Refer to the exhibit.
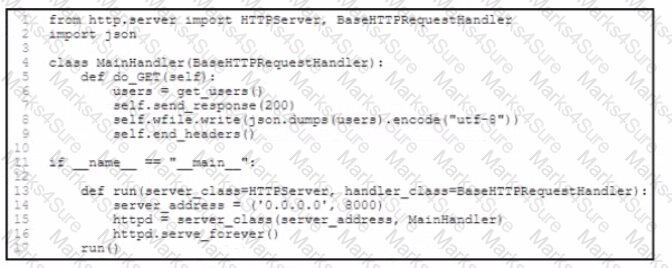
Refer to the exhibit An application hosting server with the local data center is experiencing large amounts of traffic from enclusers. A developer must optimize this API server to reduce the toad on its host. What are two ways to optimize this code through HTTP cache controls? (Choose two.)
Include the "ETag" header in the API response.
A developer needs to build a new Docker image and has created a tag by using the command:
$ docker tag 32df423320458 local/app.1.2
Which command must be executed next to build the Docker image using the tag?
A)
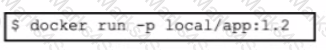
B)

C)

D)

Refer to the exhibit.
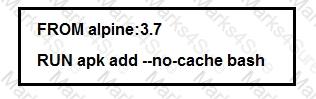
Which additional line results in the output of Test 1 upon execution of the docker run --rm devnet 1 command in a Dockerfile with this content?
Refer to the exhibit.
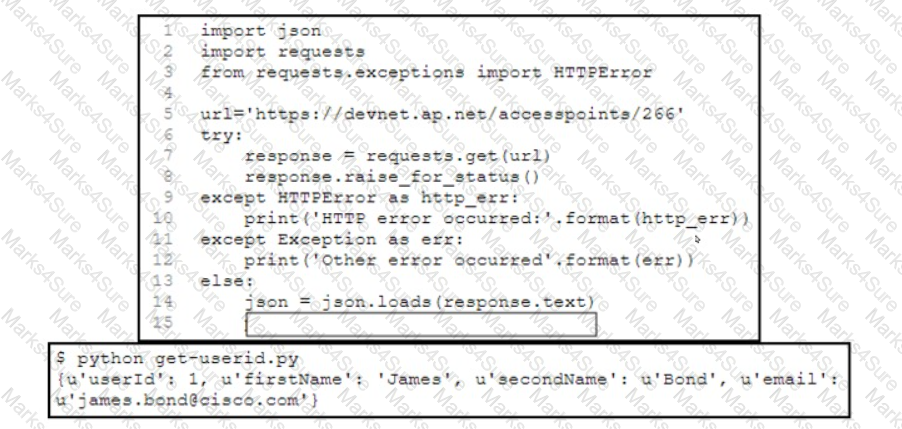
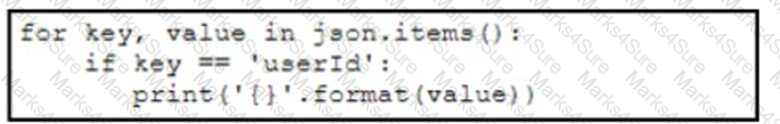
A developer has created a Python script that retrieves information about the deployment of Cisco wireless access points using REST API. Which two code snippets must be added to the blank in the code to print the value of the userid key instead of printing the full JSON response? (Choose two.)
A)

B)

C)

D)
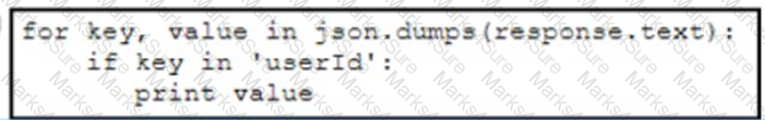
E)
Click on the GET Resource button above to view resources that will help with this question.
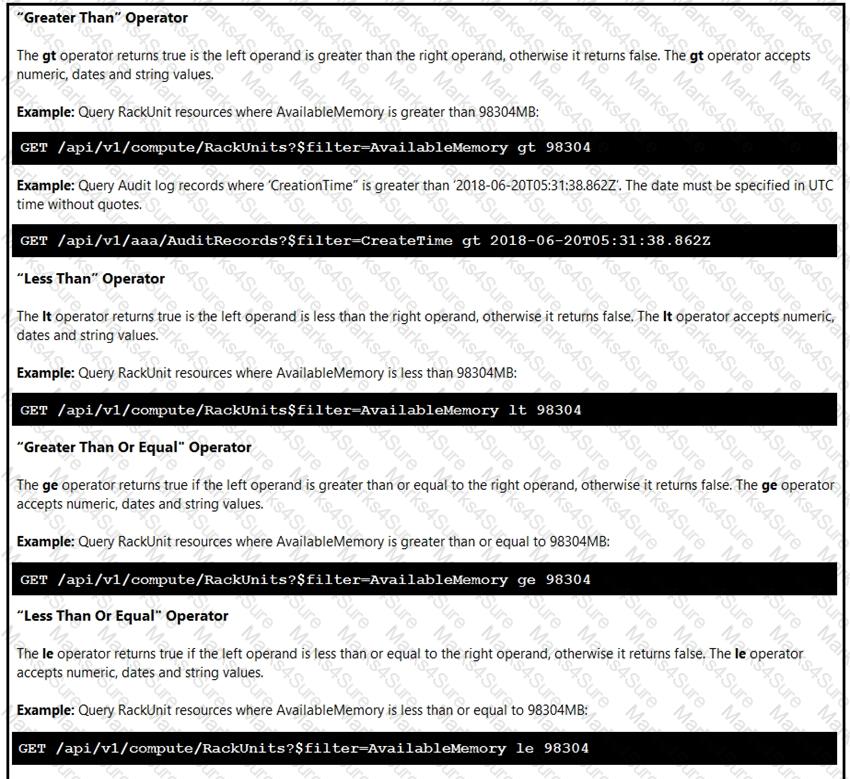
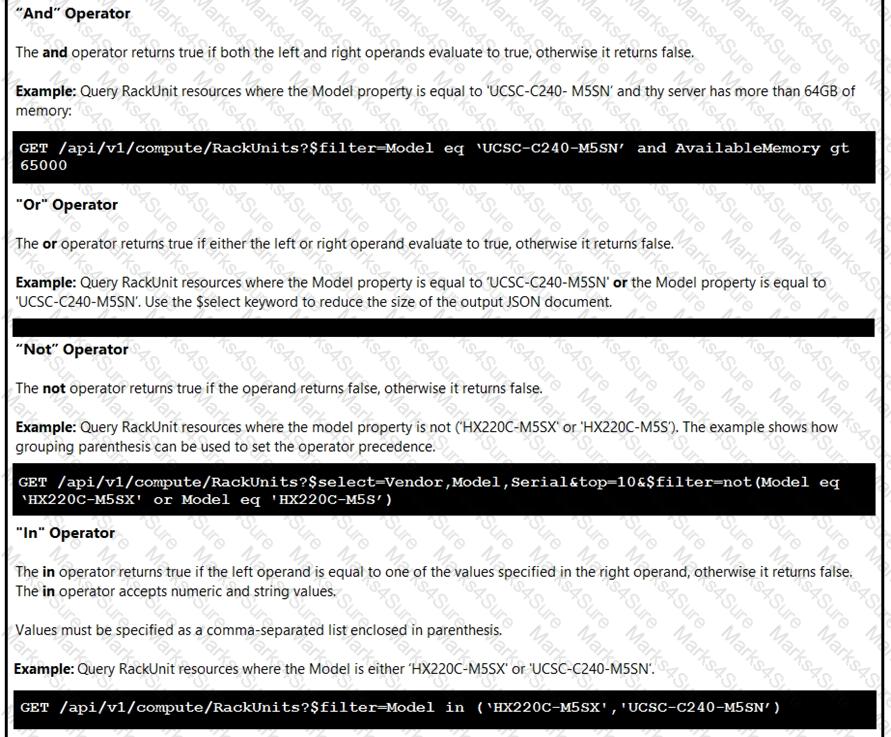
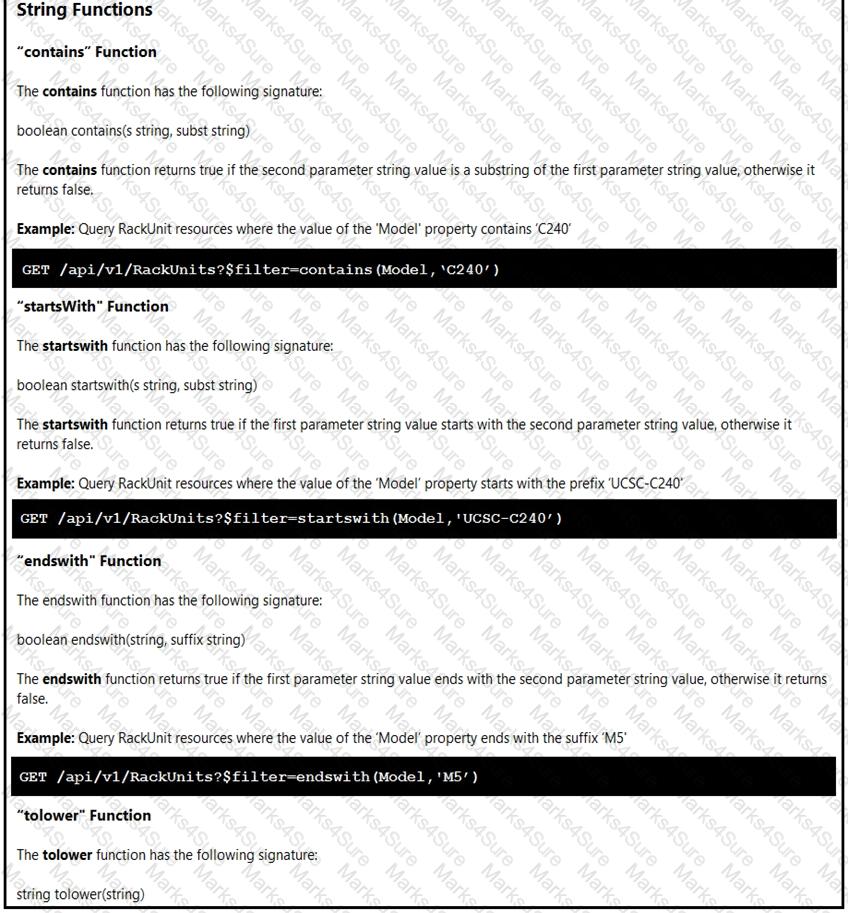
An engineer is managing a DC with 6000 Cisco UCS servers installed and running. The engineer has been asked to identify all resources where the model is in the UCSB family and the available memory is less than or equal to 5 GB.
Which REST API call accomplishes this task?
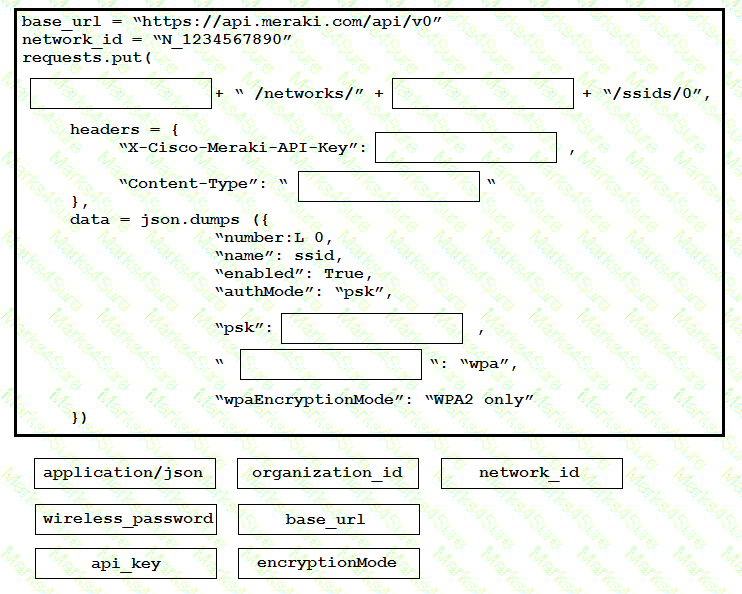
Drag and drop the code onto the snippet to update a SSID in Meraki using the Dashboard API. Not all options are used.
Why is end-to-end encryption deployed when exposing sensitive data through APIs?
A client is written that uses a REST API to interact with a server. Using HTTPS as the transport, an HTTP request is sent and received an HTTP response. The response contains the HTTP response status code: 503 Service Unavailable.
Which action is the appropriate response?
Which configuration stop must be performed on a Cisco IOS XE device to present collected data in Cisco DNA Center?
Refer to the exhibit.
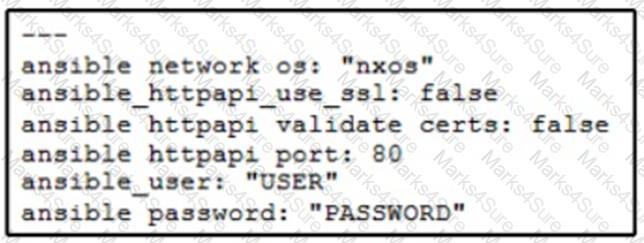
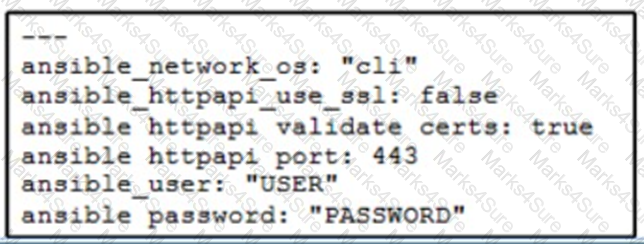
A network administrator copies SSL certificates to a Cisco NX-OS switch. An Ansible playbook is created to enable NX-API, which will use the new certificate. In the group_vars/vars.yml file, which code snippet must be used to define the properly formatted variables?
A)
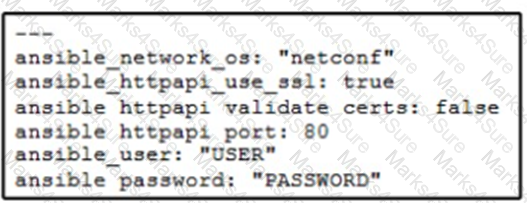
B)
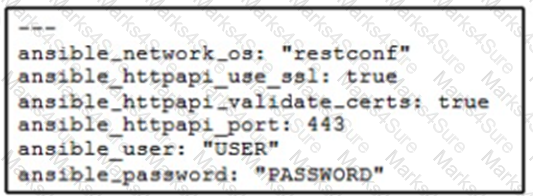
C)
D)
Refer to the exhibit.
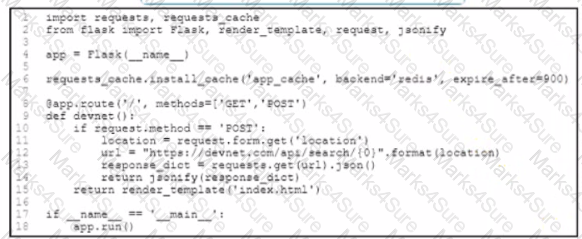
An application has been developed to serve the users in an enterprise After HTTP cache controls are implemented m the application users report that they receive state data when they refresh the page Without removing HTTP cache controls, which change ensures that the users get current data when refreshing the page'
Refer to the exhibit
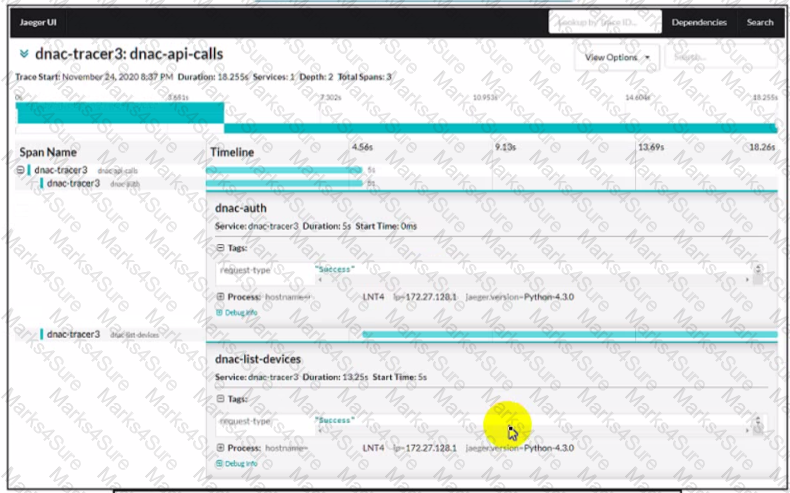

An application is developed to perform multiple API calls. The calls will be performed on the infrastructure devices Delays in the information transfer occur when the application is executed What are two reasons for the issue? (Choose two )
Refer to the exhibit.
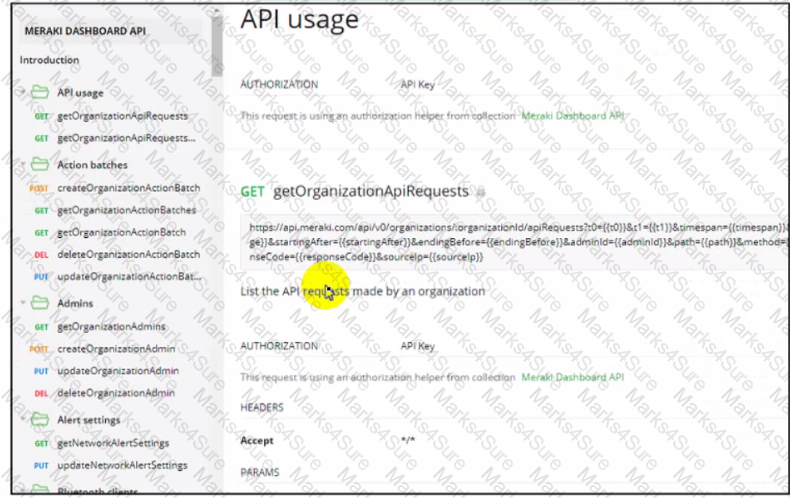
Drag and drop the code from the bottom onto the box where the code is missing to construct a Python script that will retrieve location data Not all options are used.
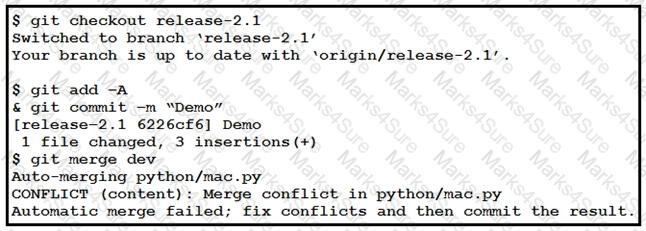
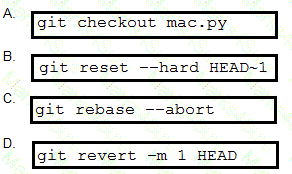
Refer to the exhibit. Which command resolves the merge conflict by removing the previous commit from the commit history?
Which transport layer protocol does gRPC use to retrieve telemetry information?
Refer to the exhibit.
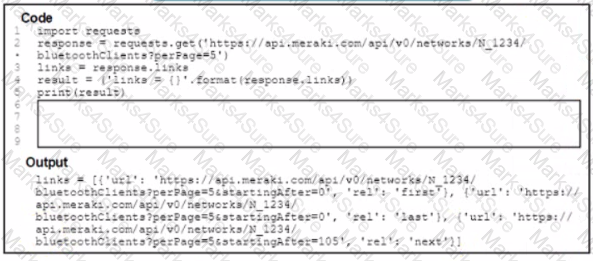
A Python script has these requirements
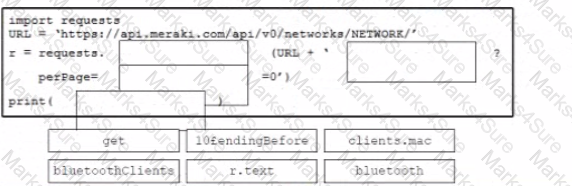
• Retrieve a list of Bluetooth clients seen by the access pants on a network.
• Print the content of the response
• Retrieve the next page only if it is available in the response headers
What must be added where the code is missing to get the remaining pages by using the next link from the link response header of the last request?
A)
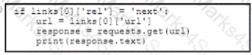
B)

C)
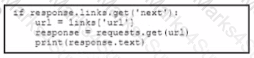
D)
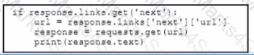
A bot has been created, called "386231131”, to respond to alarm messages. A developer is now creating a Webhook to allow the bot to respond to messages. Which format allows the Webhook to respond to messages for the bot within Webex Teams?
A)
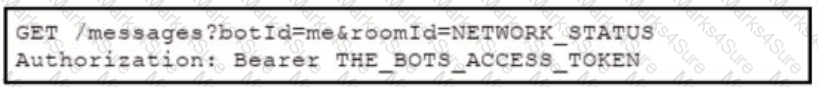
B)
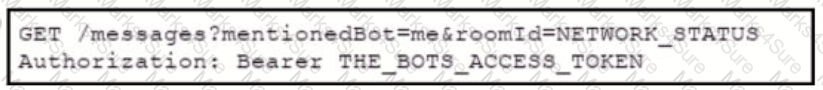
C)

D)
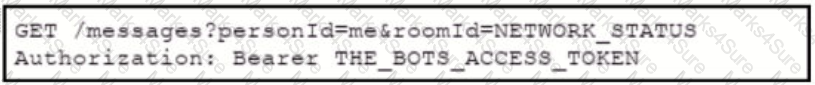
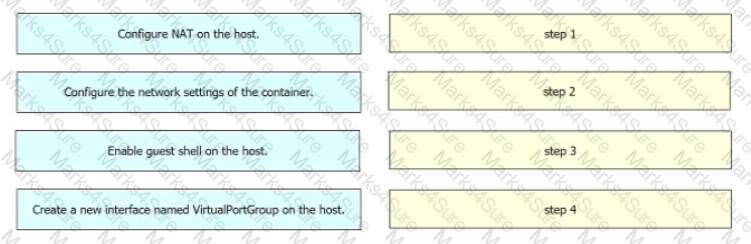
Drag and drop the steps from the left into the order on the right to ensure that an application requiring communication to the external network is hosted on a Cisco Catalyst 9000 switch.
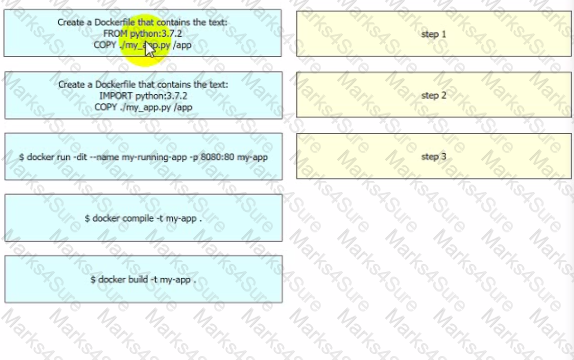
Drag and drop the steps from the left into the order on the right to build and run a customized Python DocKer image. Not all options are used
Refer to the exhibit.

A network engineer created a simple Python Flask application but must incorporate a CSRF token. Which code snippet must be added in the blank in the script to manually incorporate the token?
In the three-legged OAuth2 authorization workflow, which entity grants access to a protected resource?
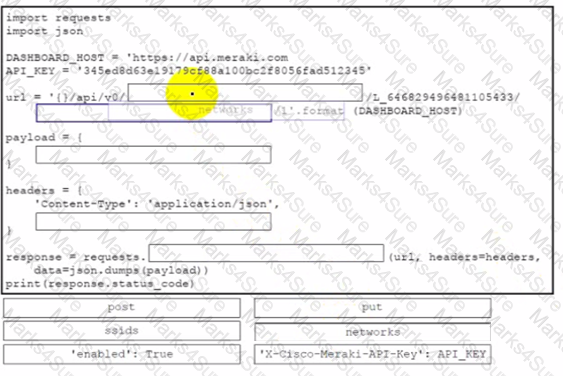
Drag and drop the code from the bottom onto the box where the code is missing to enable an SSID by using the Cisco Meraki Dashboard API. Not all options are used.
Refer to the exhibit.
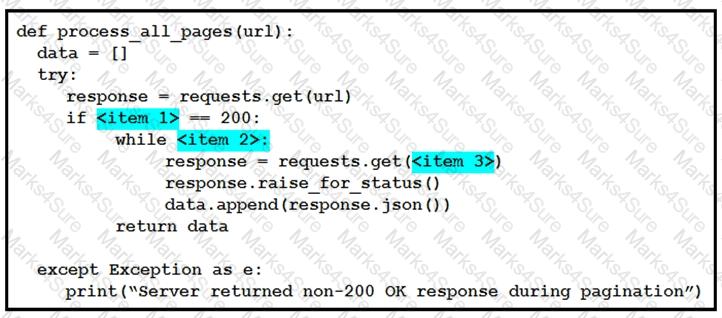
Drag and drop the parts of the Python code from the left onto the item numbers on the right that match the missing sections in the exhibit that consumes REST API pagination.
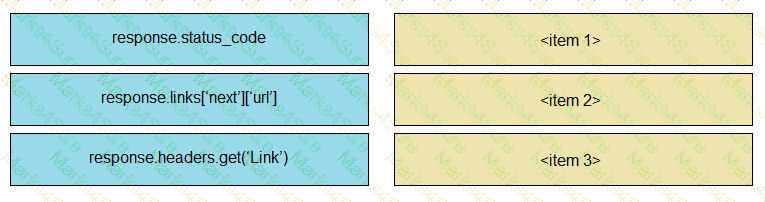
Refer to the exhibit.
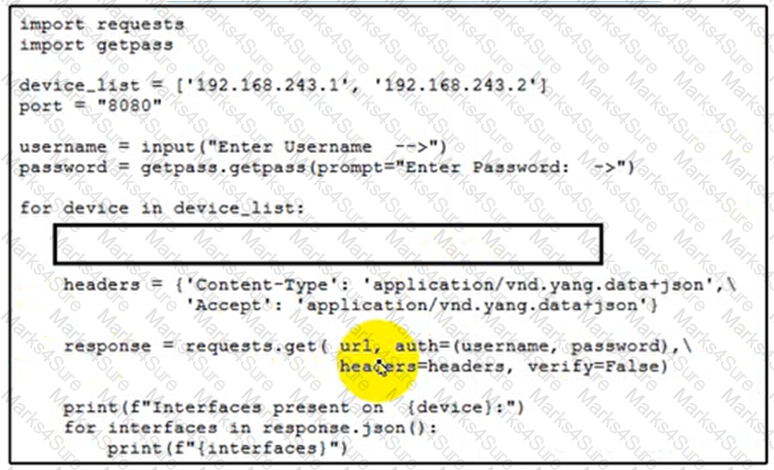
Cisco IOS XE switches are used across the entire network and the description that is filed for all interfaces must be configured. Which code snippet must be placed in the blank in the script to leverage RESTCONF to query all the devices in the device list for the interfaces that are present?
A)

B)
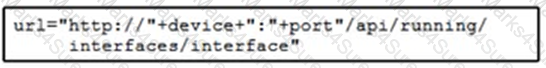
C)
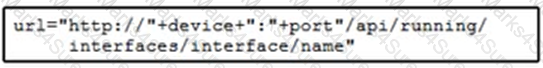
D)

An application requires SSL certificates signed by an intermediate CA certificate. The crt files must be available to the application:
• The root CA certificate is root_certrficate.crt.
• The intermediate CA certificate is intermediate_certificate.crt
• The application-specific SSL certificate is crt_certificate.crt.
Which Bash command outputs the certificate bundle as a .pern file?
A)

B)

C)

D)

An application is developed in order to communicate with Cisco Webex. For reporting, the application must retrieve all the messages sent to a Cisco Webex room on a monthly basis.
Which action calls /v1/messages directly?
Refer to the exhibit.
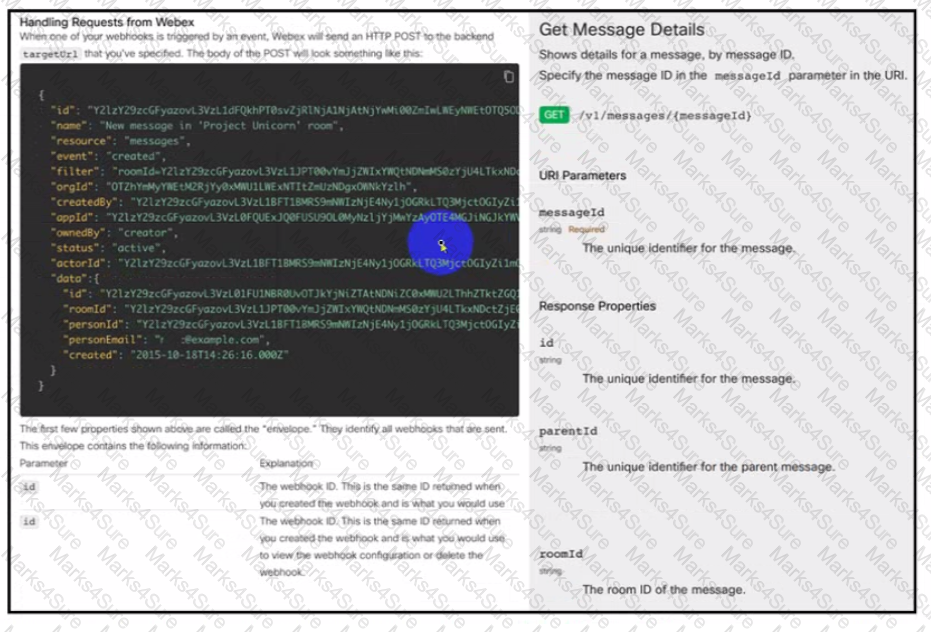
Drag and drop the code from the bottom onto the box where the code is missing to complete the API request. An engineer is using this API request to implement Chat-Ops to generate notifications m a Webex space by using webhooks. Not all options are used.

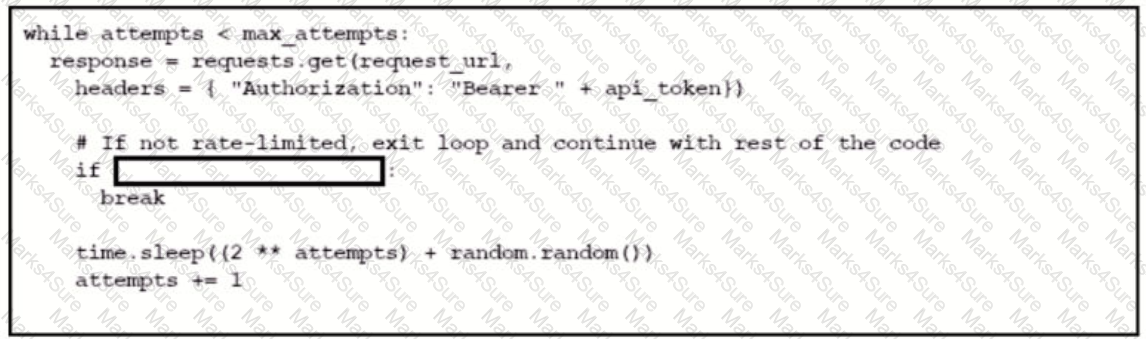
Drag and drop the code from the bottom onto the box where the code is missing to stop the REST API requests if a 'Too Many Requests" response is received Not all options are used.
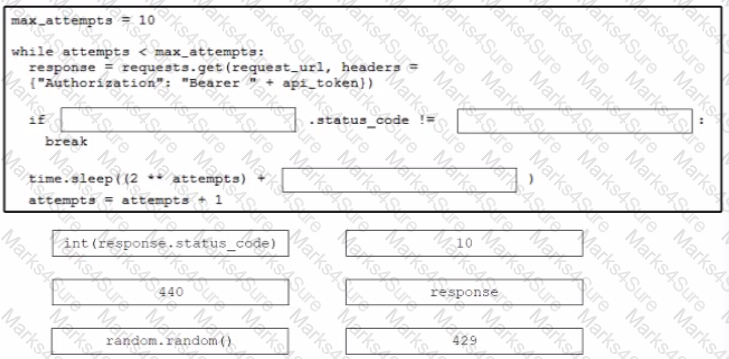
There is a requirement to securely store unique usernames and passwords. Given a valid username, it is also required to validate that the password provided is correct. Which action accomplishes this task?
A developer corrects an application bug with ID buglDa98416945110x and then installs it on a Cisco Catalyst 9300 series switch. Which command will enable the application called myapp?
Refer to the exhibit.
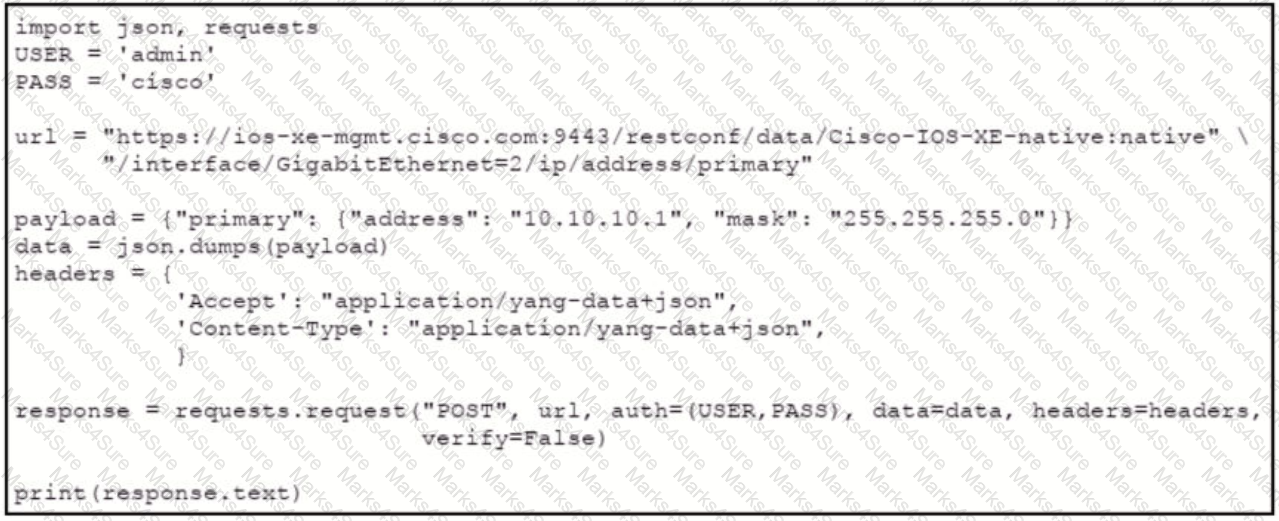
An engineer needs to change the IP address via RESTCOMF on interface GigabitEthernet2. An error message is received when the script is run. Which amendment to the code will result in a successful RESTCONF action?
What is a consideration for using gRPC as the model-driven telemetry protocol on a Cisco IOS XE device?
While developing an application following the 12-factor app methodology, which approach should be used in the application for logging?
A timeframe custom dashboard must be developed to present data collected from Cisco Meraki. The dashboard must include a wireless health alert count. What needs to be built as a prerequisite?
A developer is working on a live project and must apply a new feature. After the commit,the manager informs the team that the wrong file was applied. The developer must undo the single commit and apply the file with the name feature-App-UXU1411841916ADD. Which command must the developer use?
Refer to the exhibit.
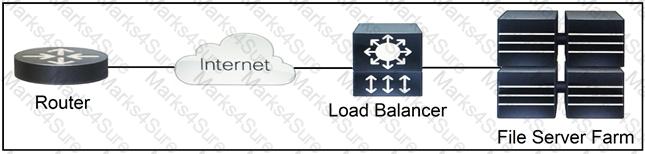
Which two functions are performed by the load balancer when it handles traffic originating from the Internet destined to an application hosted on the file server farm? (Choose two.)
Refer to the exhibit. The code fetches the latest order from the purchases table for a specific user. An engineer needs to pass query parameters to the execute function to prevent an SQL injection attack. Which code snippet must be placed in the blank in the code to meet this requirement?
A)
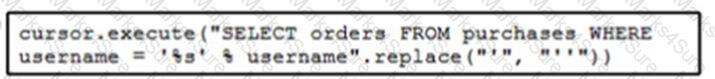
B)
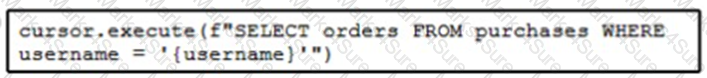
C)
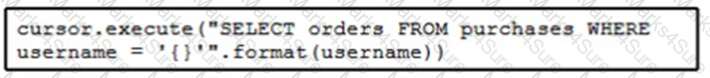
D)
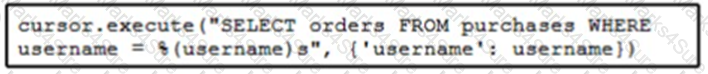
Refer to the exhibit.
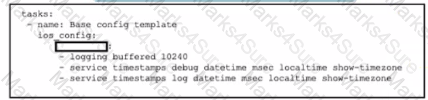
Which word is missing from this Ansible playbook shown, to allow the Cisco IOS XE commands for router configuration to be pushed after the playbook is executed?
A developer plans to create a new bugfix branch to fix a bug that was found on the release branch. Which command completes the task?
Drag and Drop the application requirement on the left onto the database type that should be selected for the requirement on the right.
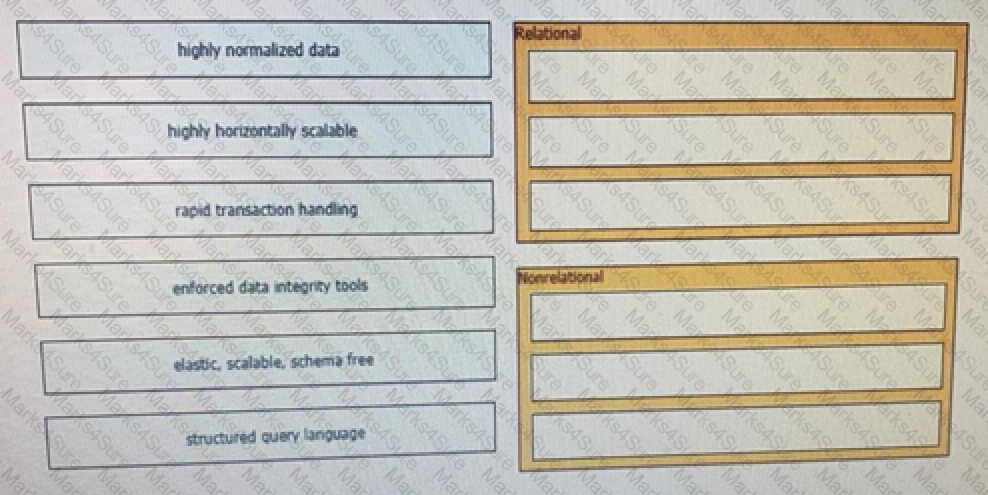
An application has these characteristics
• provide one service or function
• distributed database
• API gateway
• central repository for code
• configuration database
• uses session management
Which two design approaches contribute to the scalability of the application? (Choose two.)
Refer to the exhibit.
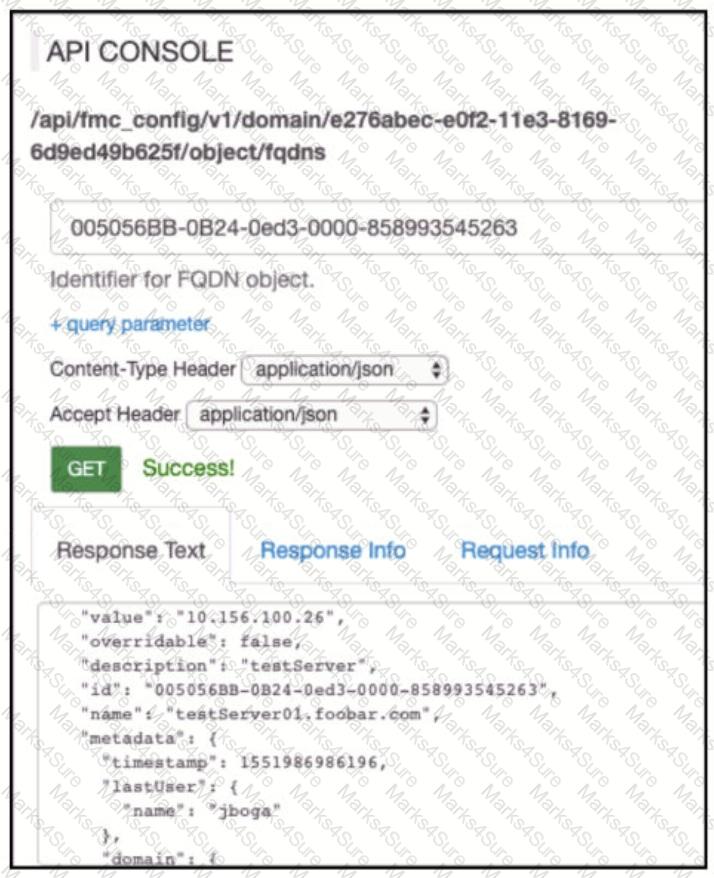
Which AP! call does an engineer use to delete the FQDN object?
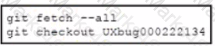
A development team is working on a bug fix in a remote branch named "UXbug000222134' and the current working primary branch is named ,prod409024967’ A developer who just joined the learn needs to checkout the remote branch Which Git commands must be used?
A)

B)

C)

D)
Refer to the exhibit.
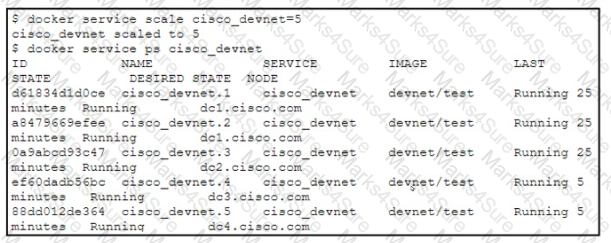
A developer runs the docker service scale command to increase the number of replicas for the cisco_devnet service. The swarm cluster is using a private IP address subnet. The service has these design requirements:
Which design approach is used to fulfill the requirements?
Which two gRPC modes of model-driven telemetry are supported on Cisco IOS XE Software? (Choose two.)
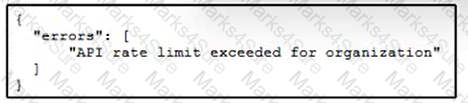
Which HTTP status code indicates that a client application is experiencing intentional rate limiting by the server?
Drag and drop the expressions from below onto the code to implement error handling. Not all options are used.
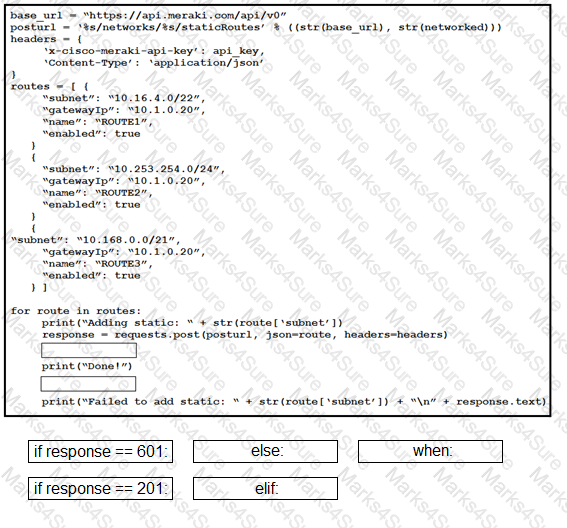
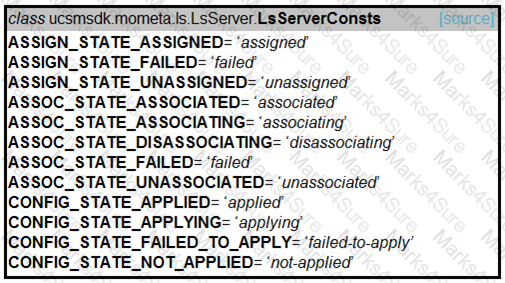
Refer to the exhibit. Drag and drop the code snippets from the bottom onto the blanks in the code to provision a new UCS server. Not all options are used.
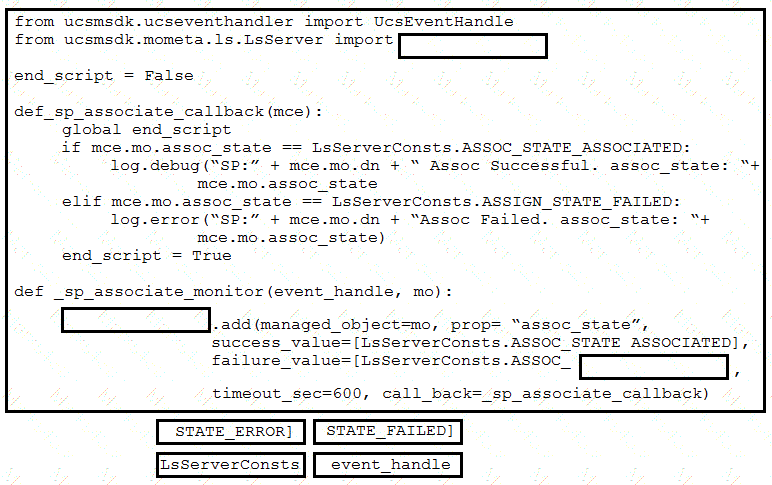
Refer to the exhibit.
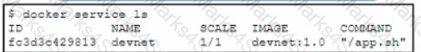
Refer to the exhibit A Docker swarm service is currently running m a local data center The service is hosting an HTML website it the container fads then the service becomes unavailable The design must meet these requirements
• The service must be highly available and resilient against a data center outage.
• The service must be accessible from a single URL
• The HTTP session must remain on the server from which the original request was sent
• Failure of the server must force the client to reconnect
Which two design approaches must be used to meet the requirements? (Choose two.)
A web application has those requirements for HTTP cache control:
Which header must the engineer use?
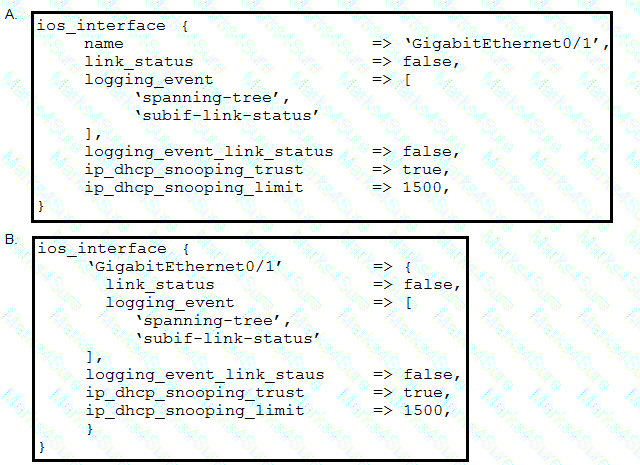
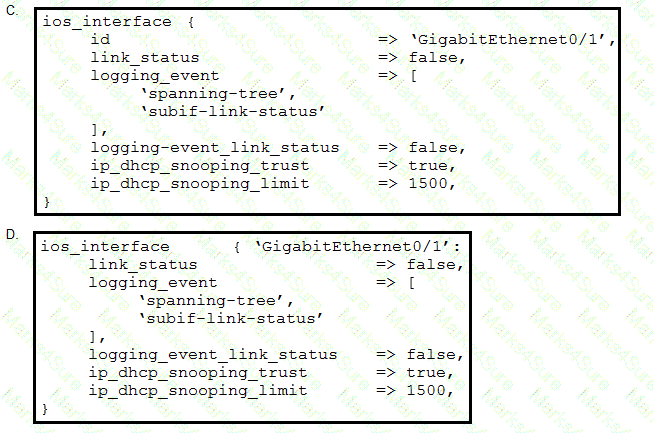
Which Puppet manifest needs to be used to configure an interface GigabitEthernet 0/1 on a Cisco IOS switch?
Refer to the exhibit.
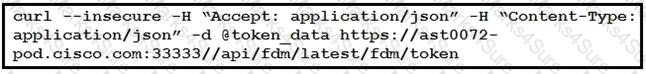
The cURL POST request creates an OAuth access token for authentication with FDM API requests. What is the purpose of the file “@token_data” that cURL is handling?
A developer has created an application based on customer requirements. The customer needs to run the application with the minimum downtime. Which design approach regarding high-availability applications, Recovery Time Objective, and Recovery Point Objective must be taken?
Refer to the exhibit.

An engineer is managing a network that consists of Cisco IOSXE devices. There is a need to retrieve the details of the interface GigabitEthernet2 using RESTCONF. Which URI will accomplish this by providing the same response as shown in the JSON body?
A)

B)

C)

D)

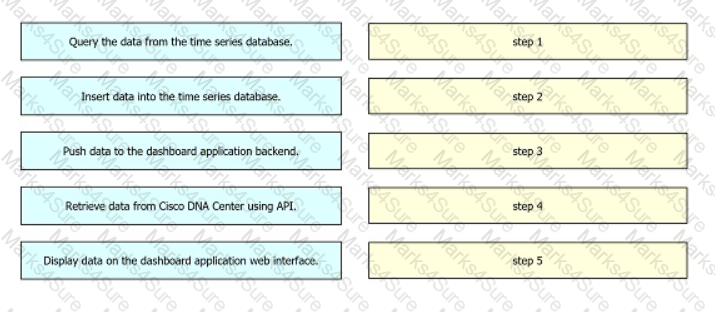
Drag and drop the operations from the left into the order on the right to create a web dashboard that displays Cisco DNA Center data for an organization.
Refer to the exhibit.
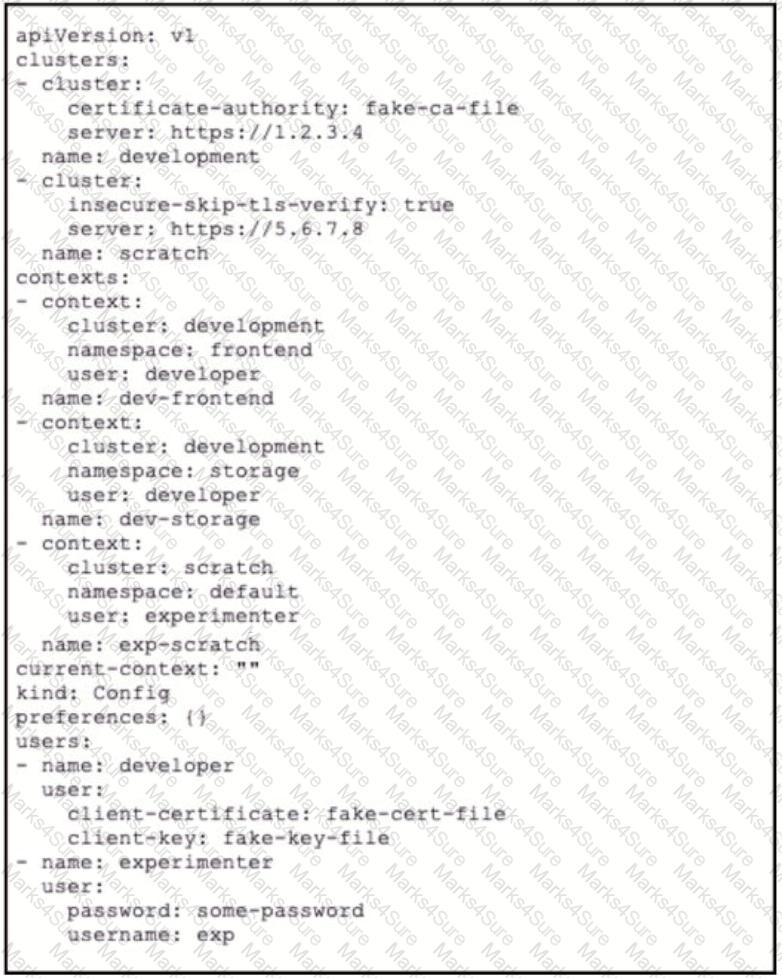
A kubeconfig file to manage access to Kubernetes clusters is shown. How many Kubernetes clusters are defined in the
file, and which cluster FS accessed using username/password authentication rather than using a certificate?
A user is receiving a 429 Too Many Requests error. Which scheme is the server employing that causes this error?
Drag and drop the code from the bottom onto the box where the code is missing to create a new Cisco Webex space and attach a previously configured bot named 'sampleBot'. Not all options are used.

Application sometimes store configuration as constants in the code, which is a violation of strict separation of configuration from code. Where should application configuration be stored?
An application is made up of multiple microservices, each communicating via APIs. One service is beginning to be a bottleneck for the application because it can take a lot of time to complete requests. An engineer tried adding additional instances of this service behind the load balancer, but it did not have any effect. Which application design change must be implemented m this scenario?
Refer to the exhibit.
Drag and drop the code snippets from the bottom onto the boxes where the code is missing to retrieve a list of all the members of a specific Cisco Webex organization Not at options are used.

A container running a Python script is failing when it reaches the integration testing phase of the CI/CD process. The code has been reviewed thoroughly and the build process works on this container and all other containers pass unit and integration testing.
What should be verified to resolve the issue?

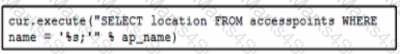
Refer to the exhibit A script returns the location of a specific access point when given the access point name If a user enters a search value such as DROP TABLE access points then the entire table is removed. What must be added to the box where the code is missing to prevent a SQL injection attack?
A)
B)
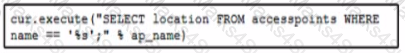
C)

D)

An application must be able to print the values of the variables in specific modules. Different message levels will be used for production and for development. Proof of access and activity must be documented. What must be included in the implementation to support these observability requirements?
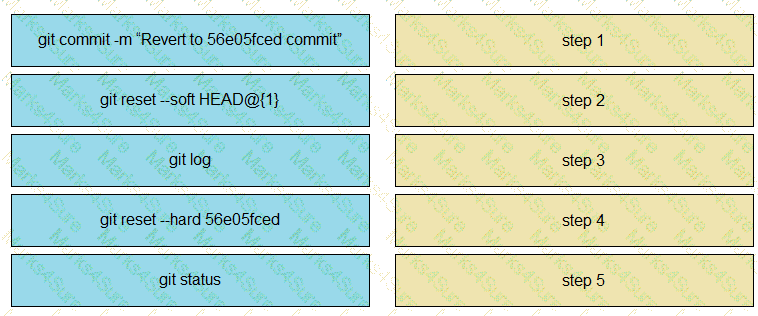
Drag and drop the steps from the left into the correct sequence on the right to describe how to use Git to maintain the current HEAD and revert back to a previous commit, while undoing all intermediate commits.
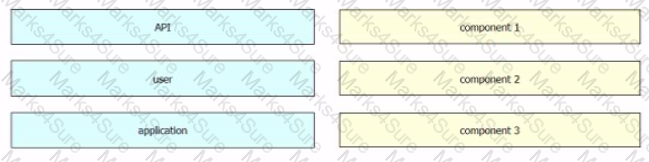
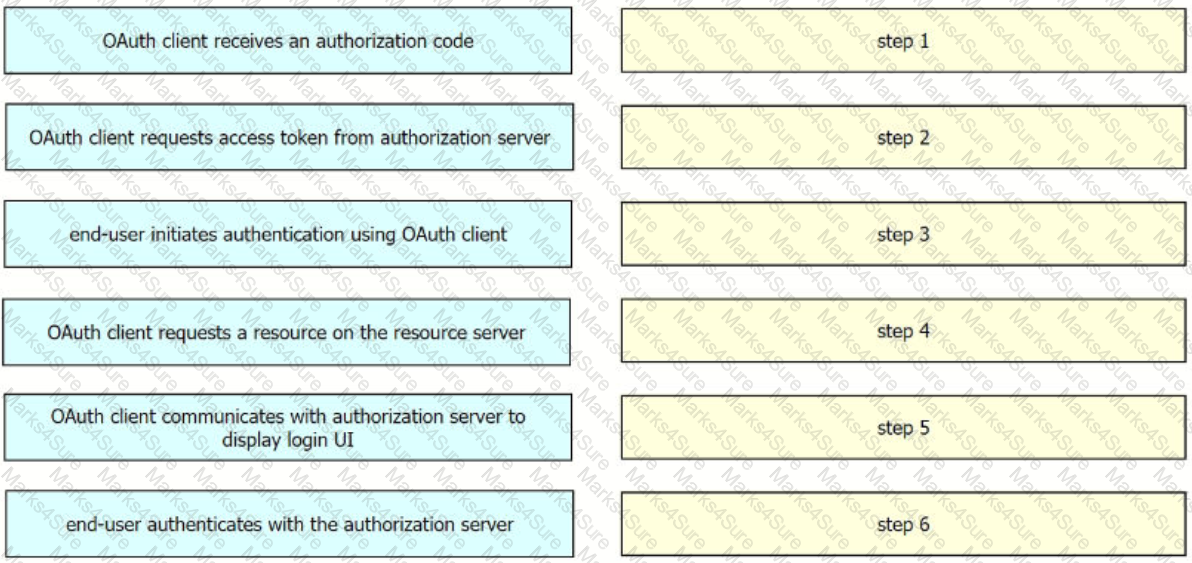
Drag and drop the components from the left into the order on the right to create the flow of the three-legged OAuth2.
A developer is creating a Python script to analyze errors during REST API call operations. The script will be used with Cisco solution and devices. Drag and drop the code from the bottom to the box where the code is missing to implement control flow for handling unrecoverable REST API calls. Not all options are used.

Refer to the exhibit.
Which code snippet completes this code to handle API rate-limit?
Drag and drop the steps on the left into the order on the right for an end-user to access an OAuth2 protected resource using the Authorization Code Grant1 flow.
A developer is working on an enhancement for an application feature and has made changes to a branch called ‘devcor-432436127a-enhance4‘. When merging the branch to production, conflicts occurred. Which Git command must the developer use to recreate the pre-merge state?
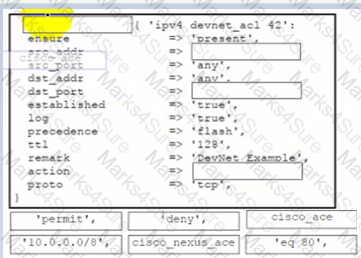
Drag and drop the code from the bottom onto the box where the code is missing to permit network traffic between 10.0.0.0/8 and all other networks on port 80 for a Cisco Nexus 9000 switch by using the Puppet module. Not all options are used.
Refer to the exhibit.
An architect wrote an application to collect device information from the Cisco Meraki Dashboard API. Every time a network change occurs the application collects information and records new endpoint MAC addresses. The application stopped working after the locations and network equipment of a competitor were acquired. Which application approach must be applied to reduce latency and rate limiting?
The Meraki API URL https://api.meraki.com/api/v0/networks/123456789/ssids/2 has been stored in the environment variable meraki_url and the API key has been stored in meraki_api_key. Which snippet presents the API call to configure, secure and enable an SSID using the Meraki API?
A)
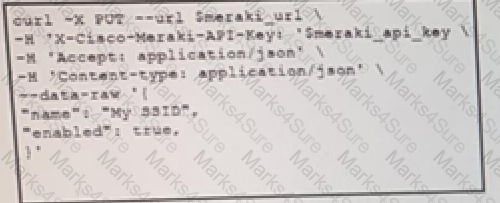
B)

C)

D)

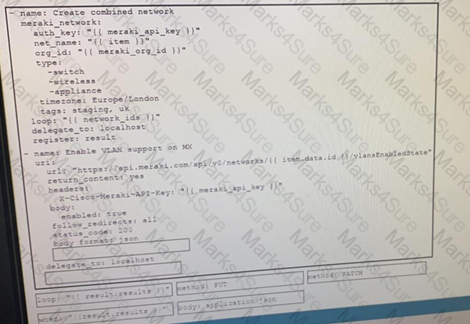
Drag and drop the code from the bottom onto the box where the code is missing on the Ansible task to enable a VLAN on a Meraki MX Device, Not all options are used.
An enterprise refactors its monolithic application into a modem cloud-native application that is based on microservices. A key requirement of the application design is to ensure that the IT team is aware of performance issues or bottlenecks in the new application Which two approaches must be part of the design considerations'' (Choose two.)
Refer to the exhibit.
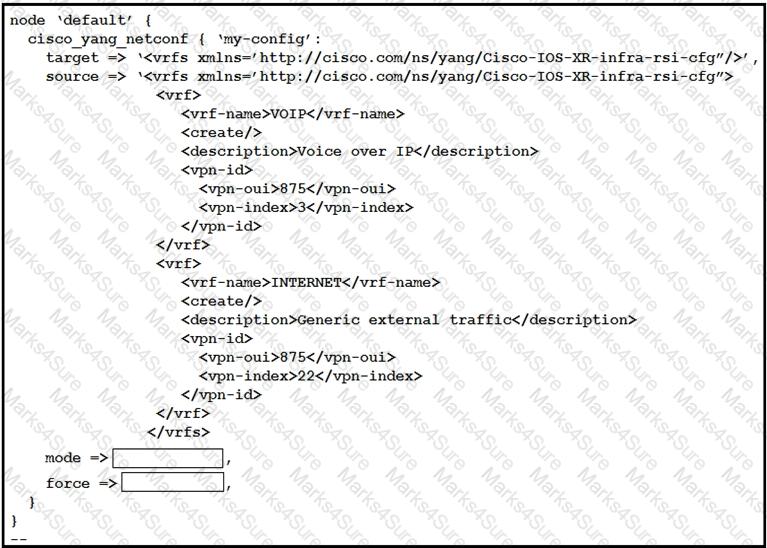
This script uses ciscoyang to configure two VRF instances on a Cisco IOS-XR device using the Yang NETCONF type.
Which two words are required to complete the script? (Choose two.)
A team is developing a cloud-native application for network monitoring and management of various devices. An increased growth rate of users is expected. The solution must be easily managed and meet these requirements:
•able to use dependencies
•easy disposability
•flexible configuration
Which application design approach must be used?
Refer to the exhibit.
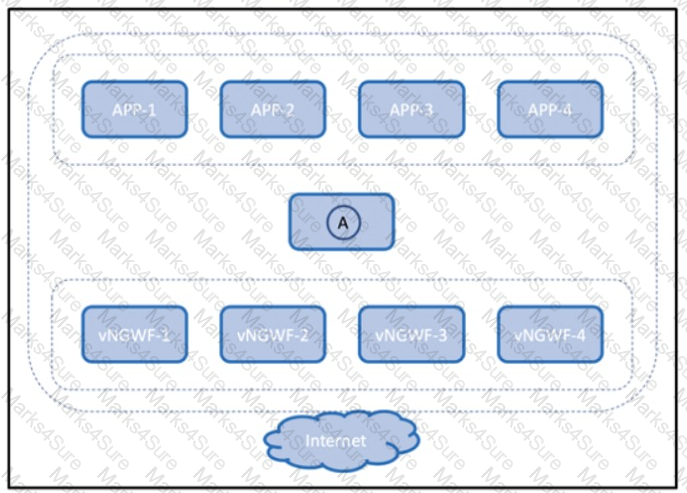
The virtual next-generation firewalls running in the public cloud must be scaled out to meet the throughput requirements of the application layer. Which component is deployed to location A in the diagram?
An engineer needs to configure an interface named GigabitEthernet3 with an IP address on several RESTCONF-enabled Cisco IOS XE devices. Which code snippet must be placed in the blank in the code to meet this requirement?
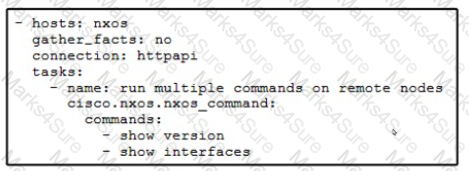
An engineer needs to automate the configuration on a Cisco NX-OS switch. The solution must meet these requirements:
•Ansible is used
•The transport protocol is encrypted
•Support for Asynchronous requests.
Which two access mechanisms must be used? (Choose two.)
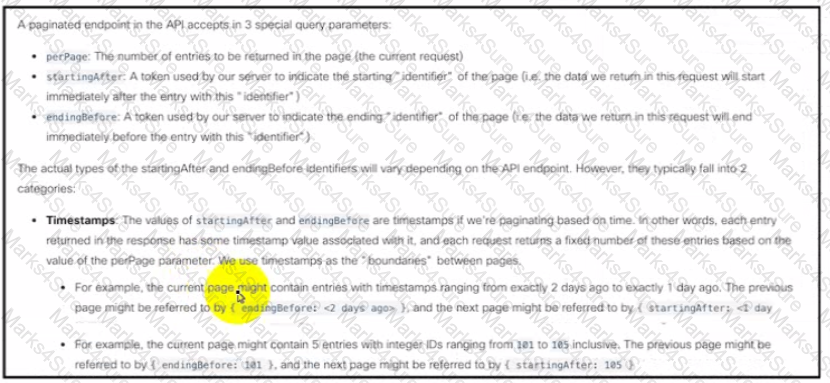
Refer to the exhibit Drag and drop the code from the bottom onto the box where the code is missing to query the last 10 Bluetooth clients seen by APs in their network using the Meraki Dashboard API Not all options are used.
Refer to the exhibit.
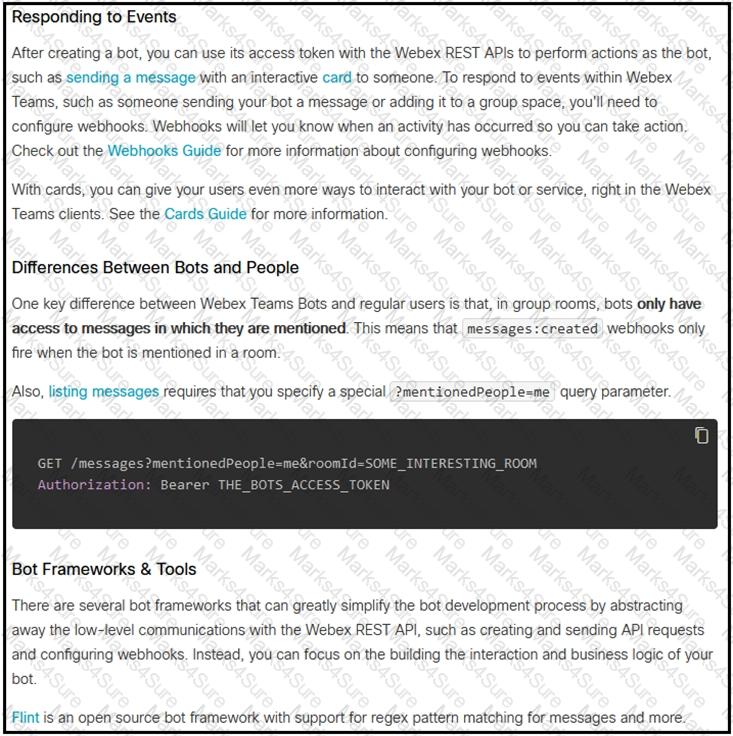
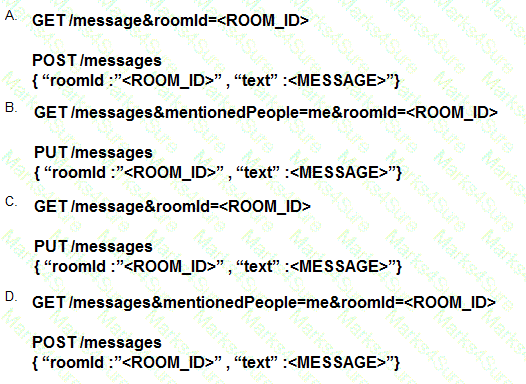
Which set of API requests must be executed by a Webex Teams bot after receiving a webhook callback to process messages in a room and reply with a new message back to the same room?
Which two countermeasures help reduce the risk of playback attacks? (Choose two.)
While working with the Webex Teams API, on an application that uses end-to-end encryption, a webhook has
been received. What must be considered to read the message?
Refer to the exhibit.
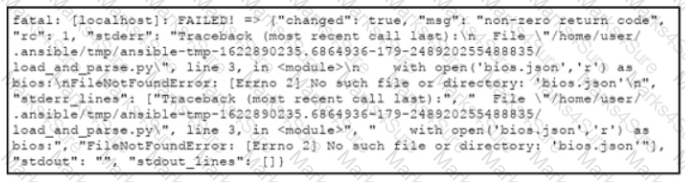
An engineer creates an application that leverages the Ansible framework to provision CPE endpoints that have configuration changes. The application contains an Ansible playbook named provision_cpes.yml that uses the ansible.builtin.script Ansible module to execute these two Python scripts:
•gather and_create.py. which creates a JSON file named bios.json that contains the CPE models and their respective IOS file information
•load and parse.py. which loads the file data and parses it for later consumption
After several successful runs, the application fails. During a review of the Ansible execution logs, the engineer discovers an error output that indicates that one of the stages failed. What is the cause of this issue?
Refer to the exhibit.
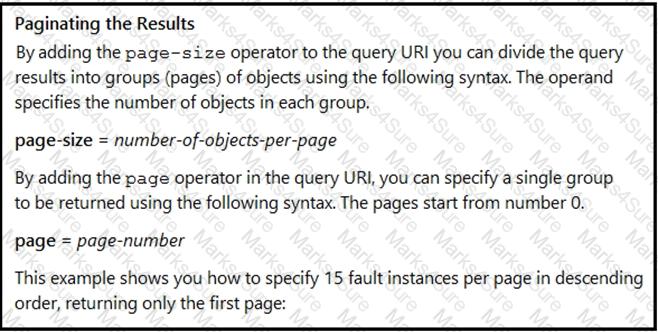
Many faults have occurred in the ACI environment and a sample of them needs to be examined. Which API call retrieves faults 30 through 45?
A developer wants to automate virtual infrastructure to provision and manage it. The system will be implemented m large-scale deployment while offering redundancy and scalability with ease of management The solution must meet these requirements:
• Support the provisioning of up to 500 new virtual machines into private datacenters or the public cloud
• Support the modeling of a complex environment that consists of multiple virtual machines while supporting disaster recovery
• Maintain steady-state environments
Which configuration management solution must the developer use?
Refer to the exhibit.
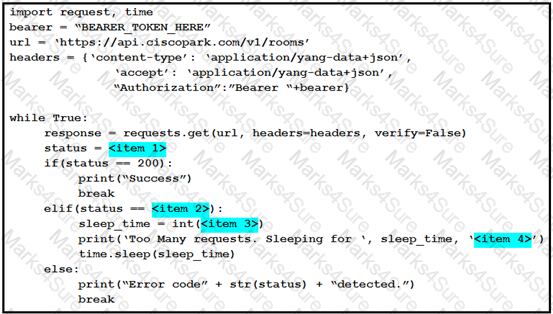
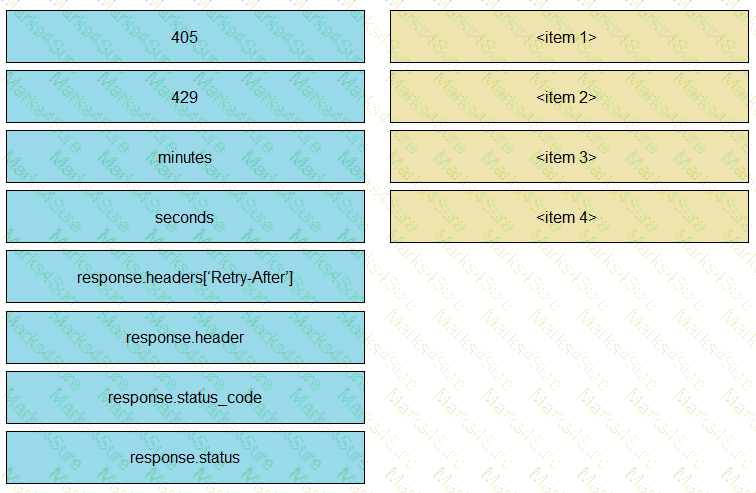
A developer is creating a Python script to use the Webex Teams REST API to list joined spaces, retry after the server-specified amount of time if a “Too many requests” response is received, and print any other error that is received. Drag and drop the code snippets from the left onto the item numbers on the right that match the missing sections in the exhibit to complete the script. Not all code snippets are used.
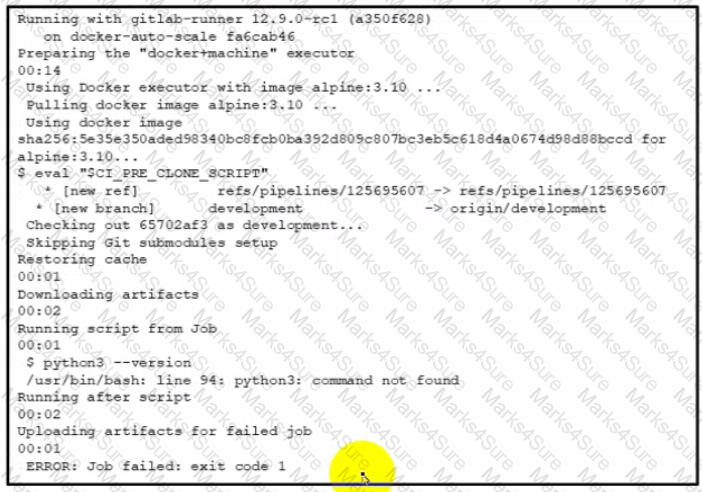
Refer to the exhibit. Which action resolves the error for the GitLab CI/CD pipeline execution?
Refer to the exhibit.
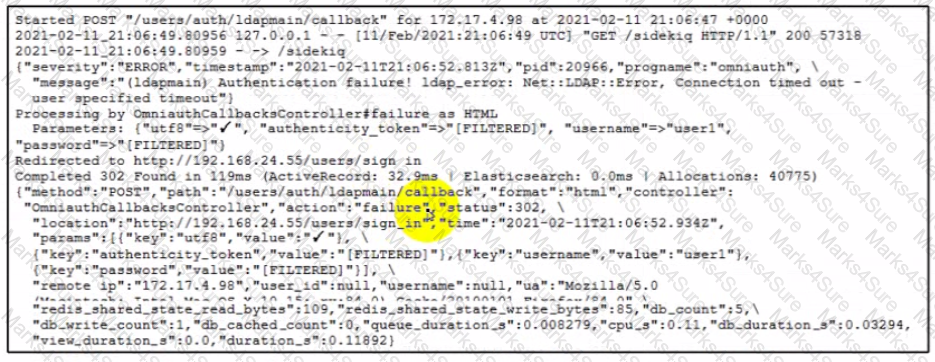
Recently, users have reported problems logging into an application with their usernames and passwords. The logs have captured an authentication attempt. Based on the messages and errors contained, what is the cause of the problem?
A developer is working on a new feature in a branch named 'newfeay000222118' and the current working primary branch is named 'pnm409024967' The developer requires a merge commit during a fast forward merge for record-keeping purposes. Which Git command must Be used?
A)
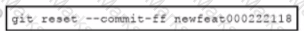
B)

C)

D)

Drag and drop the code snippets from the bottom onto the boxes where the code is missing to complete the API call to implement error handling Not all options are used.
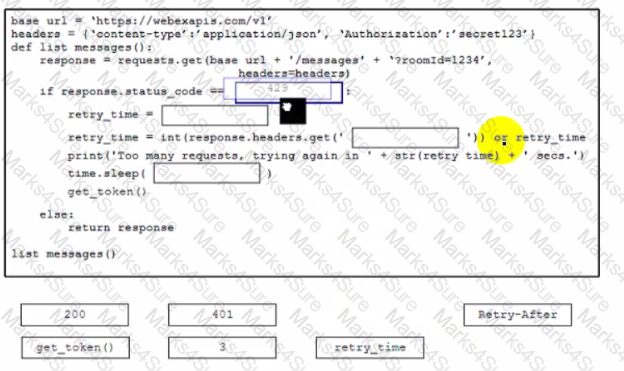
How does the use of release packaging allow dependencies to be effectively managed during deployments?
Refer to the exhibit.
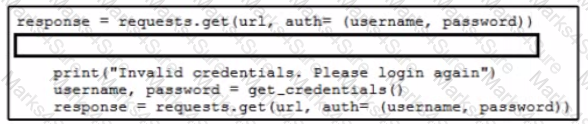
Which code snippet must be added to the blank in the code to automate the evaluation and handling of errors due to wrong credentials when Basic Authorization is used?
A)

B)

C)

D)
