The file ~, GlAC/hickory.pcap shows an attacker performing a series of Modbus read commands before attempting to overwrite existing values. Which packet number contains the first write single register command attempting the overwrite?
A plant is being retrofitted with new cyber security devices in Purdue Level 3. What should the network security architect suggest for the installation?
Which of the following types of network devices sends traffic only to the intended recipient node?
Implementation of LDAP to manage and control access to your systems is an outcome of which NIST CSF core function?
An attacker writes a program that enters a large number of characters into the password field of a website, followed by a command. The website gave him administrative access, even though he did not use a valid username or password.
What is the name of this attack?
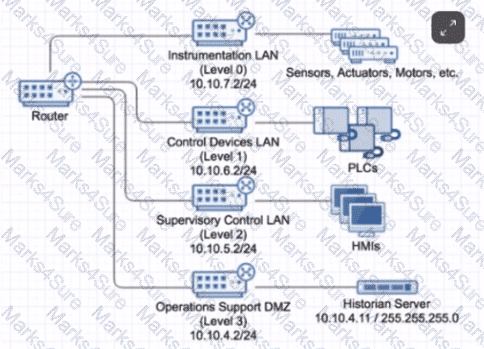
What can be configured on the router so that it can most effectively implement and enforce zones for the shown subnets?
Which of the followingis a team of incident responders that often coordinate with organizations and law enforcement to reduce risks and advise on security threats?
Which type of device is the following configuration setting from?
deny modbus function write-multiple-holdingregisters
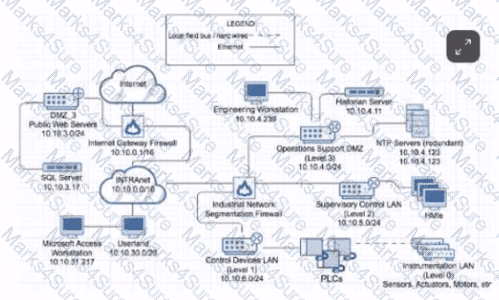
Observe the network diagram. Which of the following hosts is intended to keep ICS process data in a database?
Which of the following is part of the Respond function of the NIST CSF (cybersecurity framework)?
According to the DHS suggested patch decision tree, what should the next step be if there is a vulnerability with an available patch, but without an available workaround?
Martin is writing a document that describes in general terms how to secure embedded operating systems. The document includes issues that are specific to embedded devices vs desktop and laptop operating systems. However, it does not call out specific flavors and versions of embedded operating systems. Which type of document is Martin writing?
An attacker crafts an email that will send a user to the following site if they click a link in the message. What else is necessary for this type of attack to work?
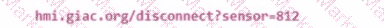
Which command can be used on a Linux system to search a file for a string of data and return the results to the screen?