A SaaS company is launching a new product based in a cloud environment. The new product will be provided as an API and should not be exposed to the internet. Which of the following should the company create to best meet this requirement?
An administrator needs to add a device to the allow list in order to bypass user authentication of an AAA system. The administrator uses MAC filtering and needs to discover the device's MAC address to accomplish this task. The device receives an IP address from DHCP, but the IP address changes daily. Which of the following commands should the administrator run on the device to locate its MAC address?
A partner is migrating a client from on-premises to a hybrid cloud. Given the following project status information, the initial project timeline estimates need to be revised:

(Refer to image: Phases like Discovery, Design, Implementation, and Knowledge Transfer have all exceeded their initial estimated timelines.)
Which of the following documents needs to be revised to best reflect the current status of the project?
A network architect is creating a network topology for a global SD-WAN deployment. The business has offices in Asia, Europe, and the United States and makes use of data centers in theUnited States and Europe. Most traffic between sites must have the lowest latency possible. Which of the following topologies best meets this requirement?
Server A (10.2.3.9) needs to access Server B (10.2.2.7) within the cloud environment since theyare segmented into different network sections. All external inbound traffic must be blocked to those servers. Which of the following need to be configured to appropriately secure the cloud network? (Choose two.)
A network administrator recently deployed new Wi-Fi 6E access points in an office and enabled 6GHz coverage. Users report that when they are connected to the new 6GHz SSID, the performance is worse than the 5GHz SSID. The network administrator suspects that there is a source of 6GHz interference in the office. Using the troubleshooting methodology, which of the following actions should the network administrator do next?
A network architect must design a new branch network that meets the following requirements:
No single point of failure
Clients cannot be impacted by changes to the underlying medium
Clients must be able to communicate directly to preserve bandwidth
Which of the following network topologies should the architect use?
A cafe uses a tablet-based point-of-sale system. Customers are complaining that their food is taking too long to arrive. During an investigation, the following is noticed:
Every kitchen printer did not print the orders
Payments are processing correctly
The cloud-based system has record of the orders
This issue occurred when the cafe was busy
Which of the following is the best way to mitigate this issue?
A cloud architect must recommend an architecture approach for a new medical application that requires the lowest downtime possible. Which of the following is the best application deployment strategy given the high-availability requirement?
A company provides an API that runs on the public cloud for its customers. A fixed number of VMs host the APIs. During peak hours, the company notices a spike in usage that results in network communication speeds slowing down for all customers. The management team has decided that access for all customers should be fair and accessible at all times. Which of the following is the most cost-effective way to address this issue?
A network engineer identified several failed log-in attempts to the VPN from a user's account. When the engineer inquired, the user mentioned the IT help desk called and asked them to change their password. Which of the following types of attacks occurred?
A network architect is designing a solution to secure the organization's applications based on the security policy. The requirements are:
Users must authenticate using one set of credentials.
External users must be located in authorized sites.
Session timeouts must be enforced.
Network access requirements should be changed as needed.
Which of the following best meet these requirements? (Choose two.)
A company deployed new applications in the cloud and configured a site-to-site VPN to connect the internal data center with the cloud. The IT team wants the internal servers to connect to those applications without using public IP addresses. Which of the following is the best solution?
A company is expanding its network and needs to ensure improved stability and reliability. The proposed solution must fulfill the following requirements:
Detection and prevention of network loops
Automatic configuration of ports
Standard protocol (not proprietary)
Which of the following protocols is the most appropriate?
An organization's Chief Technical Officer is concerned that changes to the network using IaC are causing unscheduled outages. Which of the following best mitigates this risk?
A network administrator is troubleshooting a user's workstation that is unable to connect to the company network. The results of ipconfig and arp -a are shown. The user’s workstation:

A router on the same network shows the following output:
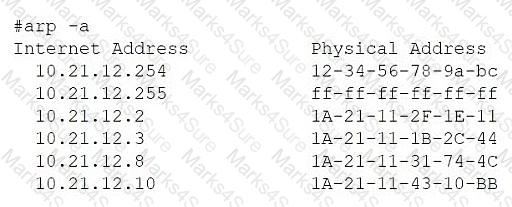
Has an IP address of 10.21.12.8
Has subnet mask 255.255.255.0
Default gateway is 10.21.12.254
ARP table shows 10.21.12.8 mapped to 1A-21-11-31-74-4C (a different MAC address than the local adapter)
A customer asks a MSP to propose a ZTA (Zero Trust Architecture) design for its globally distributed remote workforce. Given the following requirements:
Authentication should be provided through the customer's SAML identity provider.
Access should not be allowed from countries where the business does not operate.
Secondary authentication should be added to the workflow to allow for passkeys.
Changes to the user's device posture and hygiene should require reauthentication into the network.
Access to the network should only be allowed to originate from corporate-owned devices.
Which of the following solutions should the MSP recommend to meet the requirements?
A network administrator receives a ticket from one of the company's offices about video calls that work normally for one minute and then get very choppy. The network administrator pings the video server from that site to ensure that it is reachable:
(Ping output shows responses with varying latency times, including spikes: 11ms, 672ms, 849ms, 92ms, etc.)

Which of the following is most likely the cause of the video call issue?
As part of a project to modernize a sports stadium and improve the customer service experience for fans, the stadium owners want to implement a new wireless system. Currently, all tickets are electronic and managed by the stadium mobile application. The new solution is required to allow location tracking precision within 5ft (1.5m) of fans to deliver the following services:
Emergency/security assistance
Mobile food order
Event special effects
Raffle winner location displayed on the giant stadium screen
Which of the following technologies enables location tracking?
A network architect is designing an expansion solution for the branch office network and requires the following business outcomes:
Maximize cost savings with reduced administration overhead
Easily expand connectivity to the cloud
Use cloud-based services to the branch offices
Which of the following should the architect do to best meet the requirements?
A network engineer is installing new switches in the data center to replace existing infrastructure. The previous network hardware had administrative interfaces that were plugged into the existing network along with all other server hardware on the same subnet. Which of the following should the engineer do to better secure these administrative interfaces?
A company is experiencing numerous network issues and decides to expand its support team. The new junior employees will need to be onboarded in the shortest time possible and be able to troubleshoot issues with minimal assistance. Which of the following should the company create to achieve this goal?