Which technology reduces the implementation of STP and leverages both unicast and multicast?

Refer to the exhibit. Which Python snippet stores the data structure of the device in JSON format?
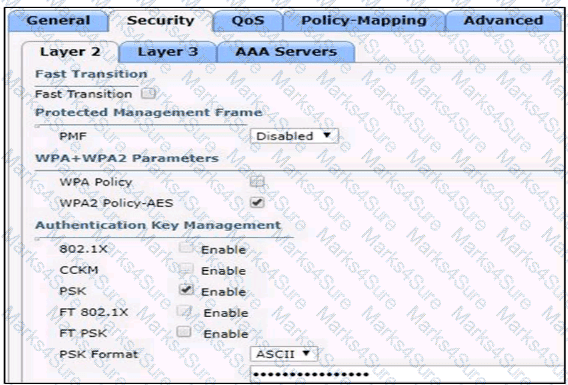
Based on the configuration in this WLAN security setting,Which method can a client use to authenticate to the network?
Which two components are needed when a Cisco SD-Access fabric is designed? (Choose two.)
Which configuration enables a Cisco router lo send information to a TACACS+ server for individual EXEC commands associated with privilege level 15?
A customer wants to use a single SSID to authenticate loT devices using different passwords. Which Layer 2 security type must be configured in conjunction with Cisco ISE to achieve this requirement?
Which two Cisco SD-Access components provide communication between traditional network elements and the controller layer? (Choose two.)
Refer to the exhibit.
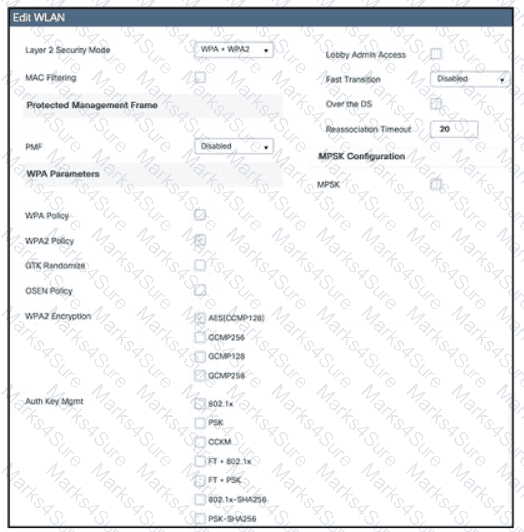
Which action must be taken to configure a WLAN for WPA2-AES with PSK and allow only 802.11r-capable clients to connect?
Refer to the exhibit. A customer reports occasional brief audio dropouts on its Cisco Wi-Fi phones. The environment consists of a Cisco Catalyst 9800 Series WLC with Catalyst 9120 APs running RRM. The phones connect on the 5-GHz band. Which action resolves this issue?
An engineer is configuring local web authentication on a WLAN. The engineer chooses the Authentication radio button under the Layer 3 Security options for Web Policy. Which device presents the web authentication for the WLAN?
A wireless administrator must create a new web authentication corporate SSID that will be using ISE as the external RADIUS server. The guest VLAN must be specified after the authentication completes. Which action must be performed to allow the ISE server to specify the guest VLAN?
Which next generation firewall feature supports separate security services for multiple departments?
Which new security enhancement is introduced by deploying a next-generation firewall at the data center in addition to the Internet edge?
What is calculated using the numerical values of the transmitter power level, cable loss, and antenna gain?