Scrum is a subset of Agile and is a lightweight process framework for Agile development Which role becomes the interface between the business the customers and their product-related needs on one side and the Team on the other?
Which three elements help network designers to construct secure systems that protect information and resources (such as devices, communication, and data) from unauthorized access, modification, inspection, or destruction? (Choose three.)
A business requirement stating that failure of WAN access for dual circuits into an MPLS provider for a Data Centre cannot happen due to related service credits that would need to be paid has led to diversely routed circuits to different points of presence on the providers network? What should a network designer also consider as part of the requirement?
You have been asked to design a remote access VPN solution to support up to 2000 devices. You must ensure that only corporate assets are allowed to connect to the VPN, and users must authenticate to gain access of their based on their user role. Users must use a password that they are already using to access existing applications . A user may not always use the same device to access the VPN. Which two options combined meet the requirements? (Choose two)
Company XYZ has implemented policy-based routing in their network. Which potential problem must be kept in mind about network reconvergence and PBR?
A green data center is being deployed and a design requirement is to be able to readily scale server virtualization Which IETF standard technology can provide this requirement?
Which technology is an open-source infrastructure automation tool that automates repetitive tasks for users who work in networks such as cloud provisioning and intraservice orchestration?
You are designing an Out of Band Cisco Network Admission Control. Layer 3 Real-IP Gateway deployment for a customer Which VLAN must be trunked back to the Clean Access Server from the access switch?
Which optimal use of interface dampening on a fast convergence network design is true?
Which two statements describe the usage of the IS-IS overload bit technique? (Choose two )
Enterprise XYZ wants to implement fast convergence on their network and optimize timers for OSPF However they also want to prevent excess flooding of LSAs if there is a constantly flapping link on the network Which timers can help prevent excess flooding of LSAs for OSPF?
Refer to the exhibit.
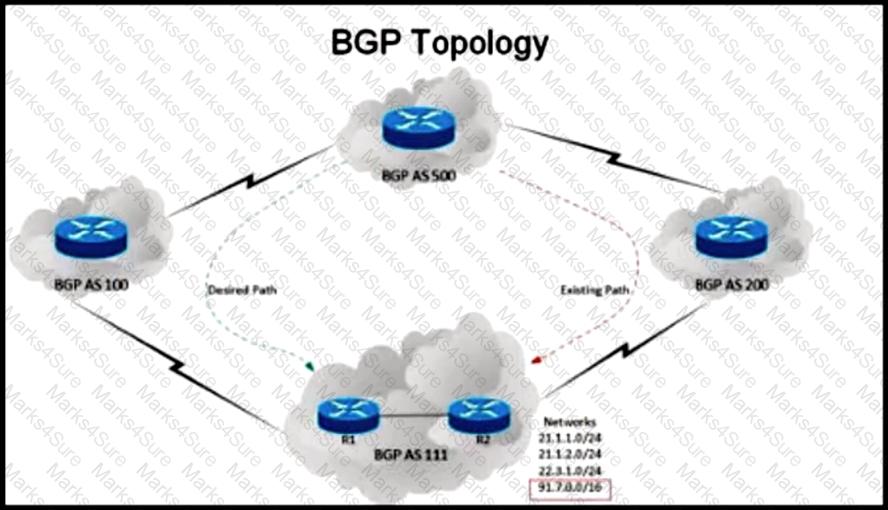
An engineer has been asked to redesign the traffic flow toward AS 111 coming from AS 500.Traffic destined to AS 111 network 91 7 0.0/16 should come in via AS 100. while traffic destined to all other networks in AS 111 should continue to use the existing path Which BGP attributes are best suited to control this inbound traffic coming from BGP AS 500 Into the 91.7.0.0/16 network?
An existing wireless network was designed to support data traffic only. You must now install context Aware services for location tracking changes must be applied to the existing wireless network to increase the location accuracy? (Chose two)
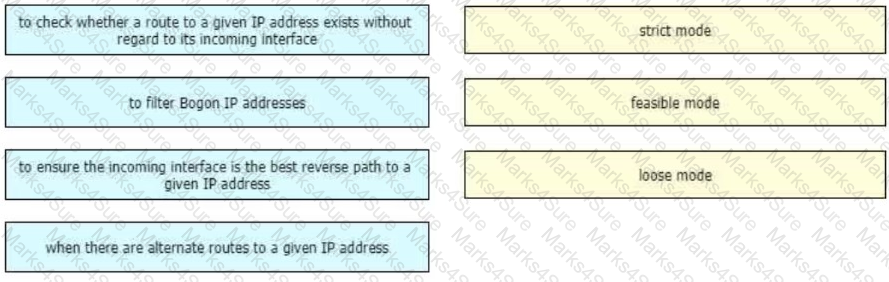
Drag and drop the design use cases from the left onto the correct uRPF techniques used to prevent spoofing attacks Not all options are used.
Refer to the exhibit.
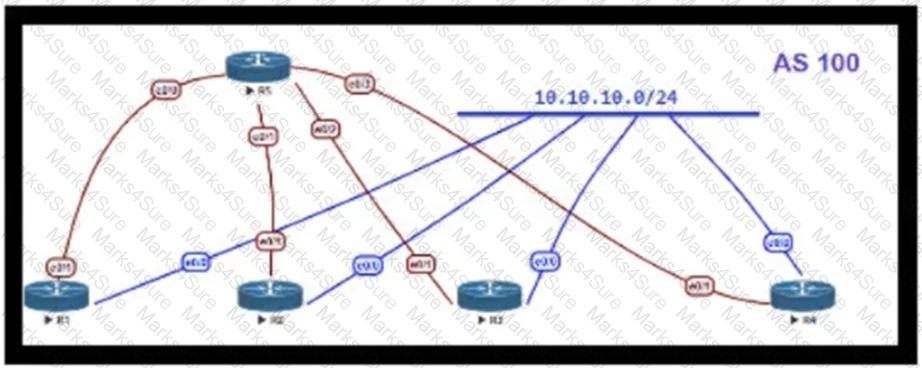
OSPF is running as the IGP to provide reachability to all AS100 networks R3 and R4 are the current ABRs at the boundary of OSPF Area0 and Areal Now BGP must be deployed within AS 100 because it will be receiving Internet routes from its eBGP peers (the service provider) connected to R1 and R2 What is an optimal solution for this deployment to configure BGP relationships and redistribute BGP learned routes into OSPF?
Which tool automates network implementation activities and shortens the implementation lifecycle?
Which network management framework can be used to develop a network architecture that contains business requirements analysis, gap analysis, and network diagrams as artifacts to be used for design and implementation later?
The Company XYZ network requires OSPF dead neighbor detection in a subsecond manner However the company network does not support BFD Which other feature can be used to fulfill the design requirement?
The Agile Manifesto is a document that defines the key values and principles behind the Agile philosophy and helps development teams work more efficiently and sustainably Each of the four key values is split into two sections a left-hand side and a right-hand side In other words, though there is value in the items on the right we value the items on the left more What is one of the key values of the Agile Manifesto?
A software-defined networking (SDN) controller teams network topology information by using BGP link-state sessions with the route reflectors of an MPLS-enabled network. The controller then uses the topology information to apply on-demand traffic policies to the network through a protocol that is supported from all Layer 3 routers Each policy is represented as a RIB entry in the control plane of the router Which SDN model has been implemented?
Which two statements explain the operation of BFD asynchronous mode? (Choose two )
A healthcare provider discovers that protected health information of patients was altered without patient consent. The healthcare provider is subject to HIPAA compliance and is required to protect PHI data. Which type of security safeguard should be implemented to resolve this issue?
The General Bank of Greece plans to upgrade its legacy end-of-life WAN network with a new flexible, manageable, and scalable solution. The mam requirements are ZTP support, end-to-end encryption application awareness and segmentation. The CTO states that the main goal of the bank is CAPEX reduction. Which WAN technology should be used for the solution?
Company XYZ is migrating their existing network to IPv6 and they must plan for Layer 2 and Layer 3 devices Some of the access layer switches do not support IPv6, however, core and distribution switches fully support unicast and multicast routing. The company wants to minimize cost of the migration. Which migration strategy should be used in the design?
Refer to the exhibit.
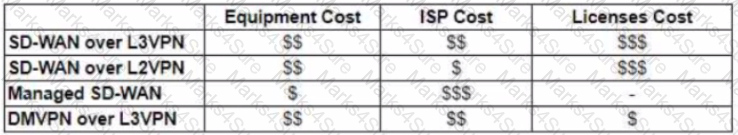
The WAN network of the General Bank of Greece has experienced several outages It takes too long to activate a new branch site The networking department of the bank plans to upgrade the legacy end-of-life WAN network with a new flexible manageable, and scalable in-house solution The number of branches will increase exponentially in the next fiscal year The CTO states that the bank’s mam goal is OPEX reduction The network engineering team prepares a table to evaluate the available options Which WAN technology can be used for the solution?
Two routers R1 and R2 are directly connected through an Ethernet link. Both routers are running OSPF over the Ethernet link and OSPF has been registered with BFD. R1 has been set up to transmit BFD at a 50 ms interval, but R2 can receive only at a 100 ms rate due to platform limitations. What does this mean?
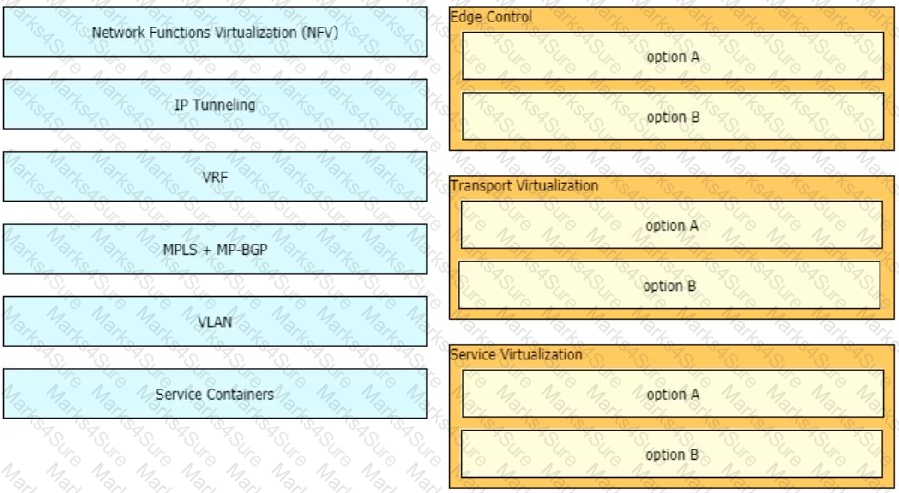
Drag and drop the end-to-end network virtualization elements from the left onto the correct network areas on the right.
Company XYZ is revisiting the security design for their data center because they now have a requirement to control traffic within a subnet and implement deep packet inspection Which technology meets the updated requirements and can be incorporated into the design?
Which two features describe controller-based networking solutions compared to traditional networking solutions? (Choose two.)
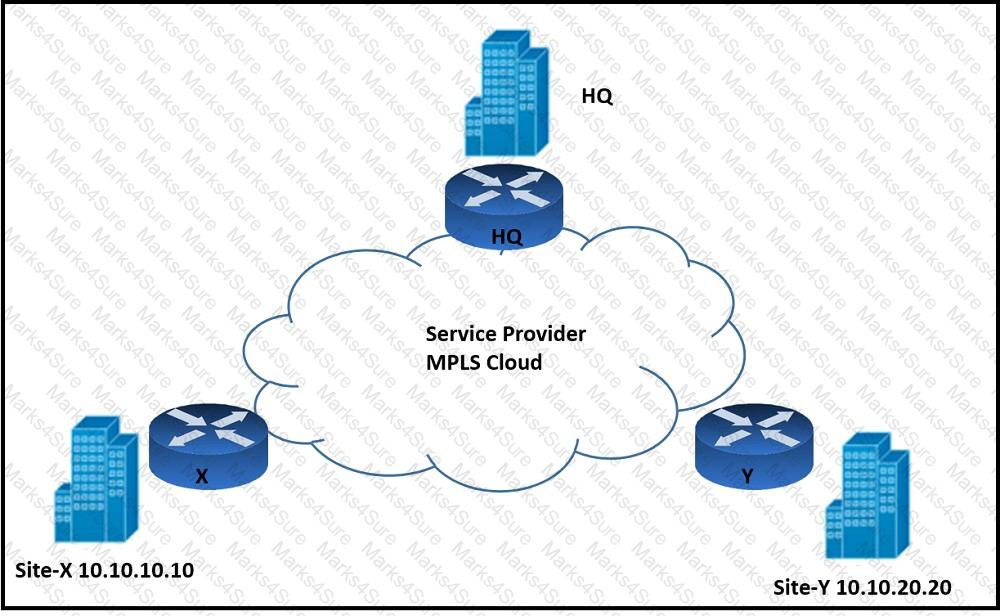
Refer to the exhibit. An architect must design an enterprise WAN that connects the headquarters with 22 branch offices. The number of remote sites is expected to triple in the next three years. The final solution must comply with these requirements:
Only the loopback address of each of the enterprise CE X and Y routers must be advertised to the interconnecting service provider cloud network.
The transport layer must carry the VPNv4 label and VPN payload over the MP-BGP control plane.
The transport layer must not be under service provider control.
Which enterprise WAN transport virtualization technique meets the requirements?
Which actions are performed at the distribution layer of the three-layer hierarchical network design model? (Choose two)
A healthcare customer requested that SNMP traps must be sent over the MPLS Layer 3 VPN service. Which protocol must be enabled?
The Company XYZ network is experiencing attacks against their router. Which type of Control Plane Protection must be used on the router to protect all control plane IP traffic that is destined directly for one of the router interfaces?
In the case of outsourced IT services, the RTO is defined within the SLA. Which two support terms are often included in the SLA by IT and other service providers? (Choose two.)
An enterprise solution team is performing an analysis of multilayer architecture and multicontroller SDN solutions for multisite deployments. The analysis focuses on the ability to run tasks on any controller via a standardized interface. Which requirement addresses this ability on a multicontroller platform?
SDN is still maturing Throughout the evolution of SDN which two things will play a key role in enabling a successful deployment and avoiding performance visibility gaps in the infrastructure? (Choose two.)
Refer to the table.
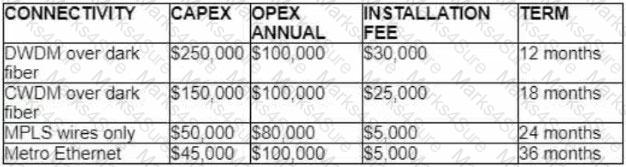
A customer investigates connectivity options for a DCI between two production data centers to aid a large-scale migration project. The solution must provide a single 10G connection between locations and be able to run its own varying QoS profiles without service provider interaction based on the migration stages. All connectivity methods are at 10 Gbps. Which transport technology costs the least if the connectivity is required for just one year?
When designing a WAN that will be carrying real-time traffic, what are two important reasons to consider serialization delay? (Choose two )
Which two conditions must be met for EIGRP to maintain an alternate loop-free path to a remote network? (Choose two.)
A network architect in an enterprise is designing a network policy for certain database applications. The goal of the policy is to allow these applications to access the internet directly, whereas other user and network applications that communicate with systems or users outside their own network must be routed through the data center. The focus is on achieving higher availability and a better user experience for the database applications, but switching between different network paths based on performance characteristics must be supported.
Which solution meets these requirements?
Retef to the exhibit.
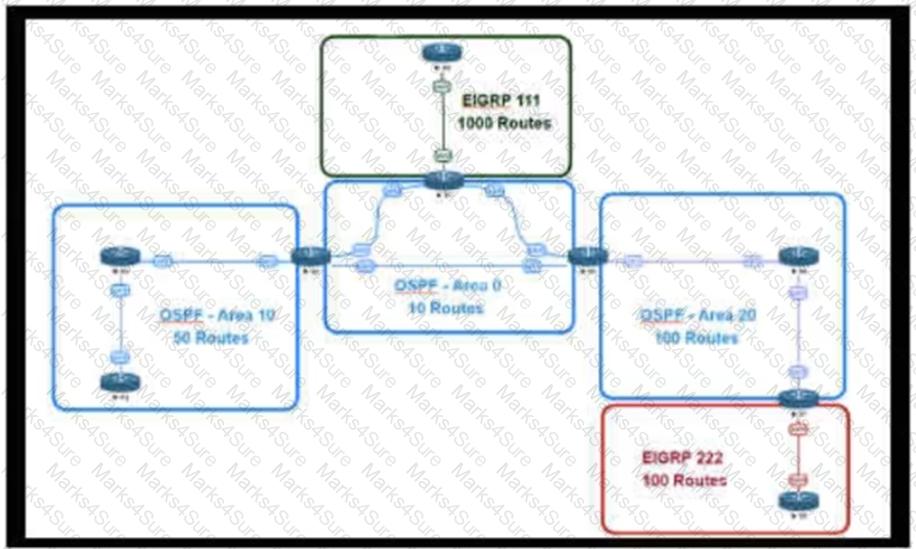
An engineer is designing a multiarea OSPF network for a client who also has a large EIGRP domain EIGRP routes are getting redistributed into OSPF ,OSPF area 20 has routers with limited memory and CPU resources The engineer wants to block routes from EIGRP 111 from propagating into area 20 and allow EIGRP 222 routes to How in Which OSPF area type fulfills this design requirement?
Company XYZ wants to use the FCAPS ISO standard for network management design. The focus of the design should be to minimize network outages by employing a set of procedures and activities to detect and isolate network issues and the appropriate corrective actions to overcome current issues and prevent them from occurring again. Which layer accomplishes this design requirement?
A large enterprise customer has a single router that uses two active/active 10-Mbps internet links in one of its
offices. Each link currently handles approximately 7 Mbps of traffic, which is close to the full link capacity.
When a link fails, the failure leads to significantly degraded performance of all applications. Static routing is
used. The current ISP cannot deliver additional bandwidth capacity on the existing links. The customer needs
a network design that is resistant to failure, but does not increase CAPEX. Which solution should be proposed
to the customer?
While access lists are generally associated with routers and firewalls, they can also be applied on layer 2 interfaces and to VLANs to provide granular security. Which are two benefits of using layer 2 access lists for segmentation? (Choose two.)
A service provider hires you to design its new managed CE offering to meet these requirements
• The CEs cannot run a routing protocol with the PE
• Provide the ability for equal or unequal ingress load balancing in dual-homed CE scenarios.
• Provide support for IPv6 customer routes
• Scale up to 250.000 CE devices per customer.
• Provide low operational management to scale customer growth.
• Utilize low-end (inexpensive) routing platforms for CE functionality.
Which tunneling technology do you recommend?
Refer to the exhibit.
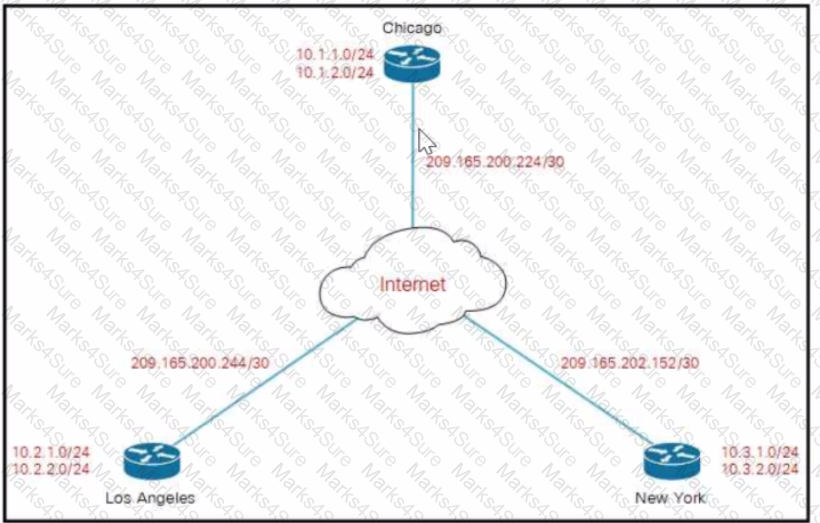
Company XYZ must design a DMVPN tunnel between the three sites Chicago is going to act as the NHS and the company wants DMVPN to detect peer endpoint failures Which technology should be used m the design?
A senior network designer suggests that you should improve network convergence times by reducing BGP timers between your CE router and the PE router of the service provider. Which two factors should you consider to adjust the timer values? (Choose two.)
The network designer needs to use GLOP IP addresses in order to make them unique within their ASN Which multicast address range should be used?
SDN emerged as a technology trend that attracted many industries to move from traditional networks to SDN. Which challenge is solved by SDN for cloud service providers?
VPLS is implemented in a Layer 2 network with 2000 VLANs. What is the primary concern to ensure successful deployment of VPLS?
You have been asked to design a high-density wireless network for a university campus. Which two principles would you apply in order to maximize the wireless network capacity? (Choose two.)
You want to mitigate failures that are caused by STP loops that occur before UDLD detects the failure or that are caused by a device that is no longer sending BPDUs. Which mechanism do you use along with UDLD?
An architect designs a multi-controller network architecture with these requirements:
Achieve fast failover to control traffic when controllers fail.
Yield a short distance and high resiliency in the connection between the switches and the controller.
Reduce connectivity loss and enable smart recovery to improve the SDN survivability.
Improve connectivity by adding path diversity and capacity awareness for controllers.
Which control plane component of the multi-controller must be built to meet the requirements?
A software-defined network can be defined as a network with an API that allows applications to understand and react to the state of the network in near real time. A vendor is building an SDN solution that exposes an API to the RIB and potentially the forwarding engine directly. The solution provides off-box processes with the capability to interact with the routing table in the same way as a distributed routing process. Which SDN framework model does the solution use?
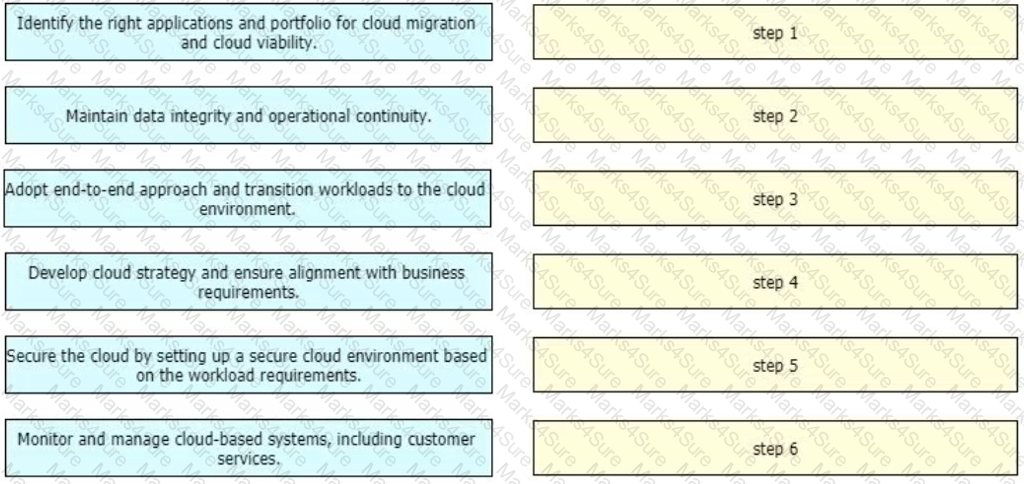
An enterprise wants to migrate an on-premises network to a cloud network, and the design team is finalizing the overall migration process. Drag and drop the options from the left into the correct order on the right.
An engineer must redesign the QoS strategy for Company XYZ The current network is experiencing many dropped packets due to oversubscription of the guaranteed bandwidth allocated by the service provider. Company XYZ wants a design with a QoS strategy that controls the traffic flow leaving the Edge router to minimize packet drops Which QoS technique can be recommended as a solution?
A network uses an SDN architecture with switches and a centralized controller What should be on the switches but not on the controller?
Router R1 is a BGP speaker with one peering neighbor over link "A". When the R1 link/interface "A" fails, routing announcements are terminated, which results in the tearing down of the state for all BGP routes at each end of the link. What is this a good example of?
Company XYZ wants design recommendations for Layer 2 redundancy (using Layer 2 technologies) The company wants to prioritize flexibility and scalability elements in the new design Which two technologies help meet these requirements'? (Choose two)
Your company utilizes many different types of network transports and you want to increase the efficiency of the network Which solution can be used to improve network efficiency over PPPoE IPsec, and GRE networks'?
The network designer needs to use GLOP IP address in order make them unique within their ASN, which
multicast address range will be considered?
Which two types of planning approaches are used to develop business-driven network designs and to facilitate the design decisions? (Choose two)
Which DCI technology utilizes a “flood and learn” technique to populate the Layer2 forwarding table?
It is often seen that companies pick a cloud vendor solely based on technical preferences without putting enough weight on the business strategies that are driving the cloud initiatives Which strategic requirement may come into play where it is more likely that the decision makers will look to leverage laaS over SaaS or PaaS?
You are using iSCSI to transfer files between a 10 Gigabit Ethernet storage system and a 1 Gigabit Ethernet server The performance is only approximately 700 Mbps and output drops are occurring on the server switch port. Which action will improve performance in a cost-effective manner?
While designing a switched topology, in which two options is UplinkFast recommended? (Choose two )
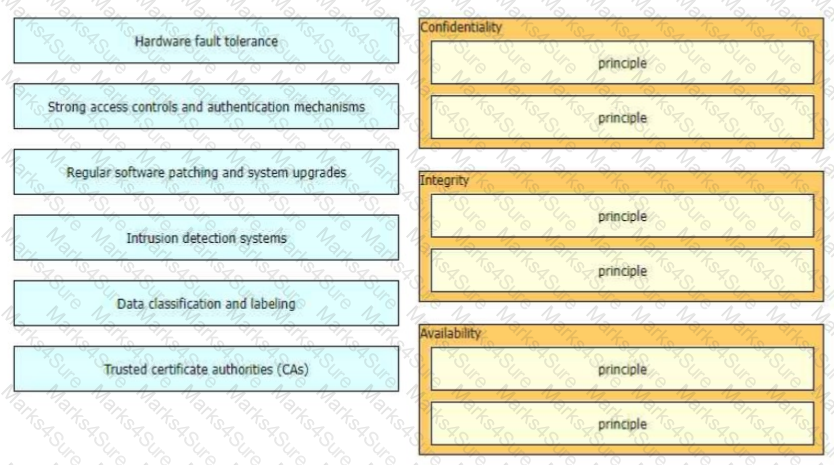
The CIA triad is foundational to information security, and one can be certain that one or more of the principles within the CIA triad has been violated when data is leaked or a system is attacked Drag and drop the countermeasures on the left to the appropriate principle section on the right in any order
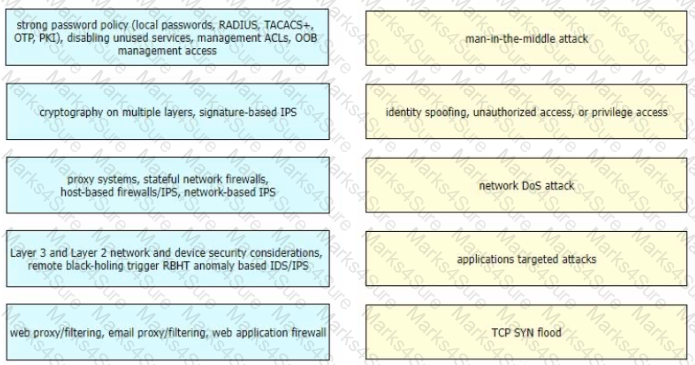
Drag and drop the correct mitigation methods from the left onto the corresponding types of attack on the right
Which solution component helps to achieve comprehensive threat protection and compliance for migration to multicloud SDX architectures?
Refer to the exhibit.
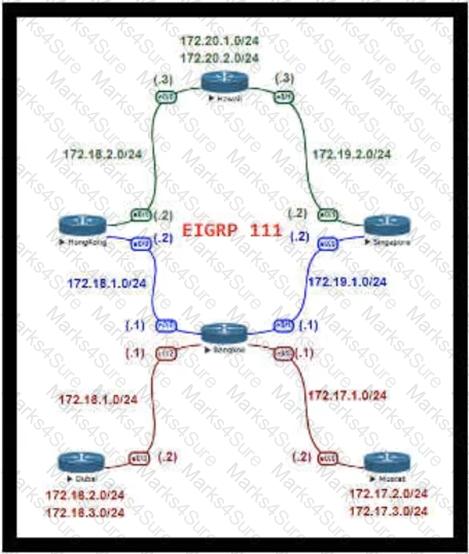
For Company XYZ Bangkok is using ECMP to reach the 172 20 2 0/24 network The company wants a design that would allow them to forward traffic from 172 16 2 0/24 toward 172 20 2 0/24 via the Singapore router as the preferred route The rest of the traffic should continue to use ECMP Which technology fulfills this design requirement?
A network architect must redesign a service provider edge, where multiservice and multitenant PEs are currently present. Which design feature should be minimized in the new design to achieve reliability?
Agile and Waterfall are two popular methods for organizing projects. What describes any Agile network design development process?
Refer to the exhibit.
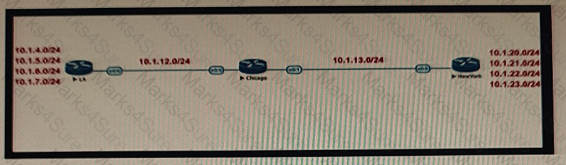
Company XYZ BGP topology is as shown in the diagram. The interface on the LA router connected toward the 10 1.5.0/24 network is faulty and is going up and down, which affects the entire routing domain. Which routing technique can the network administrator use so that the rest of the network is not affected by the flapping issue?
Company XYZ must design a strategy to protect their routers from DoS attacks, such as traffic destined to the router's own route processor, using separate control plane categories. Which two capabilities can be used to achieve this requirement? (Choose two.)
What are two advantages of controller-based networks versus traditional networks? (Choose two.)
Which two features control multicast traffic in a VLAN environment? (Choose two)
Company XYZ is planning to deploy primary and secondary (disaster recovery) data center sites. Each of these sites will have redundant SAN fabrics and data protection is expected between the data center sites. The sites are 100 miles (160 km) apart and target RPO/RTO are 3 hrs and 24 hrs, respectively. Which two considerations must Company XYZ bear in mind when deploying replication in their scenario? (Choose two.)
Which project management methodology is characterized by a having a low client
involvement?
Organizations that embrace Zero Trust initiatives ranging from business policies to technology infrastructure can reap business and security benefits. Which two domains should be covered under Zero Trust initiatives? (Choose two)
A thorough examination of the curant network infrastructure has revealed that several devices have an unusual high CPU load A traffic analysis indicates that control plane protocols and management traffic are affected as the devices are busy processing inbound traffic The networking team is working on updating their design for the entre network to handle situations like this Which feature or technology can be added to help mitigate the problem?
Which effect of using ingress filtering to prevent spoofed addresses on a network design is true?
Which layer of the SDN architecture orchestrates how the applications are given the resources available in the network?
Which two statements describe network automation and network orchestration? (Choose two.)
What are two top cloud-native security challenges faced by today's cloud-oriented organizations? (Choose two.)
What is a disadvantage of the traditional three-tier architecture model when east west traffic between different pods must go through the distribution and core layers?
An engineer is designing a DMVPN network where OSPF has been chosen as the routing protocol A spoke-to-spoke 'J
Which two design solutions ensure sub 50 msec of the convergence time after a link failure in the network?
(Choose two)
Which two statements describe the functionality of OSPF packet-pacing timers? (Choose two )
The group-pacing timer controls the interval that is used for group and individual LSA refreshment
The SD-WAN architecture is composed of separate orchestration management, control, and data planes Which activity happens at the orchestration plane?
Which two benefits can software defined networks provide to businesses? (Choose two.)
One of the approaches used in cloud bursting scenarios is distributed load-balanced, which operate the workloads in tandem between a public cloud and a data center In which way can the characteristics of distributed load-balancing be described?
Cost is often one of the motivators for a business to migrate from a traditional network to a software- defined network. Which design decision is directly influenced by CAPEX drivers?
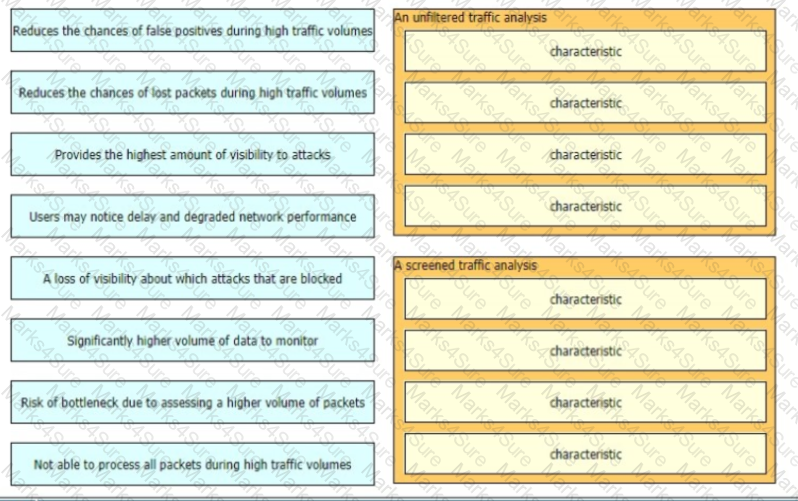
When a detection system for protecting a network from threats sourced from the Internet is designed there are two common deployment methods, where the system is placed differently relative to the perimeter firewall
•An unfiltered detection system examines the raw Internet data streams before it reaches the firewall
•A screened detection solution which monitors traffic that is allowed through the firewall Both have its advantages and disadvantages drag and drop the characteristics on the left to the corresponding category on the right in no particular order.
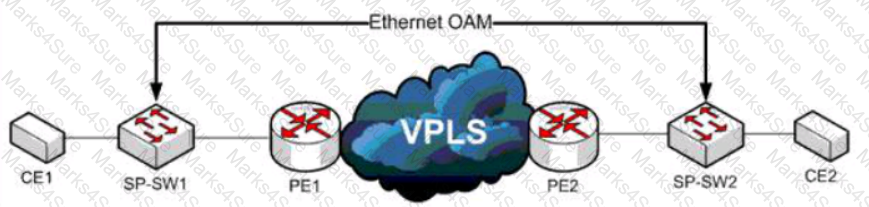
Refer to the exhibit A service provider has a requirement to use Ethernet OAM to detect end-to-end connectivity failures between SP-SW1 and SP- SW2 Which two ways to design this solution are true? (Choose two)
A BGP route reflector in the network is taking longer than expected to coverage during large network changes. Troubleshooting shows that the router cannot handle all the TCP acknowledgements during route updates. Which action can be performed to tune the device performance?
In a redundant hub and spoke "wheel" design, all spokes are connected to the hub, and spokes are connected to other spokes as well. During failure on one spoke link, the traffic from that site can be sent to a neighboring site for it to be forwarded to the hub site. But during peak hours, a link is overloaded and traffic is re-routed to a neighbor, which subsequently becomes overloaded. This overload results in network traffic oscillation as the load varies at each spoke site. This design provides more redundancy but not more resiliency because the routing protocol must process many alternate paths to determine the lowest cost path. Which two design
changes help to improve resilience in this case? (Choose two.)
As more links are added to the network, information and attributes related to the link is added to the control plane meaning every link that gets added will slow down the convergence of the control plane by some measurable amount of time. As a result when additional redundancy is built or added the MTTR will increase too Which risk increases along with the increased MTTR?
Refer to the exhibit.

The enterprise customer wants to stream one-way video from their head office to eight branch offices using multicast. Their current service provider provides a Layer3 VPN solution and manages the CE routers, but they do not currently support multicast. Which solution quickly allows this multicast traffic to go through while allowing for future scalability?
Drag and drop the design characteristics from the left onto the correct network filter techniques on the right. Not all options are used.

Company XYZ has 30 sites running a legacy private WAN architecture that connects to the Internet via multiple high- speed connections The company is now redesigning their network and must comply with these design requirements :
Use a private WAN strategy that allows the sites to connect to each other directly and caters for future expansion.
Use the Internet as the underlay for the private WAN.
Securely transfer the corporate data over the private WAN.
Which two technologies should be Incorporated into the design of this network? (Choose two.)