The BGP ORF function can be used to control the maximum number of routes that can be sent by a BGP peer. To achieve this, which of the following tools is used to send such a route list to BGP peers?
In a scenario where a VXLAN tunnel is dynamically established through BGP EVPN, which of the following command needs to be run on the VBDIF interface to enable the VTEP peer to generate BGP EVPN Type 2 routes based on ARP information of the local terminal?
Which of the following statements is correct about the differences between NSR and NSF?
Refer to the following command output on the router R3. Which of the following statements are correct?
Tunnel0/0/0 current state : UP
Line protocol current state : UP
Last line protocol up time : 15:21:26 UTC-08:00
Description: HUAWEI, AR Series, Tunnel0/0/0 Interface
Route Port, The Maximum Transmit Unit is 1500
Internet Address is 20.1.1.2/24
Encapsulation is TUNNEL, loopback not set
Tunnel source 10.0.3.3 (LoopBack0), destination 10.0.1.1
Tunnel protocol/transport GRE/IP, key disabled
keepalive disabled
Checksumming of packets disabled
On a virtualized network deployed using iMaster NCE-Campus, after creating VNs, you need to configure inter-VN communication. Which of the following configurations is used to achieve VN communication?
On the network shown in the figure, OSPF-based SR-MPLS TE is enabled on all routers. Which of the following adjacency labels are allocated by P3?
In the Huawei CloudCampus Solution, which of the following deployment modes are supported by Huawei switches?
Which of the following fields is added to BGP4+ Update packets to advertise IPv6 routes?
IPsec uses an asymmetric encryption algorithm to encrypt the symmetric algorithm key, which it uses to encrypt/decrypt data, ensuring security and performance.
In Huawei's NAC solution, which of the following cannot be used for Portal authentication?
Based on the configuration in the following figure, how many interfaces on R4 are advertised into IS-IS?
plaintext
CopyEdit
Interface information for ISIS(1)
Interface Id IPV4.State IPV6.State MTU Type DIS
GE0/0/0 001 Up Down 1497 L1/L2 No/No
GE0/0/1 002 Up Down 1497 L1/L2 No/No
Loop0 001 Up Down 1500 L1/L2 -
With telemetry, certain data can be sampled based on specific sampling paths. Which of the following sampling paths are supported by telemetry?
Which of the following methods can be used to establish IPsec SAs? (Select All that Apply)
To obtain the token ID of iMaster NCE, you need to send an HTTP request message that includes the following Python code to invoke an iMaster NCE RESTful API.
Which of the following statements is incorrect?
import requests
nbi_name = "demo13@north.com"
nbi_pwd = "CgocVcVe1@"
host = "139.9.213.72"
port = "18002"
URI = "/controller/v2/tokens"
post_token_url = "https:// " + host + ":" + port + URI
headers_post = {"Content-Type": "application/json", "Accept": "application/json"}
r = requests.post(post_token_url, headers=headers_post, json={"userName": nbi_name, "password": nbi_pwd}, verify=False)
After a wireless user passes Portal authentication, which of the following parameterscannotbe used for authorizing the user?
MACsec can provide secure services during MAC-layer data transmitting and receiving. Which of the following services isnotprovided by MACsec?
Which of the following statements is incorrect about Authentication Header (AH)?
For telemetry data push, data can be transferred between devices and collectors using the TLS protocol. TLS must be configured for data encryption if data is pushed based on gRPC.
O&M personnel for a large-scale event center receive feedback about Wi-Fi access failures. iMaster NCE-CampusInsight provides the function for personnel to view packet exchange processes and locate the root cause. It is found that IP addresses in the DHCP address pool are exhausted, preventing IP addresses from being assigned to mobile terminals. Which of the following functions is used by O&M personnel in this scenario?
Which of the following inter-AS MPLS L3VPN solutions need VPN user data packets to carry MPLS labels when being forwarded between ASs?
A network administrator runs thedisplay telemetry subscriptioncommand on a device to check telemetry subscription information. The command output is as follows:
[~CE] display telemetry subscription
Sub-name : Sub1
Sensor group:
Sensor-name Sample-interval(ms) State
Sensor1 1000 RESOLVED
Destination group:
Dest-name Dest-IP Dest-port State Vpn-name Protocol
Dest1 192.168.56.1 20000 RESOLVED - GRPC
Sub-state : PASSIVE
Total subscription number is : 1
Which of the following statements is incorrect?
When static IPsec VPN is used for WAN interconnection in the Huawei CloudCampus Solution, the AP, Router, and _____ can be used as egress devices. (Use full spelling with the first letter capitalized.)
Which of the following commands are mandatory for configuring an OSPF-based SR-MPLS TE tunnel? (Select All that Apply)
MPLS supports both static and dynamic LSP establishment. Which of the following protocols cannot dynamically establish LSPs in MPLS TE scenarios? (Select all that apply)
YANG is a data modeling language for the definition of data sent over network management protocols such as NETCONF. Which of the following are basic YANG data models? (Select all that Apply)
The TTL field encapsulated in the MPLS label header can prevent infinite loops of MPLS packets. Which of the following statements regarding the TTL field are correct?
SR-MPLS is enabled on all routers. The label information encapsulated byR1into a data packet is shown in the figure.
Which of the following is the forwarding path of the data packet?
Which of the following statements aboutprefix segments and adjacency segmentsare correct?
MPLS supports forwarding equivalence class (FEC). Which of the following cannot be used as an FEC allocation standard?
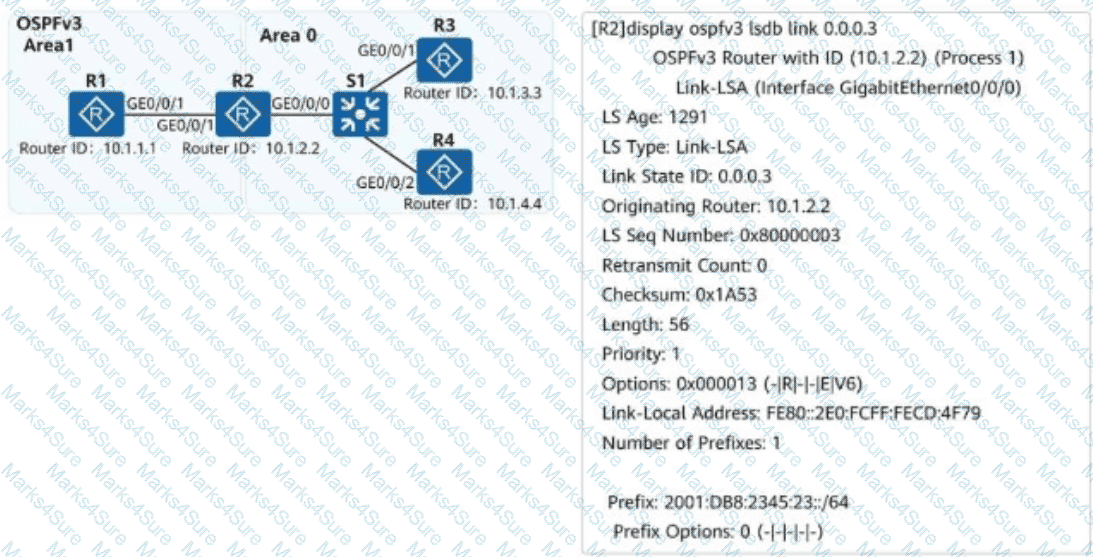
On the campus network shown, IPv6 is deployed for service tests. Four routers are deployed on the network, and OSPFv3 is used for IPv6 network connectivity. An engineer checks the LSDB of R2 and obtains a Link-LSA. Which of the following statements about the LSA are correct?
As shown in the figure, what is known about the default routes on R4?
Routing Table on R4:
Destination/Mask Proto Pre Cost Flags NextHop Interface
0.0.0.0/0 ISIS-L1 15 10 D 10.1.24.1 GigabitEthernet0/0/1
ISIS-L1 15 10 D 10.1.34.1 GigabitEthernet0/0/0
172.16.1.2/32 ISIS-L1 15 10 D 10.1.24.1 GigabitEthernet0/0/1
172.16.1.3/32 ISIS-L1 15 10 D 10.1.34.1 GigabitEthernet0/0/0
As shown in the figure, SW1 and SW2 use asymmetric IRB (Integrated Routing and Bridging) forwarding, and PC1 and PC2 communicate with each other. Which of the following is the destination MAC address of the original data frame in the packet sent from VTEP1 to VTEP2?
IS-IS supports multi-instance and multi-process. Which of the following statements are correct about IS-IS multi-instance and multi-process?
Network administrator A wants to use an IP prefix list to match specific routes. Which of the following routes can be matched by the IP prefix list shown in this figure?
ip ip-prefix TEST permit 10.0.0.0 24 less-equal 30
An SR-MPLS Policy needs to divert service traffic to a tunnel for forwarding. If traffic from various services is destined for the same address, which of the following traffic diversion modes is recommended to ensure the quality of each service?
NETCONF provides a set of mechanisms for managing network devices. NETCONF operations take place on a configuration datastore of network devices. Which of the following statements is incorrect about the configuration datastore?
During telemetry static subscription, the NMS delivers subscription configuration to devices for data sampling. Which of the following statements is incorrect about the sampling path huawei-debug:debug/cpu-infos/cpu-info?
Refer to the following command output on the router R1. Which of the following statements isincorrect?
Tunnel0/0/0 current state : UP
Line protocol current state : UP
Last line protocol up time : 15:21:23 UTC-08:00
Description: ! 0.0.3.3
Route Port, The Maximum Transmit Unit is 1500
Internet Address is 20.1.1.1/24
Encapsulation is TUNNEL, loopback not set
Tunnel source 10.0.1.1 (LoopBack0), destination 10.0.3.3
Tunnel protocol/transport GRE/IP, key disabled
keepalive disabled
Checksumming of packets disabled
Current system time: 15:21:37-08:00
300 seconds input rate 0 bits/sec, 0 packets/sec
300 seconds output rate 0 bits/sec, 0 packets/sec
13 seconds input rate 0 bits/sec, 0 packets/sec
13 seconds output rate 448 bits/sec, 0 packets/sec
9 packets output, 824 bytes
0 output error
Input bandwidth utilization : -
Output bandwidth utilization : -
iMaster NCE-Campus restricts RESTful APIs. If a client sends aGET requestthat invokes a RESTful API to obtain site information from iMaster NCE-Campus, which of the following fields should be included in the request header?
In a scenario where a VXLAN tunnel is dynamically established through BGP EVPN, which of the following BGP EVPN routes is used to advertise MAC addresses, ARP entries, and IRB routes?
NETCONF provides a set of mechanisms for managing network devices. What layers can NETCONF be conceptually partitioned into?
When a client invokes the iMaster NCE-Campus RESTful API, it sends an HTTP request. The server then returns the status code 401. Which of the following errors has occurred?
A network administrator runs the display telemetry subscription command on a device to check telemetry subscription information. The command output is as follows. Which of the following statements is incorrect?
[~CE] display telemetry subscription
Sub name : Sub1
Sensor group:
Sensor-name Sample-interval(ms) State
Sensor1 1000 RESOLVED
Destination group:
Dest-name Dest-IP Dest-port State Vpn-name Protocol
Dest1 192.168.56.1 20030 RESOLVED - GRPC
Sub state : PASSIVE
Total subscription number is : 1
On traditional campus networks, network admission control (NAC), VLAN, and ACL technologies are used to control users' network access rights. This results in heavy network O&M workload. Which of the following improvements does the free mobility solution of iMaster NCE-Campus make to traditional campus networks in terms of policy management and control?
Network Quality Analysis (NQA) is a real-time network performance detection and measurement technology. It monitors the performance of multiple protocols running on a network. Which of the following protocols can be monitored by NQA?
Which of the following technologies can be used to isolate users in the same VLAN?
SR-MPLS uses IGP extensions to advertise labels and reserve bandwidth to support high-bandwidth services.
During the migration test, which of the following indicates that the test is completed?
To prevent hackers from attacking user devices or networks using MAC addresses, you can configure MAC addresses of untrusted users as blackhole MAC addresses to filter out such invalid MAC addresses. When receiving a packet whose source or destination MAC address is a blackhole MAC address on a device, the device discards the packet.
In OSPF, an ABR translates all Type 7 LSAs in a Not-So-Stubby Area (NSSA) into Type 5 LSAs.
In a scenario where a VXLAN tunnel is dynamically established through BGP EVPN, which of the following statements about symmetric IRB forwarding are correct?
To enhance reliability, you can deploy Huawei iMaster NCE-WAN controllers in active/standby mode. Which of the following IP addresses must be configured to be the same for the active and standby controllers so that the controllers can be accessed properly? (Select All that Apply)
When configuring a static VXLAN tunnel, you need to manually configure the _____, VTEP IP address, and ingress replication list. (Enter only uppercase letters.)
In DU label advertisement mode, if the liberal label retention mode is used, the device reserves labels received from all the LDP peers regardless of whether the LDP peer is the optimal next hop for reaching the destination network.
In the CloudCampus public cloud scenario, if deployment through the Huawei registration query center is used, you do not need to configure DHCP Option 148 on the DHCP server of the campus network.
In a BGP/MPLS IP VPN scenario, if a PE and CE use OSPF to exchange routing information, domain IDs are used to identify whether the routes imported to VPN instances are from the same OSPF domain.
SR-MPLS uses the MPLS forwarding plane, and therefore requires MPLS to be enabled. Which of the following conditions must be met for MPLS to be automatically enabled on an interface? (Select all that apply)
Free mobility implements policy management and permission control based on users' VLAN IDs and IP addresses.
The Huawei SD-WAN solution has three types of channels. Drag the channel names to their corresponding callouts.

In the LDP session establishment process, the initiator sends an Initialization message for parameter negotiation. Which message will be sent by the responder if it does not accept negotiation parameters?
As shown in the following figure, OSPF is deployed on a campus network to implement network interconnection, and Area 1 is deployed as an NSSA. To enable R1 to access R4’s loopback interface address, an engineer imports a direct route to R4’s OSPF process. Which of the following statements about this scenario are correct?
[R4-ospf-1] import-route direct
Loopback0: 10.1.4.4/32