Refer to the exhibits.
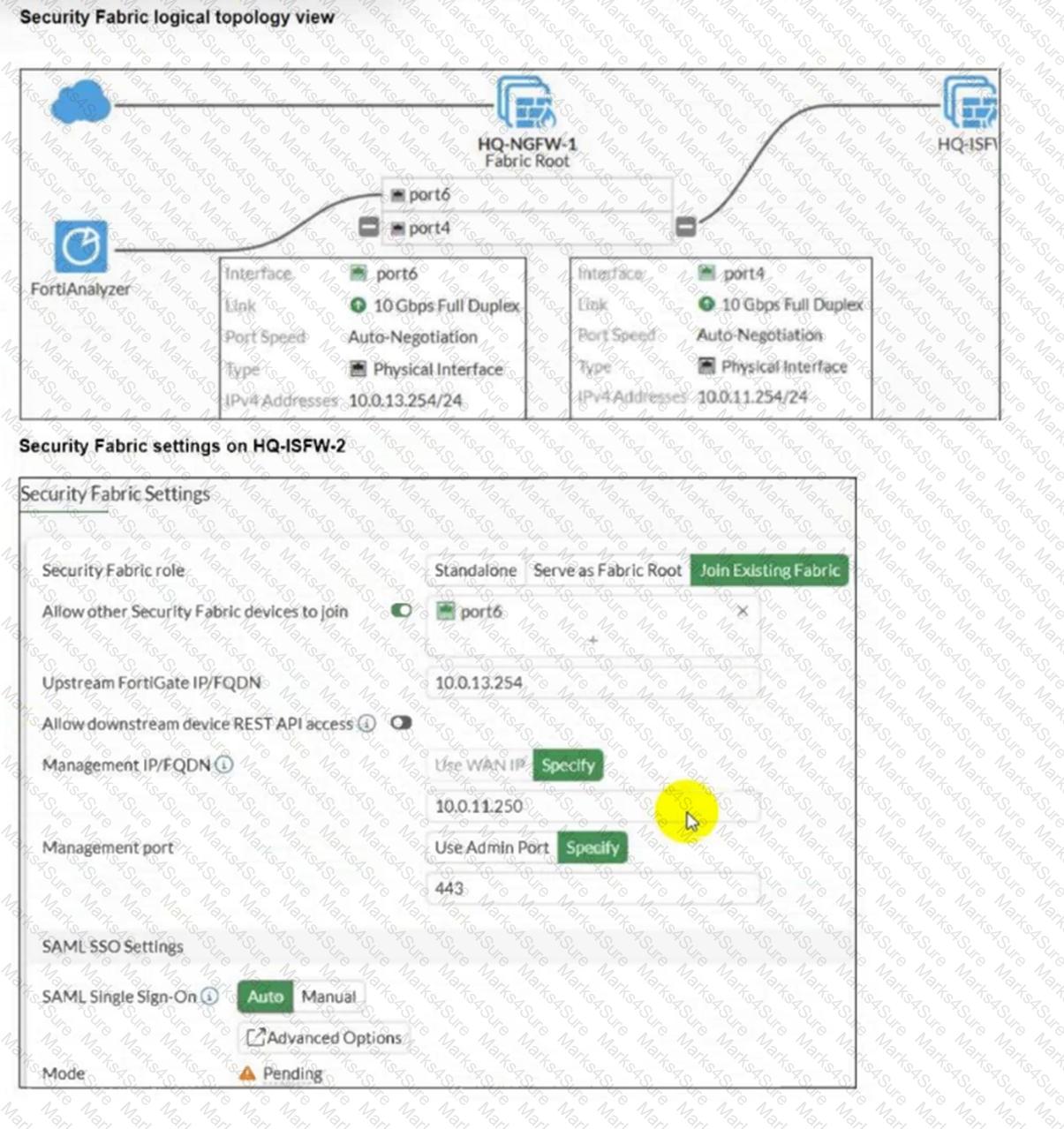
An administrator wants to add HQ-ISFW-2 in the Security Fabric. HQ-ISFW-2 is in the same subnet as HQ-ISFW. After configuring the Security Fabric settings on HQ-ISFW-2, the status staysPending.
What can be the two possible reasons? (Choose two.)
Refer to the exhibits.
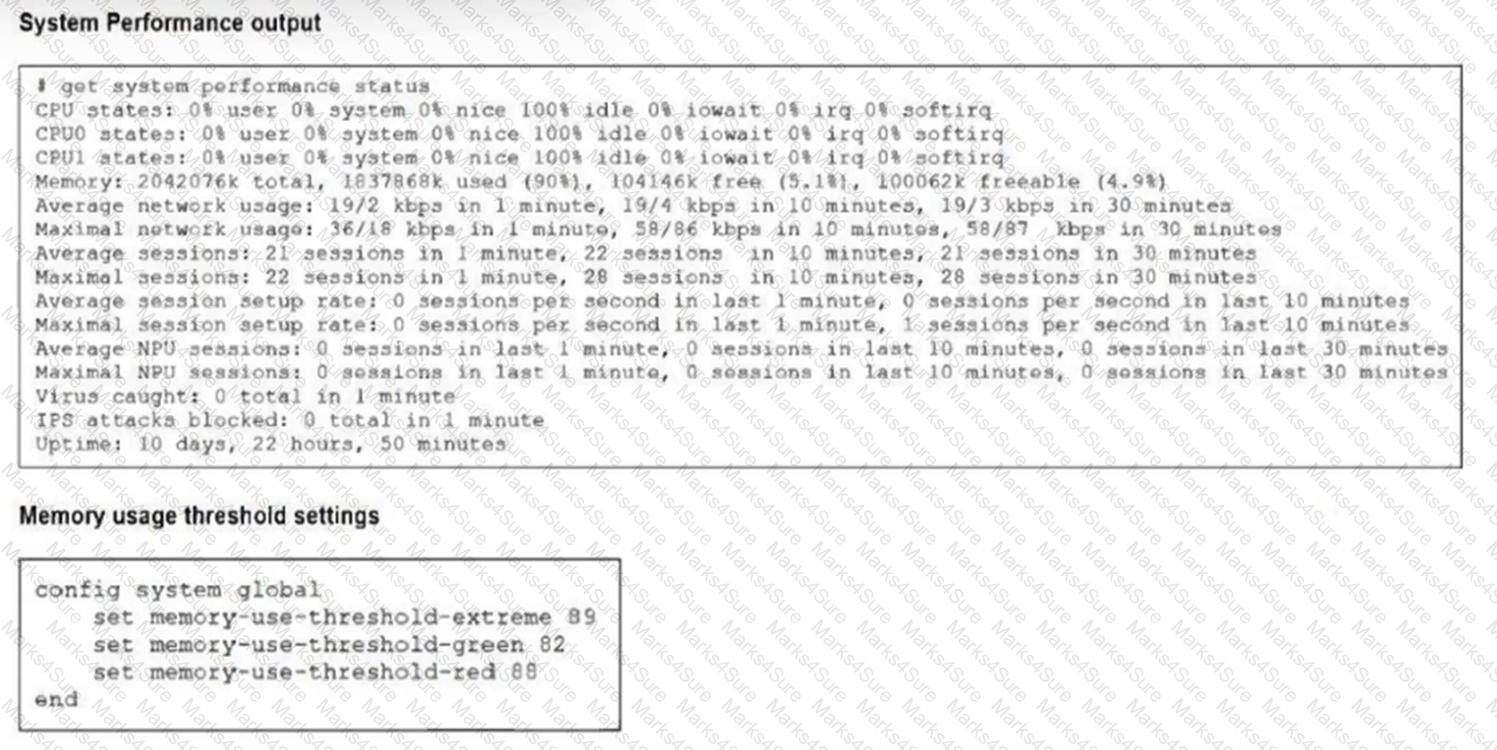
The exhibits show the system performance output and default configuration of high memory usage thresholds on a FortiGate device.
Based on the system performance output, what are the two possible outcomes? (Choose two.)
Refer to the exhibits.

An administrator has observed the performance status outputs on an HA cluster for 55 seconds.
Which FortiGate is the primary?
You have configured the FortiGate device for FSSO. A user is successful in log-in to windows, but their access to the internet is denied.
What should the administrator check first?
You have configured an application control profile, set peer-to-peer traffic to Block under the Categories tab, and applied it to the firewall policy. However, your peer-to-peer traffic on known ports is passing through the FortiGate without being blocked.
What FortiGate settings should you check to resolve this issue?
A remote user reports slow SSL VPN performance and frequent disconnections. The user is located in an area with poor internet connectivity.
What setting should the administrator adjust to improve the user's experience?
Refer to the exhibit, which shows a partial configuration from the remote authentication server.
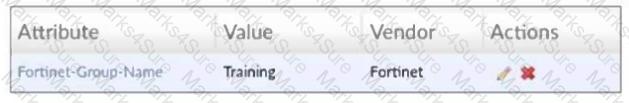
Why does the FortiGate administrator need this configuration?
An administrator wants to configure dead peer detection (DPD) on IPsec VPN for detecting dead tunnels. The requirement is that FortiGate sends DPD probes only when there is no inbound traffic.
Which DPD mode on FortiGate meets this requirement?
Refer to the exhibits.
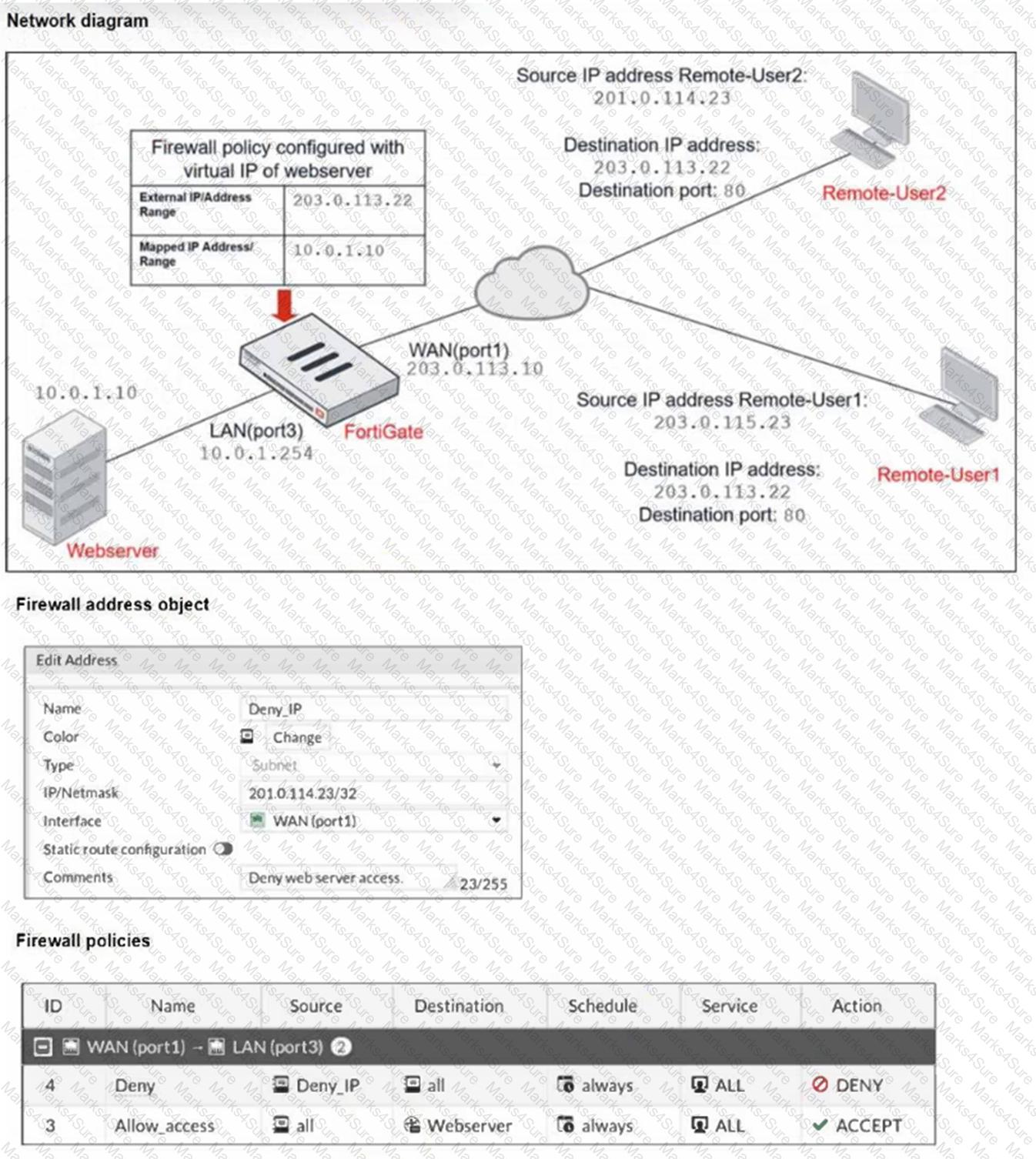
The exhibits show a diagram of a FortiGate device connected to the network, and the firewall configuration.
An administrator created aDenypolicy with default settings to deny Webserver access forRemote-User2.
The policy should work such thatRemote-User1must be able to access the Webserver while preventingRemote-User2from accessing theWebserver.
Which additional configuration can the administrator add to a deny firewall policy, beyond the default behavior, to blockRemote-User2from accessing theWebserver?
Which two statements are correct when FortiGate enters conserve mode? (Choose two.)