In FusionCompute, the security auditor in role-based access control (RBAC) mode is only permitted to view and export logs.
KVM is a type of paravirtualization. It can implement CPU and memory virtualization, but not device I/O virtualization.
Which of the following storage types isrecommendedfor VRM deployment during Huawei FusionCompute installation?
Which of the following statements aretrueabout the features and functions of the FusionCompute virtualization suite?
To enhance the security of user desktops, FusionAccess supports diverse access management policies. Which of the following statements about access management policies are true?
Complete the following configuration file for a network interface card (NIC) in theopenEuleroperating system to set astatic IP addressand enable the NIC toautomatically start upon system boot.
TYPE=Ethernet
BOOTPROTO=_____
NAME=enp0s4
DEVICE=enp0s4
ONBOOT=_____
IPADDR=172.28.100.100
NETMASK=255.255.255.0
Which of the following statements about the differences between adomainand anorganizational unit (OU)aretrue?
On FusionAccess, modifying or deleting a full copy template will affect the virtual machines created using the template.
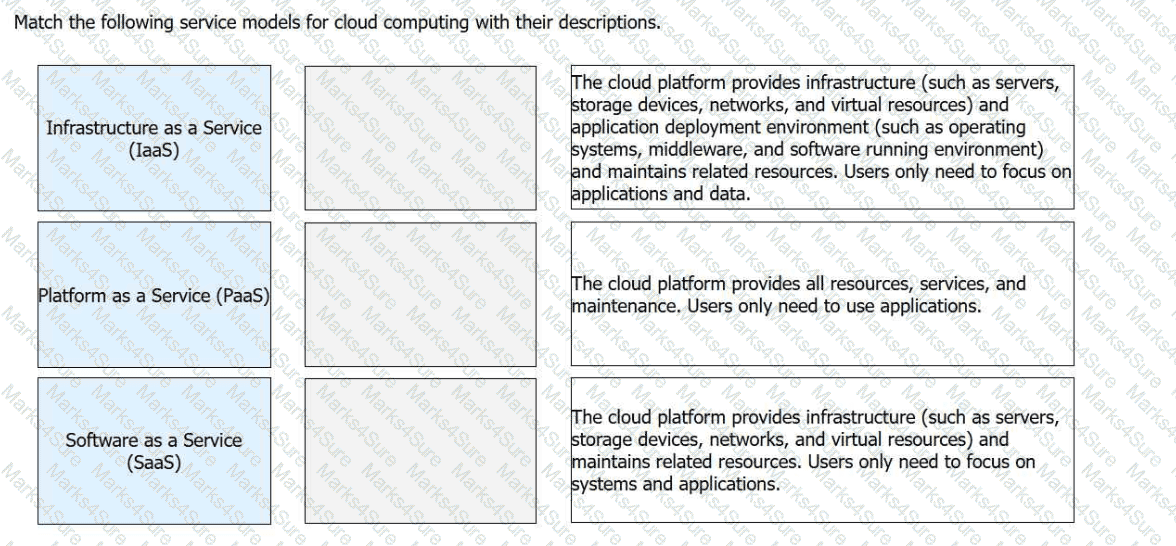
Match the following service models for cloud computing with their descriptions.
Which of the following operations must be performed on FusionAccess when you create a Windows template?
In compute virtualization, which of the following is the operating system running on a virtual machine (VM)?
After installing infrastructure VMs, you must configure the virtualized environment and vAG/vLB so that FusionAccess can work properly. Which of the following statements aboutFusionAccess initializationaretrue?
Which of the following statements is false about centralized storage and distributed storage?
During template creation on FusionAccess, you need to enter a temporary account to install Windows OS. Which of the following is the temporary account?
Which of the following statements about the differences betweenuser groupsandorganizational units (OUs)aretrue?
When a user VM uses a USB device, FusionAccess defaults to "USB Port Redirection". If the device is still unavailable, the"Device Redirection"policy can be configured.
On FusionAccess, when creating afull copy, QuickPrep, or linked clone template, the template must be added to a domain.
Which of the following parameters are mandatory for quickly provisioning desktops on FusionAccess?
In Huawei FusionCompute, which of the following functions enables virtual machines (VMs) to be migrated between CNA hosts with different CPU models?
Which of the following statements are true about the differences between OpenStack and FusionCompute?
Which of the following statements isfalseabout the development of cloud computing architecture?
In Huawei FusionCompute, a virtual machine running Linux is created. In this scenario, which of the following does thehost OSrun in?
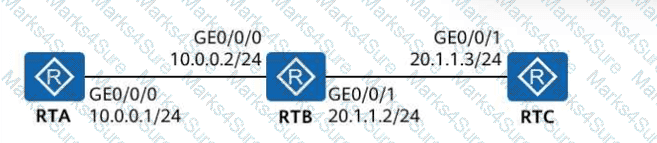
Which of the following statements arefalseabout the network shown in the figure?
Which of the following statements is false about a Virtual Image Management System (VIMS) file system?