The major business applications of an enterprise are largely monolithic and hard-coded. As part of a major modernization and overhaul of the applications, the goal is to move to a modular and containerized application architecture model. At the same time, decoupling from the hardware is desired to move to an on-demand provisioning. However, the CyberOps team mandated that the final architecture must provide the same security levels as an air-gapped data center. Which cloud architecture meets these requirements?
Company XYZ wants to deploy OSPF. The design plan requires that two OSPF networks be mutually redistributed at multiple locations and ensure end-to-end connectivity to all of the company's networks. Which technology can be used to fulfill the requirements while avoiding the creation of routing loops?
A legacy enterprise is using a Service Provider MPLS network to connect its head office and branches. They want to extend the existing IP CCTV network to a new branch without routing changes or IP address changes. What is the best approach?
Hybrid cloud computing allows organizations to take advantage of public and private cloud models. Which best practice should organizations follow to ensure data security in the private cloud?
Company XYZ is in the process of identifying which transport mechanism(s) to use as their WAN technology. Their main two requirements are:
A technology that could offer DPI, SLA, secure tunnels, privacy, QoS, scalability, reliability, and ease of management.
A technology that is cost-effective.
Which WAN technology(ies) should be included in the design of company XYZ?
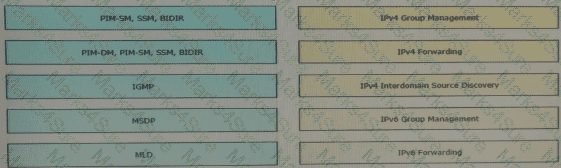
Drag and drop the multicast protocols from the left onto the current design situation on the right.
An attacker exploits application flaws to obtain data and credentials. What is the next step after application discovery in Zero Trust networking?
An enterprise network has two core routers that connect to 200 distribution routers and uses full-mesh IBGP peering between these routers as its routing method. The distribution routers are experiencing high CPU utilization due to the BGP process. Which design solution is the most cost effective?
Refer to the exhibit.
This network is running OSPF and EIGRP as the routing protocols. Mutual redistribution of the routing protocols has been configured on the appropriate ASBRs. The OSPF network must be designed so that flapping routes in EIGRP domains do not affect the SPF runs within OSPF. The design solution must not affect the way EIGRP routes are propagated into the EIGRP domains. Which technique accomplishes the requirement?
A customer migrates from a traditional Layer 2 data center network into a new SDN-based spine-and-leaf VXLAN EVPN data center within the same location. The networks are joined to enable host migration at Layer 2. Which activity should be completed each time a legacy network is migrated?
Refer to the diagram.
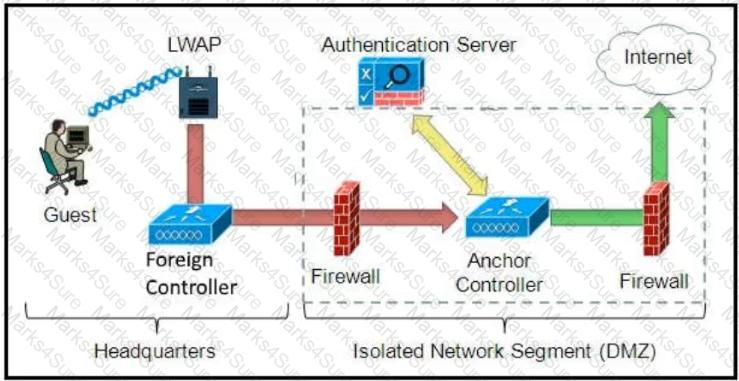
Which solution must be used to send traffic from the foreign wireless LAN controller to the anchor wireless LAN controller?
Which two design solutions ensure sub-50 msec of the convergence time after a link failure in the network? (Choose two)
Refer to the table.
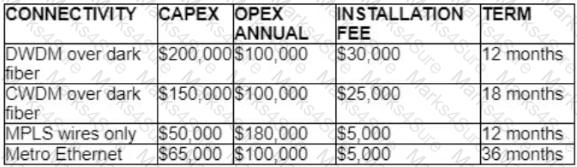
A customer investigates connectivity options for a DCI between two production data centers to aid a large-scale migration project. The migration is estimated to take 20 months to complete but might extend an additional 10 months if issues arise. All connectivity options meet the requirements to migrate workloads. Which transport technology provides the best ROI based on cost and flexibility?
Which two pain points are the most common for container technology adoption? (Choose two)
Company XYZ is designing their network using the three-layer hierarchical model. At which layer must the QoS design classify or mark the traffic?
Which two characteristics apply to firewall transparent mode operations in a firewall solution design? (Choose two.)
SDN emerged as a technology trend that attracted many industries to move from traditional networks to SDN. Which challenge is solved by SDN for cloud service providers?
SD-WAN can be used to provide secure connectivity to remote offices, branch offices, campus networks, data centers, and the cloud over any type of IP-based underlay transport network. Which two statements describe SD-WAN solutions? (Choose two.)
Company XYZ wants to prevent switch loops caused by unidirectional point-to-point link conditions on Rapid PVST+ and MST. Which technology can be used in the design to meet this requirement?
Two enterprise networks must be connected together. Both networks are using the same private IP addresses. The client requests from both sides should be translated using hide NAT (dynamic NAT) with the overload feature to save IP addresses from the NAT pools. Which design addresses this requirement using only one Cisco IOS NAT router for both directions?
Refer to the exhibit.
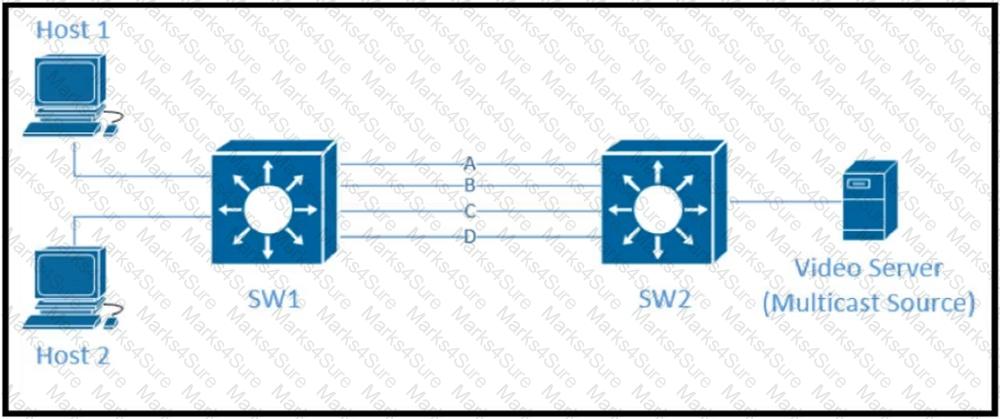
Traffic was equally balanced between Layer 3 links on core switches SW1 and SW2 before an introduction of the new video server in the network. This video server uses multicast to send video streams to hosts and now one of the links between core switches is overutilized. Which design solution solves this issue?
An architect designs a multi-controller network architecture with these requirements:
Achieve fast failover to control traffic when controllers fail.
Yield a short distance and high resiliency in the connection between the switches and the controller.
Reduce connectivity loss and enable smart recovery to improve the SDN survivability.
Improve connectivity by adding path diversity and capacity awareness for controllers.
Which control plane component of the multi-controller must be built to meet the requirements?
Company XYZ is designing the network for IPv6 security and they have these design requirements:
A switch or router must deny access to traffic from sources with addresses that are correct but topologically incorrect.
Devices must block Neighbor Discovery Protocol resolution for destination addresses not found in the binding table.
Which two IPv4 security features are recommended for this company? (Choose two)
Two routers R1 and R2 are directly connected through an Ethernet link. Both routers are running OSPF over the Ethernet link and OSPF has been registered with BFD. R1 has been set up to transmit BFD at a 50 ms interval, but R2 can receive only at a 100 ms rate due to platform limitations. What does this mean?
When consumers that leverage IaaS reach 100% resource capacity, what can be used to redirect the overflow of traffic to the public cloud so there is no disruption to service?
Which two factors provide multifactor authentication for secure access to applications and data? (Choose two.)
Company XYZ is migrating their existing network to IPv6. Some access layer switches do not support IPv6, while core and distribution switches fully support unicast and multicast routing. The company wants to minimize cost of the migration. Which migration strategy should be used?
A service provider recently migrated to an SD-WAN solution for delivering WAN connections to its customers. One of the main challenges with the SD-WAN deployment is that branch site volume increases every year, which causes management complexity. Which action resolves the issue?
Customer XYZ network consists of an MPLS core, IS-IS running as IGP, a pair of BGP route reflectors for route propagation, and a few dozen MPLS-TE tunnels for specific tactical traffic engineering requirements. The customer's engineering department has some questions about the use of the Overload Bit in the IS-IS networks and how it could be used to improve their current network design. Which two concepts about the Overload Bit are true? (Choose two.)
Company XYZ is running OSPF in their network. They have merged with another company that is running EIGRP as the routing protocol. Company XYZ now needs the two domains to talk to each other with redundancy, while maintaining a loop-free environment. The solution must scale when new networks are added into the network in the near future. Which technology can be used to meet these requirements?
A business wants to refresh its legacy Frame Relay WAN and consolidate product specialists via video in 200 branches. Which technology should be used?
You are designing the QoS policy for a company that is running many TCP-based applications. The company is experiencing tail drops for these applications. The company wants to use a congestion avoidance technique for these applications. Which QoS strategy can be used?
You have been tasked with designing a data center interconnect to provide business continuity. You want to encrypt the traffic over the DCI using IEEE 802.1AE MACsec to prevent the deployment of any firewall or IPS. Which two interconnect technologies support MACsec? (Choose two.)
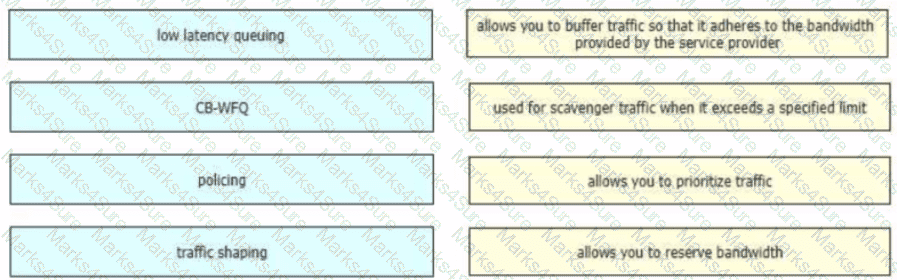
Drag and drop the QoS technologies from the left onto the correct capabilities on the right
Company XYZ has 30 sites running a legacy private WAN architecture that connects to the Internet via multiple high-speed connections. The company is now redesigning their network and must comply with these design requirements:
Use a private WAN strategy that allows the sites to connect to each other directly and caters for future expansion.
Use the Internet as the underlay for the private WAN.
Securely transfer the corporate data over the private WAN.
Which two technologies should be incorporated into the design of this network? (Choose two.)
Which two factors must be considered for high availability in campus LAN designs to mitigate concerns about unavailability of network resources? (Choose two.)
When an SDN-based model is used to transmit multimedia traffic, which aspect should an architect consider while designing the network?
Company XYZ is running SNMPv1 in their network and understands that it has some flaws. They want to change the security design to implement SNMPv3 in the network. Which network threat is SNMPv3 effective against?
Identity and access management between multiple users and multiple applications has become a mandatory requirement for Company XYZ to fight against ever-increasing cybersecurity threats. To achieve this, federated identity services have been deployed to provide Single Sign-On and Multi-Factor Authentication. Which protocol can be used by Company XYZ to provide authentication and authorization services?
If the desire is to connect virtual network functions together to accommodate different types of network service connectivity, what must be deployed?
Which two types of planning approaches are used to develop business-driven network designs and to facilitate the design decisions? (Choose two)
You want to split an Ethernet domain in two.
Which parameter must be unique in this design to keep the two domains separated?
A product manufacturing organization is integrating cloud services into their IT solution. The IT team is working on the preparation phase of the implementation approach, which includes the Define Strategy step. This step defines the scope of IT, the application, and the service. What is one topic that should be considered in the Define Strategy step?
A service provider hires you to design its new managed CE offering to meet these requirements:
The CEs cannot run a routing protocol with the PE.
Provide the ability for equal or unequal ingress load balancing in dual-homed CE scenarios.
Provide support for IPv6 customer routes.
Scale up to 250,000 CE devices per customer.
Provide low operational management to scale customer growth.
Utilize low-end (inexpensive) routing platforms for CE functionality.
Which tunneling technology do you recommend?
A banking customer determines that it is operating POS and POI terminals that are noncompliant with PCI DSS requirements, as it is running TLSv1.0. The customer plans to migrate the terminals to TLSv1.2. What are two requirements to complete the migration? (Choose two.)
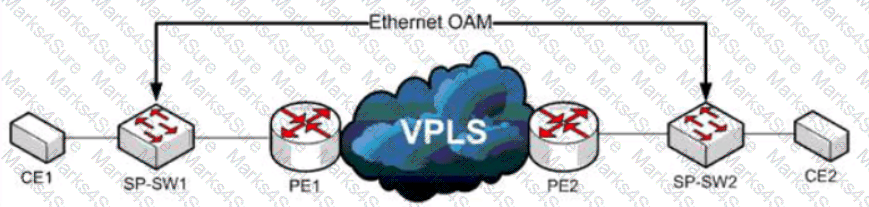
Refer to the exhibit. A service provider has a requirement to use Ethernet OAM to detect end-to-end connectivity failures between SP-SW1 and SP-SW2. Which two ways to design this solution are true? (Choose two)
Drag and drop the design characteristics from the left onto the correct network filter techniques on the right. Not all options are used.

A software-defined networking (SDN) controller learns network topology information by using BGP link-state sessions with the route reflectors of an MPLS-enabled network. The controller then uses the topology information to apply on-demand traffic policies to the network through a protocol that is supported from all Layer 3 routers. Each policy is represented as a RIB entry in the control plane of the router. Which SDN model has been implemented?
Which network management framework can be used to develop a network architecture that contains business requirements analysis, gap analysis, and network diagrams as artifacts to be used for design and implementation later?
A financial company requires that a custom TCP-based stock-trading application be prioritized over all other traffic for the business due to the associated revenue. The company also requires that VoIP be prioritized for manual trades. Which directive should be followed when a QoS strategy is developed for the business?
Refer to the exhibit.
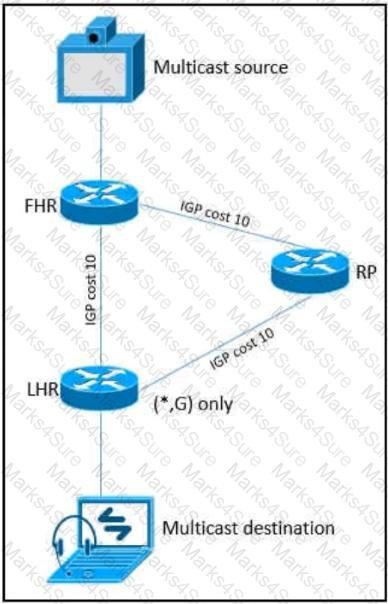
As part of a redesign project, you must predict multicast behavior. What happens to the multicast traffic received on the shared tree (*,G), if it is received on the LHR interface indicated?
Drag and drop the optical technology design characteristics on the left to the correct optical technologies on the right. Not all options are used

A multinational enterprise integrates a cloud solution with these objectives:
• Achieve seamless connectivity across different countries and regions
• Extend data center and private clouds into public clouds and provider-hosted clouds
What are two outcomes of deploying data centers and fabrics that interconnect different cloud networks? (Choose two.)
Refer to the table.
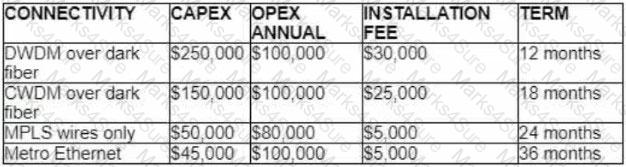
A customer investigates connectivity options for a DCI between two production data centers to aid a large-scale migration project. The solution must provide a single 10G connection between locations and be able to run its own varying QoS profiles without service provider interaction based on the migration stages. All connectivity methods are at 10 Gbps. Which transport technology costs the least if the connectivity is required for just one year?
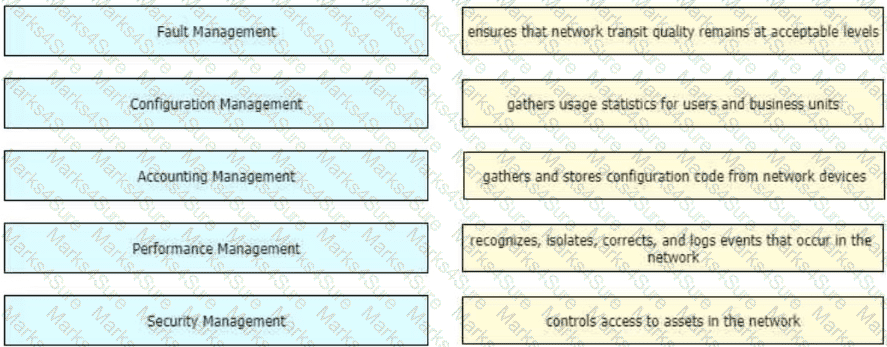
Drag and drop the FCAPS network management reference models from the left onto the correct definitions on the right.
What are two common approaches to analyzing and designing networks? (Choose two.)
In outsourced IT services, the RTO is defined within the SLA. Which two support terms are often included in the SLA by IT and other service providers? (Choose two.)
Refer to the exhibit.
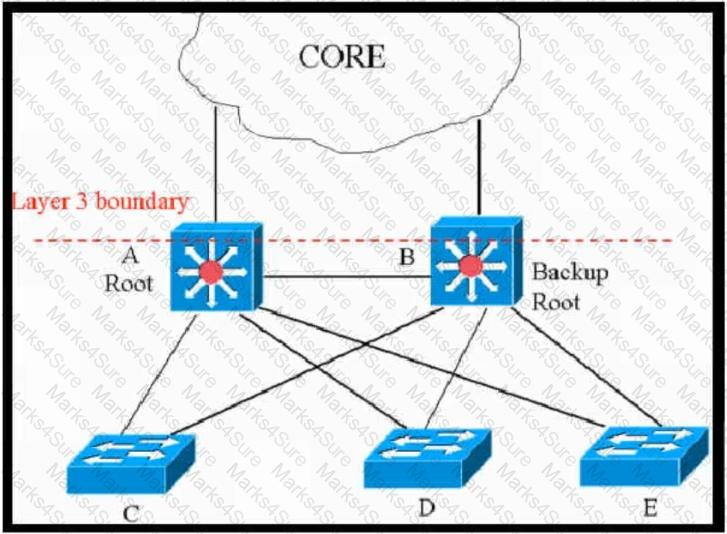
This network is running legacy STP 802.1d. Assuming "hello_timer" is fixed to 2 seconds, which parameters can be modified to speed up convergence times after single link/node failure?
A consultant needs to evaluate project management methodologies for a new service deployment on the existing network of a customer. The customer wants to be involved in the end-to-end project progress and be provided with frequent updates. The customer also wants the ability to change the requirements if needed, as the project progresses. Which project management methodology should be used?
A company uses equipment from multiple vendors in a data center fabric to deliver SDN, enable maximum flexibility, and provide the best return on investment. Which YANG data model should be adopted for comprehensive features to simplify and streamline automation for the SDN fabric?
Company XYZ wants to redesign the Layer 2 part of their network to use all uplinks for increased performance, support host reachability with conversational learning, and avoid port-channels. Which other technique can be used?
Which two features are advantages of SD-WAN compared to MPLS-based connectivity? (Choose two.)
An engineer is designing a DMVPN network where OSPF has been chosen as the routing protocol. A spoke-to-spoke data propagation model must be set up. Which two design considerations must be taken into account? (Choose two)
Retef to the exhibit.
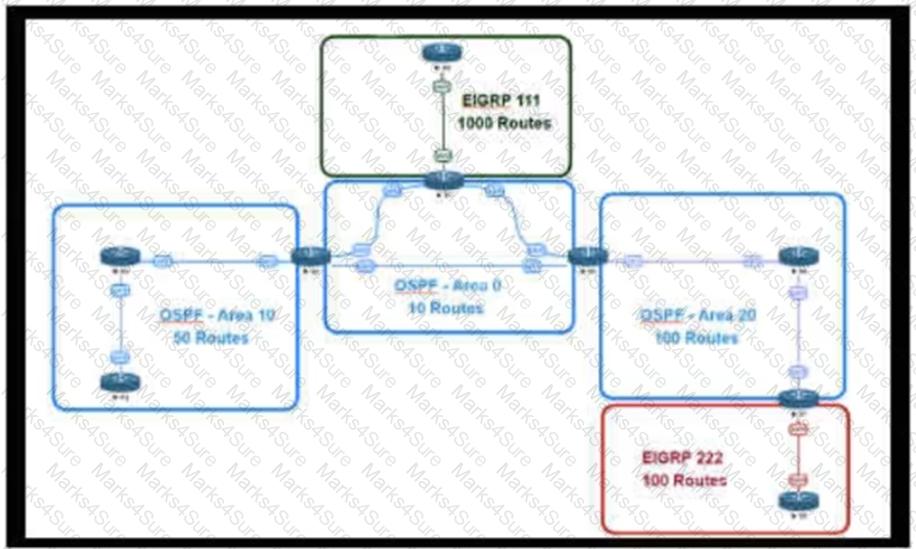
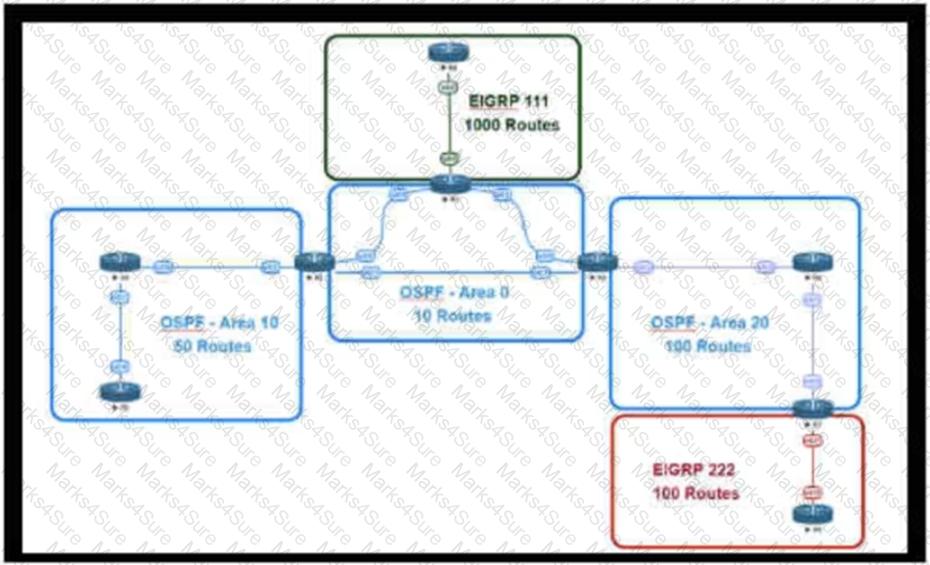
An engineer is designing a multiarea OSPF network for a client who also has a large EIGRP domain. EIGRP routes are getting redistributed into OSPF. OSPF area 20 has routers with limited memory and CPU resources. The engineer wants to block routes from EIGRP 111 from propagating into area 20 and allow EIGRP 222 routes to flow in. Which OSPF area type fulfills this design requirement?
Which two benefits can software defined networks provide to businesses? (Choose two.)
Refer to the exhibit.
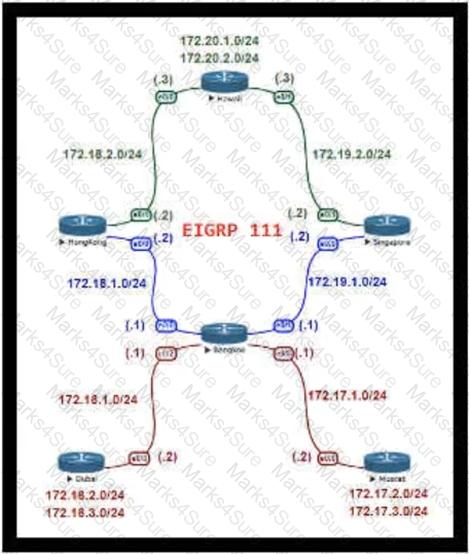
For Company XYZ, Bangkok is using ECMP to reach the 172.20.2.0/24 network. The company wants a design that would allow them to forward traffic from 172.16.2.0/24 toward 172.20.2.0/24 via the Singapore router as the preferred route. The rest of the traffic should continue to use ECMP. Which technology fulfills this design requirement?
A large enterprise is planning a new WAN connection to headquarters. The current dual-homed setup with static routing is not providing consistent resiliency. Users complain when one specific link fails, while failure of the other causes no issues. The organization wants to improve resiliency and ROI.
Which solution should be recommended?
A network security team uses a purpose-built tool to actively monitor the campus network, applications, and user activity. The team also analyzes enterprise telemetry data from IPFIX data records that are received from devices in the campus network. Which action can be taken based on the augmented data?
Refer to the exhibit.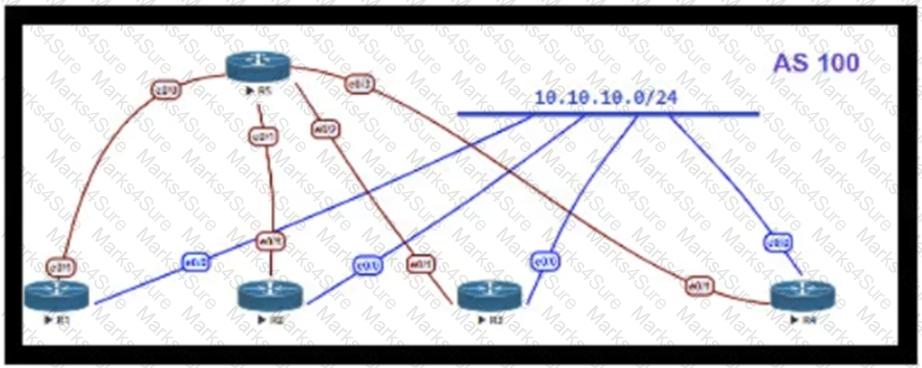
OSPF is running as the IGP to provide reachability to all AS100 networks. R3 and R4 are the current ABRs at the boundary of OSPF Area 0 and Area 1. Now BGP must be deployed within AS 100 because it will be receiving Internet routes from its eBGP peers (the service provider) connected to R1 and R2. What is an optimal solution for this deployment to configure BGP relationships and redistribute BGP learned routes into OSPF?
An enterprise wants to provide low-cost delivery of network systems that can be scaled on business demand, followed by an initiative to reduce capital expenses for new IT equipment. Which technology meets these goals?
Which two statements explain the operation of BFD asynchronous mode? (Choose two.)
Refer to the exhibit.
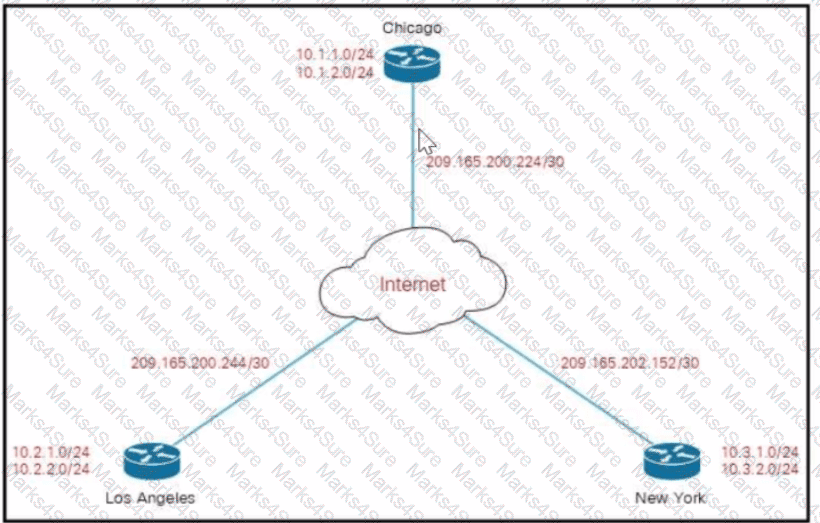
Company XYZ must design a DMVPN tunnel between the three sites. Chicago is going to act as the NHS, and the company wants DMVPN to detect peer endpoint failures. Which technology should be used in the design?
How must the queue sizes be designed to ensure that an application functions correctly?
A network architect is designing a policy where database applications access the internet directly, while other traffic routes through the data center, with dynamic path switching based on performance. Which solution meets these requirements?
Sometimes SDN leverages various overlay networking technologies to create layer(s) of network abstraction. What describes an overlay network?
Organizations that embrace Zero Trust initiatives ranging from business policies to technology infrastructure can reap business and security benefits. Which two domains should be covered under Zero Trust initiatives? (Choose two)
A healthcare customer requested that SNMP traps must be sent over the MPLS Layer 3 VPN service. Which protocol must be enabled?
Which two features describe controller-based networking solutions compared to traditional networking solutions? (Choose two.)
Which two mechanisms avoid suboptimal routing in a network with dynamic mutual redistribution between multiple OSPFv2 and EIGRP boundaries? (Choose two.)
An engineer must design a network for a company that uses OSPF LFA to reduce loops. Which type of loop would be reduced by using this design?
You are using iSCSI to transfer files between a 10 Gigabit Ethernet storage system and a 1 Gigabit Ethernet server. The performance is only approximately 700 Mbps and output drops are occurring on the server switch port. Which action will improve performance in a cost-effective manner?
Which protocol does an SD-Access wireless Access Point use for its fabric data plane?
Company XYZ needs advice in redesigning their legacy Layer 2 infrastructure. Which technology should be included in the design to minimize or avoid convergence delays due to STP or FHRP and provide a loop-free topology?
The General Bank of Greece plans to upgrade its legacy end-of-life WAN network with a new flexible, manageable, and scalable solution. The main requirements are ZTP support, end-to-end encryption, application awareness, and segmentation. The CTO states that the main goal of the bank is CAPEX reduction. Which WAN technology should be used for the solution?
An international media provider faces challenges managing deployed services with a homegrown orchestration system. Which platform is well-suited as a state-aware orchestration system?
The network designer needs to use GLOP IP addresses to make them unique within their ASN. Which multicast address range will be considered?
Your company wants to deploy a new data center infrastructure. Based on the requirements you have chosen VXLAN as encapsulation technology. The customer is concerned about misconfiguration of Layer 2 devices and DC-wide outages caused by Layer 2 loops. What do you answer?
Company XYZ has a multicast domain that spans across multiple autonomous systems. The company wants a simplified and controlled approach to interconnecting multicast domains. Which technology is the best fit?
Which three items do you recommend for control plane hardening of an infrastructure device? (Choose three.)