A cloud administrator needs to collect process-level, memory-usage tracking for the virtual machines that are part of an autoscaling group. Which of the following is the best way to
accomplish the goal by using cloud-native monitoring services?
A project manager must determine how ideas from the organization and results from the review committee should move through the enterprise for a new project. Which of the following does the project manager need to do?
Which of the following is a field of computer science that enables computers to identify and understand objects and people in images and videos?
Which of the following vulnerability management concepts is best defined as the process of discovering vulnerabilities?
A DevOps engineer is performing maintenance on the mail servers for a company's web application. Part of this maintenance includes checking core operating system updates. The servers are currently running version 3.2 of the operating system. The engineer has two update options—one to version 4.1 and the other to version 3.7. Both versions are fully supported by the operating system manufacturer. Which of the following best describes the action the engineer should take?
Which of the following is the most cost-effective way to store data that is infrequently accessed?
Which of the following will best reduce the cost of running workloads while maintaining the same performance? (Select two).
A project manager is reviewing quality planning techniques. Which of the following involves comparing results of similar activities?
A project team that handles sensitive data analysis recently onboarded three new employees. Which of the following should the PM do first?
A cloud engineer wants to run a script that increases the volume storage size if it is below 100GB. Which of the following should the engineer run?

A software engineer notices that the newest update to the reporting software includes many new features that were not defined in the requirements document. Which of the following steps should the engineer take next?
A cloud solutions architect needs to have consistency between production, staging, and development environments. Which of the following options will best achieve this goal?
A cloud developer is creating a static website that customers will be accessing globally. Which of the following services will help reduce latency?
A company wants to implement a work environment that will have low operational overhead and highly accessible enterprise resource planning, email, and data resources. Which of
the following cloud service models should the company implement?
A developer is testing code that will be used to deploy a web farm in a public cloud. The main code block is a function to create a load balancer and a loop to create 1.000 web servers, as shown below:

The developer runs the code against the company's cloud account and observes that the load balancer is successfully created, but only 100 web servers have been created. Which of the following should the developer do to fix this issue?
A cloud engineer is designing a cloud-native, three-tier application. The engineer must adhere to the following security best practices:
• Minimal services should run on all layers of the stack.
• The solution should be vendor agnostic.
• Virealization could be used over physical hardware.
Which of the following concepts should the engineer use to design the system to best meet these requirements?
A project manager is taking notes along with gathering feedback about a prior project in order to consider known issues with a project enhancement. Which of the following best describes the plan that the project team is working on?
A network administrator is budding a site-to-site VPN tunnel from the company's headquarters office 10 the company's public cloud development network. The network administrator confirms the following:
The VPN tunnel is established on the headquarter office firewall.
While inside the office, developers report that they cannot connect to the development network resources.
While outside the office on a client VPN, developers report that they can connect to the development network resources.
The office and the client VPN have different IP subnet ranges.
The firewall flow logs show VPN traffic is reaching the development network from the office.
Which of the following is the next step the next network administrator should take to troubleshoot the VPN tunnel?
The change control board received a request to approve a configuration change 10 deploy in the cloud production environment. Which of the following should have already been competed?
A project sponsor has asked for a log listing all the bugs identified within a specific project. Which of the following tools should the project manager provide to the sponsor?
Which of the following best describes why a project manager would decide to sign a fixed-price contract with a vendor?
An e-commerce store is preparing for an annual holiday sale. Previously, this sale has increased the number of transactions between two and ten times the normal level of
transactions. A cloud administrator wants to implement a process to scale the web server seamlessly. The goal is to automate changes only when necessary and with minimal cost.
Which of the following scaling approaches should the administrator use?
A cloud administrator shortens the amount of time a backup runs. An executive in the company requires a guarantee that the backups can be restored with no data loss. Which of th€ following backup features should the administrator lest for?
A company operates a website that allows customers to upload, share, and retain full ownership of their photographs. Which of the following could affect image ownership as the website usage expands globally?
Which of the following network protocols is generally used in a NAS environment?
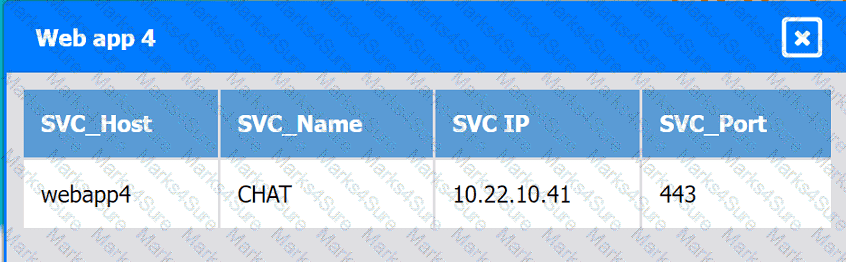
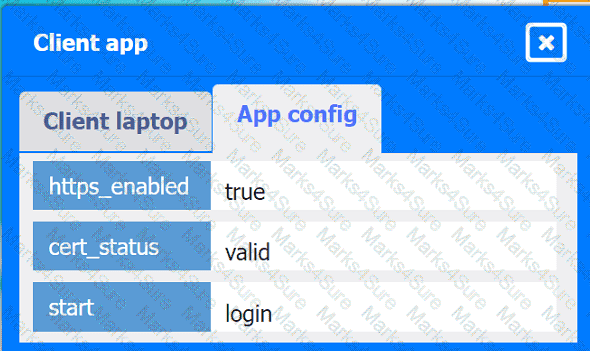
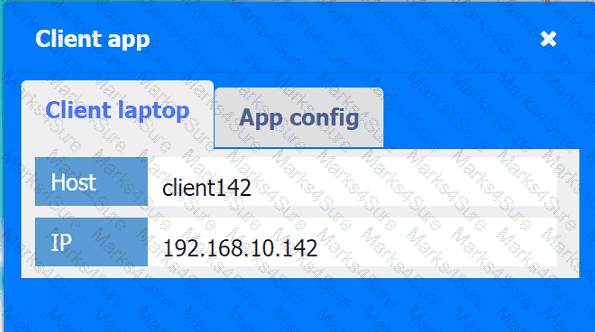
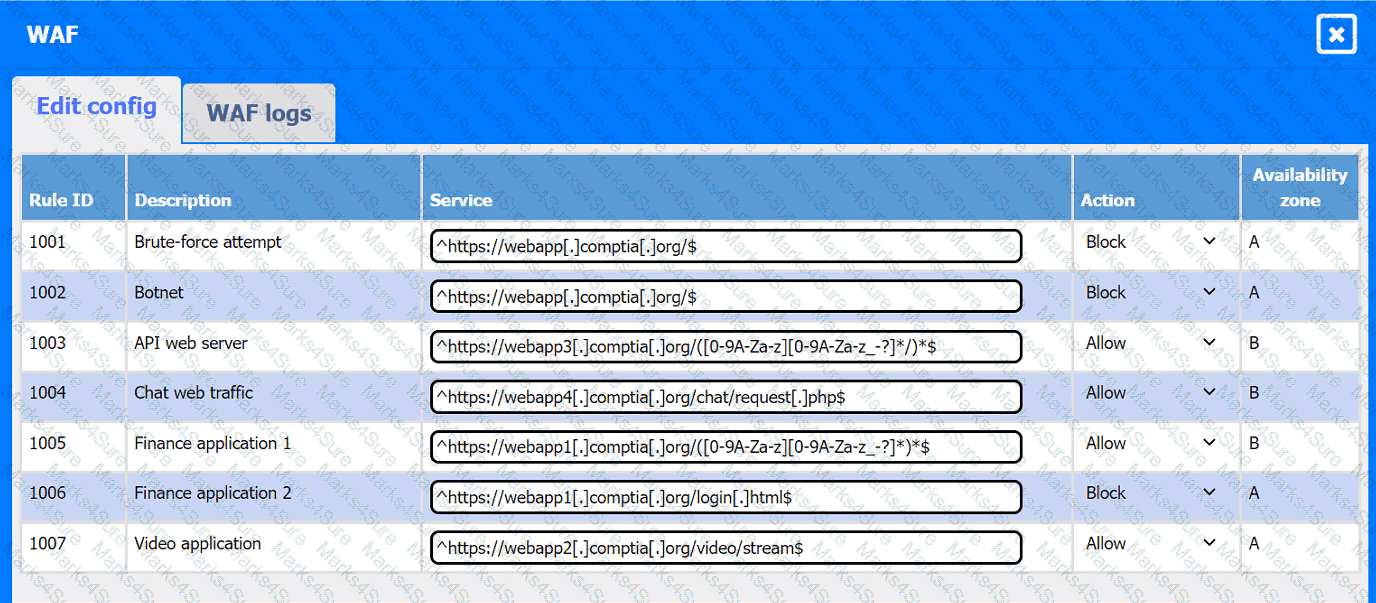
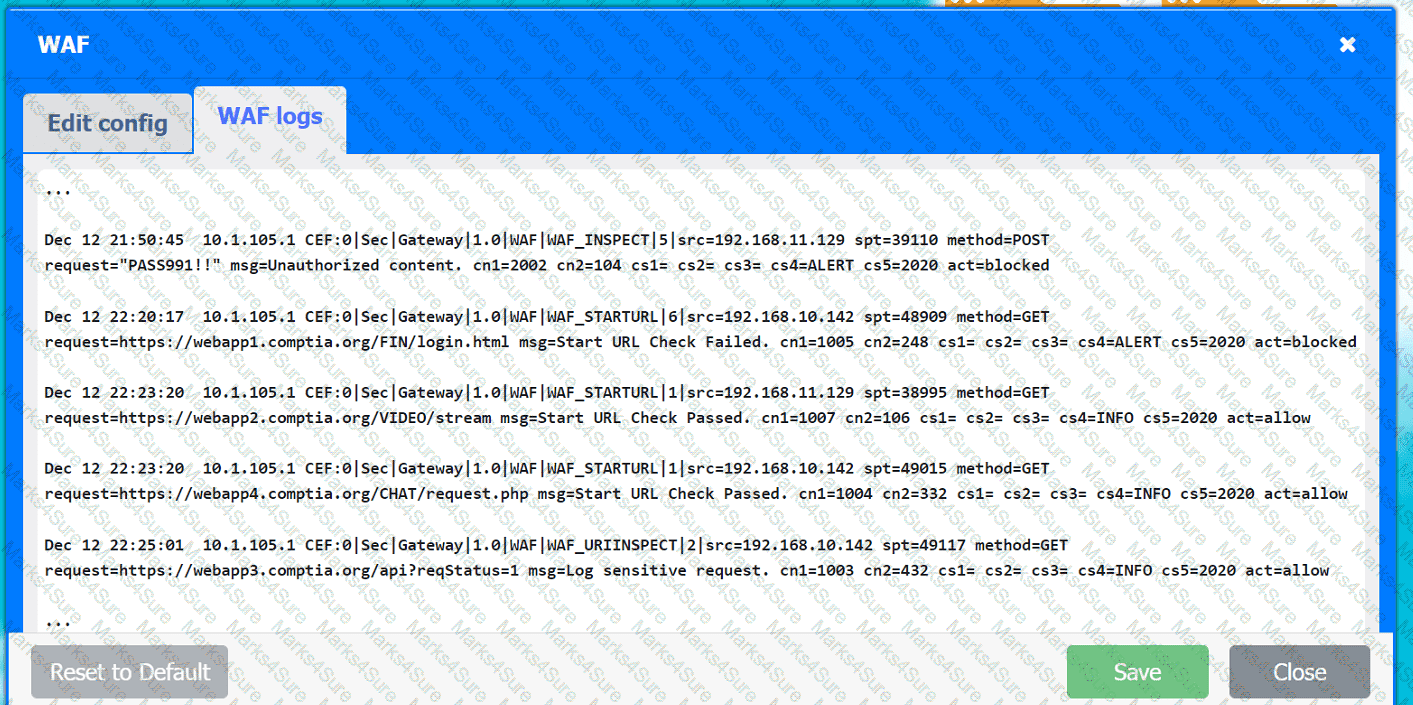
A company hosts various containerized applications for business uses. A client reports that one of its routine business applications fails to load the web-based login prompt hosted in the company cloud.
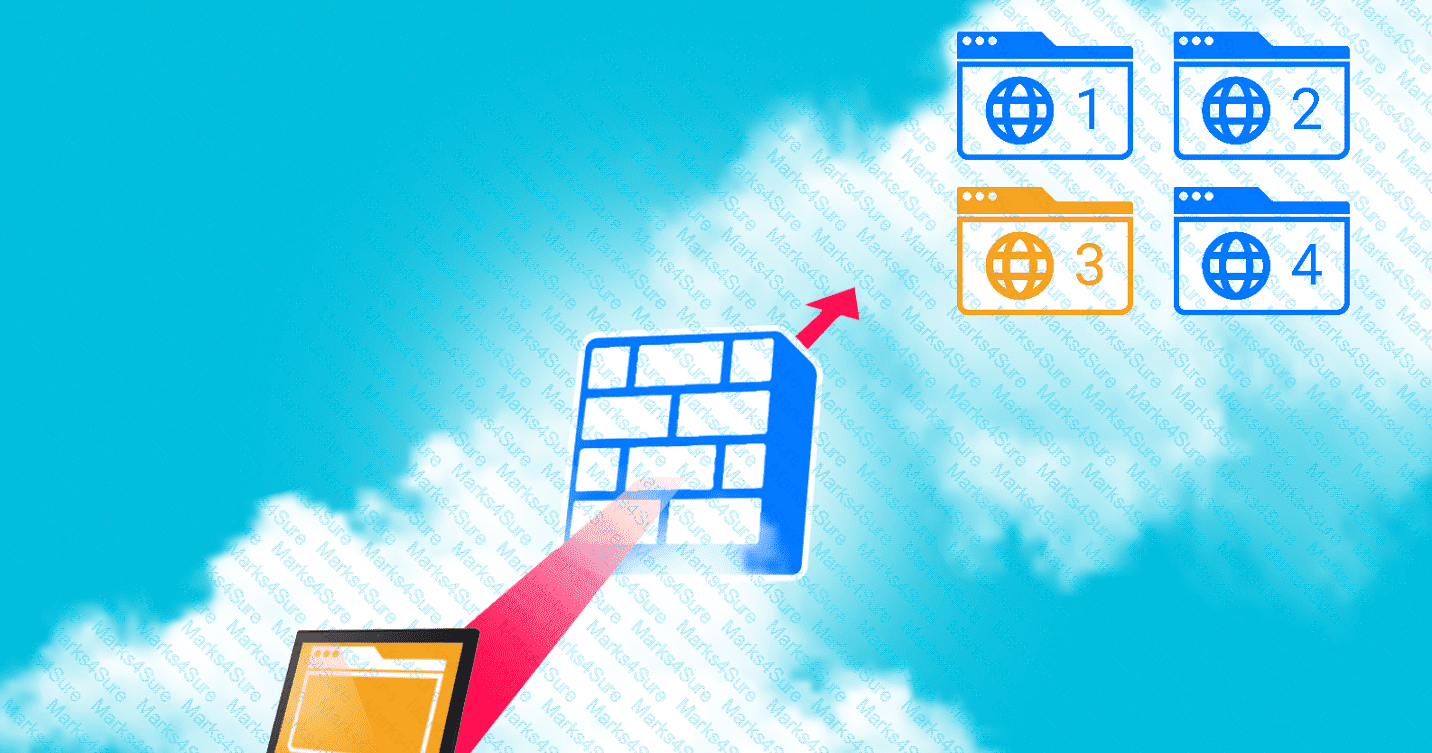
INSTRUCTIONS
Click on each device and resource. Review the configurations, logs, and characteristics of each node in the architecture to diagnose the issue. Then, make the necessary changes to the WAF configuration to remediate the issue.
Web app 1
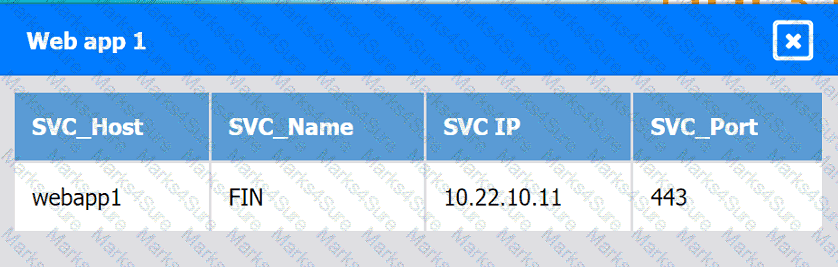
Web app 2
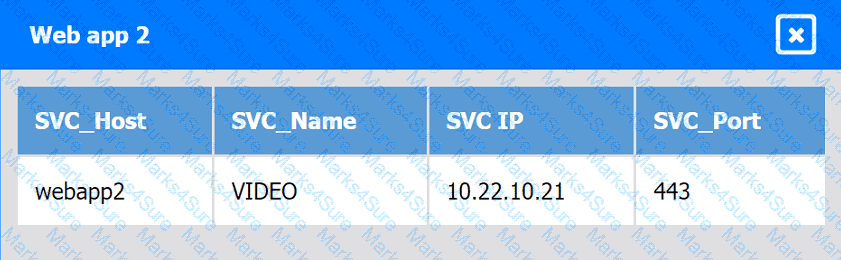
Web app 3
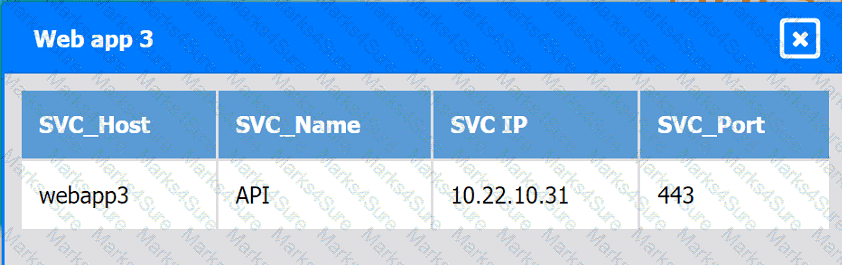
Web app 4
Client app
A cloud engineer is provisioning a new application that requires access to the organization's public cloud resources. Which of the following is the best way for the cloud engineer to authenticate the application?
A government agency in the public sector is considering a migration from on premises to the cloud. Which of the following are the most important considerations for this cloud migration? (Select two).
Which of the following would help a project manager identify that project goals have been reached?
During a phase review, two stakeholders discuss the approval of a deliverable. The project manager convinces the stakeholders to agree on a common solution. Which of the following best describes what the project manager did to gain approval from both stakeholders?
A cloud engineer is concerned about command-and-control (C2) communication out of a cloud network over HTTPS. Which of the following should the cloud engineer implement to most efficiently identify the type of communication?
Which of the following compute resources is the most optimal for running a single scripted task on a schedule?
A software engineer needs to transfer data over the internet using programmatic access while also being able to query the data. Which of the following will best help the engineer to complete this task?
A company's content management system (CMS) service runs on an laaS cluster on a public cloud. The CMS service is frequently targeted by a malicious threat actor using DDoS.
Which of the following should a cloud engineer monitor to identify attacks?
A cloud engineer is extending on-premises services to a public cloud. The following design requirements must be considered in the overall solution:
" The ability to remotely connect systems from both environments
• No IP address conflicts or overlap
• Cost-effectiveness
Which of the following cloud network concepts best meets these requirements?
A cloud engineer is reviewing a disaster recovery plan that includes the following requirements:
• System state, files, and configurations must be backed up on a weekly basis.
• The system state, file, and configuration backups must be tested annually.
Which of the following backup methods should the engineer implement for the first week the plan is executed?
A cloud engineer wants to deploy a new application to the cloud and is writing the following script:
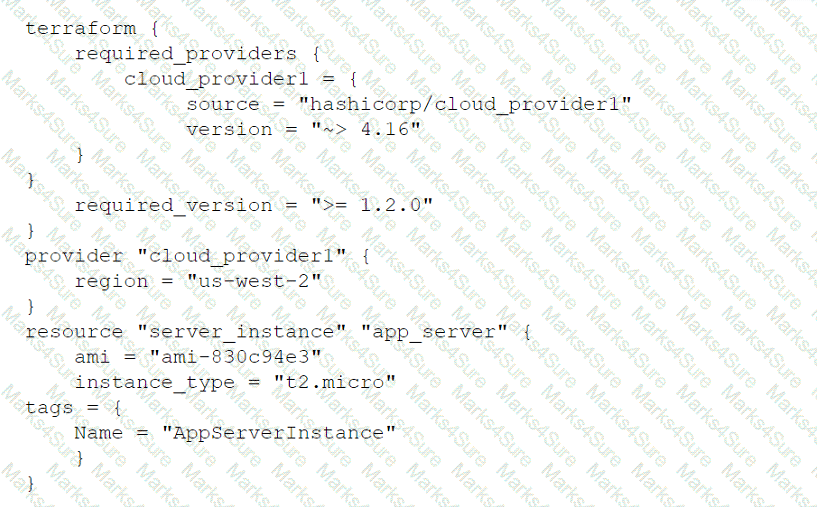
Which of the following actions will this script perform?
A customer's facility is located in an area where natural disasters happen frequently. The customer requires the following:
• Data resiliency due to exposure to frequent natural disasters
• Data localization because of privacy regulations in the country
• High availability
Which of the following cloud resources should be provisioned to meet these requirements?
A cloud administrator is working on the deployment of an e-commerce website. The administrator evaluates the scaling methods to be implemented when seasonal or flash sales are launched. Which of the following scaling approaches should the administrator use to best manage this scenario?
An DevOps engineer is receiving reports that users can no longer access the company's web application after hardening of a web server. The users are receiving the following error:
ERR_SSLJ/ERSION_OR_CIPHER_MISMATCH.
Which of the following actions should the engineer take to resolve the issue?
A critical security patch is required on a network load balancer in a public cloud. The organization has a major sales conference next week, and the Chief Executive Officer does not want any interruptions during the demonstration of an application behind the load balancer. Which of the following approaches should the cloud security engineer take?
An on-premises data center is located in an earthquake-prone location. The workload consists of real-time, online transaction processing. Which ot the following data protection strategies should be used to back up on-premises data to the cloud while also being cost effective?
Which of the following application migration strategies will best suit a customer who wants to move a simple web application from an on-premises server to the cloud?
Participant attendance has been poor at the last few weekly meetings. The project manager wants to validate who the participants should be, how often the meetings should occur, and on which day and at what time the meeting should be held. Which of the following is the best place to validate this information?
Which of the following storage resources provides higher availability and speed for currently used files?
A systems administrator notices a surge of network traffic is coming from the monitoring server. The administrator discovers that large amounts of data are being downloaded to an external source. While investigating, the administrator reviews the following logs:
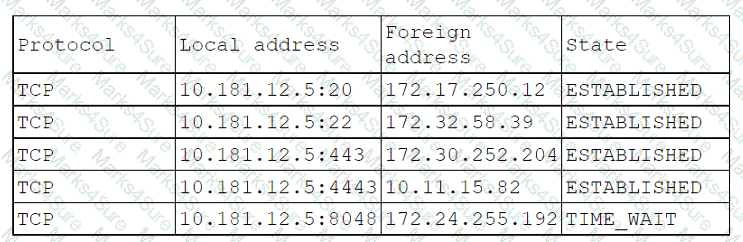
Which of the following ports has been compromised?
A project stakeholder has asked the project manager to provide the performance data of a project. Which of the following should the project manager send to the stakeholder?
A cross-site request forgery vulnerability exploited a web application that was hosted in a public laaS network. A security engineer determined that deploying a WAF in blocking mode at a CDN would prevent the application from being exploited again. However, a week after implementing the WAF, the application was exploited again. Which of the following should the security engineer do to make the WAF control effective?
A company wants to create a few additional VDIs so support vendors and contractors have a secure method to access the company's cloud environment. When a cloud
administrator attempts to create the additional instances in the new locations, the operation is successful in some locations but fails in others. Which of the following is the
most likely reason for this failure?
A system surpasses 75% to 80% of resource consumption. Which of the following scaling approaches is the most appropriate?
A security engineer Identifies a vulnerability m a containerized application. The vulnerability can be exploited by a privileged process to read tie content of the host's memory. The security engineer reviews the following Dockerfile to determine a solution to mitigate similar exploits:

Which of the following is the best solution to prevent similar exploits by privileged processes?
A highly scored negative risk causes a risk trigger, but the issue has not started yet. Which of the following is the next step the project team should take?
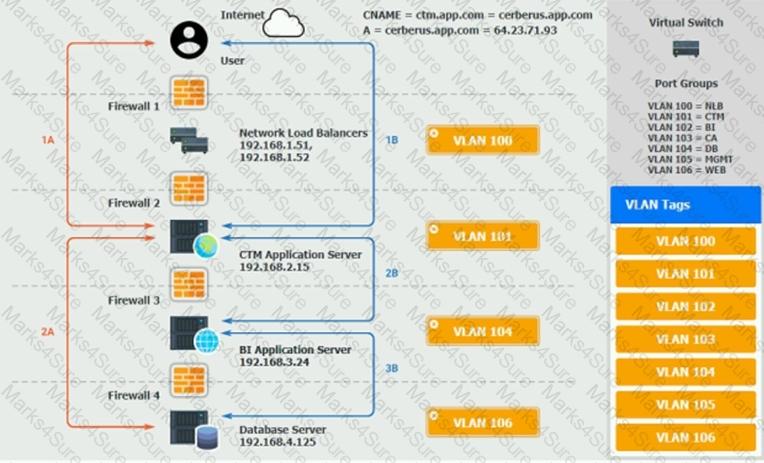
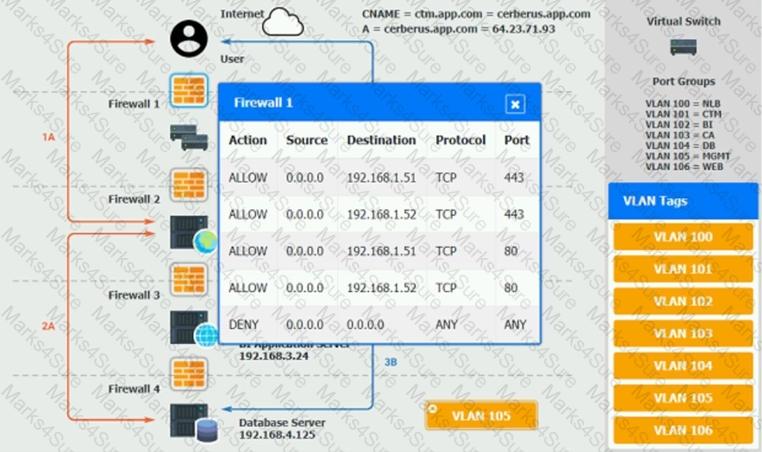
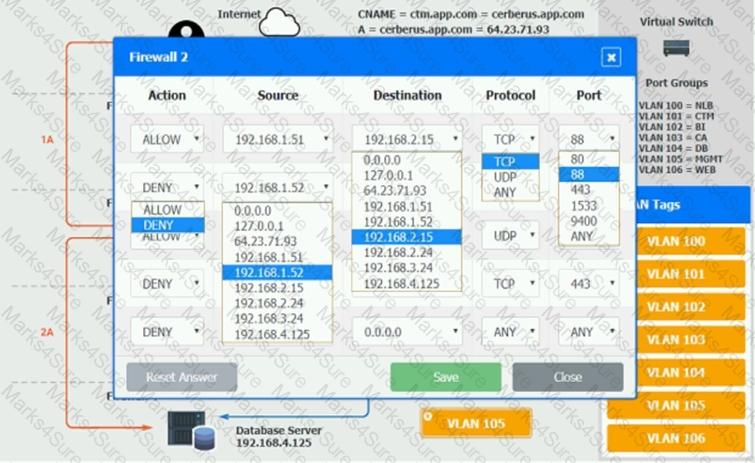
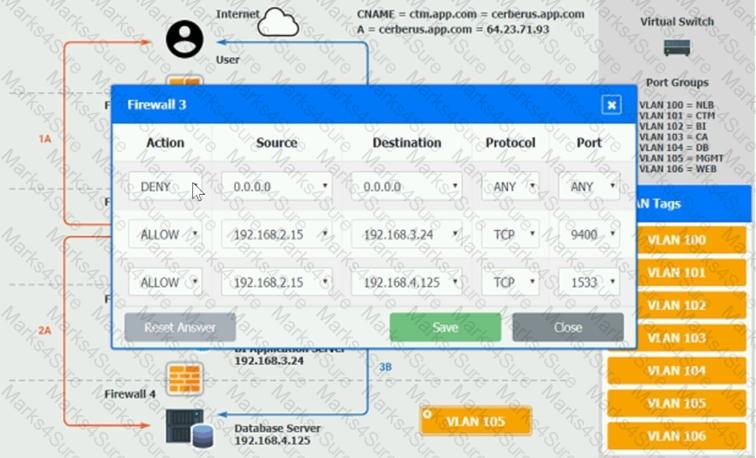
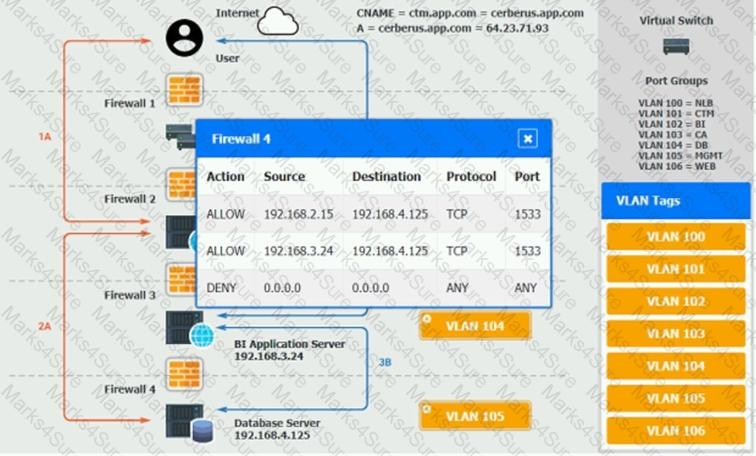
The QA team is testing a newly implemented clinical trial management (CTM) SaaS application that uses a business intelligence application for reporting. The UAT users were instructed to use HTTP and HTTPS.
Refer to the application dataflow:
1A – The end user accesses the application through a web browser to enter and view clinical data.
2A – The CTM application server reads/writes data to/from the database server.
1B – The end user accesses the application through a web browser to run reports on clinical data.
2B – The CTM application server makes a SOAP call on a non-privileged port to the BI application server.
3B – The BI application server gets the data from the database server and presents it to the CTM application server.
When UAT users try to access the application using https://ctm.app.com or http://ctm.app.com, they get a message stating: “Browser cannot display the webpage.” The QA team has raised a ticket to troubleshoot the issue.
INSTRUCTIONS
You are a cloud engineer who is tasked with reviewing the firewall rules as well as virtual network settings.
You should ensure the firewall rules are allowing only the traffic based on the dataflow.
You have already verified the external DNS resolution and NAT are working.
Verify and appropriately configure the VLAN assignments and ACLs. Drag and drop the appropriate VLANs to each tier from the VLAN Tags table. Click on each Firewall to change ACLs as needed.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
Which of the following is the best type of database for storing different types of unstructured data that may change frequently?
A company wants to use a solution that will allow for quick recovery from ransomware attacks, as well as intentional and unintentional attacks on data integrity and availability. Which of the following should the company implement that will minimize administrative overhead?
An administrator needs to provide a backup solution for a cloud infrastructure that enables the resources to run from another data center in case of a outage. Connectivity to the
backup data center is via a third-party, untrusted network. Which of the following is the most important feature required for this solution?
A log-parsing application requires significant processing power to ingest the logs streaming from web servers. The engineering team presents the cloud architect with four proposals
using the same underlying hardware. Which of the following should the cloud architect select in order to minimize the impact of an instance failure while keeping the cost as low as
possible?
An engineer wants lo scale several cloud workloads on demand. Which of the following approaches is the most suitable?
A developer at a small startup company deployed some code for a new feature to its public repository. A few days later, a data breach occurred. A security team investigated the
incident and found that the database was hacked. Which of the following is the most likely cause of this breach?
A systems administrator is configuring backups on a VM and needs the process to run as quickly as possible, reducing the bandwidth on the network during all times from Monday through Saturday. In the event of data corruption, the management team expects the mean time to recovery to be as low as possible. Which of the following backup methods can the administrator use to accomplish these goals?
A cloud security analyst is looking for existing security vulnerabilities on software applications. Which of the following describes this vulnerability management phase?
A cloud engineer is designing a high-performance computing cluster for proprietary software. The software requires low network latency and high throughput between cluster nodes.
Which of the following would have the greatest impact on latency and throughput when designing the HPC infrastructure?
Once a change has been made to templates, which of the following commands should a cloud architect use next to deploy an laaS platform?
A cloud administrator recently created three servers in the cloud. The goal was to create ACLs so the servers could not communicate with each other. The servers were configured
with the following IP addresses:
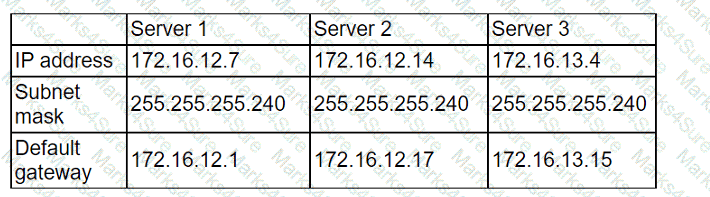
After implementing the ACLs, the administrator confirmed that some servers are still able to reach the other servers. Which of the following should the administrator change to
prevent the servers from being on the same network?
A company experienced a data leak through its website. A security engineer, who is investigating the issue, runs a vulnerability scan against the website and receives the following output:
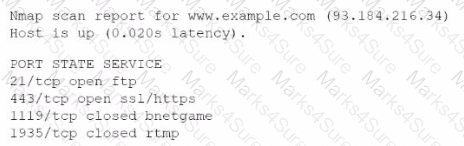
Which of the following is the most likely cause of this leak?
A software engineer is integrating an application lo The cloud that is web socket based. Which of the following applications is the engineer most likely deploying?
Given the following command:
Sdocker pull images.comptia.org/user1/myimage:latest
Which of the following correctly identifies images.comptia.org?