What is the primary benefit of the Federated Learning approach to machine learning?
You are developing a prediction model. Your team indicates they need an algorithm that is fast and requires low memory and low processing power. Assuming the following algorithms have similar accuracy on your data, which is most likely to be an ideal choice for the job?
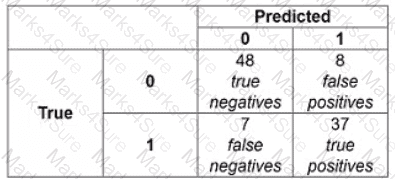
The following confusion matrix is produced when a classifier is used to predict labels on a test dataset. How precise is the classifier?
Which of the following can take a question in natural language and return a precise answer to the question?
Which of the following tests should be performed at the production level before deploying a newly retrained model?
Which of the following text vectorization methods is appropriate and correctly defined for an English-to-Spanish translation machine?
You are building a prediction model to develop a tool that can diagnose a particular disease so that individuals with the disease can receive treatment. The treatment is cheap and has no side effects. Patients with the disease who don't receive treatment have a high risk of mortality.
It is of primary importance that your diagnostic tool has which of the following?
Which of the following describes a neural network without an activation function?
Which three security measures could be applied in different ML workflow stages to defend them against malicious activities? (Select three.)
For each of the last 10 years, your team has been collecting data from a group of subjects, including their age and numerous biomarkers collected from blood samples. You are tasked with creating a prediction model of age using the biomarkers as input. You start by performing a linear regression using all of the data over the 10-year period, with age as the dependent variable and the biomarkers as predictors.
Which assumption of linear regression is being violated?
You train a neural network model with two layers, each layer having four nodes, and realize that the model is underfit. Which of the actions below will NOT work to fix this underfitting?
Which of the following sentences is TRUE about the definition of cloud models for machine learning pipelines?
Which of the following statements are true regarding highly interpretable models? (Select two.)
Which of the following scenarios is an example of entanglement in ML pipelines?
Which type of regression represents the following formula: y = c + b*x, where y = estimated dependent variable score, c = constant, b = regression coefficient, and x = score on the independent variable?
In which of the following scenarios is lasso regression preferable over ridge regression?
Which two of the following statements about the beta value in an A/B test are accurate? (Select two.)
Which two of the following decrease technical debt in ML systems? (Select two.)
What is the open framework designed to help detect, respond to, and remediate threats in ML systems?
You have a dataset with thousands of features, all of which are categorical. Using these features as predictors, you are tasked with creating a prediction model to accurately predict the value of a continuous dependent variable. Which of the following would be appropriate algorithms to use? (Select two.)