For the description of URPF technology, which of the following options are correct? (multiple choice)
Which of the following options belong to the keyword matching mode? (multiple choice)
Regarding the sequence of the mail transmission process, which of the following is correct?
1. The sender PC sends the mail to the designated SMTP Server.
2. The sender SMTP Server encapsulates the mail information in an SMTP message and sends it to the receiver SMTP Server according to the destination address of the mail
3. The sender SMTP Server encapsulates the mail information in an SMTP message according to the destination address of the mail and sends it to the receiver POP3/MAP Senver
4. The recipient sends an email.
Regarding Huawei's anti-virus technology, which of the following statements is wrong?
Regarding traditional firewalls, which of the following statements are correct? (multiple choice)
Which of the following statement is correct about Policy Center system client function?
After the user deploys the firewall anti-virus strategy, there is no need to deploy anti-virus software
In the penetration stage of an APT attack, which of the following attack behaviors will the attacker generally have?
Due to differences in network environment and system security strategies, intrusion detection systems are also different in specific implementation. From the perspective of system composition, the main
Which four major components are included?
In Huawei USG6000 products, IAE provides an integrated solution, all content security detection functions are integrated in a well-designed
In the high-performance engine. Which of the following is not the content security detection function supported by this product?
Regarding the strong statement of DNS Request Flood attack, which of the following options is correct?
The core technology of content security lies in anomaly detection, and the concept of defense lies in continuous monitoring and analysis.
When you suspect that the company's network has been attacked by hackers, you have carried out a technical investigation. Which of the following options does not belong to the behavior that occurred in the early stage of the attack?
The user needs of a university are as follows:
1. The environment is large, and the total number of two-way traffic can reach 800M. Huawei USG6000 series firewall is deployed at its network node.
2. The intranet is divided into student area, server area, etc., users are most concerned about the security of the server area to avoid attacks from various threats.
3. At the same time, some pornographic websites in the student area are prohibited.
The external network has been configured as an untrust zone and the internal network has been configured as a trust zone on the firewall. How to configure the firewall to meet the above requirements?
155955cc-666171a2-20fac832-0c042c0415
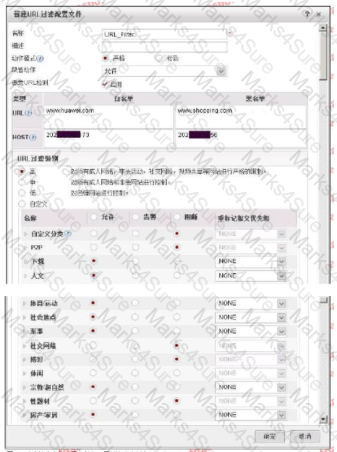
The following figure shows the configuration of the URL filtering configuration file. Regarding the configuration, which of the following statements is correct?
Huawei WAF products are mainly composed of front-end execution, back-end central systems and databases. Among them, the database mainly stores the front-end detection rules and black
Whitelist and other configuration files.
A True
B. False
When the Anti DDoS system finds the attack flow, the state will redirect the attack flow to the cleaning device. After the cleaning device is cleaned, it will flow back.
Note to the original link, which of the following options does not belong to the method of re-injection?
Which of the following descriptions are correct for proxy-based anti-virus gateways? (multiple choice)
Anti-DDoS defense system includes: management center, detection center and cleaning center.
Threats detected by the big data intelligent security analysis platform will be synchronized to each network device at the same time C and then collected from the network device
Collect it in the log for continuous learning and optimization.
Terminal fault diagnosis tool can diagnose fault, also can collect terminal information.
Among the following options, which attack is a malformed packet attack based on the TCR protocol?
For special message attacks, which of the following option descriptions is correct?
A Special control packet attack is a potential attack and does not have direct destructive behavior
B. The attacker probes the network structure by sending special control messages to launch a real attack.
C. Special control message attacks do not have the ability to detect the network structure. Only scanning attacks can detect the network.
D. Special control message items can only use ICMP to construct attack messages.