are events that may indicate that an organization's systems or data have been compromised or that measures put in place to protect them have failed
6 Which access control method uses attributes and rules to define access policies that are evaluate by a central Policy Decision Point (PDP)
Access control used in in high-security situations such as military and government organizations.
provide integrity services that allow a recipient to verify that a message has not been altered.
Which access control model grants permission based on the sensitivity of the data and the user job functions
What kind of control is, when we add a backup firewall that takes over if the main one stops working?
Set of rules that everyone must comply with and usually carry monetary penalties for noncompliance
In which of the following phases of an incident recovery plan the incident responses prioritized
Communication between end systems is encrypted using a key, often known as________?
Mark works in the security office. During research, Mark learns that a configuration change could better protect the organization's IT environment. Mark makes a proposal for this change, but the change cannot be implemented until it is approved, tested, and then cleared for deployment by the Change Control Board. This is an example of__________
Why is the recovery of IT often crucial to the recovery and sustainment of business operations
A Hacker launched a specific attack to exploit a known system vulnerability. What term best describes this situation?
Exhibit.
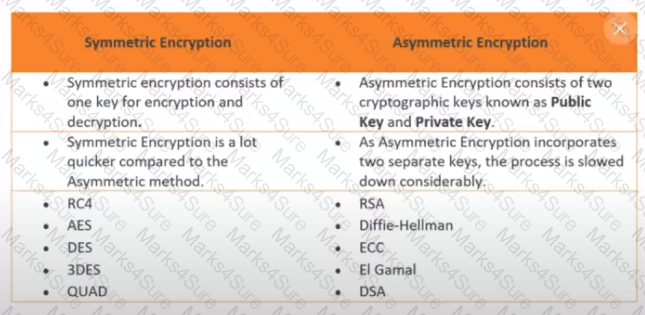
How many keys would be required to support 50 users in an asymmetric cryptography system?
Which protocol would be most suitable to fulfill the secure communication requirements between clients and the server for a company deploying a new application?
Which one of the following cryptographic algorithms does not depend upon the prime factorization problem?
Which term describes a communication tunnel that provides point-to-point transmission of both authentication and data traffic over an untrusted network?
Natalia is concerned about the security of his organization's domain name records and would like to adopt a technology that ensures their authenticity by adding digital signatures. Select the MOST appropriate technology to use?
What is the term used to denote the inherent set of privileges assigned to a user upon the creation of a new account?
Networks are often micro segmented networks, with firewalls at nearly every connecting point
Raj is considering a physical deterrent control to dissuade unauthorized people from entering the organization's property. Which of the following would serve this purpose?
COVID-19 is one of the perfect example of a situation, where a________plan is
enacted to sustain the business
A organization's security system which involves in preventing, detecting, analyzing, and responding to cybersecurity incidents.
Mark has purchased a MAC LAPTOP. He is scared of losing his screen and planning to buy an insurance policy. So, which risk management strategy is?
Which version of TLS is considered to be the most secure and recommended for use?
Which of the following best describes the puposes of a business impact analysis?
A hacker gains access to an organization system without authorization and steal confidential data. What term best describes this ?
Permitting authorized access to information while protecting it from improper disclosure
A company needs to protect its confidential data from unauthorized access which logical control is best suited for this scenario
DevOps team has updated the application source code, Tom has discovered that many unauthorized changes have been made. What is the BEST control Tom can implement to prevent a recurrence of this problem?
After an Earthquake disrupting business operations, which documents contains the reactive procedures required to return business to normal operations
Devid's team recently implemented a new system that gathers information from a variety of different log sources, analyses that information, and then triggers automated playbooks in response to security events, what term BEST describes this technology?
Measure of the extent to which an entity is threatened by a potential circumstance or event and likelihood of occurrence
An employee unintentionally shares confidential information with an unauthorized party. What term best describes this situation?
What are the primary responsibilities of a computer incident response team (CIRT) during an incident?
What is a type of system architecture where a single instance can serve multiple distinct user groups.
Also known as a virtual machine monitor or VMM, is software that creates and runs virtual machines (VMs)
The documentation of a predetermined set of instructions or procedures to detect, respond to andlimit consequences of a malicious cyberattack against an organization's information systems(s).
Often offered by third-party organizations and cover specific
advisory or compliance objectives.
System capabilities designed to detect and prevent the unauthorized use and transmission of information.
The requirement of both the manager and the accountant to approve the transaction fund exceeding $ 50000. Which security concept best suits this
Mark is configuring an automated data transfer between two hosts and is choosing an authentication technique for one host to connect to the other host. What approach would be best-suited for this scenario?
The prevention of authorized access to resources or the delaying of time-critical operations. (Time-critical may be milliseconds or it may be hours, depending upon the service provided.)
A security event, or combination of security events, that constitutes a secu incident in which an intruder gains, or attempts to gain, access to a system or system resource without authorization
Which type of control is used to minimize the impact of an attack and to restore normal operations as quick as possible
A set of instructions to help IT staff detect, respond to, and recover from network security incidents?
The method of distributing network traffic equally across a pool of resources that support an application
Devid's team recently implemented a new system that gathers information from a variety of different log sources, analyses that information, and then triggers automated playbooks in response to security events, what term BEST describes this technology?
Which Prevent crime by designing a physical environment that positively influences human behavior.
Which type of control is used to restore systems or processes to their normal state after an attack has occurred
Dani is an ISC2 member and an employee of New Corporation. One of Dani's colleagues offers to share a file that contains an illicit copy of a newly released movie. What should Dani do
Which type of attack attempts to gain information by observing the devices power consumption
John was recently offered a consulting opportunity as a side job. He is concerned that this might constitute a conflict of interest. Which one of the following sources that he needs to refer to take an appropriate decision?
Actions, processes and tools for ensuring an organization can continue critical operations during a contingency.
What is the difference between business continuity planning and disaster recovery planning?
A cybercrime in which the attacker floods a server with internet traffic to prevent users from accessing connected online services and sites
Which penetration testing technique requires the team to do the MOST work and effort?
A company security team detected a cyber attack against it information systems and activates a set of procedures to mitigate the attack., What type of plan is this?
allows for extremely granular restrictions within the IT environment, to the
point where rules can be applied to individual machines and/or users,
Which type of database combines related records and fields into a logical tree structure?
The common term used to describe the mechanisms that control the temperature and humidity in a data center
Created by switches to logically segment a network without altering its physical topology.
EKristal is the security administrator for a large online service provider. Kristal learns that the company is harvesting personal data of its customers and sharing the data with local governments where the company operates, without the knowledge of the users, to allow the governments to persecute users on the basis of their political and philosophical beliefs. The published user agreement states that the company will not share personal user data with any entities without the users' explicit permission. According to the ISC2 Code of Ethics, to whom does Kristal ultimately report in this situation?
What type of attack does the attacker store and reuse login information. Select the BEST answer?
A measure of the degree to which an organization depends on the information or information system for the success of a mission or of a business function.
What cybersecurity principle focuses on granting users only the privileges necessary to perform their job functions?
Finance Server and Transactions Server has restored its original facility after a disaster, what should be moved in FIRST?