to escalate privileges without exploiting software vulnerabilities. Which modeling approach BEST supports this analysis?
While investigating multiple incidents, analysts notice that attackers consistently use SMB for lateral movement and avoid PowerShell execution. Why is this observation valuable for attribution?
A threat hunting team wants to ensure hunts are repeatable, scalable, and less dependent on individual analyst intuition. What is the MOST important process improvement?
While analyzing telemetry from Cisco Secure Endpoint and Secure Network Analytics, analysts observe that an adversary consistently avoids deploying malware and instead abuses built-in administrative tools. Why does this observation matter for attribution?
After a multi-week threat hunting exercise, a security team confirms that an attacker gained access using valid credentials, moved laterally, and exfiltrated data without deploying malware. Senior leadership asks how the hunting program reduced organizational risk. Which outcome BEST demonstrates the value of threat hunting?
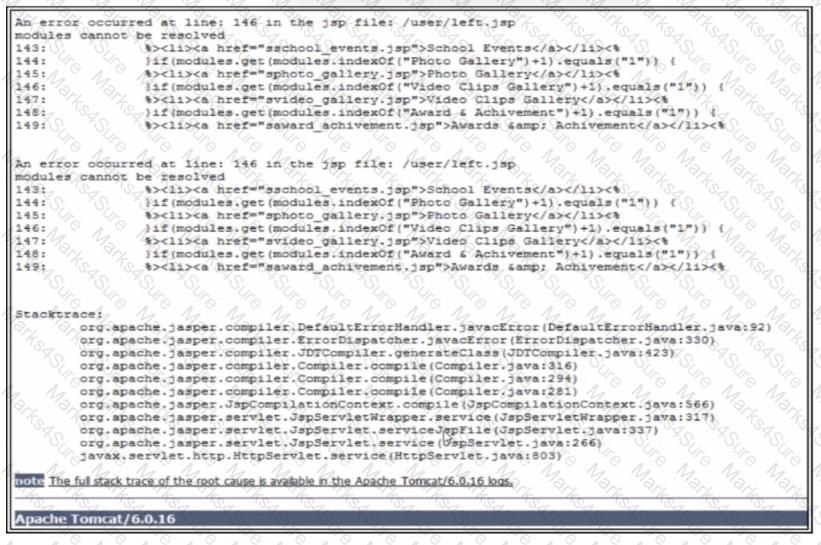
Refer to the exhibit. A penetration test performed against a web application generates the error message. Which two pieces of information are exposed? (Choose two.) Q Internal paths of the web server
A SOC manager wants to evaluate whether the organization’s Cisco-based threat hunting program is improving over time. Which metric BEST reflects increased threat hunting effectiveness?
Refer to the exhibit.

A company went through several rounds of restructuring and the previous security team has been let go A new engineer joins and rediscovers all the tools thatthe previous team left behind.One of the tools Is a Bash script related to monitoring AWS accounts for threats What is the purpose of the script?
A SOC team using Cisco security technologies wants to improve its ability to detect threats that bypass traditional security controls by abusing valid user credentials. Which hunting focus MOST effectively addresses this challenge?