The BIG-IP Administrator runs the command:
netstat -an | grep 443
and sees the following output:
tcp 0 0 0.0.0.0:443 0.0.0.0:* LISTEN
What does this output indicate about the service on port 443? (Choose one answer)
The BIG-IP Administrator suspects unauthorized SSH login attempts on the BIG-IP system.
Which log file would contain details of these attempts? (Choose one answer)
A BIG-IP Administrator needs to check the memory utilization on a BIG-IP system. Which two methods can the BIG-IP Administrator use? (Choose two.)
A BIG-IP Administrator needs to view the CPU utilization of a particular Virtual Server. Which section of the Configuration Utility should the administrator use for this purpose?
A local user account (Users) on the BIG-IP device is assigned the User Manager role. User1 attempts to modify the properties of another account (User2), but the action fails. The BIG-IP Administrator can successfully modify the User2 account. Assuming the principle of least privilege, what is the correct way to allow User1 to modify User2 properties?
A BIG-IP Administrator discovers malicious brute-force attempts to access the BIG-IP device on the management interface via SSH. The BIG-IP Administrator needs to restrict SSH access to the management interface. Where should this be accomplished?
One of the two members of a device group has been decommissioned. The BIG-IP Administrator tries to delete the device group, but is unsuccessful. Prior to removing the device group, which action should be performed?
A BIG-IP device sends out the following SNMP trap: big-ipo.f5.com - bigipExternalLinkChange Link: 1.0 is DOWN. Where in the BIG-IP Configuration utility should the BIG-IP Administrator verify the current status of Link 1.0?
Users report that traffic is negatively affected every time a BIG-IP device fails over. The traffic becomes stabilized after a few minutes. What should the BIG-IP Administrator do to reduce the impact of future failovers?
A BIG-IP Administrator needs to update the license on a BIG-IP device. Where can this be done?
What are the recommended methods for forcing a BIG-IP system to standby mode? (Choose two answers)
A BIG-IP Administrator reviews the Plane CPU Usage performance chart and discovers a high percentage of Control Plane utilization. Which type of traffic does this indicate a higher usage of?
As an organization grows, more people have to log into the BIG-IP. Instead of adding more local users, the BIG-IP Administrator is asked to configure remote authentication against a central authentication server.
Which two types of remote server can be used here? (Choose two answers)
A BIG-IP Administrator suspects that one of the BIG-IP device power supplies is experiencing power outages. Which log file should the BIG-IP Administrator check to verify the suspicion?
Which TMSH command initiates a manual configuration synchronization to the specified device group? (Choose one answer)
Refer to the exhibit.
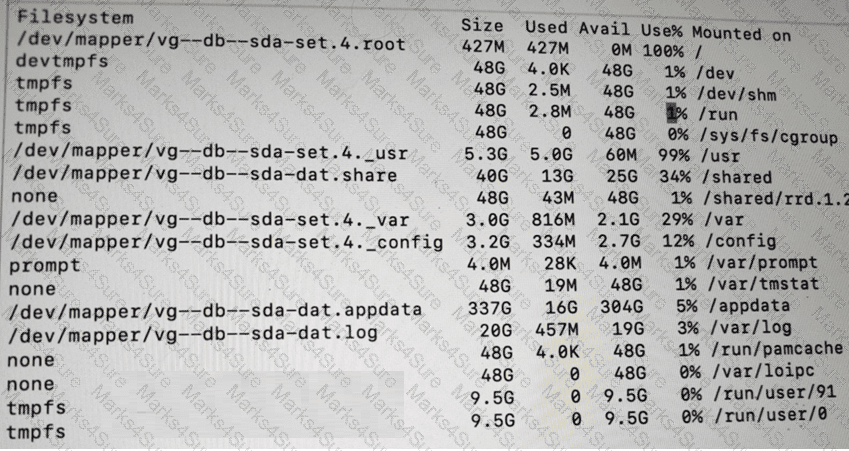
The BIG-IP Administrator is investigating disk utilization on the BIG-IP device. What should the BIG-IP Administrator check next? (Choose one answer)
A node is a member of various pools and hosts different web applications. If a web application is unavailable, the BIG-IP appliance needs to mark the pool member down for that application pool. What should a BIG-IP Administrator deploy at the pool level to accomplish this?