A network engineer is in the predeployment discovery phase of a Cisco ISE deployment and must discover the network. There is an existing network management system in the network.
Which type of probe must be configured to gather the information?
Which two events trigger a CoA for an endpoint when CoA is enabled globally for ReAuth? (Choose two.)
An engineer is configuring Cisco ISE policies to support MAB for devices that do not have 802.1X capabilities. The engineer is configuring new endpoint identity groups as conditions to be used in the AuthZ policies, but noticed that the endpoints are not hitting the correct policies. What must be done in order to get the devices into the right policies?
An administrator is adding a switch to a network that is running Cisco ISE and is only for IP Phones The phones do not have the ability to authenticate via 802 1X Which command is needed on each switch port for authentication?
A network administrator adds network access devices to Cisco ISE. After a security breach, the management team mandates that all network devices must comply with certain standards. All network devices must authenticate through Cisco ISE. Some devices use nondefault CoA ports.
What must be configured in Cisco ISE?
An organization is migrating its current guest network to Cisco ISE and has 1000 guest users in the current database There are no resources to enter this information into the Cisco ISE database manually. What must be done to accomplish this task effciently?
A customer wants to set up the Sponsor portal and delegate the authentication flow to a third party for added security while using Kerberos Which database should be used to accomplish this goal?
A network engineer must configure BYOD using Cisco ISE. In the deployment, the users must be able to submit CSR through the end devices. Which two features must be enabled to meet the requirement?
(Choose two.)
Which two methods should a sponsor select to create bulk guest accounts from the sponsor portal? (Choose two )
The Cisco Wireless LAN Controller and guest portal must be set up in Cisco ISE. These configurations were performed:
• configured all the required Cisco Wireless LAN Controller configurations
• added the wireless controller to Cisco ISE network devices
• created an endpoint identity group
• configured credentials to be sent by email
• configured the SMTP server
• configured an authorization profile with redirection to the guest portal and redirected the access control list
• configured an authentication policy for MAB users
• created an authorization policy
Which two components would be required to complete the configuration? (Choose two.)
Which two components are required for creating a Native Supplicant Profile within a BYOD flow? (Choose two)
TION NO: 69
Refer to the exhibit.
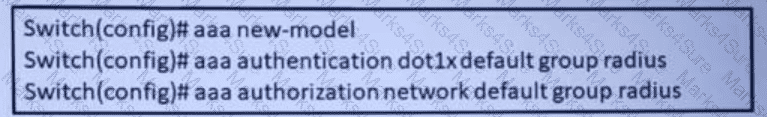
A network engineers configuring the switch to accept downloadable ACLs from a Cisco ISC server Which two commands should be run to complete the configuration? (Choose two)
An engineer is assigned to enhance security across the campus network. The task is to enable MAB across all access switches in the network. Which command must be entered on the switch to enable MAB?
A network engineer must create a guest portal for wireless guests on Cisco ISE. The guest users must not be able to create accounts; however, the portal should require a username and password to connect. Which portal type must be created in Cisco ISE to meet the requirements?
An administrator is configuring the Native Supplicant Profile to be used with the Cisco ISE posture agents and needs to test the connection using wired devices to determine which profile settings are available. Which two configuration settings should be used to accomplish this task? (Choose two.)
Which two external identity stores are supported by Cisco ISE for password types? (Choose two.)
Which command displays all 802 1X/MAB sessions that are active on the switch ports of a Cisco Catalyst switch?
An engineer must use Cisco ISE profiler services to provide network access to Cisco IP phones that cannot support 802.1X. Cisco ISE is configured to use the access switch device sensor information — system-description and platform-type — to profile Cisco IP phones and allow access.
Which two protocols must be configured on the switch to complete the configuration? (Choose two.)
A network administrator is configuring authorization policies on Cisco ISE There is a requirement to use AD group assignments to control access to network resources After a recent power failure and Cisco ISE rebooting itself, the AD group assignments no longer work What is the cause of this issue?
An engineer is configuring TACACS+ within Cisco ISE for use with a non-Cisco network device. They need to send special attributes in the Access-Accept response to ensure that the users are given the appropriate access. What must be configured to accomplish this'?
An administrator is adding network devices for a new medical building into Cisco ISE. These devices must be in a network device group that is identifying them as "Medical Switch" so that the policies can be made separately for the endpoints connecting through them. Which configuration item must be changed in the network device within Cisco ISE to accomplish this goal?
An engineer is implementing Cisco ISE and needs to configure 802.1X. The port settings are configured for port-based authentication. Which command should be used to complete this configuration?
Which two probes must be enabled for the ARP cache to function in the Cisco ISE profile service so that a user can reliably bind the IP address and MAC addresses of endpoints? (Choose two.)
A Cisco ISE administrator needs to ensure that guest endpoint registrations are only valid for one day When testing the guest policy flow, the administrator sees that the Cisco ISE does not delete the endpoint in the Guest Endpoints identity store after one day and allows access to the guest network after that period. Which configuration is causing this problem?
An engineer is working with a distributed deployment of Cisco ISE and needs to configure various network probes to collect a set of attributes from the endpoints on the network. Which node should be used to accomplish this task?
An engineer is configuring the remote access VPN to use Cisco ISE for AAA and needs to conduct posture checks on the connecting endpoints After the endpoint connects, it receives its initial authorization result and continues onto the compliance scan What must be done for this AAA configuration to allow compliant access to the network?
An administrator is configuring RADIUS on a Cisco switch with a key set to Cisc403012128 but is receiving the error “Authentication failed: 22040 Wrong password or invalid shared secret. “what must be done to address this issue?
Which type of identity store allows for creating single-use access credentials in Cisco ISE?
An organization is adding nodes to their Cisco ISE deployment and has two nodes designated as primary and secondary PAN and MnT nodes. The organization also has four PSNs An administrator is adding two more PSNs to this deployment but is having problems adding one of them What is the problem?
A network engineer is configuring Cisco TrustSec and needs to ensure that the Security Group Tag is being transmitted between two devices Where in the Layer 2 frame should this be verified?
Refer to the exhibit:
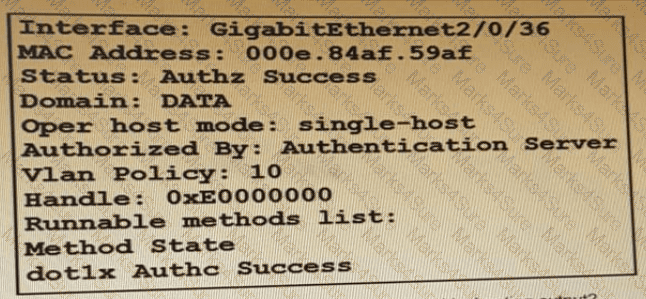
Which command is typed within the CU of a switch to view the troubleshooting output?
Refer to the exhibit.
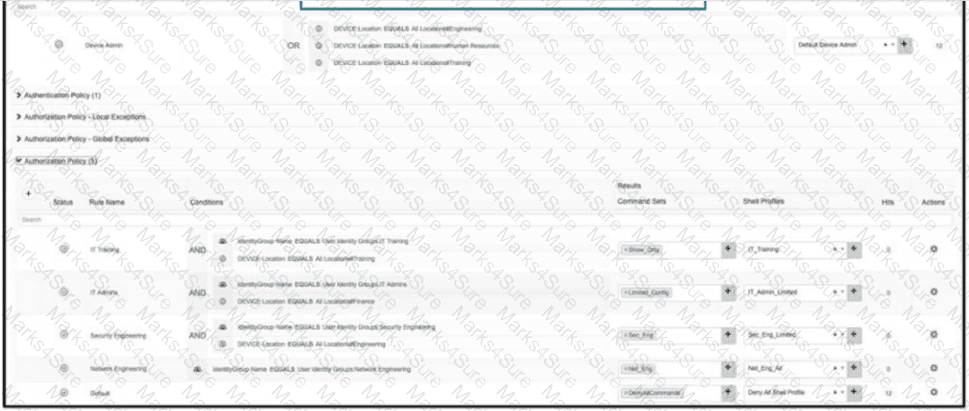
An organization recently implemented network device administration using Cisco ISE. Upon testing the ability to access all of the required devices, a user in the Cisco ISE group IT Admins is attempting to login to a device in their organization's finance department but is unable to. What is the problem?
Which two task types are included in the Cisco ISE common tasks support for TACACS+ profiles?
(Choose two.)
An administrator must provide network access to legacy Windows endpoints with a specific device type and operating system version using Cisco ISE profiler services. The ISE profiler services and access switches must be configured to identify endpoints using the dhcp-class-identifier and parameters-request-list attributes from the DHCP traffic. These configurations were performed:
enabled the DHCP probe in Cisco ISE
configured the Cisco ISE PSN interface to receive DHCP packets
configured the attributes in custom profiling conditions
configured a custom profiling policy
configured an authorization rule with permit access
Which action completes the configuration?
A Cisco ISE administrator must authenticate users against Microsoft Active Directory. The solution must meet these requirements:
Users and computers must be authenticated.
User groups must be retrieved during authentication.
Which protocol must be added to the allowed protocols on the policy to authenticate the users?
Drag and drop the description from the left onto the protocol on the right that is used to carry out system authentication, authentication, and accounting.
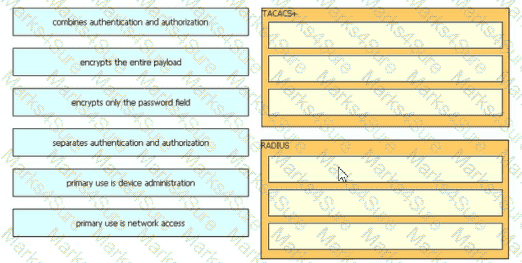
An administrator adds a new network device to the Cisco ISE configuration to authenticate endpoints to the network. The RADIUS test fails after the administrator configures all of the settings in Cisco ISE and adds the proper configurations to the switch. What is the issue"?
An organization is hosting a conference and must make guest accounts for several of the speakers attending. The conference ended two days early but the guest accounts are still being used to access the network. What must be configured to correct this?
An engineer is implementing network access control using Cisco ISE and needs to separate the traffic based on the network device ID and use the IOS device sensor capability. Which probe must be used to accomplish this task?
A Cisco ISE administrator must restrict specific endpoints from accessing the network while in closed mode. The requirement is to have Cisco ISE centrally store the endpoints to restrict access from. What must be done to accomplish this task''
Which port does Cisco ISE use for native supplicant provisioning of a Windows laptop?
An engineer must organize endpoints in a Cisco ISE identity management store to improve the operational management of IP phone endpoints. The endpoints must meet these requirements:
• classify endpoints for finance, sales, and marketing departments
• tag each endpoint as profiled
Which action organizes the endpoints?
What are two components of the posture requirement when configuring Cisco ISE posture? (Choose two)
A network engineer needs to deploy 802.1x using Cisco ISE in a wired network environment where thin clients download their system image upon bootup using PXE. For which mode must the switch ports be configured?
An engineer has been tasked with standing up a new guest portal for customers that are waiting in the lobby. There is a requirement to allow guests to use their social media logins to access the guest network to appeal to more customers What must be done to accomplish this task?
An administrator connects an HP printer to a dot1x enable port, but the printer in not accessible Which feature must the administrator enable to access the printer?
An engineer is configuring static SGT classification. Which configuration should be used when authentication is disabled and third-party switches are in use?
Wireless network users authenticate to Cisco ISE using 802.1X through a Cisco Catalyst switch. An engineer must create an updated configuration to assign a security group tag to the user's traffic using inline tagging to prevent unauthenticated users from accessing a restricted server. The configurations were performed:
• configured Cisco ISE as a Cisco TrustSec AAA server
• configured the switch as a RADIUS device in Cisco ISE
• configured the wireless LAN controller as a TrustSec device in Cisco ISE
• created a security group tog for the wireless users
• created a certificate authentication profile
■ created an identity source sequence
• assigned an appropriate security group tag to the wireless users
• defined security group access control lists to specify an egress policy
• enforced the access control lists on the TrustSec policy matrix in Cisco ISE
• configured TrustSec on the switch
• configured TrustSec on the wireless LAN controller
Which two actions must be taken to complete the configuration? (Choose two.)
An administrator needs to add a new third party network device to be used with Cisco ISE for Guest and BYOD authorizations. Which two features must be configured under Network Device Profile to achieve this? (Choose two.)
What is a valid status of an endpoint attribute during the device registration process?
A network administrator notices that after a company-wide shut down, many users cannot connect their laptops to the corporate SSID. What must be done to permit access in a timely manner?
An engineer is unable to use SSH to connect to a switch after adding the required CLI commands to the device to enable TACACS+. The device administration license has been added to Cisco ISE, and the required policies have been created. Which action is needed to enable access to the switch?
An engineer is configuring a new Cisco ISE node. Context-sensitive information must be shared between the Cisco ISE and a Cisco ASA. Which persona must be enabled?
An administrator plans to use Cisco ISE to deploy posture policies to assess Microsoft Windows endpoints that run Cisco Secure Client. The administrator wants to minimize the occurrence of messages related to unknown posture profiles if Cisco ISE fails to determine the posture of the endpoint. Secure Client is deployed to all the endpoints. and all the required Cisco ISE authentication, authorization, and posture policy configurations were performed. Which action must be taken next to complete the configuration?
What must be configured on the WLC to configure Central Web Authentication using Cisco ISE and a WLC?
An administrator is configuring a Cisco ISE posture agent in the client provisioning policy and needs to ensure that the posture policies that interact with clients are monitored, and end users are required to comply with network usage rules Which two resources must be added in Cisco ISE to accomplish this goal? (Choose two)
Refer to the exhibit.
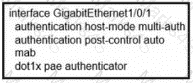
Which switch configuration change will allow only one voice and one data endpoint on each port?
An organization is implementing Cisco ISE posture services and must ensure that a host-based firewall is in place on every Windows and Mac computer that attempts to access the network They have multiple vendors’ firewall applications for their devices, so the engineers creating the policies are unable to use a specific application check in order to validate the posture for this What should be done to enable this type of posture check?
A user reports that the RADIUS accounting packets are not being seen on the Cisco ISE server.
Which command is the user missing in the switch’s configuration?
A network engineer has been tasked with enabling a switch to support standard web authentication for Cisco ISE. This must include the ability to provision for URL redirection on authentication Which two commands must be entered to meet this requirement? (Choose two)
An engineer is starting to implement a wired 802.1X project throughout the campus. The task is to ensure that the authentication procedure is disabled on the ports but still allows all endpoints to connect to the network. Which port-control option must the engineer configure?
Using the SAK Active Directory Federation Services server. The configurations were performed:
• created a new SAML Identity provider profile in Cisco ISE
• exported the service provider Information
• configured all the required Active Directory Federation Services configurations
• Imported the Active Directory Federation Services metadata
• configured groups in the new SAML identity
• added attributes to the new SAML identity provider profile
• configured Advanced Settings in the new SAML identity provider profile
Which two actions must be taken to complete the configuration? (Choose two.)
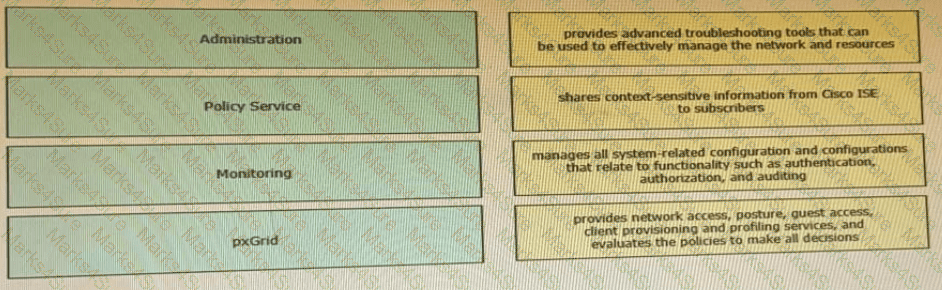
Drag the Cisco ISE node types from the left onto the appropriate purposes on the right.
An engineer is configuring a guest password policy and needs to ensure that the password complexity requirements are set to mitigate brute force attacks. Which two requirement complete this policy? (Choose two)
ESTION NO: 100
An organization wants to improve their BYOD processes to have Cisco ISE issue certificates to the BYOD endpoints. Currently, they have an active certificate authority and do not want to replace it with Cisco ISE. What must be configured within Cisco ISE to accomplish this goal?
When configuring Active Directory groups, what does the Cisco ISE use to resolve ambiguous group names?
An engineer is configuring ISE for network device administration and has devices that support both protocols. What are two benefits of choosing TACACS+ over RADUs for these devices? (Choose two.)
The security team identified a rogue endpoint with MAC address 00:46:91:02:28:4A attached to the network. Which action must security engineer take within Cisco ISE to effectively
restrict network access for this endpoint?
Which compliance status is set when a matching posture policy has been defined for that endpomt. but all the mandatory requirements during posture assessment are not met?
A network security administrator wants to integrate Cisco ISE with Active Directory. Which configuration action must the security administrator take to accomplish the task?
An engineer is deploying a new Cisco ISE environment for a company. The company wants the deployment to use TACACS+. The engineer verifies that Cisco ISE has a Device Administration license. What must be configured to enable TACACS+ operations?