Your VMware environment is configured without using NSX. How can Deep Security provide protection to the virtual images hosted on your ESXi servers?
Where does Deep Security Manager store the credentials it uses to access the database?
An administrator enables Multi-Tenancy in Deep Security and creates multiple tenants. After a period of time, the administrator would like to review the usage and resource consumption by a specific tenant. How can the administrator retrieve this information?
Your organization stores PDF and Microsoft Office files within the SAP Netweaver platform and requires these documents to be scanned for malware. Which Deep Security component is required to satisfy this requirement?
An administrator attempts to activate the Deep Security Agent installed on a server by typing the following command in the Command Prompt on the Deep Security Agent computer:
dsa_control -a dsm://server1.acme.com:4120
The Agent does not activate as expected. What is a valid reason for this issue?
While viewing the details of the Firewall Protection Module, as displayed in the exhibit, you note that a few rules have already been assigned. You try to disable these rules, but they can not be unassigned. Why can the displayed rules not be unassigned?
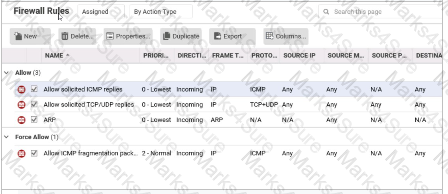
Which of the following correctly describes the Firewall rule Action of Force Allow?