The service provider is serving hosts with two different multicast streams from source X and source Y. Source X is multicast group 224.0.0.0/8, and source Y is multicast group 226.0.0.0/8. Multicast source X should send its stream through bidirectional RP address 10.20.1.1, and multicast source Y should send its stream through RP address 10.20.2.1. Which configuration meets these requirements?
Refer to the exhibit.
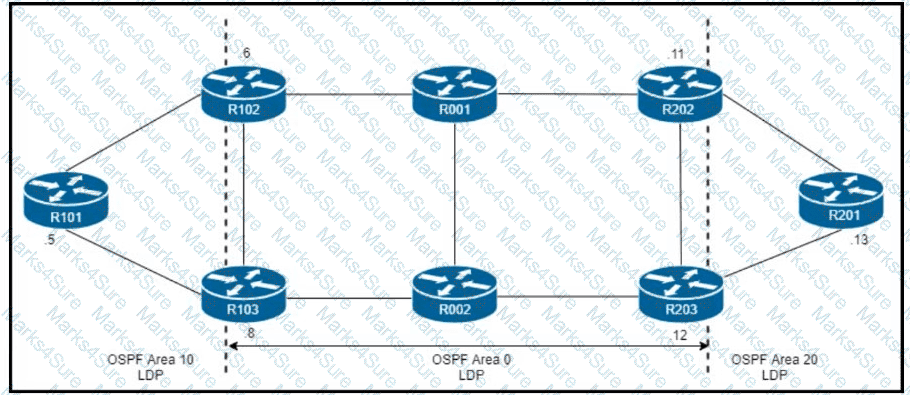
R101 is peering with R102 and R103, and R201 is peering with R202 and R203 using iBGP Labeled Unicast address families. The OSPF area 0 border routers are in a full iBGP Labeled Unicast mesh, and VPNv4 routes are exchanged directly between PE routers R101 and R201 through iBGP Which address family-level configuration must be applied on ABR R102 on ABR R102 to support a Unified MPLS routing architecture with partitioned IGP domains?
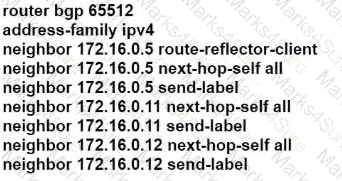
A)

B)
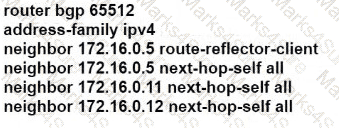
C)
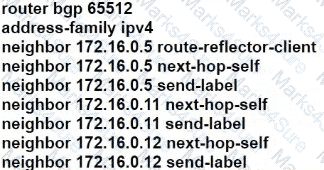
D)
Refer to the exhibit.
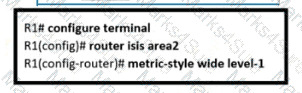
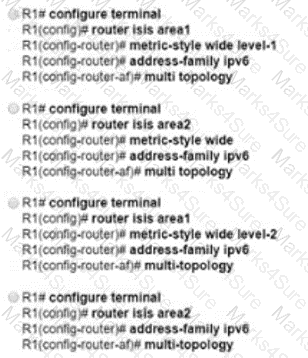
An engineer is configuring multitopology IS-IS for IPv6 on router R1. Which additional configuration must be applied to the router to complete the task?
Refer to the exhibit.
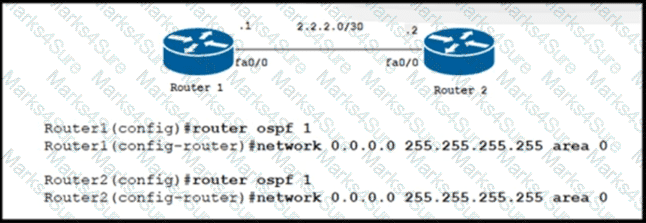
A network engineer must configure an LDP neighborship between two newly installed routers that are located in two different offices. Router 1 is the core router in the network and it has already established OSPF adjacency with router 2. On router 1 and router 2. interface fa0/0 is configured for BFD. Which additional configuration must the engineer apply to the two devices to meet the requirement?
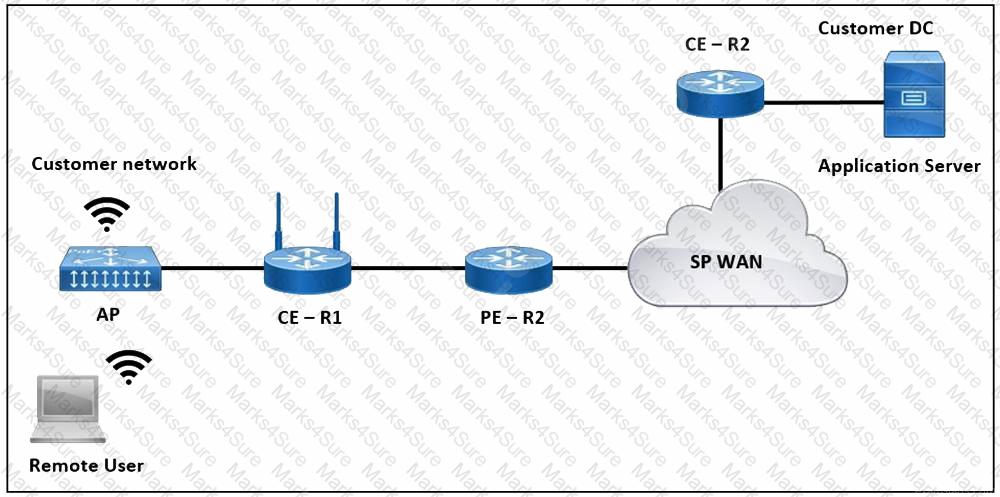
Refer to the exhibit. The application server in the data center hosts voice, video, and data applications over the internet. The data applications run more slowly than the voice and video applications. To ensure that all applications run smoothly, the service provider decided to implement a QoS policy on router PER 2 to apply traffic shaping. Which two actions must an engineer take to implement the task? (Choose two.)
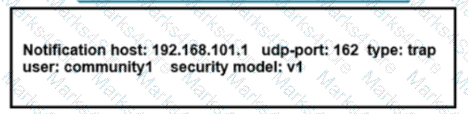
Refer to the exhibit. Over the last few months. ISP A has doubled Its user base. The IT Director asked the engineering team to monitor memory consumption and buffer statistics on all P and PE devices In the MPLS core. Most devices have CPU usage of 70% or more, so the solution must be targeted and secure. Which two commands must the engineering team implement on P and PE devices to meet these requirements? (Choose two.)
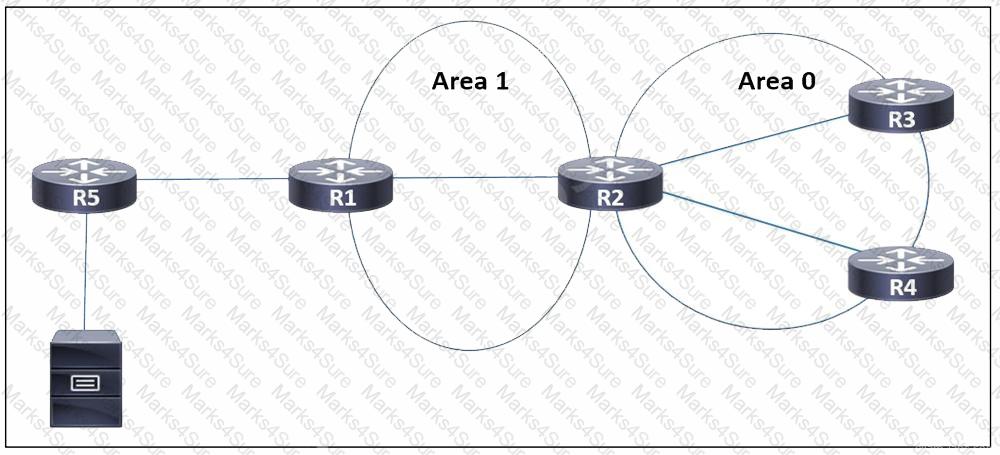
Refer to the exhibit. EIGRP is running between routers R5 and R1, and OSPF is used in the rest of the network. Users in a network attached to router R3 need to access a server connected to R5. Which task must the engineer perform so that only the users attached to R3 are able to access the server, but no other network is shared to OSPF?
Refer to the exhibit:
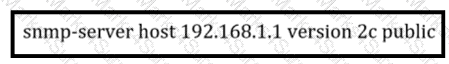
A network administrator wants to enhance the security for SNMP for this configuration.
Which action can the network administrator implement?
Which programmable API allows the service provider to plan and optimize the automation of network operations and achieve closed-loop operations?
In an EVPN operation, how does the PE determine and advertise Ethernet segment reachability?
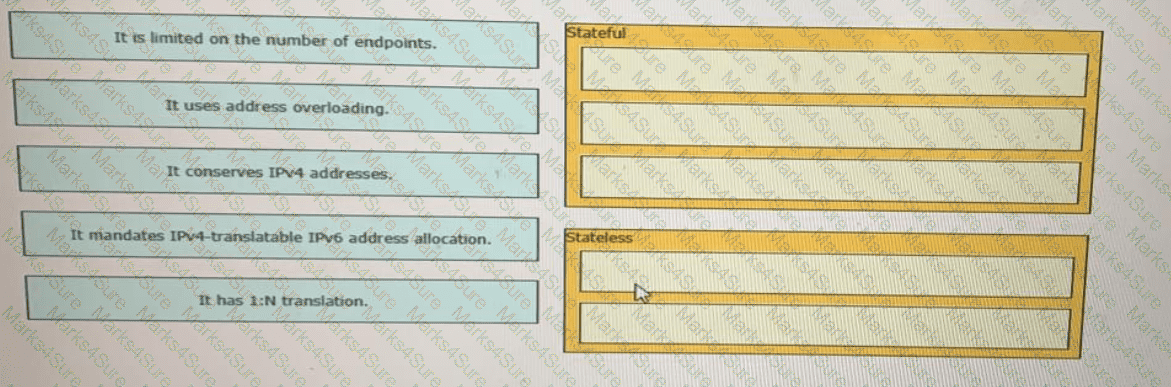
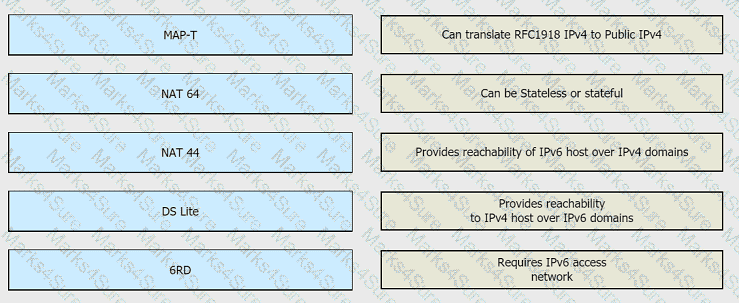
Drag and drop the NAT64 descriptions from the left onto the correct NAT64 types on the right.
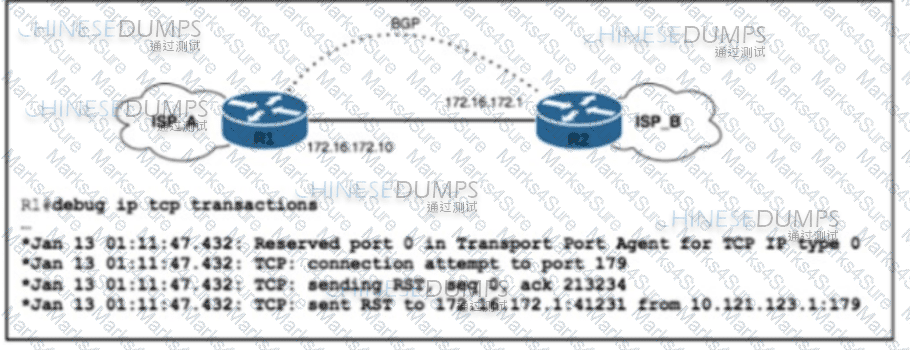
Refer to the exhibit. ISP_A and ISP_B use AS numbers 38321 and 16213 respectively. After a network engineer reloaded router R1, the BGP session with R2 failed to establish. The engineer confirmed BGP next-hop availability with a connectivity test between the router loopback addresses 10.121.123.2 and 10.121.123.1, as well as between interfaces Gi1/1 and Gi1/2. EBGP multihop has been configured on both routers. Which action must the engineer take to resolve the issue?
Which technology enables the addition of new wavelengths in a fiber-optic network?
A company needs to improve the use of the network resources that is used to deploy internet access service to customers on separate backbone and internet access network. Which two major design models should be used to configure MPLS L3VPNs and internet service in the same MPLS backbone? (Choose two.)
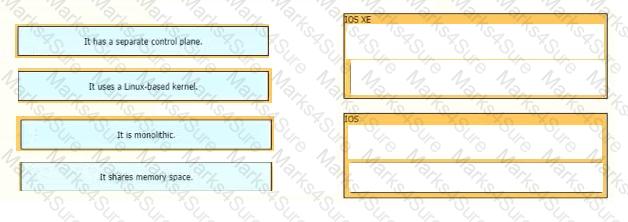
Drag and drop the descriptions from the left onto the corresponding OS types on the right.
Which statement about TLS is accurate when using RESTCONF to write configurations on network devices'?
Refer to the exhibit.
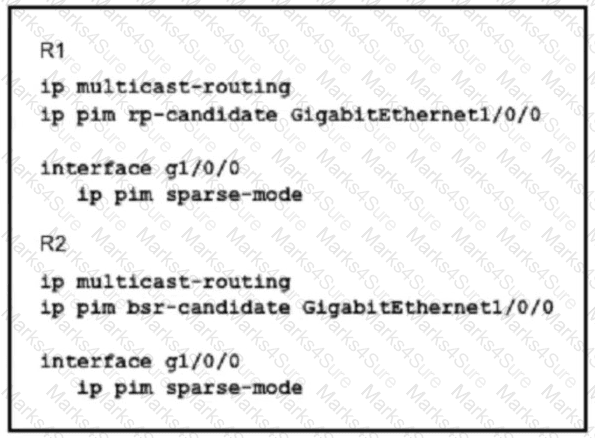
An engineer configured multicast routing on client's network. What is the effect of this multicast implementation?
Refer to the exhibit.
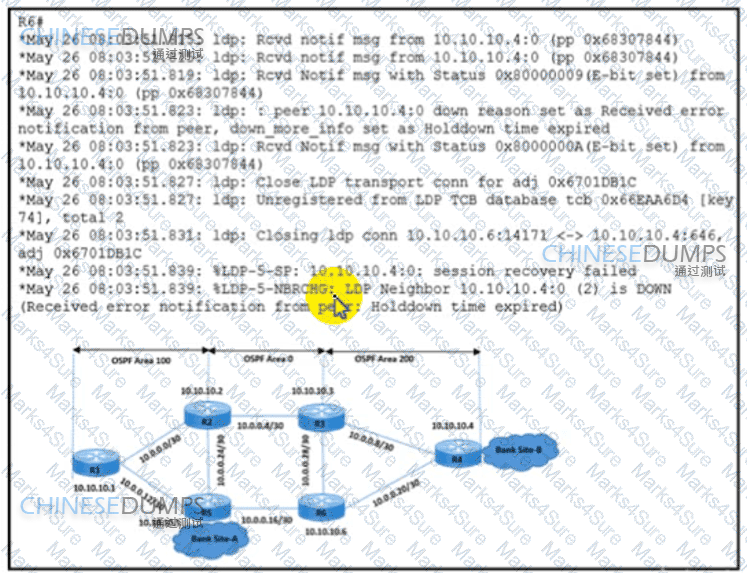
A network engineer is implementing an LDP-based MPLS solution to enable packet flow between the two bank sites The engineer was given two requirements
·LDP peering must stay up when there is a link failure between R3 and R6
·LDP peering must not flap when there is a link failure between R5 and R6
Which action meets these requirements?
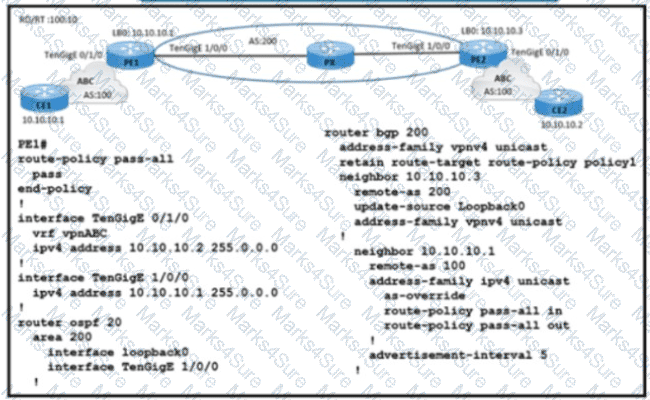
Refer to the exhibit. A service provider engineer Is configuring the connection between CE1 and CE2. AS 200 of the service provider and AS 100 of enterprise ABC should connect using BGP. The engineer already completed the configuration of VRF RT 100:10 of enterprise ABC. Which configuration must the engineer apply on PE1 to meet the requirement?
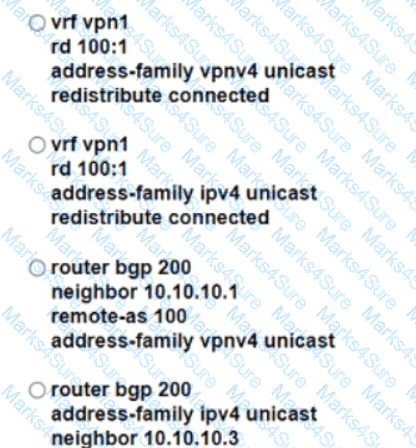
Refer to the exhibit:
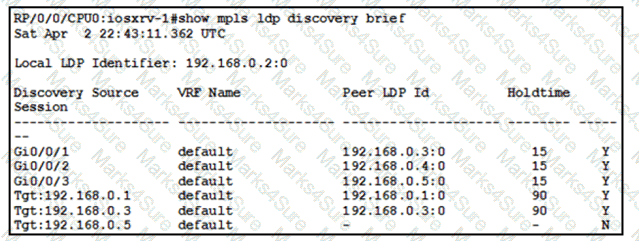
With which router does IOSXRV-1 have LDP session protection capability enabled but session hold up is not active?
Refer to the exhibit.
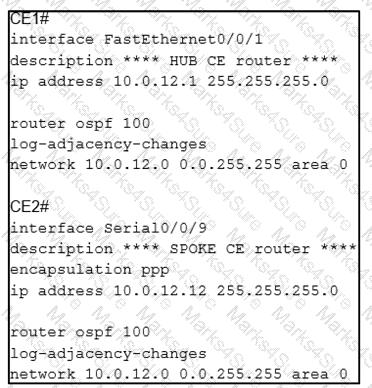
A network engineer is configuring customer edge routers to finalize a L2VPN over MPLS deployment Assume that the AToM L2VPN service that connects the two CEs is configured correctly on the service provider network Which action causes the solution to fail?
Refer to the exhibit. An organization s network recently experienced several significant outages due to device failures. The network administrator just moved the network devices to a new central data center, and packets are switched using labels. The administrator Is now implementing NSF on the network to reduce potential risk factors in the event of another outage. Which task must the administrator perform on each router as part of the process?
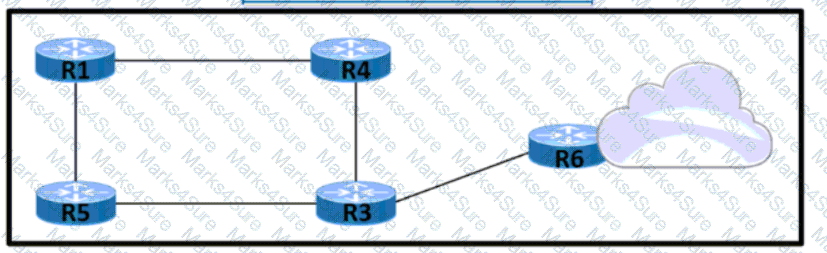
Refer to the exhibit.

Router R1 is reporting that its BGP neighbor adjacency to router R2 is down, but its state is Active as shown. Which configuration must be applied to routers R1 and R2 to fix the problem?
A)
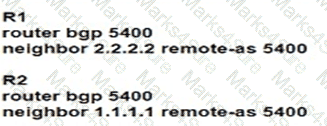
B)
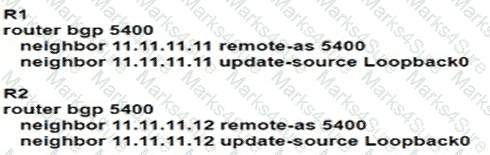
C)
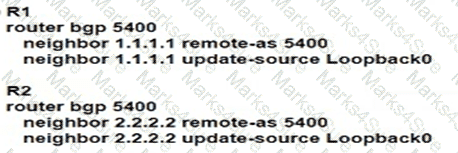
D)
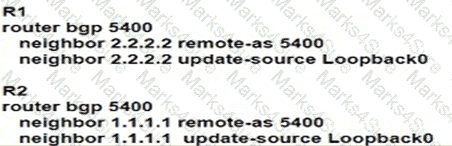
What is the purpose of OSPF-TE extensions to MPLS traffic engineering functionality?
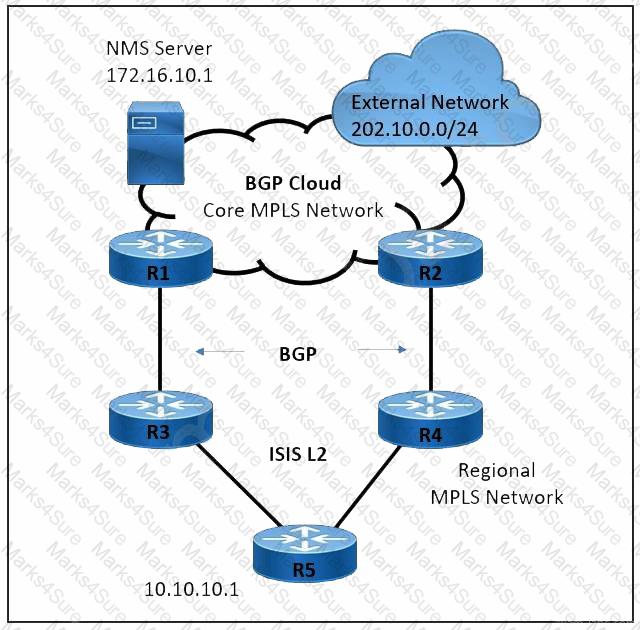
Refer to the exhibit. A large service provider is migrating device management from Layer 2 VLAN-based to Layer 3 IP-based solution. An engineer must configure the ISIS solution with these requirements:
Network management server IP 172.16.10.1 must be advertised from the core MPLS network to the regional domain.
The external network 202.10.0.0/24 must not establish ISIS peering with the R5 router.
The regional network must prevent sending unnecessary hello packets and flooding the routing tables of the R5 router.
Which two ISIS parameters must be implemented to meet these requirements? (Choose two.)
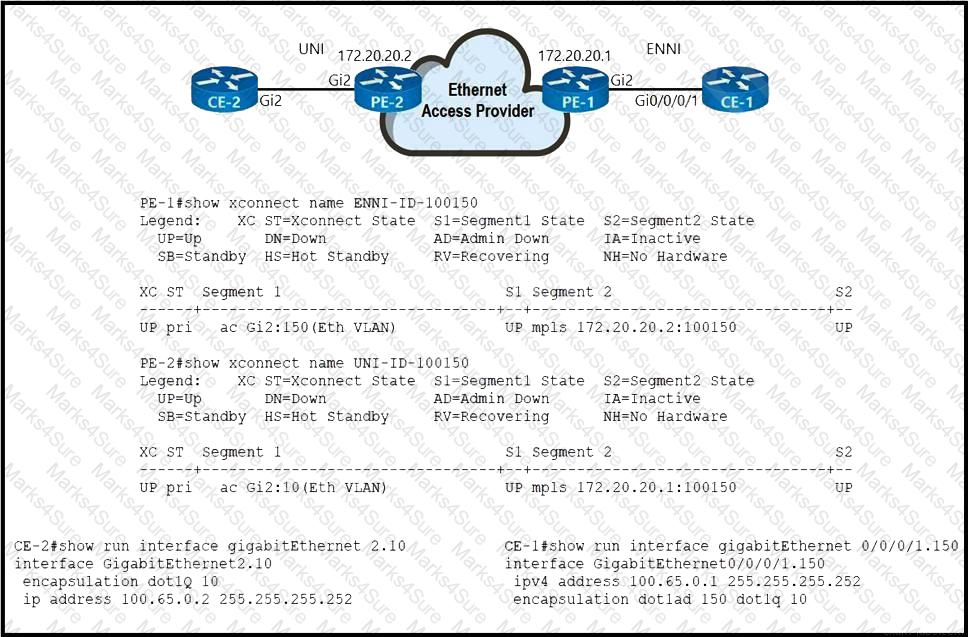
Refer to the exhibit. An Ethernet access provider is configuring routers PE-1 and PE-2 to provide E-Access EVPL service between UNI and ENNI. ENNI service multiplexing is based on 802.1ad tag 150, and service-multiplexed UNI is based on 802.1q tag 10. Which EFP configurations must the provider implement on PE-1 and PE-2 to establish end-to-end connectivity between CE-1 and CE-2?
Refer to the exhibit.
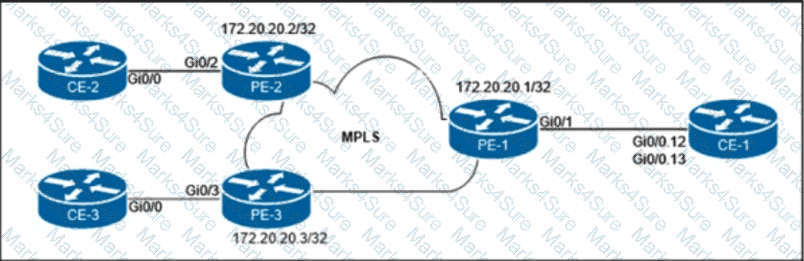
The customer that owns the CE-1, CE-2, and CE-3 routers purchased point-to-point E-Line services from the Carrier Ethernet provider. The service provider is delivering multiplexed UNI at the customer HQ location on PE-1 and untagged UNIs at the PE-2 and PE-3 locations. Additionally, the customer provided these VLAN to EVC mapping requirements:
• EVC 1 between CE-1 and CE-2 must be provisioned with C-VLAN 12 at the HQ location.
• EVC 2 between CE-1 and CE-3 must be provisioned with C-VLAN 13 at the HQ location.
Which configuration must the network engineer implement on the PE routers to provide end-to-end Carrier Ethernet service to the customer?
Which feature will an operator use while implementing MPLS TE on customer's network, to prevent an LSP from using any overseas inks?
Refer to the exhibit.
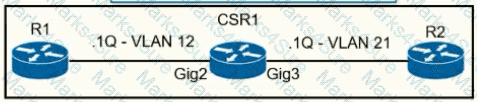
A network operator must configure CSR1 interlaces GigabitEihernet2 and GigabitEthemet to rewrite VLAN tags 12 and 21 for traffic between R1 and R2 respectively. Which configurator accomplishes this task?
A)

B)
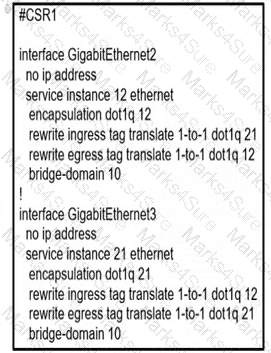
C)
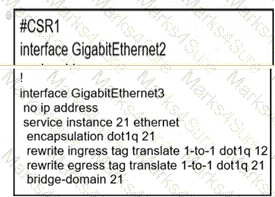
D)
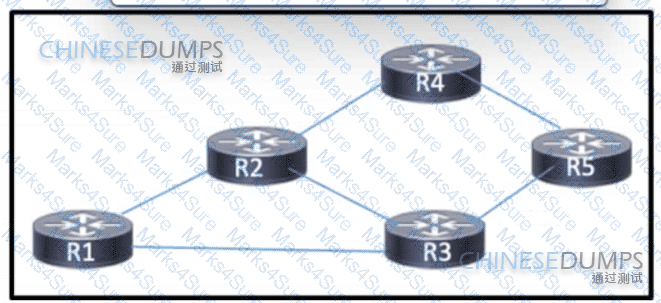
Refer to the exhibit. Routers R1 through R5 are being deployed within the core of a service provider running BGP The core supports distribution of VPNv4 routes using MPLS. R3 currently has multiple paths to reach R4. A network engineer must implement BGP attributes so that R3 can reach R4 via R1. Which action must the engineer take to meet the requirement?
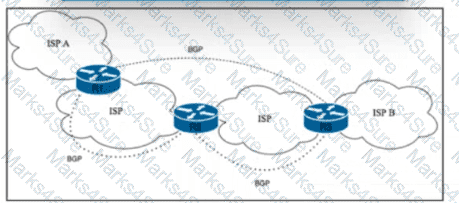
Refer to the exhibit. Tier 1 ISP A is connected to small Tier 3 ISP B. The EBGP routing protocol is used for route exchange. The networking team at ISP A noticed the flapping of BGP sessions with ISP B. The team decides to Improve stability on the network by suppressing the subnet for 30 minutes when a session begins to flap. Which action must the team perform to meet this goal?
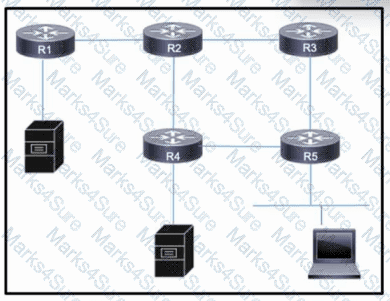
Refer to the exhibit. Users on a LAN connected to router R5 frequently open high-traffic connections with servers connected to R1 and R4. Users on R2 also require access to the servers, but performance is not a major concern and their traffic can be treated as secondary. As traffic on all links grows, the network architect wants to mitigate the potential for congestion on the link between R2 and R4.
Which action must the engineering team take to improve performance on the R2-R4 link for users on R5 while still allowing other traffic to flow?
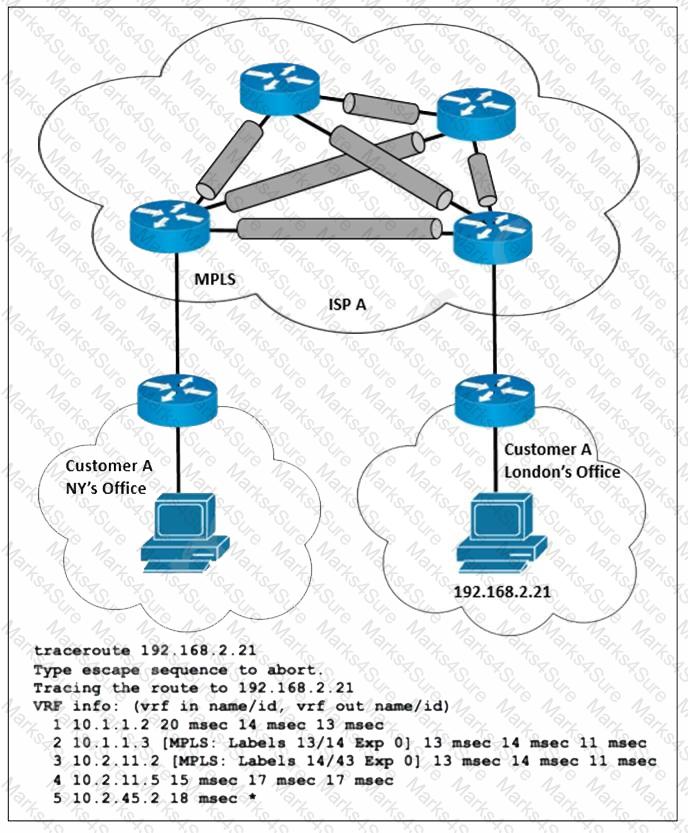
Refer to the exhibit. ISP A provides MPLS L3VPN service to customer A with BGP as the external routing protocol. Customer A has just opened a new branch office in London and requested the service provider to implement lossless service between its two offices. The LDP is enabled over the MPLS backbone and label exchange is working normally. Which action must the ISP engineering team take to enable the service?
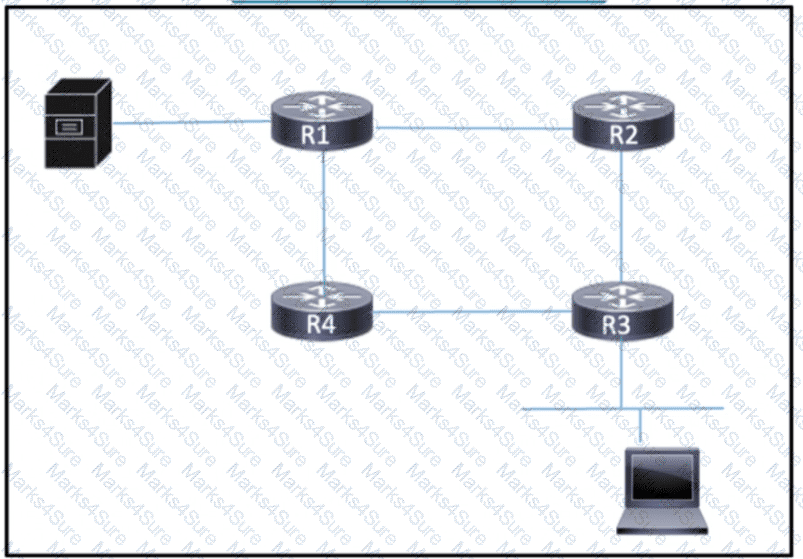
Refer to the exhibit. A host connected to R3 must connect with a server on R1 that provides critical, time-sensitive data. Traffic between the host and server must always be given bandwidth to traverse the links when they are congested, with other traffic being dropped. How must the network engineer implement a QoS strategy with classification to ensure that the traffic is given the appropriate bandwidth?
A network engineer is testing an automation platform that interacts with Cisco networking devices via NETCONF over SSH. In accordance with internal security requirements:
NETCONF sessions are permitted only from trusted sources in the 172.16.20.0/24 subnet.
CLI SSH access is permitted from any source.
Which configuration must the engineer apply on R1?
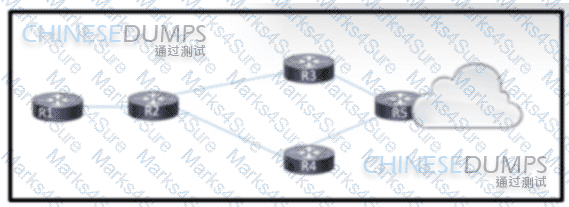
Refer to the exhibit. An engineer is scripting ACLs to handle traffic on the given network. The engineer must block users on the network between R1 and R2 from leaving the network through R5. but these users must still be able to access all resources within the administrative domain. How must the engineer implement the ACL configuration?
Under which circumstance does BGP ignore the best-path algorithm after receiving multiple routes to a destination?
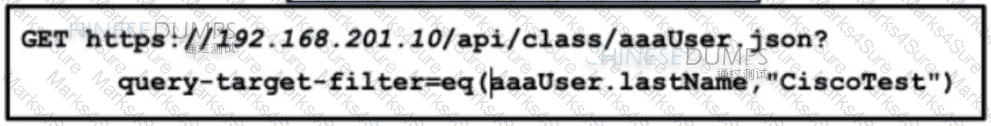
Refer to the exhibit. An engineer configured several network devices to run REST APIs. After testing, the organization plans to use REST APIs throughout the network to manage the network more efficiently. What is the effect if this script?
Refer to the exhibit:
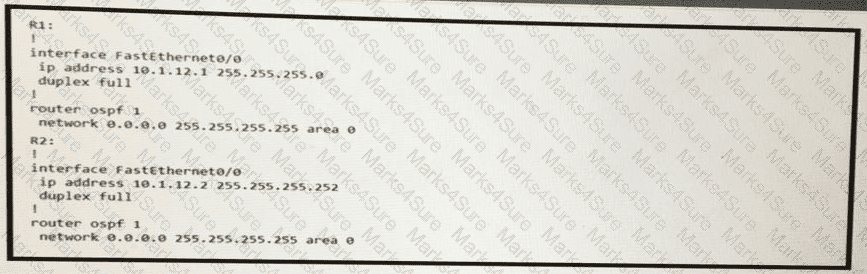
R1 and R2 are directly connected with Fast Ethernet interfaces and have the above configuration applied OSPF adjacency is not formed. When the debug ip ospf hello command is issued on R1. these log messages are seen.

Which command can be configured on routers R1 and R2 on fO/O interfaces to form OSPF adjacency?
Refer to the exhibit.

A network engineer must implement SNMPv3 on a Cisco IOS XR router running BGP. The engineer configures SNMPv3 to use SHA for authentication and AES for privacy on the routers, which are in a different data center in the same exchange as other routers. The engineer must also verify the associated MIB view family name, storage type, and status. Which set of actions meets these requirements?
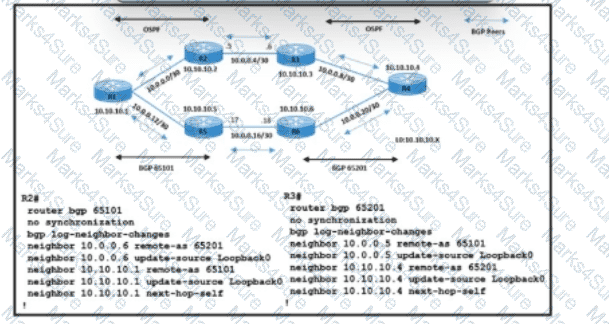
Refer to the exhibit. A network operations team is implementing eBGP on the service provider network. Data traffic between routers R1 and R4 must use the R2-R3 link, which connects AS 65101 and AS65201. iBGP sessions with adjacent routers are up on 10.10.10.1 and 10.10.10.4. The team is now updating the configuration for eBGP peers on routers R2 and R3. Which action must be taken to meet the requirements?
A network administrator must monitor network usage to provide optimal performance to the network end users when the network is under heavy load. The administrator asked the engineer to install a new server to receive SNMP traps at destination 192.168.1.2. Which configuration must the engineer apply so that all traps are sent to the new server?
After you analyze your network environment, you decide to implement a full separation model for Internet access and MPLS L3VPN services For which reason do you make this decision?
Refer to the exhibit:
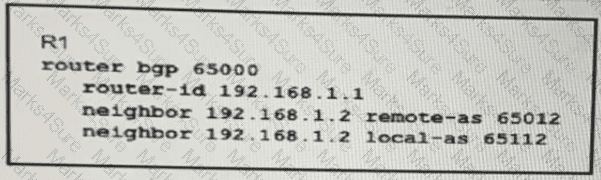
A network engineer is implementing a BGP protocol. Which effect of the local-as keyword in this configuration is true?
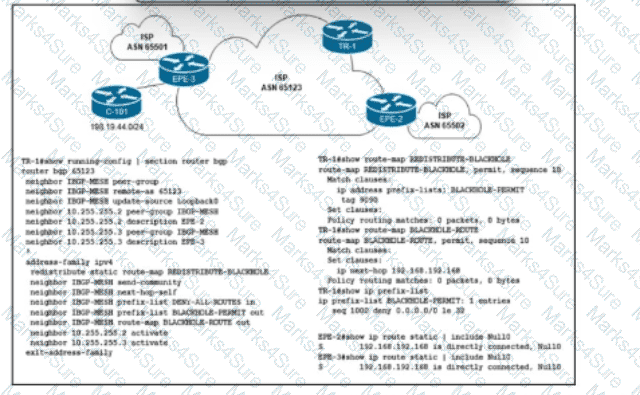
Refer to the exhibit. Customer C-101 in ASN 65123 requested that the ISP blackholes a host route 198.19.44.195, to which the customer is receiving a significant amount of malicious traffic. Which configuration must the network engineer implement on the trigger router TR-1 to fulfill the request without affecting other IP destinations in the customer's block?
Refer to the exhibit:
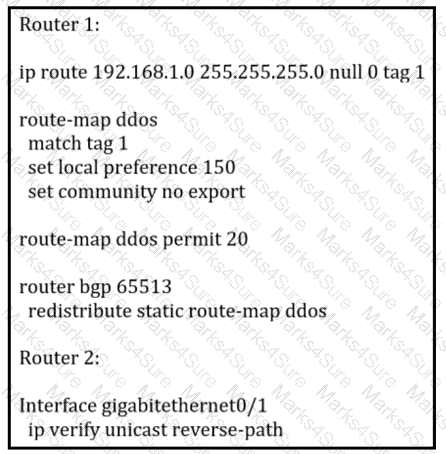
An engineer is preparing to implement data plane security configuration.
Which statement about this configuration is true?
Drag and drop the message types from the left onto the target field of the message originator on the right.
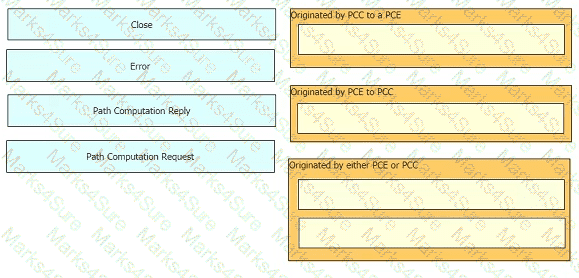
Refer to the exhibit.

An engineer at a new ISP must configure many Cisco devices in the data center. To make the process more efficient, the engineer decides to automate the task with a REST API. Which action does this JSON script automate?
An engineer must extend Layer 2 Between two campus sites connected through an MPLS backbone that encapsulates Layer 2 and Layer 3 data Which action must the engineer perform on the routers to accomplish this task?
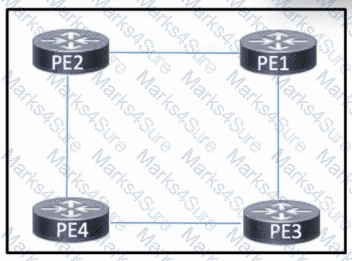
Refer to the exhibit. The four PE routers in the network are connected and running OSPF to share routes. MPLS is enabled on the four routers. The routers are connected and configured to use /30 networks. A network engineer must implement Layer 3 VPN support for traffic between customer sites.
Which task must the engineer perform?
Which configuration enables BGP FlowSpec client function and installation of policies on all local interfaces?
A)

B)

C)

D)

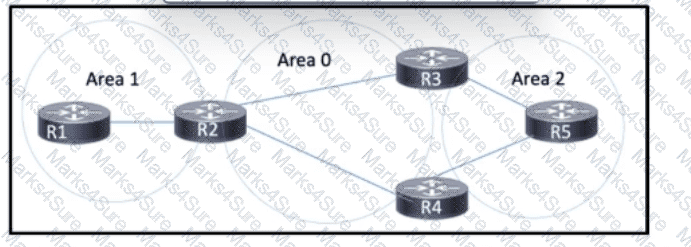
Refer to the exhibit. OSPF is running in the network, which is segmented into three areas. MPLS is enabled on all routers to support Layer 3 VPN. The network architect is concerned about potential packet loss when new OSPF adjacencies form. Which two tasks should the architect perform to implement MPLS LDP synchronization? (Choose two.)

Refer to the exhibit. A large enterprise streams training videos from a server connected to R4 to hosts connected to R5. PIM-SM is configured in the network using IGMPv2, with R2 serving as the RP. OSPF is configured in the network to support IGP routing, and the network uses BGP to access the internet through R3. The network engineering team must migrate the network to SSM.
Which action must the team take to begin the migration?
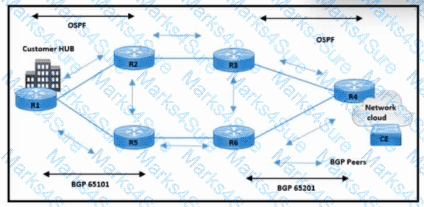
Refer to the exhibit. The NOC is configuring PE router R4 for BGP-originated traffic. R4 is connected to a CE device at a customer location. The customer requires:
BGP peers must establish a neighborship with NSR and NSF capability.
BGP must maintain state with the CE and provide continuous forwarding during ISSU and RP switchover events.
Which action meets the NSR requirement on PE routers?
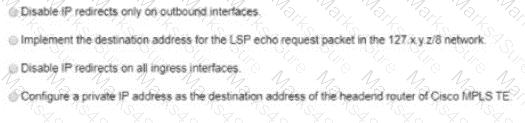
An engineer is implementing MPLS to monitor within the MPLS domain. Which must the engineer perform to prevent packets from being forwarded beyond the service provider domain when the LSP is down?
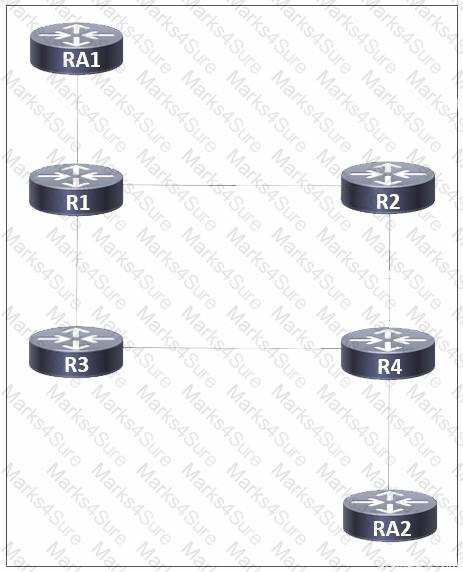
Refer to the exhibit. A network administrator implemented MPLS routing between routers R1, R2, R3, and R4. AToM is configured between R1 and R4 to allow Layer 2 traffic from hosts on RA1 and RA2. A targeted MPLS session is established between R1 and R4. Which additional action must the administrator take on all routers so that LDP synchronization occurs between connected LDP sessions?
You are writing an RPL script to accept routes only from certain autonomous systems Consider this code.

If you apply this code to BGP filters, which effect does the code have on your router?
Which additional configuration is required for NetFlow to provide traceback information?
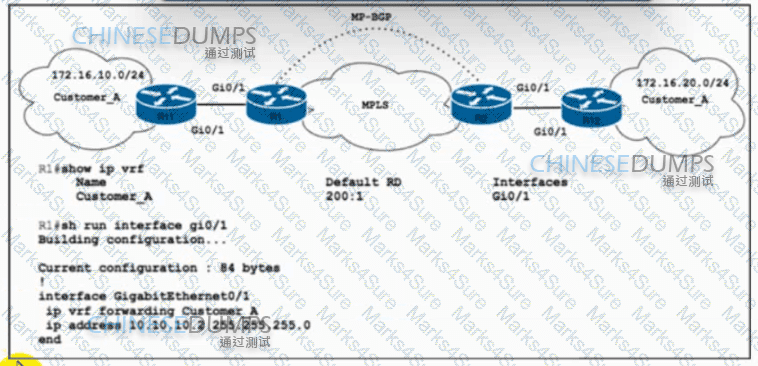
Refer to the exhibit. Customer_A asked ISP_A to connect two offices via an MPLS L3 VPN. Customer_A is currently using only the default route toward ISP_A. The engineer at ISP_A already configured the ip route vrf Customer_A 172.16.10.0 255.255.255.0 10.10.10.1 command on R1. Which action completes the configuration?
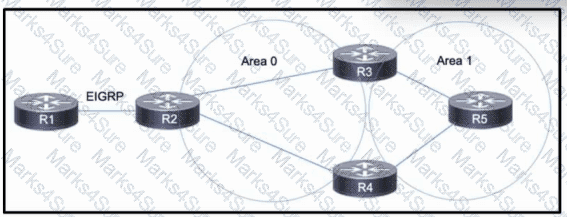
Refer to the exhibit. Company A is running OSPF within its network, comprised of routers R2, R3, R4, and R5 and consisting of two areas. Company A just acquired Company B, which uses EIGRP on its own R1. R1 has several routes in its routing table. The network engineering team at Company A needs access to the Company B network to manage network devices there, but each company will otherwise operate independently. R2 will serve as the ASBR between the two networks. Which action must the team take to reduce the number of EIGRP routes received on R2 and include only the necessary routes in the routing table?
Guidelines -
This is a lab item in which tasks will be performed on virtual devices.
• Refer to the Tasks tab to view the tasks for this lab item.
• Refer to the Topology tab to access the device console(s) and perform the tasks.
• Console access is available for all required devices by clicking the device icon or using the tab(s) above the console window.
• All necessary preconfigurations have been applied.
• Do not change the enable password or hostname for any device.
• Save your configurations to NVRAM before moving to the next item.
• Click Next at the bottom of the screen to submit this lab and move to the next question.
• When Next is clicked, the lab closes and cannot be reopened.
Topology:
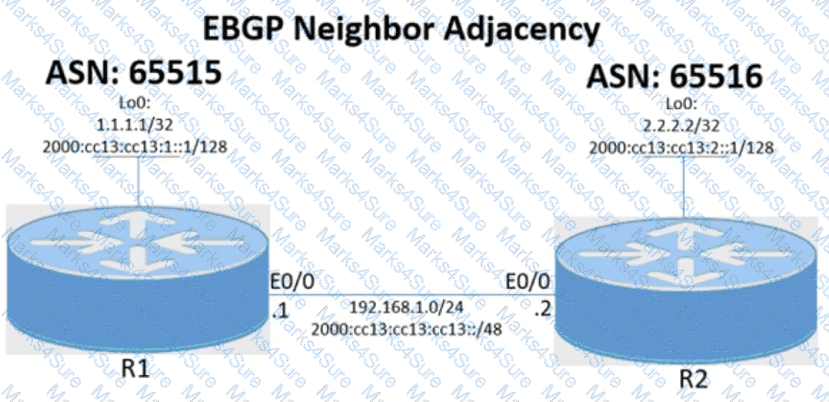
Tasks -
Configure the BGP routing protocol for R1 and R2 according to the topology to achieve these goals:
1. Configure EBGP neighbor adjacency for the IPv4 and IPv6 address family between R1 and R2 using Loopback0 IPv4 and IPv6 addresses. All BGP updates must come from the Loopback0 interface as the source. Do not use IGP routing protocols to complete this task.
2. Configure MD5 Authentication for the EBGP adjacency between R1 and R2. The password is clear text C1sc0!.
Refer to the exhibit.

Which type of DDoS attack will be mitigated by this configuration?

Refer to the exhibit. MPLS is running in the network with OSPF as the IGP. Full routes are shared between the routers, and each connected link has an MPLS neighbor relationship. A network engineer must update the network configuration so that it will maintain LDP neighbor relationships if a directly connected link goes down. Which action must the engineer take as part of the process?
Which capability does the MPLS TE FRR facility backup protection method provide?
Refer to the exhibit.

A network operator working for a telecommunication company with an employee ID: 4350:47:853 must implement an IGP solution based on these requirements:
• Subnet 10.50.10.0 traffic must exit through the R1 router to connect with the Syslog server.
• Subnet 10.50.20.0 traffic must exit through the R2 router to connect with the NTP server.
• In case of link failure between R2 and R4, traffic must be routed via R1 and R3.
Which two configurations must be implemented on R5 to meet these requirements? (Choose two.)
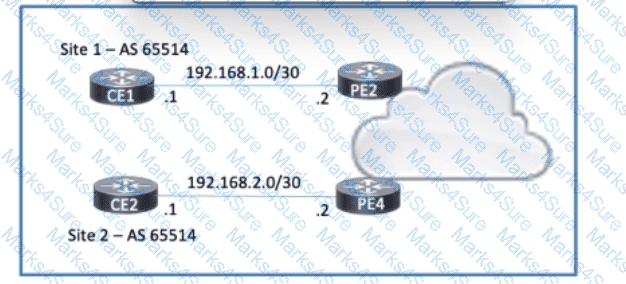
Refer to the exhibit. Company A has two offices that communicate via a service provider in AS 65516. CE1 and CE2 provide connections to the service provider from site 1 and site 2 respectively. Both customer sites use BGP as the PE-CE routing protocol. Which configuration must the engineer apply to ensure that traffic passes between the two sites?
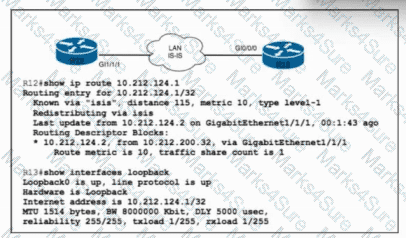
Refer to the exhibit. Router R13 is operating in Level 1 / Level 2 mode. A network engineer with an employee ID: 5209:82:636 must change the IS-IS cost of the route IP address 10.212.124.1 to 90. The metric update must be carried over in TLV 128. Which configuration must be implemented to complete the task?
Which is the benefit of implementing model-driven telemetry in a service provider environment?
A network architect plans to implement MPLS OAM to provide additional troubleshooting functionality for the NOC team. After analyzing the configuration on the MPLS P/PE nodes, the architect decides to revise the CoPP policies. Which two actions ensure that the new solution is secure? (Choose two.)
Refer to the exhibit.
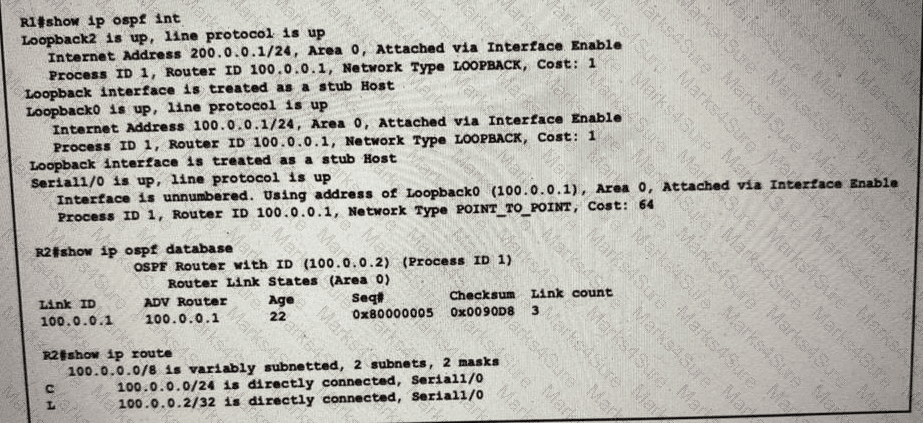
While troubleshooting a connectivity issue on router R2, a network engineer with an employee id:3876.13.497 notices that although it detects three OSPF links from R1, the OSPF prefixes are missing from the routing table. What is the reason for the problem?
You are configuring MPLS traffic-engineering tunnels in the core.
Which two ways exist for the tunnel path across the core? (Choose two )
Refer to the exhibit.
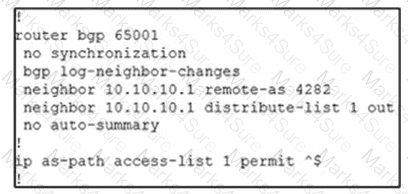
An engineer is reviewing the BGP configuration. Which routes must be advertised to 10.10.10.1
Refer to the exhibit:
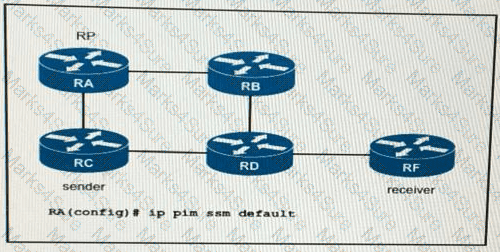
If router RA is configured as shown, which IPv4 multicast address space does it use?
An ISP Is Implementing end-to-end fault monitoring for a customer based on the IEEE 802.3ah standard. The solution must detect when 15 or more corrupted Ethernet packets arrive within 10 ms and stop propagating traffic through the ISP backbone network or to the customer side. Which configuration must the ISP engineer apply?
Company A is implementing VoIP services across the company. The network architect designed a QoS policy to allow only specific IP subnets and mark the signaling flow with DSCP 36. The solution should be as secure as possible. Phones receive their IP addresses from the 172.184.12.0/24 pool and are assigned by the RADIUS server to VLAN 1021. Skinny Client Control Protocol is used as a signaling protocol in the network. For security reasons, switchport port-security maximum 1 vlan voice has been preconfigured on the switch side. Which two tasks must an engineer perform on SW_1 to achieve this goal? (Choose two.)
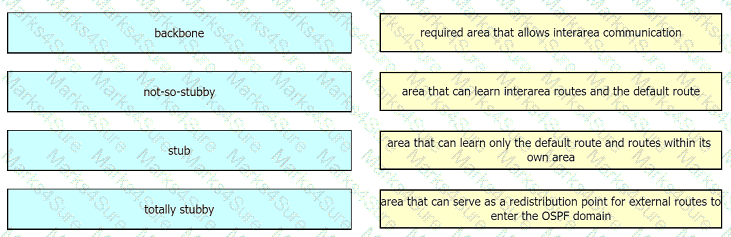
Drag and drop the OSPF area types from the left onto the correct statements on the right
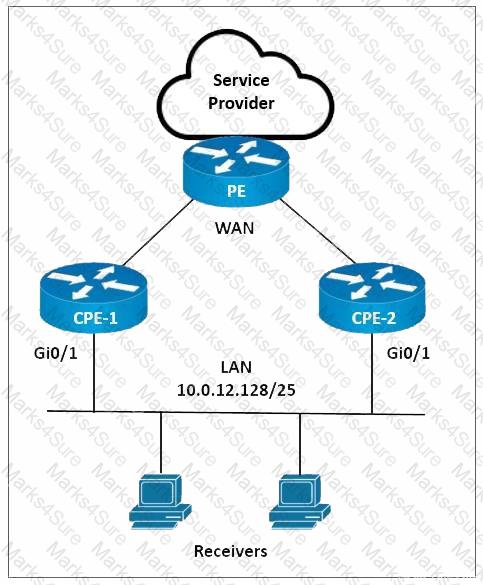
Refer to the exhibit. A network engineer is implementing multicast services on CPE-1 and CPE-2. CPE-1 must be configured as the preferred IGMP querier for the LAN segment. PIM-SM must be implemented on the LAN interfaces with an IGMP version that supports (*, G) joins only. Which configurations must the engineer implement on CPE-1 and CPE-2?
What must a network engineer consider when designing a Cisco MPLS TE solution with OSPF?
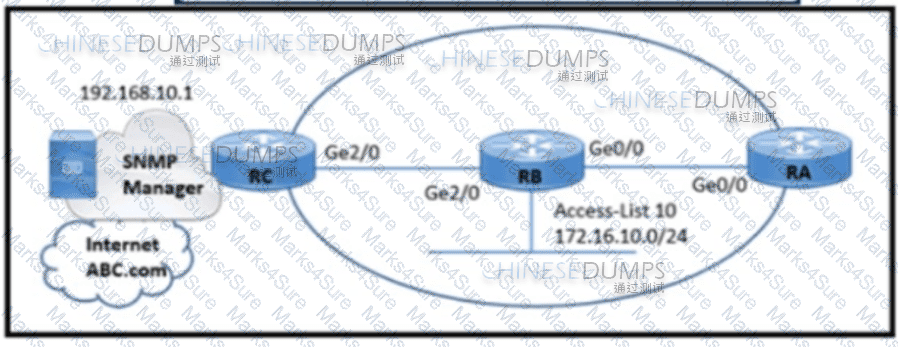
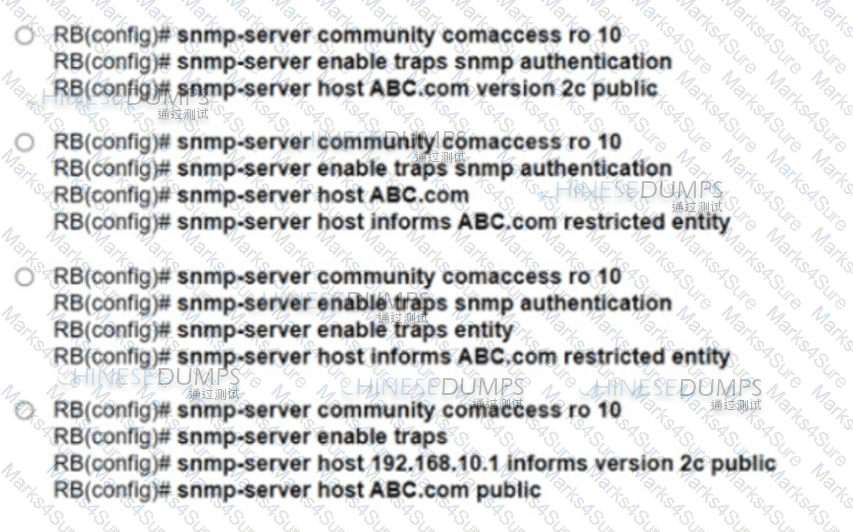
Refer to the exhibit. A network engineer is configuring an SNMP community on router RB with these requirements:
Allow read-only access for all objects to members of Access-List 10 that use the comaccess community string.
Other SNMP managers must not have access to objects.
SNMP authentication failure traps must be sent to SNMPv2c and then to the host using SNMPv2c with the public community string.
Which configuration meets these requirements?
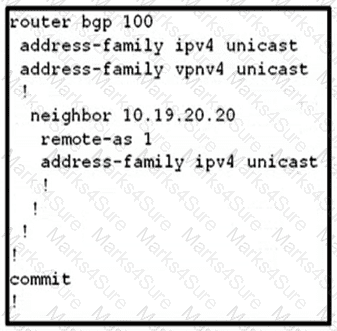
Refer to the exhibit:

This configuration is being applied on an IOS XR router.
Which statement about this configuration is true?

Refer to the exhibit. An engineer must Implement a traceroute operation to verity the R1 point-to-multipoint LSP connections. The traceroute operation must return all labels and hop-by-hop IP addresses for destinations 10.20.0.1. 10.30.0.1, and 10.40.0.1. and the maximum number of hops is 4. Which command must be executed to meet the requirements?
Refer to the exhibit.
An engineer is trying to implement BGP configuration on a router Which configuration error prevents the ASBR from establishing a BGP neighborship to a directly connected BGP speaker?
A mid-size service provider uses L2VPN as its standard for connectivity between offices. A small company wants the service provider to connect the company's two sites across the service provider core. To meet service requirements, the service provider must extend the Layer 2 domain between the company's two locations.
Which configuration must the engineer apply to implement an attachment circuit between the two sites using a VLAN tag of 12?
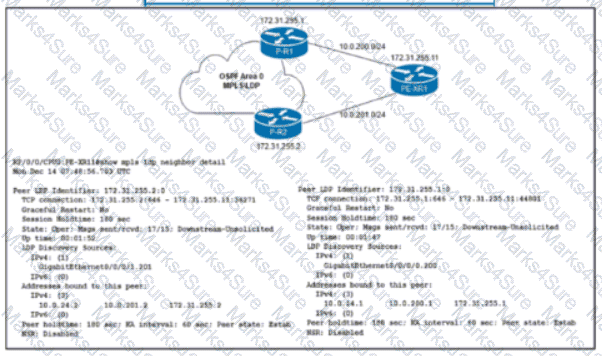
Refer to the exhibit. The network team must implement MPLS LDP session protection with two requirements:
Session protection is provided for core loopback IP addresses only.
The LDP session must remain operational for one hour when the WAN link on PE-XR1 fails.
Which configuration must the team implement on PE-XR1?
An engineer working for a private telecommunication company with an employe id:3948:613 needs to limit the malicious traffic on their network. Which configuration must the engineer use to implement URPF loose mode on the GigabitEthernet0/1 interface?
A)

B)

C)

D)

After troubleshooting multiple outages on the network due to repeated configuration errors, the network architect asked an engineer to enable NETCONF to facilitate future configurations. The configuration must enable syslog messaging to record NETCONF notifications from each of the numerous devices on the network. Which configuration must the engineer apply?
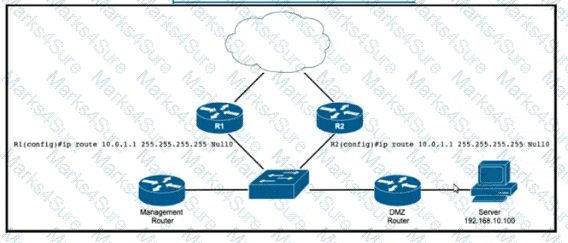

Refer to the exhibit. EIGRP a running across the core lo exchange Internal routes, and each router maintains 6GP adjacency with the other routers on the network. An operator has configured static routes on the edge routers R1 and R2 for IP address 10.0.1.1. which is used as a black hole route as shown. Which configuration should the operator Implement to me management rouler to create a route map that will redistribute lagged static routes into BGP and create a static route to blackhole traffic with tag 777 that Is destined to server at 192.168.10.100?

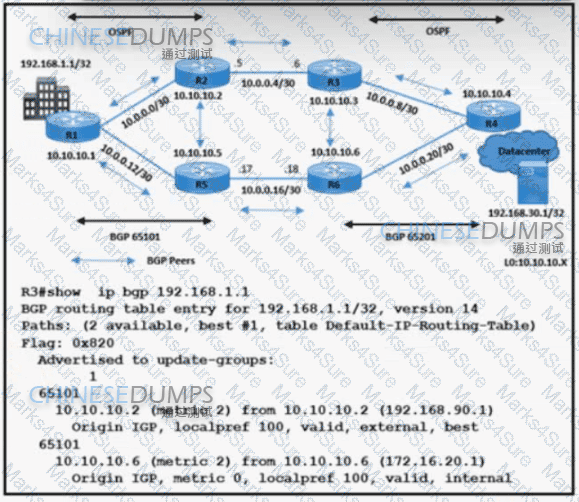
Refer to the exhibit. A network engineer is implementing BGP in AS 65101 and AS 65201. R3 sends data traffic to 192.168.1.1 /32 via the path R3-R2-R1. The traffic must travel via alternate path R6-R5 for prefix 192.168.1.1/32. Which action must be taken to meet the requirement?
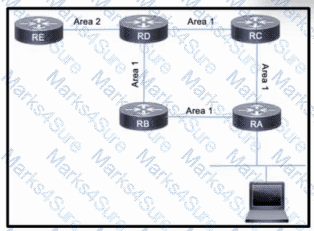
Refer to the exhibit. The company is running IS-IS in its core. A network engineer must segment the network into two areas to isolate departments. However, some networks must be shared from area 2 to area 1, so the engineer has decided to implement route filtering between devices.
Which action must the engineer take so that the correct networks are shared between IS-IS areas?
A customer site is being connected to a Frame Relay network via a T1 link. The customer has a contract for 512 kbps service with a Tc value of 125 ms. Under peak line conditions, customer traffic can reach four times the contracted speed. Which QoS configuration must the service provider implement to limit the customer to the contracted values?

Refer to the exhibit.
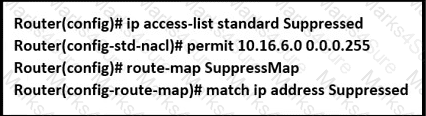
An engineer is implementing BGP selective prefix suppression. The router must advertise only 10.16.4.0/24,10.16.5.0/24. and summarized route 10.16.0.0/21. and suppress 10.16.6.0/24. Which configuration must the engineer apply to the router?
A)
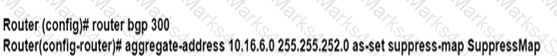
B)

C)
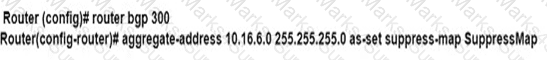
D)

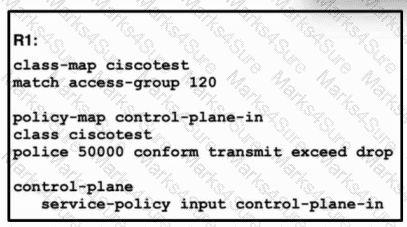
Refer to the exhibit. A network engineer installed router R1 as the new core router and must secure the control plane. The configuration has been applied, and now the engineer is creating ACL 120. Only hosts 192.168.1.1 and 192.168.2.2 should be allowed to access the router using Telnet. All other hosts should be rate-limited, with excess traffic dropped. Which configuration accomplishes this goal?
An engineer is setting up overlapping VPNs to allow VRF ABC and XYZ to communicate with VRF CENTRAL but wants to make sure that VRF ABC and XYZ cannot communicate. Which configuration accomplishes these objectives?




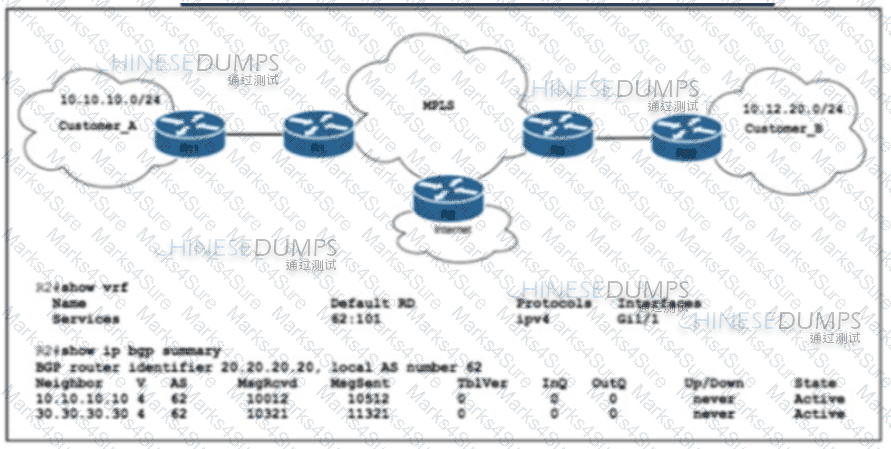
Refer to the exhibit. ISP_A is about to launch a new internet service. ISP_A is already providing MPLS VPN Layer 3 services to Customer_A and Customer_B, which are connected to ISP_A via OSPF. A network engineer completed the BGP and VRF configurations on R2 to support the new internet service. Which additional action completed the launch?
Refer to the exhibit:
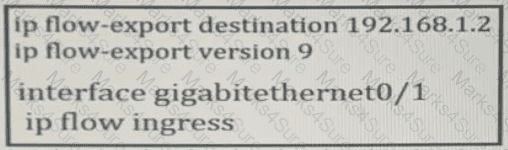
Which information is provided for traceback analysis when this configuration is applied?
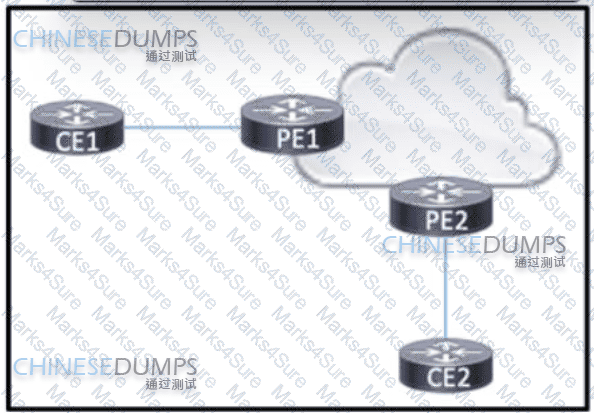
Refer to the exhibit BGP is running in the core of the service provider to exchange routes for its customers, and OSPF serves as the PE-CE routing protocol. The service provider s existing customer at CE1 is opening a new office in a different geographical location connected via CE2. A network engineer must update the BGP implementation so that PE1 and PE2 will share routes and provide communication between CE1 and CE2 Which action must the engineer take?
The network team is planning to implement IPv6 on the company’s existing IPv4 network infrastructure. The network currently uses IS-IS to share routes between peers. Which task must the team perform so that IS-IS will run in multitopology mode on the updated IPv6 network?
After implement MPLS protocol for multiple VRFs on a single Cisco device, the engineer notices all VRFs on the router still do to not LDP session protection feature enabled. Which configuration must the engineer apply to enable the LDP session protection feature FOR LDP neighbors within each VRF?
Refer to the exhibit.

An engineer is configuring multitiopology IS-IS for IPv6 on router R1. Which additional configuration must be applied to complete the task?
A)

B)

C)

D)

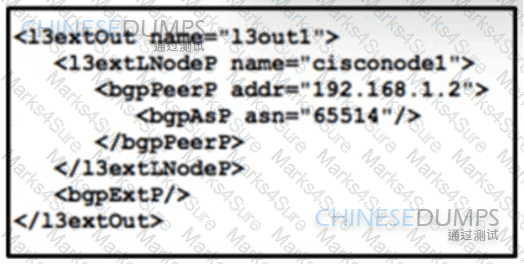
Refer to the exhibit. A global company plans to implement BGP at its newest location to provide connectivity to other offices. The global infrastructure of the company is a multivendor environment. An engineer must review the BGP core configurations at headquarters to determine if they can be repurposed at the new location. The engineer copied this JSON script for review. What is the effect of the script?

Refer to the exhibit. A network engineer with an employee ID 4379:43:595 is setting up an IS-IS network with these requirements:
Routes with a tag of 80 and IP prefixes other than 192.168.10.20/24 must be redistributed from Level 1 into Level 2.
Route leaking must be configured from Level 2 into the Level 1 domain for routes that are tagged with only 50 or 40.
Which configuration must be implemented on RB to meet the requirements?

Refer to the exhibit. A large organization is merging the network assets of a recently acquired competitor with one of its own satellite offices in the same geographic area. The newly acquired network is running different routing protocol than the company's primary network. As part of the merger a network engineer implemented this route map Which task must the engineer perform to complete the Implementation?
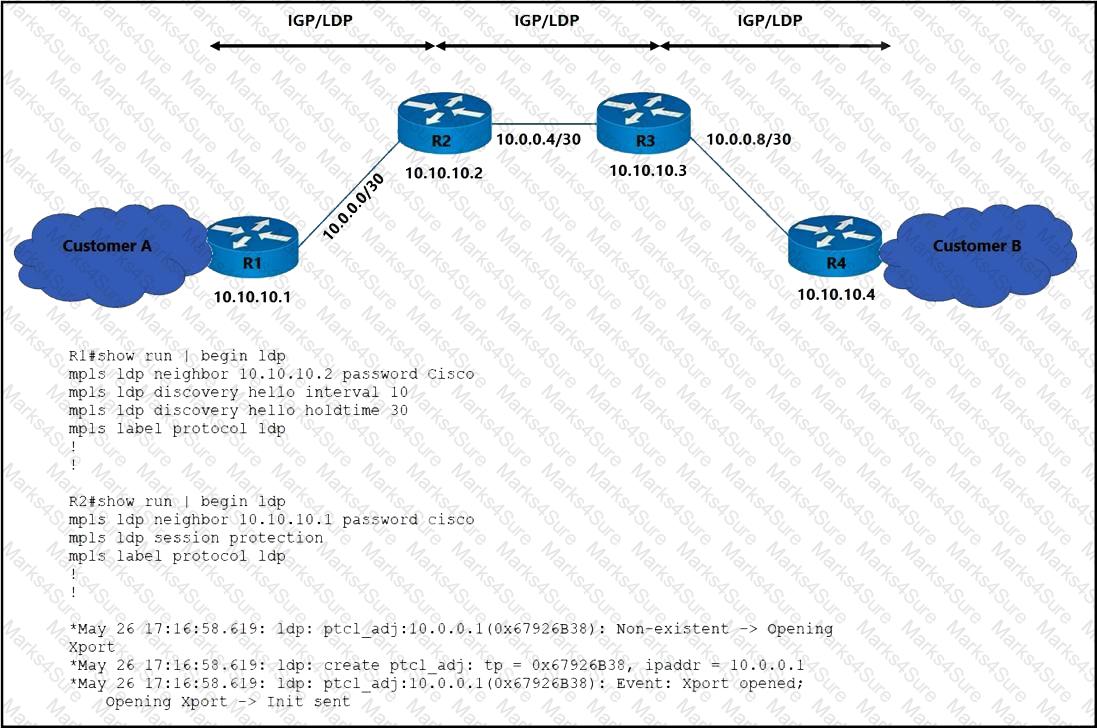
Refer to the exhibit. The operations team is implementing an LDP-based configuration in the service provider core network with these requirements:
R1 must establish LDP peering with the loopback IP address as its Router-ID.
Session protection must be enabled on R2.
How must the team update the network configuration to successfully enable LDP peering between R1 and R2?
An engineer implemented LDP protocol on the ISP network. The engineer must ensure that there are no packet loss issues when IGP and LDP protocols are not synchronized. Which configuring must the engineer implement so that the IGP routing protocol will wait until LDP convergence is completed?
Refer to the exhibit.
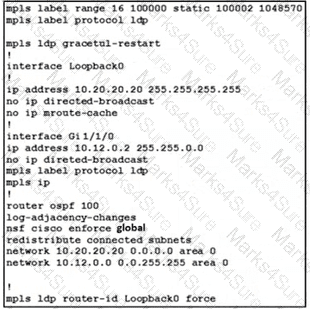
A network administrator implemented MPLS LDP changes on PE-A LSR device. The engineer must ensure there are no LDP peer are fully operational. Which LDP feature must the engineer apply to the existing configuration to eliminate the problem?
Drag and drop the LDP features from the left onto the correct usages on the right.

Refer to the exhibit.
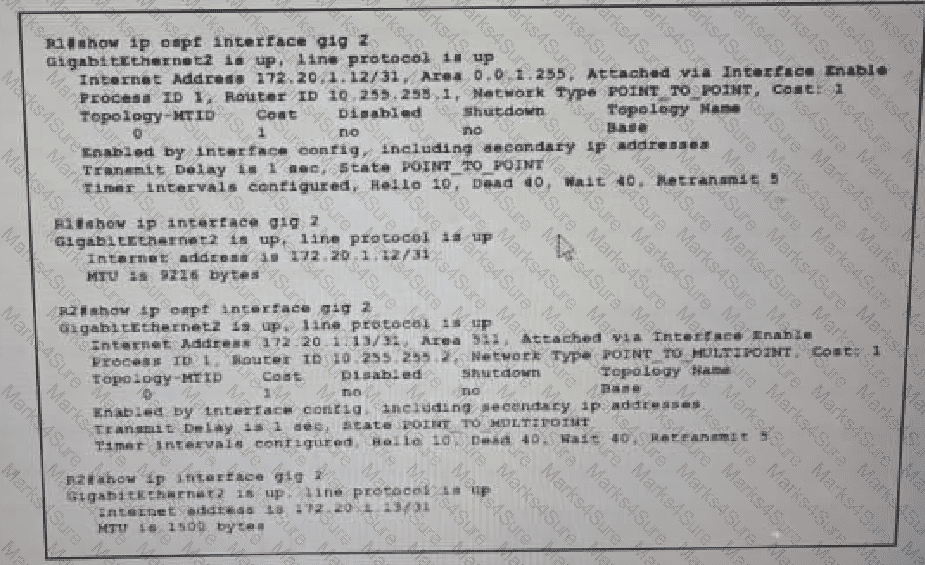
While troubleshooting the OSPF adjacency between routers R1 and R2 an engineer noticed that both routers are stuck in the EXCHANGE/EXSTART state. What should the engineer fix to solve the ongoing issue?
Refer the exhibit.

Users on a network connected to router R3 report slow speeds when they connect to the server connected to R2. After analyzing traffic on the network, a network engineer identified congestion on the link between R2 and R3 as the cause. Which QoS service must the engineer implement to drop traffic on the link when it exceeds a configured threshold?
Refer to the exhibit: 
BGPsec is implemented on R1. R2. R3. and R4 BGP peering is established between neighboring autonomous systems Which statement about implementation is true?
Refer to the exhibit.

Which show command shows statistics for the control plane policy and is used to troubleshoot?
A network operator working for a private outsourcing company with an employee id: 4261:72:778 needs to limit the malicious traffic on their network. Which configuration must the engineer use to implement URPF loose mode on the GigabitEthernet0/1 interface?
What happens when a segment-routing TE tunnel loses the link and there is no secondary path in place?
A network engineer is configuring RIP as the routing protocol between multiple PEs and CEs. The engineer must avoid advertising the same routes back to their sources. Which action should be performed on the routers to accomplish this task?

Refer to the exhibit. A growing company wants to ensure high availability and redundancy for its critical web servers, which are located in an offsite data center. The network architect decided to implement BGP so that the network can use redundant paths for outbound traffic toward the destination subnet 10.2.2.0/24. A network engineer already configured basic BGP settings on edge router R1, which is a Cisco ASR-1001X router. The engineer also confirmed loopback reachability to routers R2 and R3, and the AS path length toward the destination is the same via R2 and R3. Which action must the engineer take on R1 to complete the implementation?
How does TACACS+ facilitate secure connections for user access to network routers?
Refer to the exhibits:
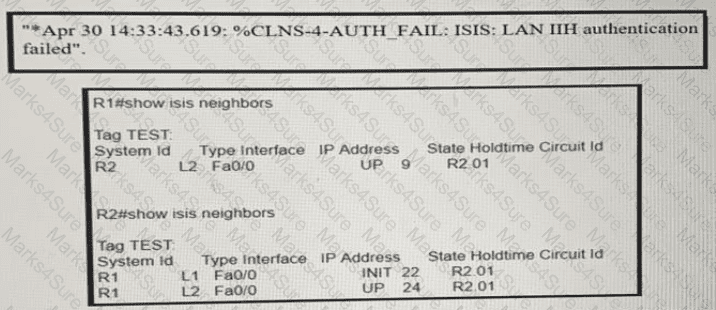
R1 and R2 are directly connected and IS-IS routing has been enabled between R1 and R2 R1 message periodically Based on this output, which statement is true?
Exhibit:
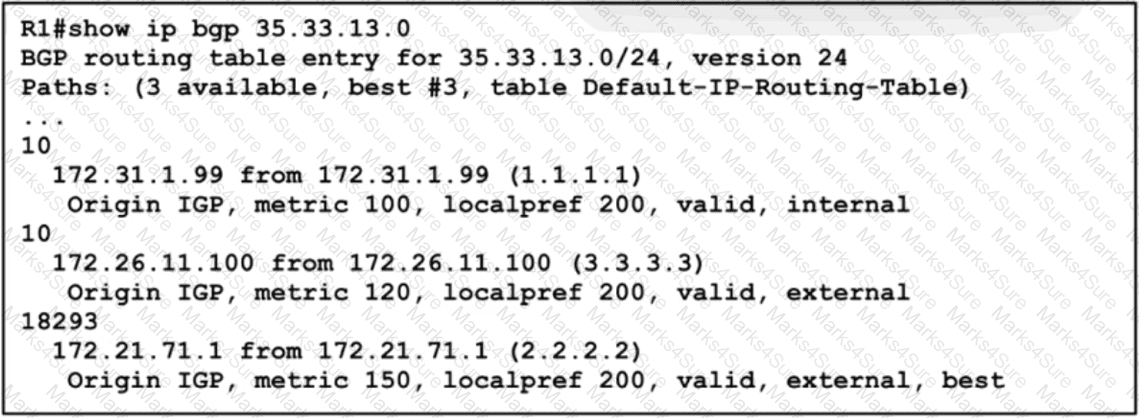
A network engineer must update the routing toward the web server with IP address 35.22.13.1. The primary path must be configured via the neighbor router with ID 1.1.1.1. However, local-preference configuration is not permitted on R1. Which task must the engineer perform on R1 to complete the implementation?
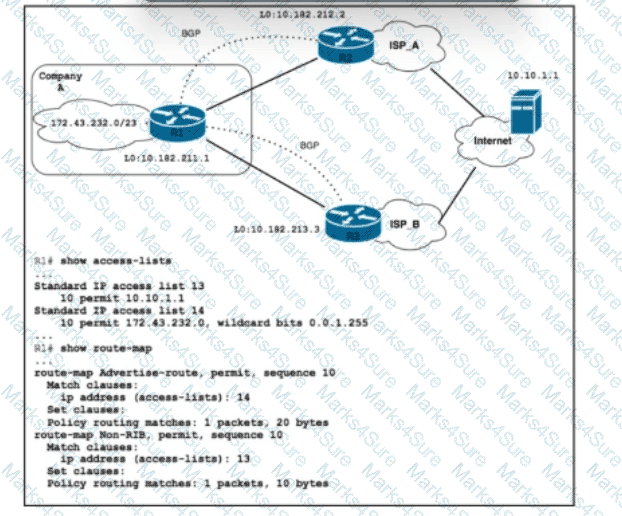
Refer to the exhibit. Company A is connected to multiple upstream ISPs, with ISP_A serving as the primary upstream ISP. The company A subnet 172.43.232.0 should be announced to the secondary ISP_B only when the FTP server with IP address 10.10.1.1 is not accessible via the primary ISP. Which configuration must be applied on R1?
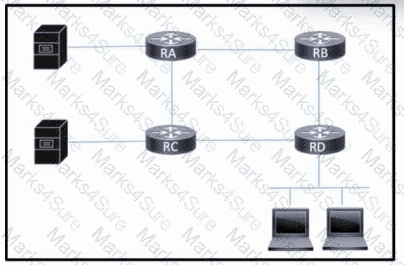
Refer to the exhibit. Users on a LAN that is connected to RD communicate to multiple servers on the corporate network. Initially, the servers were located on the same LAN. However, after congestion was reported, the engineering team decided to relocate the servers to two different networks.
Which task should the team perform to improve performance on the overall network while still allowing traffic to flow between the different hosts?
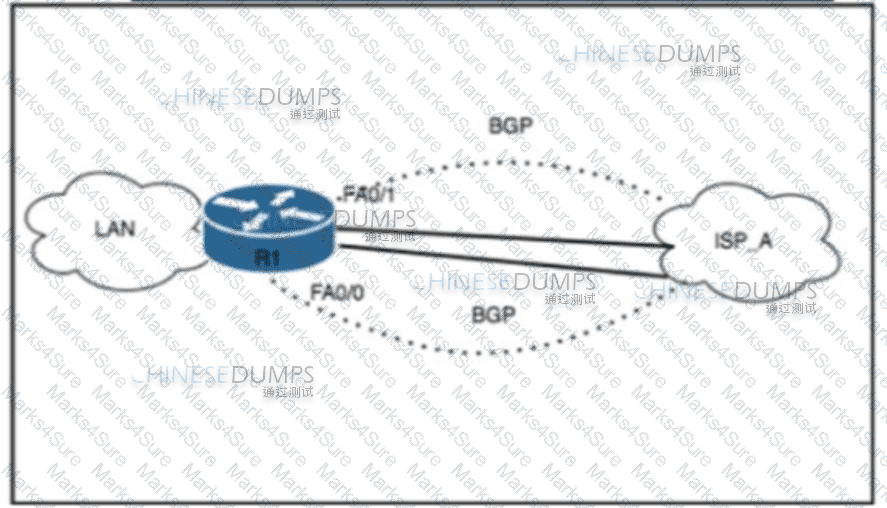
Refer to the exhibit. A network engineer must deny access from spoofed addresses to the LAN. The edge router currently has two active BGP sessions established with Tier 1 ISP_A. Due to asymmetric routing, no ACL is configured on either interface. Which two configurations must the engineer perform on the edge router to complete the task? (Choose two.)
Refer to the exhibit.
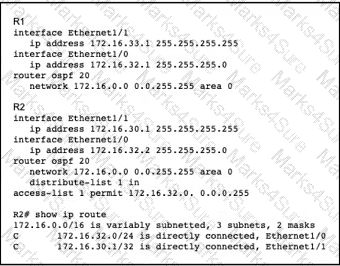
A network engineer notices that router R2 is failing to install network 172.16.33.1/32 in the routing table. Which configuration must the engineer apply to R2 to fix the problem?
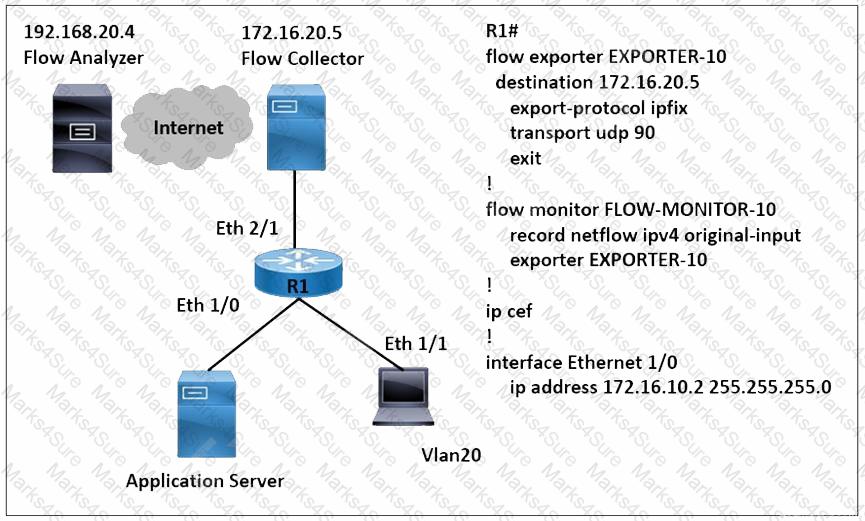
Refer to the exhibit. A network engineer wants to monitor traffic from the application server and send the output to the external monitoring device at 172.16.20.5. Application server traffic should pass through the R1 Eth2/1 interface for further analysis after it is monitored. Which configuration must be applied on the R1 router?
Egress PE NAT is being used via a single centralized router to provide Internet access to L3VPN customers.
Which description of the NAT operation is true?
Refer to the exhibit. R1 has two upstream Tier 1 service providers. BGP is in use as the exterior routing protocol, and ISP_A and ISP_B are sending the full BGP table. A network engineer must assign local-preference 70 to all routes with multiple exit discriminator 30. Which configuration must the network engineer apply?

When configuring traffic engineering tunnels in Cisco MPLS core network, you see the traffic is not taking the expected path in the core.
Which command do you use to quickly check path of a TE tunnel?
Drag and drop the functionalities from the left onto the correct target fields on the right.
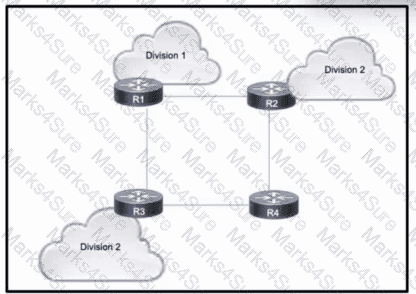
Refer to the exhibit. A large enterprise is migrating its network to use MPLS VPNs between different business divisions. Within the core, routes are shared between the routers using OSPF, and each connected link maintains an MPLS neighbor relationship.
Which action must the migration team take so that LDP neighbor relationships are maintained if a directly-connected link goes down?
An engineer is moving all of an organization’s Cisco IOS XE BGP routers to the address-family identifier format. Which command should be used to perform this upgrade quickly with the minimum service disruption?
Refer to the exhibit.
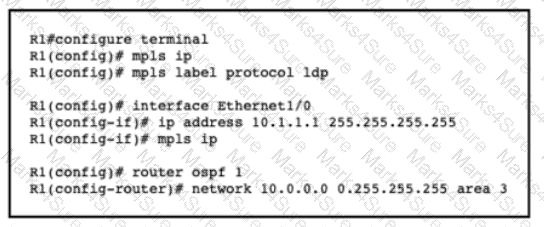
A network engineer is configuring MPLS LDP synchronization on router R1. Which additional configuration must an engineer apply to R1 so that it will synchronize to OSPF process 1?
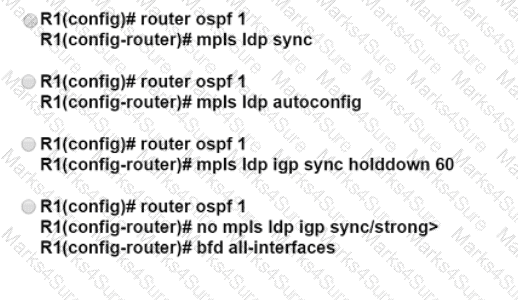


Refer to the exhbit. ISP A has a BGP peering with ISP C with the maximum-prefix 150 configuration on R1. After a recent security breach on the ISP A network, a network engineer has been asked to enable a lightweight security mechanism to protect the R1 CPU and BGP membership from spoofing attacks. Which solution must ISP A implement?

Guidelines
-
This is a lab item in which tasks will be performed on virtual devices.
• Refer to the Tasks tab to view the tasks for this lab item.
• Refer to the Topology tab to access the device console(s) and perform the tasks.
• Console access is available for all required devices by clicking the device icon or using the tab(s) above the console window.
• All necessary preconfigurations have been applied.
• Do not change the enable password or hostname for any device.
• Save your configurations to NVRAM before moving to the next item.
• Click Next at the bottom of the screen to submit this lab and move to the next question.
• When Next is clicked, the lab closes and cannot be reopened.
Topology
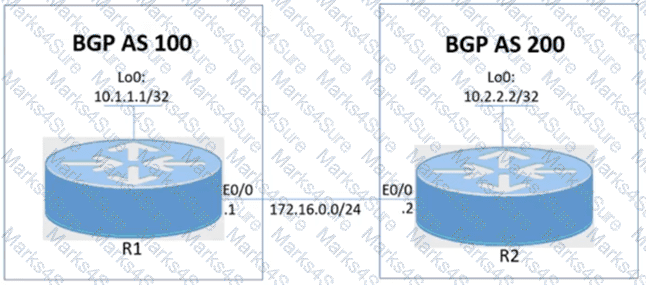
Tasks
-
R1 and R2 are having issues forming an eBGP neighbor relationship. Troubleshoot and resolve the issue to achieve these goals:
1. Configure R1 and R2 to form a BGP neighborship using their Loopback interfaces.
2. Form the neighbor relationship using a BGP multihop mechanism. Use minimal values to solve the issue.