If the SIEM generates the following four alerts at the same time:
I.Firewall blocking traffic from getting into the network alerts
II.SQL injection attempt alerts
III.Data deletion attempt alerts
IV.Brute-force attempt alerts
Which alert should be given least priority as per effective alert triaging?
Which of the following security technology is used to attract and trap people who attempt unauthorized or illicit utilization of the host system?
What does [-n] in the following checkpoint firewall log syntax represents?
fw log [-f [-t]] [-n] [-l] [-o] [-c action] [-h host] [-s starttime] [-e endtime] [-b starttime endtime] [-u unification_scheme_file] [-m unification_mode(initial|semi|raw)] [-a] [-k (alert name|all)] [-g] [logfile]
What type of event is recorded when an application driver loads successfully in Windows?
Which of the following tool can be used to filter web requests associated with the SQL Injection attack?
Harley is working as a SOC analyst with Powell Tech. Powell Inc. is using Internet Information Service (IIS) version 7.0 to host their website.
Where will Harley find the web server logs, if he wants to investigate them for any anomalies?
Which of the following attacks causes sudden changes in file extensions or increase in file renames at rapid speed?
Juliea a SOC analyst, while monitoring logs, noticed large TXT, NULL payloads.
What does this indicate?
Charline is working as an L2 SOC Analyst. One day, an L1 SOC Analyst escalated an incident to her for further investigation and confirmation. Charline, after a thorough investigation, confirmed the incident and assigned it with an initial priority.
What would be her next action according to the SOC workflow?
Which of the following steps of incident handling and response process focus on limiting the scope and extent of an incident?
Which attack works like a dictionary attack, but adds some numbers and symbols to the words from the dictionary and tries to crack the password?
In which phase of Lockheed Martin's – Cyber Kill Chain Methodology, adversary creates a deliverable malicious payload using an exploit and a backdoor?
Ray is a SOC analyst in a company named Queens Tech. One Day, Queens Tech is affected by a DoS/DDoS attack. For the containment of this incident, Ray and his team are trying to provide additional bandwidth to the network devices and increasing the capacity of the servers.
What is Ray and his team doing?
John, a SOC analyst, while monitoring and analyzing Apache web server logs, identified an event log matching Regex /(\.|(%|%25)2E)(\.|(%|%25)2E)(\/|(%|%25)2F|\\|(%|%25)5C)/i.
What does this event log indicate?
Which of the following contains the performance measures, and proper project and time management details?
John, a threat analyst at GreenTech Solutions, wants to gather information about specific threats against the organization. He started collecting information from various sources, such as humans, social media, chat room, and so on, and created a report that contains malicious activity.
Which of the following types of threat intelligence did he use?
Which of the following is a correct flow of the stages in an incident handling and response (IH&R) process?
Banter is a threat analyst in Christine Group of Industries. As a part of the job, he is currently formatting and structuring the raw data.
He is at which stage of the threat intelligence life cycle?
Which of the following event detection techniques uses User and Entity Behavior Analytics (UEBA)?
According to the forensics investigation process, what is the next step carried out right after collecting the evidence?
Which of the following attack can be eradicated by filtering improper XML syntax?
Rinni, SOC analyst, while monitoring IDS logs detected events shown in the figure below.
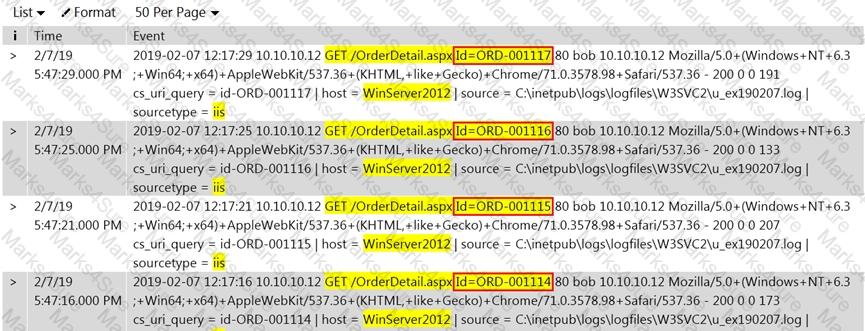
What does this event log indicate?
Which of the following attack can be eradicated by using a safe API to avoid the use of the interpreter entirely?
Which of the following are the responsibilities of SIEM Agents?
1.Collecting data received from various devices sending data to SIEM before forwarding it to the central engine.
2.Normalizing data received from various devices sending data to SIEM before forwarding it to the central engine.
3.Co-relating data received from various devices sending data to SIEM before forwarding it to the central engine.
4.Visualizing data received from various devices sending data to SIEM before forwarding it to the central engine.