In Huawei USG6000 products, IAE provides an integrated solution, all content security detection functions are integrated in a well-designed
In the high-performance engine. Which of the following is not the content security detection function supported by this product?
Which of the following series of devices does not support the function of accompanying business?
Regarding the statement of the mail protocol, which of the following is correct? (multiple choice)
Web Standards that come with the client and operating system 8021 The instrument client only has the function of identity authentication: It does not support the execution of inspection strategies and monitoring strategies. Any Office The client supports all inspection strategies and monitoring strategies.
Regarding the processing flow of file filtering, which of the following statements is wrong?
Install Agile Controller-Campus Which of the following steps do not need to be completed before?
If the user's FTP operation matches the FTP filtering policy, what actions can be performed? (multiple choice)
Regarding MAC authentication and MAC bypass authentication, which of the following descriptions are correct? (multiple choice)
For the terminal Wi-Fi The order of the push, which of the following is correct?
1. Any Office Mobile office system push Wi-Fi Configuration
2. Any Office The mobile office department automatically applies for a certificate.
3. The administrator configures the enterprise Wi-Fi Push.
4. The terminal automatically connects to the enterprise Wi-Fi.
Jailbroken mobile terminal\Mobile terminals with non-compliant applications installed or terminals with non-compliant lock screen passwords connecting to the corporate network for office operations are not safe for companies. Any 0fice How to solve the problem of mobile office system?
In a WLAN network, when the AP is in monitoring mode, what kind of packets does the AP use to determine the device type?
On WIDS functional WLAN Regarding the judgment of illegal devices in the network, which of the following statements are correct? (Multiple choice)
There are three roles in the XMPP protocol: server, gateway, and client. Corresponding to the free mobility solution: Agile Controller-Campus as For the server, Huawei USG6000 series firewall acts as the gateway; the agile switch acts as the client.
In order to increase AP The security can be AC Going online AP Perform authentication. Currently Huawei AC What are the supported authentication methods? (Multiple choice)
The application behavior control configuration file takes effect immediately after being referenced, without configuration submission.
UDP is a connectionless protocol. UDP Flood attacks that change sources and ports will cause performance degradation of network devices that rely on session forwarding.
Even the session table is exhausted, causing the network to be paralyzed. Which of the following options is not a preventive measure for UDP Flood attacks?
IPS is an intelligent intrusion detection and defense product. It can not only detect the occurrence of intrusions, but also can respond in real time through certain response methods.
Stop the occurrence and development of intrusions, and protect the information system from substantial attacks in real time. According to the description of PS, the following items are wrong?
The network-based intrusion detection system is mainly used to monitor the information of the critical path of the network in real time, listen to all packets on the network, collect data, and divide
Analyze the suspicious object, which of the following options are its main features? (multiple choices)
URL filtering technology can perform URL access control on users according to different time objects and address objects to achieve precise management of users.
The purpose of the Internet behavior.
With the continuous development of the network and the rapid development of applications, companies are making users more and more frequently start to transfer files on the network.
Virus threats are becoming more and more serious. Only by rejecting the virus outside the network can data security and system stability be guaranteed. So, which of the following are
What harm might be caused by illness? (multiple choices)
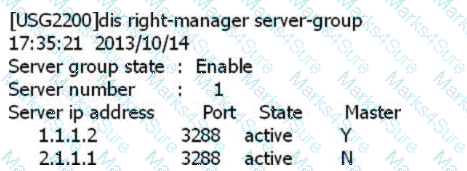
An enterprise adopts hardware SACG access method for admission control. The configuration commands are as follows, among which Key; Admin@123
[USG] right-manager server-group
[USG-rightm] localip 10.1.10.2
[USG-rightm]serverip 10. 1.31.78 shared-key AdnIn@123
[USG2100-rightm] right-manager server-group enable.
Assuming that the other configurations are correct, based on the above configuration only, which of the following options is correct?
Visitors can access the network through their registered account. Which of the following is not an account approval method?
Regarding intrusion detection I defense equipment, which of the following statements are correct? (multiple choice)
If you use a normal account for authentication, which of the following descriptions is wrong?
Mobile smartphone, tablet PC users through Any Office Client and AE Establish IPSec Encrypted tunnel, After passing the certification and compliance check, visit the enterprise business.
Which of the following options belong to the network layer attack of the TCP/IP protocol stack? (multiple choice)
Regarding the enhanced mode in HTTP Flood source authentication, which of the following descriptions are correct? Multiple choices
An enterprise administrator configures a Web reputation website in the form of a domain name, and configures the domain name as www. abc; example. com. .
Which of the following is the entry that the firewall will match when looking up the website URL?
There are two ways for Business Manager to download patches. When using hierarchical deployment, you can download patches directly from the management center or through Microsoft patches Server download patch.
In the deployment of Huawei NIP6000 products, only port mirroring can be used for streaming replication.
Which of the following descriptions about viruses and Trojans are correct? (multiple choices)
There are two types of accounts on the Agile Controller-Campus: one is a local account and the other is an external account.
Which of the following is not a local account?
How to check whether the SM and SC silverware start normally after installing the Agile Controller-Campus) (multiple delivery)
According to the user’s access5W1H Conditions determine access rights andQoS Strategy for5W1Ho[Which of the following descriptions are correct? (Multiple choice)
For the URL is htpt://www.abcd. com:8080/news/education. aspx?name=tom &age=20, which option is path?
In the anti-virus policy configuration of Huawei USG6000 product, what are the response methods of HTTP protocol? (multiple choice)
Which of the following is the default port number of Portal authentication service?
Which of the following technology, administrators can according to business requirements, to scale to achieve load sharing of business flow?
The user access security solution is one-kind"End to end"Security architecture. The user access security architecture includes three key components:Terminal equipment, network access equipment and access server.
In the following options, which of the two attacks use similar attack methods, they will generate a large number of useless response packets, occupying network bandwidth,
Consume equipment resources?
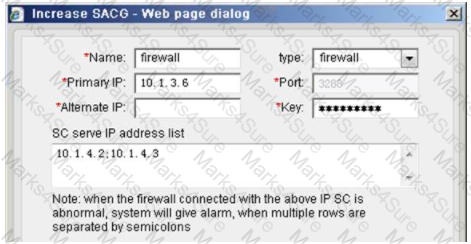
The following is a hardware SACG increase firewall configuration, which statement below is true?
In the campus network, employees can use 802.1X, Portal,MAC Address or SACG Way to access. Use different access methods according to different needs to achieve the purpose of user access control.
In centralized networking, database,SM server,SC server\ AE Servers are centrally installed in the corporate headquarters. This networking method is suitable for companies with a wide geographical distribution of users and a large number of users.
The access control server is the implementer of the corporate security policy, responsible for implementing the corresponding access control in accordance with the security policy formulated by the customer's network(Allow, deny, leave or restrict).
Which of the following descriptions are correct for proxy-based anti-virus gateways? (multiple choice)
MAC Bypass authentication means that after the terminal is connected to the network, the access control device automatically obtains the terminal MAC Address, which is sent to RADIUS The server performs euverification.
Deploying on Windows platform, using SQL Server database About the HA function of Agile Cotoller-Campus, which of the following descriptions Is it correct? (multiple choice)
SACG query right-manager information as follows, which options are correct? (Select 2 answers)