What is one of the policies that a company should define for digital forensics?
which data should be routinely logged, where logs should be forwarded, and which logs should be archived
what are the first steps that a company can take to implement micro-segmentation in their environment
to which resources should various users be allowed access, based on their identity and the identity of their clients
which type of EAP method is most secure for authenticating wired and wireless users with 802.1
In the context of digital forensics, policy A is the most relevant. It defines which data should be logged, where logs should be forwarded for analysis or storage, and which logs should be archived for future forensic analysis or audit purposes. This ensures that evidence is preserved in a way that supports forensic activities.
You have been asked to send RADIUS debug messages from an AOS-CX switch to a central SIEM server at 10.5.15.6. The server is already defined on the switch with this command:
logging 10.5.15.6
You enter this command:
debug radius all
What is the correct debug destination?
file
console
buffer
syslog
The scenario involves an AOS-CX switch that needs to send RADIUS debug messages to a central SIEM server at 10.5.15.6. The switch has already been configured to send logs to the SIEM server with the command logging 10.5.15.6, and the command debug radius all has been entered to enable RADIUS debugging.
Debug Command: The debug radius all command enables debugging for all RADIUS-related events on the AOS-CX switch, generating detailed debug messages for RADIUS authentication, accounting, and other operations.
Debug Destination: Debug messages on AOS-CX switches can be sent to various destinations, such as the console, a file, the debug buffer, or a Syslog server. The logging 10.5.15.6 command indicates that the switch is configured to send logs to a Syslog server at 10.5.15.6 (using UDP port 514 by default, unless specified otherwise).
Option D, "syslog," is correct. To send RADIUS debug messages to the SIEM server, the debug destination must be set to "syslog," as the SIEM server is already defined as a Syslog destination with logging 10.5.15.6. The command to set the debug destination to Syslog is debug destination syslog, which ensures that the RADIUS debug messages are sent to the configured Syslog server (10.5.15.6).
Option A, "file," is incorrect. Sending debug messages to a file (e.g., using debug destination file) stores the messages on the switch’s filesystem, not on the SIEM server.
Option B, "console," is incorrect. Sending debug messages to the console (e.g., using debug destination console) displays them on the switch’s console session, not on the SIEM server.
Option C, "buffer," is incorrect. Sending debug messages to the buffer (e.g., using debug destination buffer) stores them in the switch’s debug buffer, which can be viewed with show debug buffer, but does not send them to the SIEM server.
The HPE Aruba Networking AOS-CX 10.12 System Management Guide states:
"To send debug messages, such as RADIUS debug messages, to a central SIEM server, first configure the Syslog server with the logging
Additionally, the HPE Aruba Networking AOS-CX 10.12 Security Guide notes:
"RADIUS debug messages can be sent to a Syslog server for centralized monitoring. After enabling RADIUS debugging with debug radius all, use debug destination syslog to send the messages to the Syslog server configured with the logging command, such as a SIEM server at 10.5.15.6." (Page 152, RADIUS Debugging Section)
You have detected a Rogue AP using the Security Dashboard Which two actions should you take in responding to this event? (Select two)
There is no need to locale the AP If you manually contain It.
This is a serious security event, so you should always contain the AP immediately regardless of your company's specific policies.
You should receive permission before containing an AP. as this action could have legal Implications.
For forensic purposes, you should copy out logs with relevant information, such as the time mat the AP was detected and the AP's MAC address.
There is no need to locate the AP If the Aruba solution is properly configured to automatically contain it.
When responding to the detection of a Rogue AP, it's important to consider legal implications and to gather forensic evidence:
You should receive permission before containing an AP (Option C), as containing it could disrupt service and may have legal implications, especially if the AP is on a network that the organization does not own.
For forensic purposes, it is essential to document the event by copying out logs with relevant information, such as the time the AP was detected and the AP's MAC address (Option D). This information could be crucial if legal action is taken or if a detailed analysis of the security breach is required.
Automatically containing an AP without consideration for the context (Options A and E) can be problematic, as it might inadvertently interfere with neighboring networks and cause legal issues. Immediate containment without consideration of company policy (Option B) could also violate established incident response procedures.
What is a correct guideline for the management protocols that you should use on AOS-CX switches?
Make sure that SSH is disabled and use HTTPS instead.
Make sure that Telnet is disabled and use SSH instead.
Make sure that Telnet is disabled and use TFTP instead.
Make sure that HTTPS is disabled and use SSH instead.
AOS-CX switches support various management protocols for administrative access, such as SSH, Telnet, HTTPS, and TFTP. Security best practices for managing network devices, including AOS-CX switches, emphasize using secure protocols to protect management traffic from eavesdropping and unauthorized access.
Option B, "Make sure that Telnet is disabled and use SSH instead," is correct. Telnet is an insecure protocol because it sends all data, including credentials, in plaintext, making it vulnerable to eavesdropping. SSH (Secure Shell) provides encrypted communication for remote management, ensuring that credentials and commands are protected. HPE Aruba Networking recommends disabling Telnet and enabling SSH for secure management access on AOS-CX switches.
Option A, "Make sure that SSH is disabled and use HTTPS instead," is incorrect. SSH and HTTPS serve different purposes: SSH is for CLI access, while HTTPS is for web-based management. Disabling SSH would prevent secure CLI access, which is not a recommended practice. Both SSH and HTTPS should be enabled for secure management.
Option C, "Make sure that Telnet is disabled and use TFTP instead," is incorrect. TFTP (Trivial File Transfer Protocol) is used for file transfers (e.g., firmware updates), not for management access like Telnet or SSH. TFTP is also insecure (no encryption), so it’s not a suitable replacement for Telnet.
Option D, "Make sure that HTTPS is disabled and use SSH instead," is incorrect. HTTPS is used for secure web-based management and should not be disabled. Both HTTPS and SSH are secure protocols and should be used together for different management interfaces (web and CLI, respectively).
The HPE Aruba Networking AOS-CX 10.12 Security Guide states:
"For secure management of AOS-CX switches, disable insecure protocols like Telnet, which sends data in plaintext, and use SSH instead. SSH provides encrypted communication for CLI access, protecting credentials and commands from eavesdropping. Use the command no telnet-server to disable Telnet and ssh-server to enable SSH. Additionally, enable HTTPS for web-based management with https-server to ensure all management traffic is encrypted." (Page 195, Secure Management Protocols Section)
Additionally, the HPE Aruba Networking Security Best Practices Guide notes:
"A key guideline for managing AOS-CX switches is to disable Telnet and enable SSH for CLI access. Telnet is insecure and should not be used in production environments, as it transmits credentials in plaintext. SSH ensures secure remote management, and HTTPS should also be enabled for web access." (Page 25, Management Security Section)
You have enabled 802.1X authentication on an AOS-CX switch, including on port 1/1/1. That port has these port-access roles configured on it:
Fallback role = roleA
Auth role = roleB
Critical role = roleCNo other port-access roles are configured on the port. A client connects to that port. The user succeeds authentication, and CPPM does not send an Aruba-User-Role VSA.What role does the client receive?
The client receives roleC.
The client is denied access.
The client receives roleB.
The client receives roleA.
In an AOS-CX switch environment, 802.1X authentication is used to authenticate clients connecting to ports, and roles are assigned based on the authentication outcome and configuration. The roles mentioned in the question—fallback, auth, and critical—have specific purposes in the AOS-CX port-access configuration:
Auth role (roleB): This role is applied when a client successfully authenticates via 802.1X and no specific role is assigned by the RADIUS server (e.g., via an Aruba-User-Role VSA). It is the default role for successful authentication.
Fallback role (roleA): This role is applied when no authentication method is attempted (e.g., the client does not support 802.1X or MAC authentication and no other method is configured).
Critical role (roleC): This role is applied when the switch cannot contact the RADIUS server (e.g., during a server timeout or failure), allowing the client to have limited access in a "critical" state.
In this scenario, the client successfully authenticates via 802.1X, and CPPM does not send an Aruba-User-Role VSA. Since authentication is successful, the switch applies the auth role (roleB) as the default role for successful authentication when no specific role is provided by the RADIUS server.
Option A, "The client receives roleC," is incorrect because the critical role is only applied when the RADIUS server is unreachable, which is not the case here since authentication succeeded.
Option B, "The client is denied access," is incorrect because the client successfully authenticated, so access is granted with the appropriate role.
Option D, "The client receives roleA," is incorrect because the fallback role is applied only when no authentication is attempted, not when authentication succeeds.
The HPE Aruba Networking AOS-CX 10.12 Security Guide states:
"When a client successfully authenticates using 802.1X, the switch assigns the client to the auth role configured for the port, unless the RADIUS server specifies a different role via the Aruba-User-Role VSA. If no Aruba-User-Role VSA is present in the Access-Accept message, the auth role is applied." (Page 132, 802.1X Authentication Section)
Additionally, the guide clarifies the roles:
"Auth role: Applied after successful 802.1X or MAC authentication if no role is specified by the RADIUS server."
"Fallback role: Applied when no authentication method is attempted."
"Critical role: Applied when the RADIUS server is unavailable." (Page 134, Port-Access Roles Section)
You have been asked to rind logs related to port authentication on an ArubaOS-CX switch for events logged in the past several hours But. you are having trouble searching through the logs What is one approach that you can take to find the relevant logs?
Add the "-C and *-c port-access" options to the "show logging" command.
Configure a logging Tiller for the "port-access" category, and apply that filter globally.
Enable debugging for "portaccess" to move the relevant logs to a buffer.
Specify a logging facility that selects for "port-access" messages.
In ArubaOS-CX, managing and searching logs can be crucial for tracking and diagnosing issues related to network operations such as port authentication. To efficiently find logs related to port authentication, configuring a logging filter specifically for this category is highly effective.
Logging Filter Configuration: In ArubaOS-CX, you can configure logging filters to refine the logs that are collected and viewed. By setting up a filter for the "port-access" category, you focus the logging system to only capture and display entries related to port authentication events. This approach reduces the volume of log data to sift through, making it easier to identify relevant issues.
Global Application of Filter: Applying the filter globally ensures that all relevant log messages, regardless of their origin within the switch's modules or interfaces, are captured under the specified category. This global application is crucial for comprehensive monitoring across the entire device.
Alternative Options and Their Evaluation:
Option A: Adding "-C and *-c port-access" to the "show logging" command is not a standard command format in ArubaOS-CX for filtering logs directly through the show command.
Option C: Enabling debugging for "portaccess" indeed increases the detail of logs but primarily serves to provide real-time diagnostic information rather than filtering existing logs.
Option D: Specifying a logging facility focuses on routing logs to different destinations or subsystems and does not inherently filter by log category like port-access.
What distinguishes a Distributed Denial of Service (DDoS) attack from a traditional Denial or service attack (DoS)?
A DDoS attack originates from external devices, while a DoS attack originates from internal devices
A DDoS attack is launched from multiple devices, while a DoS attack is launched from a single device
A DoS attack targets one server, a DDoS attack targets all the clients that use a server
A DDoS attack targets multiple devices, while a DoS Is designed to Incapacitate only one device
The main distinction between a Distributed Denial of Service (DDoS) attack and a traditional Denial of Service (DoS) attack is that a DDoS attack is launched from multiple devices, whereas a DoS attack originates from a single device. This distinction is critical because the distributed nature of a DDoS attack makes it more difficult to mitigate. Multiple attacking sources can generate a higher volume of malicious traffic, overwhelming the target more effectively than a single source, as seen in a DoS attack. DDoS attacks exploit a variety of devices across the internet, often coordinated using botnets, to flood targets with excessive requests, leading to service degradation or complete service denial.
A company has AOS-CX switches deployed in a two-tier topology that uses OSPF routing at the core.
You need to prevent ARP poisoning attacks. To meet this need, what is one technology that you could apply to user VLANs on access layer switches? (Select two.)
ARP inspection
OSPF passive interface
BPDU guard (protection)
DHCPv4 snooping
BPDU filtering
The scenario involves AOS-CX switches in a two-tier topology (access and core layers) using OSPF routing at the core. The goal is to prevent ARP poisoning attacks on user VLANs at the access layer switches, where end-user devices connect. ARP poisoning (also known as ARP spoofing) is an attack where a malicious device sends fake ARP messages to associate its MAC address with the IP address of another device (e.g., the default gateway), allowing the attacker to intercept traffic.
ARP Inspection (Dynamic ARP Inspection, DAI): This feature prevents ARP poisoning by validating ARP packets against a trusted database of IP-to-MAC bindings. On AOS-CX switches, ARP inspection uses the DHCP snooping binding table to verify that ARP messages come from legitimate devices. If an ARP packet does not match the binding table, it is dropped.
DHCPv4 Snooping: This feature protects against rogue DHCP servers and builds a binding table of legitimate IP-to-MAC mappings by snooping DHCP traffic. The binding table is used by ARP inspection to validate ARP packets. DHCP snooping must be enabled before ARP inspection can function effectively, as it provides the trusted data for validation.
Option A, "ARP inspection," is correct. ARP inspection (DAI) directly prevents ARP poisoning by ensuring that ARP packets are legitimate, making it a key technology for this purpose.
Option B, "OSPF passive interface," is incorrect. OSPF passive interface is used to prevent OSPF from sending routing updates on specific interfaces, typically to reduce routing protocol traffic on user-facing interfaces. It does not prevent ARP poisoning, which is a Layer 2 attack.
Option C, "BPDU guard (protection)," is incorrect. BPDU guard protects against spanning tree protocol (STP) attacks by disabling a port if it receives BPDUs (e.g., from an unauthorized switch). It does not address ARP poisoning, which is unrelated to STP.
Option D, "DHCPv4 snooping," is correct. DHCP snooping is a prerequisite for ARP inspection, as it builds the binding table used to validate ARP packets. It also protects against rogue DHCP servers, which can indirectly contribute to ARP poisoning by assigning incorrect IP addresses.
Option E, "BPDU filtering," is incorrect. BPDU filtering prevents a port from sending or receiving BPDUs, which can be used to protect against STP attacks, but it does not prevent ARP poisoning.
The HPE Aruba Networking AOS-CX 10.12 Security Guide states:
"To prevent ARP poisoning attacks on user VLANs, enable Dynamic ARP Inspection (DAI) on access layer switches. DAI validates ARP packets against the DHCP snooping binding table to ensure they come from legitimate devices. Use the command ip arp inspection vlan
Additionally, the guide notes:
"DHCP snooping and ARP inspection work together to protect against Layer 2 attacks like ARP poisoning. DHCP snooping builds a trusted database of IP-to-MAC bindings, which ARP inspection uses to filter out malicious ARP packets." (Page 146, Best Practices Section)
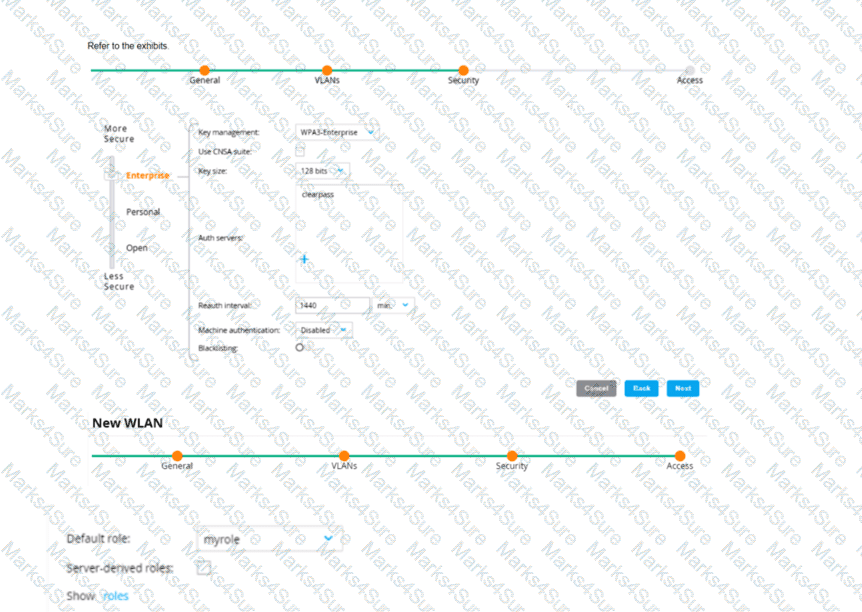
An admin has created a WLAN that uses the settings shown in the exhibits (and has not otherwise adjusted the settings in the AAA profile) A client connects to the WLAN Under which circumstances will a client receive the default role assignment?
The client has attempted 802 1X authentication, but the MC could not contact the authentication server
The client has attempted 802 1X authentication, but failed to maintain a reliable connection, leading to a timeout error
The client has passed 802 1X authentication, and the value in the Aruba-User-Role VSA matches a role on the MC
The client has passed 802 1X authentication and the authentication server did not send an Aruba-User-Role VSA
In the context of an Aruba Mobility Controller (MC) configuration, a client will receive the default role assignment if they have passed 802.1X authentication and the authentication server did not send an Aruba-User-Role Vendor Specific Attribute (VSA). The default role is assigned by the MC when a client successfully authenticates but the authentication server provides no specific role instruction. This behavior ensures that a client is not left without any role assignment, which could potentially lead to a lack of network access or access control. This default role assignment mechanism is part of Aruba's role-based access control, as documented in the ArubaOS user guide and best practices.
Which scenario requires the Aruba Mobility Controller to use a Server Certificate?
Obtain downloadable user roles (DURs) from ClearPass.
Synchronize its clock with an NTP server that requires authentication.
Use RadSec for enforcing 802.1X authentication to ClearPass.
Use RADIUS for enforcing 802.1X authentication to ClearPass.
A Server Certificate is required by Aruba Mobility Controller when using RadSec to secure RADIUS communication. RadSec provides a secure transport for RADIUS traffic through SSL/TLS which requires the use of a Server Certificate to establish the secure tunnel. In the other scenarios listed, a Server Certificate is not explicitly required for the operations mentioned.
A company has added a new user group. Users in the group try to connect to the WLAN and receive errors that the connection has no Internet access. The users cannot reach any resources. The first exhibit shows the record for one of the users who cannot connect. The second exhibit shows the role to which the ArubaOS device assigned the user's client.
What is a likely problem?
The ArubaOS device has a server derivation rule configured on it that has overridden the role sent by CPPM.
The ArubaOS device does not have the correct RADIUS dictionaries installed on it to under-stand the Aruba-User-Role VSA.
The role name that CPPM is sending does not match the role name configured on the Aru-baOS device.
The clients rejected the server authentication on their side because they do not have the root CA for CPPM's RADIUS/EAP certificate.
The image indicates that there is an issue with the user role assignment, which is key to network access in ArubaOS. If the user role name sent by CPPM doesn't match any of the roles defined in the ArubaOS, then the user will be assigned a default or incorrect role that does not have the necessary permissions, thus leading to the connection errors and lack of Internet access. Ensuring that the role names are consistent between CPPM and ArubaOS can resolve this issue.
What is one benefit of enabling Enhanced Secure mode on an ArubaOS-Switch?
Control Plane policing rate limits edge ports to mitigate DoS attacks on network servers.
A self-signed certificate is automatically added to the switch trusted platform module (TPM).
Insecure algorithms for protocol such as SSH are automatically disabled.
All interfaces have 802.1X authentication enabled on them by default.
In the context of ArubaOS-Switches, enabling Enhanced Secure mode has several benefits, one of which includes disabling insecure algorithms for protocols such as SSH. This is in line with security best practices, as older, less secure algorithms are known to be vulnerable to various types of cryptographic attacks. When Enhanced Secure mode is enabled, the switch automatically restricts the use of such algorithms, thereby enhancing the security of management access.
You configure an ArubaOS-Switch to enforce 802.1X authentication with ClearPass Policy Manager (CPPM) denned as the RADIUS server Clients cannot authenticate You check Aruba ClearPass Access Tracker and cannot find a record of the authentication attempt.
What are two possible problems that have this symptom? (Select two)
users are logging in with the wrong usernames and passwords or invalid certificates.
Clients are configured to use a mismatched EAP method from the one In the CPPM service.
The RADIUS shared secret does not match between the switch and CPPM.
CPPM does not have a network device defined for the switch's IP address.
Clients are not configured to trust the root CA certificate for CPPM's RADIUS/EAP certificate.
If clients cannot authenticate and there is no record of the authentication attempt in Aruba ClearPass Access Tracker, two possible problems that could cause this symptom are:
The RADIUS shared secret does not match between the switch and CPPM. This mismatch would prevent the switch and CPPM from successfully communicating, so authentication attempts would fail, and no record would appear in Access Tracker.
CPPM does not have a network device profile defined for the switch's IP address. Without a network device profile, CPPM would not recognize authentication attempts coming from the switch and would not process them, resulting in no logs in Access Tracker.
The other options are incorrect because:
Users logging in with the wrong credentials would still generate an attempt record in Access Tracker.
Clients configured to use a mismatched EAP method would also generate an attempt record in Access Tracker.
Clients not configured to trust the root CA certificate for CPPM's RADIUS/EAP certificate might fail authentication, but the attempt would still be logged in Access Tracker.
What is a correct description of a stage in the Lockheed Martin kill chain?
In the delivery stage, the hacker delivers malware to targeted users, often with spear phishing methods.
In the installation phase, hackers seek to install vulnerabilities in operating systems across the network.
In the weaponization stage, malware installed in the targeted network seeks to attack intrusion prevention systems (IPS).
In the exploitation phase, hackers conduct social engineering attacks to exploit weak algorithms and crack user accounts.
The Lockheed Martin Cyber Kill Chain is a framework that describes the stages of a cyber attack, from initial reconnaissance to achieving the attacker’s objective. It is often referenced in HPE Aruba Networking security documentation to help organizations understand and mitigate threats.
Option A, "In the delivery stage, the hacker delivers malware to targeted users, often with spear phishing methods," is correct. The delivery stage in the Lockheed Martin kill chain involves the attacker transmitting the weaponized payload (e.g., malware) to the target. Spear phishing, where the attacker sends a targeted email with a malicious attachment or link, is a common delivery method. This stage follows reconnaissance (gathering information) and weaponization (creating the malware).
Option B, "In the installation phase, hackers seek to install vulnerabilities in operating systems across the network," is incorrect. The installation phase involves the attacker installing the malware on the target system to establish persistence (e.g., by creating a backdoor). It does not involve "installing vulnerabilities"; vulnerabilities are pre-existing weaknesses that the attacker exploits in the exploitation phase.
Option C, "In the weaponization stage, malware installed in the targeted network seeks to attack intrusion prevention systems (IPS)," is incorrect. The weaponization stage occurs before delivery and involves the attacker creating a deliverable payload (e.g., combining malware with an exploit). The malware is not yet installed in the target network during this stage, and attacking an IPS is not the purpose of weaponization.
Option D, "In the exploitation phase, hackers conduct social engineering attacks to exploit weak algorithms and crack user accounts," is incorrect. The exploitation phase involves the attacker exploiting a vulnerability (e.g., a software flaw) to execute the malware on the target system. Social engineering (e.g., phishing) is typically part of the delivery stage, not exploitation, and "exploiting weak algorithms" is not a standard description of this phase.
The HPE Aruba Networking Security Guide states:
"The Lockheed Martin Cyber Kill Chain describes the stages of a cyber attack. In the delivery stage, the attacker delivers the weaponized payload to the target, often using methods like spear phishing emails with malicious attachments or links. This stage follows reconnaissance (gathering information about the target) and weaponization (creating the malware payload)." (Page 18, Cyber Kill Chain Overview Section)
Additionally, the HPE Aruba Networking AOS-8 8.11 User Guide notes:
"Understanding the Lockheed Martin kill chain helps in threat mitigation. The delivery stage involves the attacker sending malware to the target, commonly through spear phishing, where a targeted email tricks the user into downloading the malware or clicking a malicious link." (Page 420, Threat Mitigation Section)
An organization has HPE Aruba Networking infrastructure, including AOS-CX switches and an AOS-8 mobility infrastructure with Mobility Controllers (MCs) and APs. Clients receive certificates from ClearPass Onboard. The infrastructure devices authenticate clients to ClearPass Policy Manager (CPPM). The company wants to start profiling clients to take their device type into account in their access rights.
What is a role that CPPM should play in this plan?
Assigning clients to their device categories
Helping to forward profiling information to the component responsible for profiling
Accepting and enforcing CoA messages
Enforcing access control decisions
HPE Aruba Networking ClearPass Policy Manager (CPPM) is a network access control (NAC) solution that provides device profiling, authentication, and policy enforcement. In this scenario, the company wants to profile clients to determine their device type and use that information to define access rights. Device profiling in ClearPass involves identifying and categorizing devices based on various attributes, such as DHCP fingerprints, HTTP User-Agent strings, or TCP fingerprinting, to assign them to specific device categories (e.g., Windows, macOS, IoT devices, etc.). These categories can then be used in policy decisions to grant or restrict access.
Option A, "Assigning clients to their device categories," directly aligns with ClearPass’s role in device profiling. ClearPass collects profiling data from network devices (like APs, MCs, or switches) and uses its profiling engine to categorize devices. This categorization is a core function of ClearPass Device Insight, which is integrated into CPPM, and is used to build policies based on device type.
Option B, "Helping to forward profiling information to the component responsible for profiling," is incorrect because ClearPass itself is the component responsible for profiling. It doesn’t forward data to another system for profiling; instead, it collects data (e.g., via DHCP snooping, HTTP headers, or mirrored traffic) and processes it internally.
Option C, "Accepting and enforcing CoA messages," refers to ClearPass’s ability to send Change of Authorization (CoA) messages to network devices to dynamically change a client’s access rights (e.g., reassign a role or disconnect a session). While CoA is part of ClearPass’s enforcement capabilities, it is not directly related to the profiling process or categorizing devices.
Option D, "Enforcing access control decisions," is a broader function of ClearPass. While ClearPass does enforce access control decisions based on profiling data (e.g., by assigning roles or VLANs), the question specifically asks about its role in the profiling process, not the enforcement step that follows.
The HPE Aruba Networking ClearPass Policy Manager 6.11 User Guide states:
"ClearPass Policy Manager provides a mechanism to profile devices that connect to the network. Device profiling collects information about a device during its authentication or through network monitoring (e.g., DHCP, HTTP, or SNMP). The collected data is used to identify and categorize the device into a device category (e.g., Computer, Smartphone, Printer, etc.) and device family (e.g., Windows, Android, etc.). These categories can then be used in policy conditions to enforce access control." (Page 245, Device Profiling Section)
Additionally, the ClearPass Device Insight Data Sheet notes:
"ClearPass Device Insight uses a combination of passive and active profiling techniques to identify and classify devices. It assigns devices to categories based on their attributes, enabling organizations to create granular access policies." (Page 2)
What is one way a honeypot can be used to launch a man-in-the-middle (MITM) attack to wireless clients?
It uses ARP poisoning to disconnect wireless clients from the legitimate wireless network and force clients to connect to the hacker’s wireless network instead.
It runs an NMap scan on the wireless client to find the client's MAC and IP address. The hacker then connects to another network and spoofs those addresses.
It uses a combination of software and hardware to jam the RF band and prevent the client from connecting to any wireless networks.
It examines wireless clients' probes and broadcasts the SSIDs in the probes, so that wireless clients will connect to it automatically.
A honeypot in the context of wireless networks is a rogue access point (AP) set up by an attacker to lure wireless clients into connecting to it, often to steal credentials, intercept traffic, or launch further attacks. A man-in-the-middle (MITM) attack involves the attacker positioning themselves between the client and the legitimate network to intercept or manipulate traffic.
Option D, "It examines wireless clients' probes and broadcasts the SSIDs in the probes, so that wireless clients will connect to it automatically," is correct. Wireless clients periodically send probe requests to discover available networks, including SSIDs they have previously connected to (stored in their Preferred Network List, PNL). A honeypot AP can capture these probe requests, identify the SSIDs the client is looking for, and then broadcast those SSIDs. If the honeypot AP has a stronger signal or the legitimate AP is not available, the client may automatically connect to the honeypot AP (especially if the SSID is in the PNL and auto-connect is enabled). Once connected, the attacker can intercept the client’s traffic, making this an effective MITM attack.
Option A, "It uses ARP poisoning to disconnect wireless clients from the legitimate wireless network and force clients to connect to the hacker’s wireless network instead," is incorrect. ARP poisoning is a technique used on wired networks (or within the same broadcast domain) to redirect traffic by spoofing ARP responses. In a wireless context, ARP poisoning is not typically used to disconnect clients from a legitimate AP. Instead, techniques like deauthentication attacks or SSID spoofing (as in Option D) are more common.
Option B, "It runs an NMap scan on the wireless client to find the client's MAC and IP address. The hacker then connects to another network and spoofs those addresses," is incorrect. NMap scans are used for network discovery and port scanning, not for launching an MITM attack via a honeypot. Spoofing MAC and IP addresses on another network does not position the attacker as a honeypot to intercept wireless traffic.
Option C, "It uses a combination of software and hardware to jam the RF band and prevent the client from connecting to any wireless networks," is incorrect. Jamming the RF band would disrupt all wireless communication, including the attacker’s honeypot, and would not facilitate an MITM attack. Jamming might be used in a denial-of-service (DoS) attack, but not for MITM.
The HPE Aruba Networking AOS-8 8.11 User Guide states:
"A common technique for launching a man-in-the-middle (MITM) attack using a honeypot AP involves capturing wireless clients’ probe requests to identify SSIDs in their Preferred Network List (PNL). The honeypot AP then broadcasts these SSIDs, tricking clients into connecting automatically if the SSID matches a known network and auto-connect is enabled. Once connected, the attacker can intercept the client’s traffic, performing an MITM attack." (Page 422, Wireless Threats Section)
Additionally, the HPE Aruba Networking Security Guide notes:
"Honeypot APs can be used to launch MITM attacks by spoofing SSIDs that clients are probing for. Clients often automatically connect to known SSIDs in their PNL, especially if the legitimate AP is unavailable or the honeypot AP has a stronger signal, allowing the attacker to intercept traffic." (Page 72, Wireless MITM Attacks Section)
How can hackers implement a man-in-the-middle (MITM) attack against a wireless client?
The hacker uses a combination of software and hardware to jam the RF band and prevent the client from connecting to any wireless networks.
The hacker runs an NMap scan on the wireless client to find its MAC and IP address. The hacker then connects to another network and spoofs those addresses.
The hacker connects a device to the same wireless network as the client and responds to the client’s ARP requests with the hacker device’s MAC address.
The hacker uses spear-phishing to probe for the IP addresses that the client is attempting to reach. The hacker device then spoofs those IP addresses.
A common method for hackers to perform a man-in-the-middle (MITM) attack on a wireless network is by ARP poisoning. The attacker connects to the same network as the victim and sends false ARP messages over the network. This causes the victim's device to send traffic to the attacker's machine instead of the legitimate destination, allowing the attacker to intercept the traffic.
A company has Aruba Mobility Controllers (MCs), Aruba campus APs, and ArubaOS-CX switches. The company plans to use ClearPass Policy Manager (CPPM) to classify endpoints by type. The company is contemplating the use of ClearPass’s TCP fingerprinting capabilities.
What is a consideration for using those capabilities?
ClearPass admins will need to provide the credentials of an API admin account to configure on Aruba devices.
You will need to mirror traffic to one of CPPM's span ports from a device such as a core routing switch.
ArubaOS-CX switches do not offer the support necessary for CPPM to use TCP fingerprinting on wired endpoints.
TCP fingerprinting of wireless endpoints requires a third-party Mobility Device Management (MDM) solution.
ClearPass Policy Manager (CPPM) uses various methods to classify endpoints, and one of them is TCP fingerprinting, which involves analyzing TCP/IP packets to identify the type of device or operating system sending them. To utilize TCP fingerprinting capabilities, network traffic needs to be accessible to the CPPM. This can be done by mirroring traffic to CPPM’s span port from a device that can see the traffic, like a core routing switch. This approach allows CPPM to observe the TCP characteristics of devices as they communicate over the network, enabling it to make more accurate decisions for device classification.
How can ARP be used to launch attacks?
Hackers can use ARP to change their NIC's MAC address so they can impersonate legiti-mate users.
Hackers can exploit the fact that the port used for ARP must remain open and thereby gain remote access to another user's device.
A hacker can use ARP to claim ownership of a CA-signed certificate that actually belongs to another device.
A hacker can send gratuitous ARP messages with the default gateway IP to cause devices to redirect traffic to the hacker's MAC address.
ARP (Address Resolution Protocol) can indeed be exploited to conduct various types of attacks, most notably ARP spoofing/poisoning. Gratuitous ARP is a special kind of ARP message which is used by an IP node to announce or update its IP to MAC mapping to the entire network. A hacker can abuse this by sending out gratuitous ARP messages pretending to associate the IP address of the router (default gateway) with their own MAC address. This results in traffic that was supposed to go to the router being sent to the attacker instead, thus potentially enabling the attacker to intercept, modify, or block traffic.
What is one of the roles of the network access server (NAS) in the AAA framework?
It negotiates with each user’s device to determine which EAP method is used for authentication.
It determines which resources authenticated users are allowed to access and monitors each user’s session.
It enforces access to network services and sends accounting information to the AAA server.
It authenticates legitimate users and uses policies to determine which resources each user is allowed to access.
The AAA (Authentication, Authorization, and Accounting) framework is used in network security to manage user access. In this framework, the Network Access Server (NAS) plays a specific role. In an HPE Aruba Networking environment, the NAS is typically a device like a Mobility Controller (MC) or an AOS-CX switch that interacts with an AAA server (e.g., ClearPass Policy Manager, CPPM) to authenticate users.
NAS Role in AAA:
Authentication: The NAS acts as a client to the AAA server (e.g., via RADIUS), forwarding authentication requests from the user’s device to the server. It does not perform the authentication itself; the AAA server authenticates the user.
Authorization: After authentication, the NAS receives authorization attributes from the AAA server (e.g., a user role via Aruba-User-Role VSA) and enforces access policies (e.g., firewall rules, VLAN assignment) based on those attributes.
Accounting: The NAS sends accounting information (e.g., session start/stop, data usage) to the AAA server to track user activity.
Option A, "It negotiates with each user’s device to determine which EAP method is used for authentication," is incorrect. The NAS does not negotiate the EAP method with the user’s device. The EAP method (e.g., EAP-TLS, PEAP) is determined by the configuration on the NAS and the AAA server, and the client must support the configured method. The negotiation of EAP methods occurs between the client (supplicant) and the AAA server, with the NAS acting as a pass-through.
Option B, "It determines which resources authenticated users are allowed to access and monitors each user’s session," is incorrect. The NAS enforces access policies based on authorization attributes received from the AAA server, but it does not determine which resources users can access—that decision is made by the AAA server based on its policies. Monitoring sessions is part of accounting, but this option overstates the NAS’s role in determining access.
Option C, "It enforces access to network services and sends accounting information to the AAA server," is correct. The NAS enforces access by applying policies (e.g., firewall rules, VLANs) based on the authorization attributes received from the AAA server. It also sends accounting information (e.g., session start/stop, data usage) to the AAA server to track user activity, fulfilling its role in the accounting part of AAA.
Option D, "It authenticates legitimate users and uses policies to determine which resources each user is allowed to access," is incorrect. The NAS does not authenticate users; the AAA server performs authentication. The NAS also does not determine resource access; it enforces the policies provided by the AAA server.
The HPE Aruba Networking AOS-8 8.11 User Guide states:
"In the AAA framework, the Network Access Server (NAS), such as a Mobility Controller, acts as a client to the AAA server (e.g., a RADIUS server). The NAS forwards authentication requests from the user’s device to the AAA server, enforces access to network services based on the authorization attributes returned by the server (e.g., user role, VLAN), and sends accounting information, such as session start and stop records, to the AAA server for tracking." (Page 310, AAA Framework Section)
Additionally, the HPE Aruba Networking ClearPass Policy Manager 6.11 User Guide notes:
"The NAS in the AAA framework, such as an Aruba Mobility Controller, does not authenticate users itself; it forwards authentication requests to the AAA server (ClearPass). After authentication, the NAS enforces access policies based on the server’s response and sends accounting data to the AAA server to log user activity, such as session duration and data usage." (Page 280, NAS Role in AAA Section)
You have a network with AOS-CX switches for which HPE Aruba Networking ClearPass Policy Manager (CPPM) acts as the TACACS+ server. When an admin authenticates, CPPM sends a response with:
Aruba-Priv-Admin-User = 1
TACACS+ privilege level = 15What happens to the user?
The user receives auditors access.
The user receives no access.
The user receives administrators access.
The user receives operators access.
HPE Aruba Networking AOS-CX switches support TACACS+ for administrative authentication, where ClearPass Policy Manager (CPPM) can act as the TACACS+ server. When an admin authenticates, CPPM sends a TACACS+ response that includes attributes such as the TACACS+ privilege level and vendor-specific attributes (VSAs) like Aruba-Priv-Admin-User.
In this scenario, CPPM sends:
TACACS+ privilege level = 15: In TACACS+, privilege level 15 is the highest level and typically grants full administrative access (equivalent to a superuser or administrator role).
Aruba-Priv-Admin-User = 1: This Aruba-specific VSA indicates that the user should be granted the highest level of administrative access on the switch.
On AOS-CX switches, the privilege level 15 maps to the administrator role, which provides full read-write access to all switch functions. The Aruba-Priv-Admin-User = 1 attribute reinforces this by explicitly assigning the admin role, ensuring the user has unrestricted access.
Option A, "The user receives auditors access," is incorrect because auditors typically have read-only access, which corresponds to a lower privilege level (e.g., 1 or 3) on AOS-CX switches.
Option B, "The user receives no access," is incorrect because the authentication was successful, and CPPM sent a response granting access with privilege level 15.
Option D, "The user receives operators access," is incorrect because operators typically have a lower privilege level (e.g., 5 or 7), which provides limited access compared to an administrator.
The HPE Aruba Networking AOS-CX 10.12 Security Guide states:
"When using TACACS+ for administrative authentication, the switch interprets the privilege level returned by the TACACS+ server. A privilege level of 15 maps to the administrator role, granting full read-write access to all switch functions. The Aruba-Priv-Admin-User VSA, when set to 1, explicitly assigns the admin role, ensuring the user has unrestricted access." (Page 189, TACACS+ Authentication Section)
Additionally, the HPE Aruba Networking ClearPass Policy Manager 6.11 User Guide notes:
"ClearPass can send the Aruba-Priv-Admin-User VSA in a TACACS+ response to specify the administrative role on Aruba devices. A value of 1 indicates the admin role, which provides full administrative privileges." (Page 312, TACACS+ Enforcement Section)
You have an HPE Aruba Networking Mobility Controller (MC) that is locked in a closet. What is another step that HPE Aruba Networking recommends to protect the MC from unauthorized access?
Set the local admin password to a long random value that is unknown or locked up securely.
Disable local authentication of administrators entirely.
Change the password recovery password.
Use local authentication rather than external authentication to authenticate admins.
The scenario involves an HPE Aruba Networking Mobility Controller (MC) that is physically secured in a locked closet, which provides protection against physical tampering. However, additional steps are needed to protect the MC from unauthorized access, particularly through administrative interfaces (e.g., SSH, web UI, console).
Option A, "Set the local admin password to a long random value that is unknown or locked up securely," is correct. HPE Aruba Networking recommends securing administrative access to the MC by setting a strong, random password for the local admin account (e.g., the default "admin" user). The password should be long (e.g., 16+ characters), random, and stored securely (e.g., in a password manager or safe). This ensures that even if an attacker gains physical access to the MC (e.g., by bypassing the locked closet) or attempts remote access, they cannot easily guess or brute-force the password.
Option B, "Disable local authentication of administrators entirely," is incorrect. Disabling local authentication entirely would prevent any fallback access to the MC if external authentication (e.g., RADIUS, TACACS+) fails. HPE Aruba Networking recommends maintaining a local admin account as a backup, but securing it with a strong password.
Option C, "Change the password recovery password," is incorrect. AOS-8 Mobility Controllers do not have a specific "password recovery password." Password recovery typically involves physical access to the device (e.g., via the console port) and a factory reset, which would be mitigated by the locked closet. This option is not a standard recommendation for securing the MC.
Option D, "Use local authentication rather than external authentication to authenticate admins," is incorrect. HPE Aruba Networking recommends using external authentication (e.g., RADIUS or TACACS+) for centralized management and stronger security (e.g., two-factor authentication). Local authentication should be a fallback, not the primary method, and it must be secured with a strong password.
The HPE Aruba Networking AOS-8 8.11 User Guide states:
"To protect the Mobility Controller from unauthorized access, even if it is physically secured in a locked closet, set the local admin password to a long, random value that is unknown or locked up securely. For example, use a password of at least 16 characters generated by a password manager, and store it in a secure location (e.g., a safe). This ensures that the local admin account, which is used as a fallback, is protected against unauthorized access attempts." (Page 385, Securing Administrative Access Section)
Additionally, the HPE Aruba Networking Security Best Practices Guide notes:
"A recommended step to secure the Mobility Controller is to set a strong, random password for the local admin account. The password should be long (e.g., 16+ characters), randomly generated, and stored securely to prevent unauthorized access, even if the device is physically protected in a locked closet." (Page 28, Administrative Security Section)
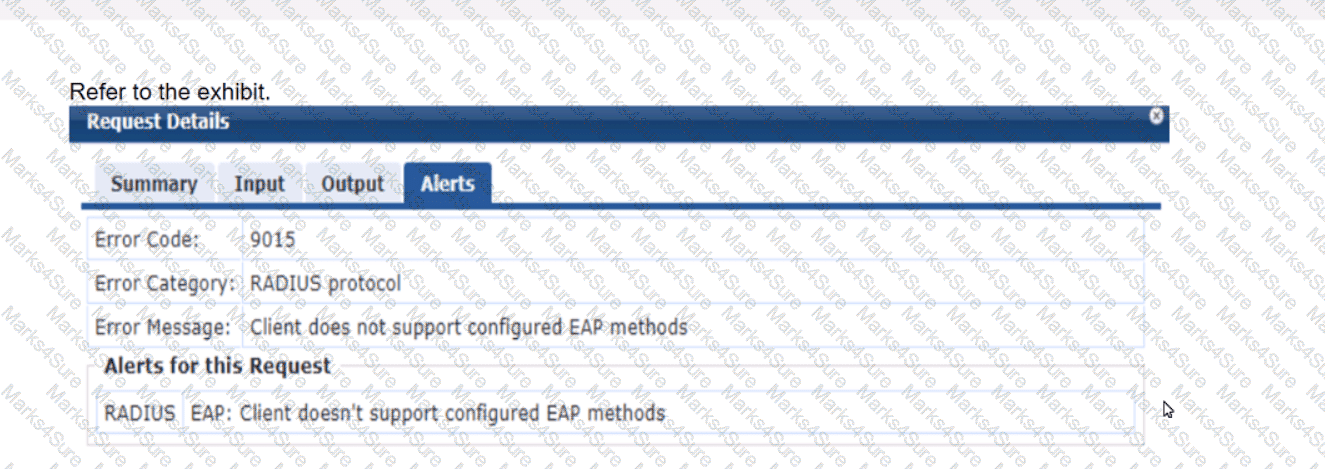
A company has an Aruba Instant AP cluster. A Windows 10 client is attempting to connect a WLAN that enforces WPA3-Enterprise with authentication to ClearPass Policy Manager (CPPM). CPPM is configured to require EAP-TLS. The client authentication fails. In the record for this client’s authentication attempt on CPPM, you see this alert.
What is one thing that you check to resolve this issue?
whether the client has a third-party 802.1 X supplicant, as Windows 10 does not support EAP-TLS
whether the client has a valid certificate installed on it to let it support EAP-TLS
whether EAP-TLS is enabled in the SSID Profile settings for the WLAN on the IAP cluster
whether EAP-TLS is enabled in the AAA Profile settings for the WLAN on the IAP cluster
In the context of WPA3-Enterprise with EAP-TLS authentication, the error message "Client doesn’t support configured EAP methods" suggests that the client is not able to complete the EAP-TLS authentication process. EAP-TLS requires that both the server (in this case, CPPM) and the client have a valid certificate for mutual authentication. Windows 10 does support EAP-TLS natively, so options A, C, and D can be ruled out.
The most likely reason for the authentication failure is that the client device does not have the correct client certificate installed, which is required to establish a TLS session with the server. Therefore, ensuring that the client has a valid certificate installed that matches the server's requirements is the correct step to resolve this issue.
What is a Key feature of me ArubaOS firewall?
The firewall is stateful which means that n can track client sessions and automatically allow return traffic for permitted sessions
The firewall Includes application layer gateways (ALGs). which it uses to filter Web traffic based on the reputation of the destination web site.
The firewall examines all traffic at Layer 2 through Layer 4 and uses source IP addresses as the primary way to determine how to control traffic.
The firewall is designed to fitter traffic primarily based on wireless 802.11 headers, making it ideal for mobility environments
The ArubaOS firewall is a stateful firewall, meaning that it can track the state of active sessions and can make decisions based on the context of the traffic. This stateful inspection capability allows it to automatically allow return traffic for sessions that it has permitted, thereby enabling seamless two-way communication for authorized users while maintaining the security posture of the network.
What is an example or phishing?
An attacker sends TCP messages to many different ports to discover which ports are open.
An attacker checks a user’s password by using trying millions of potential passwords.
An attacker lures clients to connect to a software-based AP that is using a legitimate SSID.
An attacker sends emails posing as a service team member to get users to disclose their passwords.
Phishing is a type of social engineering attack where an attacker impersonates a trusted entity to deceive people into providing sensitive information, such as passwords or credit card numbers. An example of phishing is when an attacker sends emails posing as a service team member or a legitimate organization with the intention of getting users to disclose their passwords or other confidential information. These emails often contain links to fake websites that look remarkably similar to legitimate ones, tricking users into entering their details.
What does the NIST model for digital forensics define?
how to define access control policies that will properly protect a company's most sensitive data and digital resources
how to properly collect, examine, and analyze logs and other data, in order to use it as evidence in a security investigation
which types of architecture and security policies are best equipped to help companies establish a Zero Trust Network (ZTN)
which data encryption and authentication algorithms are suitable for enterprise networks in a world that is moving toward quantum computing
The National Institute of Standards and Technology (NIST) provides guidelines on digital forensics, which include methodologies for properly collecting, examining, and analyzing digital evidence. This framework helps ensure that digital evidence is handled in a manner that preserves its integrity and maintains its admissibility in legal proceedings:
Digital Forensics Process: This process involves steps to ensure that data collected from digital sources can be used reliably in investigations and court cases, addressing chain-of-custody issues, proper evidence handling, and detailed documentation of forensic procedures.
A company is deploying AOS-CX switches to support 114 employees, which will tunnel client traffic to an HPE Aruba Networking Mobility Controller (MC) for the MC to apply firewall policies and deep packet inspection (DPI). This MC will be dedicated to receiving traffic from the AOS-CX switches.
What are the licensing requirements for the MC?
One PEF license per switch
One PEF license per switch, and one WCC license per switch
One AP license per switch
One AP license per switch, and one PEF license per switch
The scenario involves AOS-CX switches tunneling client traffic to an HPE Aruba Networking Mobility Controller (MC) in an AOS-8 architecture. The MC will apply firewall policies and perform deep packet inspection (DPI) on the tunneled traffic. The MC is dedicated to receiving traffic from the AOS-CX switches, and there are 114 employees (implying 114 potential clients). The question asks about the licensing requirements for the MC.
Tunneling from AOS-CX Switches to MC: In this setup, the AOS-CX switches act as Layer 2 devices, tunneling client traffic to the MC using a mechanism like GRE or VXLAN (though GRE is more common in AOS-8). The MC treats the tunneled traffic as if it were coming from wireless clients, applying firewall policies and DPI.
Licensing in AOS-8:
AP License (Access Point License): Required for each AP managed by the MC. Since the scenario involves AOS-CX switches tunneling traffic, not APs, AP licenses are not required.
PEF License (Policy Enforcement Firewall License): Required to enable the stateful firewall and DPI features on the MC. The PEF license is based on the number of devices (e.g., switches, APs) or users that the MC processes traffic for. In this case, the MC is processing traffic from AOS-CX switches, and the license is typically per switch (not per user or employee).
WCC License (Web Content Classification License): An optional license that enhances DPI by enabling URL-based filtering and web content classification. This is not mentioned as a requirement in the scenario.
Option A, "One PEF license per switch," is correct. Since the MC is dedicated to receiving traffic from the AOS-CX switches, and the MC will apply firewall policies and DPI, a PEF license is required. In AOS-8, when switches tunnel traffic to an MC, the PEF license is typically required per switch (not per user). With 114 employees, the number of switches is not specified, but the licensing model is per switch, so one PEF license per switch is needed.
Option B, "One PEF license per switch, and one WCC license per switch," is incorrect. While a PEF license is required, a WCC license is not mentioned as a requirement. WCC is for advanced web filtering, which is not specified in the scenario.
Option C, "One AP license per switch," is incorrect. AP licenses are for managing APs, not switches. Since the scenario involves switches tunneling traffic, not APs, AP licenses are not required.
Option D, "One AP license per switch, and one PEF license per switch," is incorrect for the same reason as Option C. AP licenses are not needed, but the PEF license per switch is correct.
The HPE Aruba Networking AOS-8 8.11 User Guide states:
"The Policy Enforcement Firewall (PEF) license is required on the Mobility Controller to enable stateful firewall policies and deep packet inspection (DPI). When AOS-CX switches tunnel client traffic to the MC for firewall processing, a PEF license is required for each switch. The license is based on the number of devices (e.g., switches) sending traffic to the MC, not the number of users. For example, if 10 switches tunnel traffic to the MC, 10 PEF licenses are required." (Page 375, Licensing Requirements Section)
Additionally, the HPE Aruba Networking Licensing Guide notes:
"PEF licenses on the Mobility Controller are required for firewall and DPI features. In deployments where switches tunnel traffic to the MC, the PEF license is typically per switch. AP licenses are not required unless the MC is managing APs. The Web Content Classification (WCC) license is optional and only needed for advanced URL filtering, which is not required for basic DPI." (Page 15, PEF Licensing Section)
Which is a correct description of a stage in the Lockheed Martin kill chain?
In the weaponization stage, which occurs after malware has been delivered to a system, the malware executes its function.
In the exploitation and installation phases, malware creates a backdoor into the infected system for the hacker.
In the reconnaissance stage, the hacker assesses the impact of the attack and how much information was exfiltrated.
In the delivery stage, malware collects valuable data and delivers or exfiltrates it to the hacker.
The Lockheed Martin Cyber Kill Chain is a framework that outlines the stages of a cyber attack, from initial reconnaissance to achieving the attacker’s objective. It is often referenced in HPE Aruba Networking security documentation to help organizations understand and mitigate threats. The stages are: Reconnaissance, Weaponization, Delivery, Exploitation, Installation, Command and Control (C2), and Actions on Objectives.
Option A, "In the weaponization stage, which occurs after malware has been delivered to a system, the malware executes its function," is incorrect. The weaponization stage occurs before delivery, not after. In this stage, the attacker creates a deliverable payload (e.g., combining malware with an exploit). The execution of the malware happens in the exploitation stage, not weaponization.
Option B, "In the exploitation and installation phases, malware creates a backdoor into the infected system for the hacker," is correct. The exploitation phase involves the attacker exploiting a vulnerability (e.g., a software flaw) to execute the malware on the target system. The installation phase follows, where the malware installs itself to establish persistence, often by creating a backdoor (e.g., a remote access tool) to allow the hacker to maintain access to the system. These two phases are often linked in the kill chain as the malware gains a foothold and ensures continued access.
Option C, "In the reconnaissance stage, the hacker assesses the impact of the attack and how much information was exfiltrated," is incorrect. The reconnaissance stage occurs at the beginning of the kill chain, where the attacker gathers information about the target (e.g., network topology, vulnerabilities). Assessing the impact and exfiltration occurs in the Actions on Objectives stage, the final stage of the kill chain.
Option D, "In the delivery stage, malware collects valuable data and delivers or exfiltrates it to the hacker," is incorrect. The delivery stage involves the attacker transmitting the weaponized payload to the target (e.g., via a phishing email). Data collection and exfiltration occur later, in the Actions on Objectives stage, not during delivery.
The HPE Aruba Networking Security Guide states:
"The Lockheed Martin Cyber Kill Chain outlines the stages of a cyber attack. In the exploitation phase, the attacker exploits a vulnerability to execute the malware on the target system. In the installation phase, the malware creates a backdoor or other persistence mechanism, such as a remote access tool, to allow the hacker to maintain access to the infected system for future actions." (Page 18, Cyber Kill Chain Overview Section)
Additionally, the HPE Aruba Networking AOS-8 8.11 User Guide notes:
"The exploitation and installation phases of the Lockheed Martin kill chain involve the malware gaining a foothold on the target system. During exploitation, the malware is executed by exploiting a vulnerability, and during installation, it creates a backdoor to ensure persistent access for the hacker, enabling further stages like command and control." (Page 420, Threat Mitigation Section)
Which is a use case for enabling Control Plane Policing on Aruba switches?
to prevent unauthorized network devices from sending routing updates
to prevent the switch from accepting routing updates from unauthorized users
to encrypt traffic between tunneled node switches and Mobility Controllers (MCs)
to mitigate Denial of Service (Dos) attacks on the switch
Control Plane Policing (CoPP) on Aruba switches is used to mitigate Denial of Service (DoS) attacks on the switch. CoPP allows network administrators to restrict the impact of control plane traffic on the switch's CPU, thereby protecting network stability and integrity. By setting rate limits and specifying allowed traffic types, administrators can prevent malicious or malformed packets from overwhelming the switch's control plane, which could otherwise lead to a DoS condition and potentially disrupt network operations. This use case of CoPP is detailed in Aruba's network management documentation, where best practices and configurations to protect against DoS attacks are discussed.
What is one benefit of a Trusted Platform Module (TPM) on an Aruba AP?
It enables secure boot, which detects if hackers corrupt the OS with malware.
It deploys the AP with enhanced security, which includes disabling the password recovery mechanism.
It allows the AP to run in secure mode, which automatically enables CPsec and disables the console port.
It enables the AP to encrypt and decrypt 802.11 traffic locally, rather than at the MC.
The TPM (Trusted Platform Module) is a hardware-based security feature that can provide various security functions, one of which includes secure boot. Secure boot is a process where the TPM ensures that the device boots using only software that is trusted by the manufacturer. If the OS has been tampered with or infected with malware, the secure boot process can detect this and prevent the system from loading the compromised OS.
Refer to the exhibits.
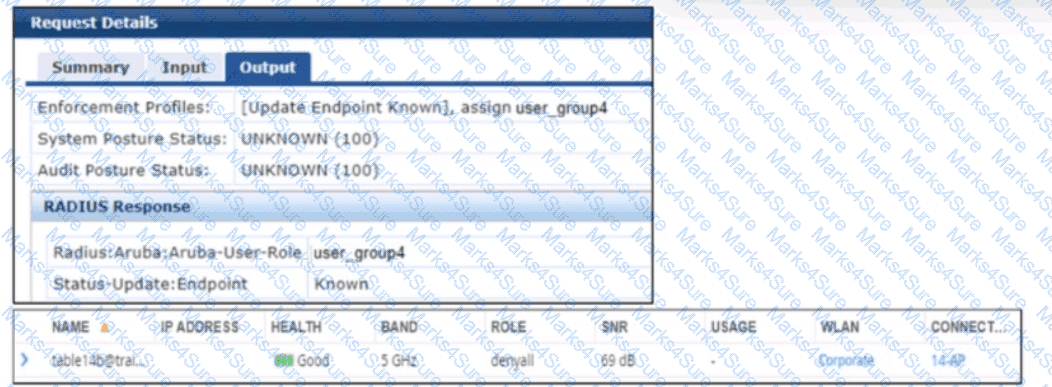
A company has added a new user group. Users in the group try to connect to the WLAN and receive errors that the connection has no Internet access. The users cannot reach any resources. The first exhibit shows the record for one of the users who cannot connect. The second exhibit shows the role to which the AOS device assigned the user’s client.
What is a likely problem?
The AOS device does not have the correct RADIUS dictionaries installed on it to understand the Aruba-User-Role VSA.
The AOS device has a server derivation rule configured on it that has overridden the role sent by CPPM.
The clients rejected the server authentication on their side because they do not have the root CA for CPPM’s RADIUS/EAP certificate.
The role name that CPPM is sending does not match the role name configured on the AOS device.
The scenario involves an AOS-8 Mobility Controller (MC) with a WLAN where a new user group has been added. Users in this group cannot connect to the WLAN, receiving errors indicating no Internet access and inability to reach resources. Exhibit 1 shows the ClearPass Policy Manager (CPPM) Access Tracker record for one user:
CPPM sends an Access-Accept with the VSA Radius:Aruba:Aruba-User-Role user_group4.
The endpoint is classified as "Known," but the user cannot access resources. Exhibit 2 (not provided but described) shows that the AOS device (MC) assigned the user’s client to the "denyall" role, which likely denies all access, explaining the lack of Internet and resource access.
Analysis:
CPPM sends the Aruba-User-Role VSA with the value "user_group4," indicating that the user should be assigned to the "user_group4" role on the MC.
However, the MC assigns the client to the "denyall" role, which typically denies all traffic, resulting in no Internet or resource access.
The issue lies in why the MC did not apply the "user_group4" role sent by CPPM.
Option A, "The AOS device does not have the correct RADIUS dictionaries installed on it to understand the Aruba-User-Role VSA," is incorrect. If the MC did not have the correct RADIUS dictionaries to understand the Aruba-User-Role VSA, it would not process the VSA at all, and the issue would likely affect all users, not just the new user group. Additionally, Aruba-User-Role is a standard VSA in AOS-8, and the dictionaries are built into the system.
Option B, "The AOS device has a server derivation rule configured on it that has overridden the role sent by CPPM," is incorrect. Server derivation rules on the MC can override roles sent by the RADIUS server (e.g., based on attributes like username or NAS-IP), but there is no indication in the scenario that such a rule is configured. If a derivation rule were overriding the role, it would likely affect more users, and the issue would not be specific to the new user group.
Option C, "The clients rejected the server authentication on their side because they do not have the root CA for CPPM’s RADIUS/EAP certificate," is incorrect. If the clients rejected the server authentication (e.g., due to a missing root CA for CPPM’s certificate), the authentication would fail entirely, and CPPM would not send an Access-Accept with the Aruba-User-Role VSA. The scenario confirms that authentication succeeded (Access-Accept was sent), so this is not the issue.
Option D, "The role name that CPPM is sending does not match the role name configured on the AOS device," is correct. CPPM sends the role "user_group4" in the Aruba-User-Role VSA, but the MC assigns the client to the "denyall" role. This suggests that the role "user_group4" does not exist on the MC, or there is a mismatch in the role name (e.g., due to case sensitivity, typos, or underscores vs. hyphens). In AOS-8, if the role specified in the Aruba-User-Role VSA does not exist on the MC, the MC falls back to a default role, which in this case appears to be "denyall," denying all access. The likely problem is that the role name "user_group4" sent by CPPM does not match the role name configured on the MC (e.g., it might be "user-group4" or a different name).
The HPE Aruba Networking AOS-8 8.11 User Guide states:
"When the Mobility Controller receives an Aruba-User-Role VSA in a RADIUS Access-Accept message, it attempts to assign the specified role to the client. If the role name sent by the RADIUS server (e.g., ‘user_group4’) does not match a role configured on the controller, the controller will fall back to a default role, such as ‘denyall,’ which may deny all access. To resolve this, ensure that the role name sent by the RADIUS server matches the role name configured on the controller, accounting for case sensitivity and naming conventions (e.g., underscores vs. hyphens)." (Page 306, Role Assignment Troubleshooting Section)
Additionally, the HPE Aruba Networking ClearPass Policy Manager 6.11 User Guide notes:
"A common issue when assigning roles via the Aruba-User-Role VSA is a mismatch between the role name sent by ClearPass and the role name configured on the Aruba device. If the role name does not match (e.g., ‘user_group4’ vs. ‘user-group4’), the device will not apply the intended role, and the client may be assigned a default role like ‘denyall,’ resulting in access issues. Verify that the role names match exactly in both ClearPass and the device configuration." (Page 290, RADIUS Role Assignment Issues Section)
What is one thing can you determine from the exhibits?
CPPM originally assigned the client to a role for non-profiled devices. It sent a CoA to the authenticator after it categorized the device.
CPPM sent a CoA message to the client to prompt the client to submit information that CPPM can use to profile it.
CPPM was never able to determine a device category for this device, so you need to check settings in the network infrastructure to ensure they support CPPM's endpoint classification.
CPPM first assigned the client to a role based on the user's identity. Then, it discovered that the client had an invalid category, so it sent a CoA to blacklist the client.
Based on the exhibits which seem to show RADIUS authentication and CoA logs, one can determine that CPPM (ClearPass Policy Manager) initially assigned the client to a role meant for non-profiled devices and then sent a CoA to the network access device (authenticator) once the device was categorized. This is a common workflow in network access control, where a device is first given limited access until it can be properly identified, after which appropriate access policies are applied.
What is one way that WPA3-Enterprise enhances security when compared to WPA2-Enterprise?
WPA3-Enterprise implements the more secure simultaneous authentication of equals (SAE), while WPA2-Enterprise uses 802.1X.
WPA3-Enterprise provides built-in mechanisms that can deploy user certificates to authorized end-user devices.
WPA3-Enterprise uses Diffie-Hellman in order to authenticate clients, while WPA2-Enterprise uses 802.1X authentication.
WPA3-Enterprise can operate in CNSA mode, which mandates that the 802.11 association uses secure algorithms.
WPA3-Enterprise enhances network security over WPA2-Enterprise through several improvements, one of which is the ability to operate in CNSA (Commercial National Security Algorithm) mode. This mode mandates the use of secure cryptographic algorithms during the 802.11 association process, ensuring that all communications are highly secure. The CNSA suite provides stronger encryption standards designed to protect sensitive government, military, and industrial communications. Unlike WPA2, WPA3's CNSA mode uses stronger cryptographic primitives, such as AES-256 in Galois/Counter Mode (GCM) for encryption and SHA-384 for hashing, which are not standard in WPA2-Enterprise.
Which attack is an example or social engineering?
An email Is used to impersonate a Dank and trick users into entering their bank login information on a fake website page.
A hacker eavesdrops on insecure communications, such as Remote Desktop Program (RDP). and discovers login credentials.
A user visits a website and downloads a file that contains a worm, which sell-replicates throughout the network.
An attack exploits an operating system vulnerability and locks out users until they pay the ransom.
An example of a social engineering attack is described in option A, where an email is used to impersonate a bank and deceive users into entering their bank login information on a counterfeit website. Social engineering attacks exploit human psychology rather than technical hacking techniques to gain access to systems, data, or personal information. These attacks often involve tricking people into breaking normal security procedures. The other options describe different types of technical attacks that do not primarily rely on manipulating individuals through deceptive personal interactions.
You have a network with ArubaOS-Switches for which Aruba ClearPass Policy Manager (CPPM) is acting as a TACACS+ server to authenticate managers. CPPM assigns the admins a TACACS+ privilege level, either manager or operator. You are now adding ArubaOS-CX switches to the network. ClearPass admins want to use the same CPPM service and policies to authenticate managers on the new switches.
What should you explain?
This approach cannot work because the ArubaOS-CX switches do not accept standard TACACS+ privilege levels.
This approach cannot work because the ArubaOS-CX switches do not support TACACS+.
This approach will work, but will need to be adjusted later if you want to assign managers to the default auditors group.
This approach will work to assign admins to the default "administrators" group, but not to the default "operators" group.
With ArubaOS-CX switches, the use of ClearPass Policy Manager (CPPM) as a TACACS+ server for authentication is supported. The privilege levels assigned by CPPM will translate onto the switches, where the "manager" privilege level typically maps to administrative capabilities and the "operator" privilege level maps to more limited capabilities. ArubaOS-CX does support standard TACACS+ privilege levels, so administrators can be assigned appropriately. If the ClearPass policies are correctly configured, they will work for both ArubaOS-Switches and ArubaOS-CX switches. The distinction between the "administrators" and "operators" groups is inherent in the ArubaOS-CX role-based access control, and these default groups need to be appropriately mapped to the TACACS+ privilege levels assigned by CPPM.
Which is an accurate description of a type of malware?
Worms are usually delivered in spear-phishing attacks and require users to open and run a file.
Rootkits can help hackers gain elevated access to a system and often actively conceal themselves from detection.
A Trojan is any type of malware that replicates itself and spreads to other systems automatically.
Malvertising can only infect a system if the user encounters the malware on an untrustworthy site.
Malware (malicious software) is a broad category of software designed to harm or exploit systems. HPE Aruba Networking documentation often discusses malware in the context of network security threats and mitigation strategies, such as those detected by the Wireless Intrusion Prevention (WIP) system.
Option A, "Worms are usually delivered in spear-phishing attacks and require users to open and run a file," is incorrect. Worms are a type of malware that replicate and spread automatically across networks without user interaction (e.g., by exploiting vulnerabilities). They are not typically delivered via spear-phishing, which is more associated with Trojans or ransomware. Worms do not require users to open and run a file; that behavior is characteristic of Trojans.
Option B, "Rootkits can help hackers gain elevated access to a system and often actively conceal themselves from detection," is correct. A rootkit is a type of malware that provides hackers with privileged (elevated) access to a system, often by modifying the operating system or kernel. Rootkits are designed to hide their presence (e.g., by concealing processes, files, or network connections) to evade detection by antivirus software or system administrators, making them a stealthy and dangerous type of malware.
Option C, "A Trojan is any type of malware that replicates itself and spreads to other systems automatically," is incorrect. A Trojan is a type of malware that disguises itself as legitimate software to trick users into installing it. Unlike worms, Trojans do not replicate or spread automatically; they require user interaction (e.g., downloading and running a file) to infect a system.
Option D, "Malvertising can only infect a system if the user encounters the malware on an untrustworthy site," is incorrect. Malvertising (malicious advertising) involves embedding malware in online ads, which can appear on both trustworthy and untrustworthy sites. For example, a legitimate website might unknowingly serve a malicious ad that exploits a browser vulnerability to infect the user’s system, even without the user clicking the ad.
The HPE Aruba Networking Security Guide states:
"Rootkits are a type of malware that can help hackers gain elevated access to a system by modifying the operating system or kernel. They often actively conceal themselves from detection by hiding processes, files, or network connections, making them difficult to detect and remove. Rootkits are commonly used to maintain persistent access to a compromised system." (Page 22, Malware Types Section)
Additionally, the HPE Aruba Networking AOS-8 8.11 User Guide notes:
"The Wireless Intrusion Prevention (WIP) system can detect various types of malware. Rootkits, for example, are designed to provide hackers with elevated access and often conceal themselves to evade detection, allowing the hacker to maintain control over the infected system for extended periods." (Page 421, Malware Threats Section)
Your company policies require you to encrypt logs between network infrastructure devices and Syslog servers. What should you do to meet these requirements on an ArubaOS-CX switch?
Specify the Syslog server with the TLS option and make sure the switch has a valid certificate.
Specify the Syslog server with the UDP option and then add an CPsec tunnel that selects Syslog.
Specify a priv key with the Syslog settings that matches a priv key on the Syslog server.
Set up RadSec and then enable Syslog as a protocol carried by the RadSec tunnel.
To ensure secure transmission of log data over the network, particularly when dealing with sensitive or critical information, using TLS (Transport Layer Security) for encrypted communication between network devices and syslog servers is necessary:
Secure Logging Setup: When configuring an ArubaOS-CX switch to send logs securely to a Syslog server, specifying the server with the TLS option ensures that all transmitted log data is encrypted. Additionally, the switch must have a valid certificate to establish a trusted connection, preventing potential eavesdropping or tampering with the logs in transit.
Other Options:
Option B, Option C, and Option D are less accurate or applicable for directly encrypting log data between the device and Syslog server as specified in the company policies.
Device A is contacting https://arubapedia.arubanetworks.com. The web server sends a certificate chain. What does the browser do as part of validating the web server certificate?
It makes sure that the key in the certificate matches the key that DeviceA uses for HTTPS.
It makes sure the certificate has a DNS SAN that matches arubapedia.arubanetworks.com
It makes sure that the public key in the certificate matches DeviceA's private HTTPS key.
It makes sure that the public key in the certificate matches a private key stored on DeviceA.
When a device like Device A contacts a secure website and receives a certificate chain from the server, the browser's primary task is to validate the web server's certificate to ensure it is trustworthy. Part of this validation includes checking that the certificate contains a DNS Subject Alternative Name (SAN) that matches the domain name of the website being accessed—in this case, arubapedia.arubanetworks.com. This ensures that the certificate was indeed issued to the entity operating the domain and helps prevent man-in-the-middle attacks where an invalid certificate could be presented by an attacker. The DNS SAN check is critical because it directly ties the digital certificate to the domain it secures, confirming the authenticity of the website to the user's browser.
What is a guideline for managing local certificates on an ArubaOS-Switch?
Before installing the local certificate, create a trust anchor (TA) profile with the root CA certificate for the certificate that you will install
Install an Online Certificate Status Protocol (OCSP) certificate to simplify the process of enrolling and re-enrolling for certificate
Generate the certificate signing request (CSR) with a program offline, then, install both the certificate and the private key on the switch in a single file.
Create a self-signed certificate online on the switch because ArubaOS-Switches do not support CA-signed certificates.
When managing local certificates on an ArubaOS-Switch, a recommended guideline is to create a trust anchor (TA) profile with the root CA certificate before installing the local certificate. This step ensures that the switch can verify the authenticity of the certificate chain during SSL/TLS communications. The trust anchor profile establishes a basis of trust by containing the root CA certificate, which helps validate the authenticity of any subordinate certificates, including the local certificate installed on the switch. This process is essential for enhancing security on the network, as it ensures that encrypted communications involving the switch are based on a verified certificate hierarchy.
What are some functions of an AruDaOS user role?
The role determines which authentication methods the user must pass to gain network access
The role determines which firewall policies and bandwidth contract apply to the clients traffic
The role determines which wireless networks (SSiDs) a user is permitted to access
The role determines which control plane ACL rules apply to the client's traffic
An ArubaOS user role determines the firewall policies and bandwidth contracts that apply to the client’s traffic. When a user is authenticated, they are assigned a role, and this role has associated policies that govern network access rights, Quality of Service (QoS), Layer 2 forwarding, Layer 3 routing behaviors, and bandwidth contracts for users or devices.
An MC has a WLAN that enforces WPA3-Enterprise with authentication to HPE Aruba Networking ClearPass Policy Manager (CPPM). The WLAN's default role is set to guest. A Mobility Controller (MC) has these roles configured on it:
authenticated
denyall
guest
general-access
guest-logon
logon
stateful-dot1x
switch-logon
voiceA client authenticates. CPPM returns an Access-Accept with an Aruba-User-Role VSA set to general_access. What role does the client receive?
guest
logon
general-access
authenticated
In an AOS-8 Mobility Controller (MC) environment, a WLAN is configured with WPA3-Enterprise security, using HPE Aruba Networking ClearPass Policy Manager (CPPM) for authentication. The WLAN’s default role is set to "guest," which would be applied if no specific role is assigned after authentication. The MC has several roles configured, including "general-access" (note the underscore in the question: "general_access").
The client successfully authenticates, and CPPM sends an Access-Accept message with an Aruba-User-Role Vendor-Specific Attribute (VSA) set to "general_access." In AOS-8, the Aruba-User-Role VSA is used to assign a specific role to the client, overriding the default role configured on the WLAN. The role specified in the VSA must match a role that exists on the MC. Since "general-access" (or "general_access" as written in the question) is listed among the roles configured on the MC, the MC will apply this role to the client.
The underscore in "general_access" in the VSA versus the hyphen in "general-access" in the MC’s role list is likely a typographical inconsistency in the question. In practice, AOS-8 role names are case-insensitive and typically use hyphens, not underscores, but for the purpose of this question, we assume "general_access" matches "general-access" as the intended role.
Option A, "guest," is incorrect because the guest role is the default 802.1X role for the WLAN, but it is overridden by the Aruba-User-Role VSA specifying "general_access."
Option B, "logon," is incorrect because the logon role is typically applied during the authentication process (e.g., to allow access to DNS or RADIUS servers), not after successful authentication when a specific role is assigned.
Option C, "general-access," is correct because the MC applies the role specified in the Aruba-User-Role VSA ("general_access"), which matches the "general-access" role configured on the MC.
Option D, "authenticated," is incorrect because the "authenticated" role is not specified in the VSA, and there is no indication that it is the default role for successful authentication in this scenario.
The HPE Aruba Networking AOS-8 8.11 User Guide states:
"When a client authenticates successfully via 802.1X, the Mobility Controller checks for an Aruba-User-Role VSA in the RADIUS Access-Accept message. If the VSA is present and the specified role exists on the controller, the controller assigns that role to the client, overriding the default 802.1X role configured for the WLAN. For example, if the VSA specifies ‘general-access’ and this role is configured on the controller, the client will be assigned the ‘general-access’ role." (Page 305, Role Assignment Section)
Additionally, the HPE Aruba Networking ClearPass Policy Manager 6.11 User Guide notes:
"The Aruba-User-Role VSA allows ClearPass to assign a specific role to a client on an Aruba Mobility Controller. The role name sent in the VSA must match a role configured on the controller, and the controller will apply this role to the client session, ignoring the default role for the WLAN." (Page 289, RADIUS Enforcement Section)
You have an Aruba Mobility Controller (MC) that is locked in a closet. What is another step that Aruba recommends to protect the MC from unauthorized access?
Use local authentication rather than external authentication to authenticate admins.
Change the password recovery password.
Set the local admin password to a long random value that is unknown or locked up securely.
Disable local authentication of administrators entirely.
Protecting an Aruba Mobility Controller from unauthorized access involves several layers of security. One recommendation is to change the password recovery password, which is a special type of password used to recover access to the device in the event the admin password is lost. Changing this to something complex and unique adds an additional layer of security in the event the physical security of the device is compromised.
An AOS-CX switch currently has no device fingerprinting settings configured on it. You want the switch to start collecting DHCP and LLDP information. You enter these commands:
Switch(config)# client device-fingerprint profile myprofile
Switch(myprofile)# dhcp
Switch(myprofile)# lldp
What else must you do to allow the switch to collect information from clients?
Configure the switch as a DHCP relay
Add at least one LLDP option to the policy
Apply the policy to edge ports
Add at least one DHCP option to the policy
Device fingerprinting on an AOS-CX switch allows the switch to collect information about connected clients to aid in profiling and policy enforcement, often in conjunction with a solution like ClearPass Policy Manager (CPPM). The commands provided create a device fingerprinting profile named "myprofile" and enable the collection of DHCP and LLDP information:
client device-fingerprint profile myprofile: Creates a fingerprinting profile.
dhcp: Enables the collection of DHCP information (e.g., DHCP options like Option 55 for fingerprinting).
lldp: Enables the collection of LLDP (Link Layer Discovery Protocol) information (e.g., system name, description).
However, creating the profile and enabling DHCP and LLDP collection is not enough for the switch to start collecting this information from clients. The profile must be applied to the interfaces (ports) where clients are connected.
Option C, "Apply the policy to edge ports," is correct. In AOS-CX, the device fingerprinting profile must be applied to the edge ports (ports where clients connect) to enable the switch to collect DHCP and LLDP information from those clients. This is done using the command client device-fingerprint profile
text
CollapseWrapCopy
Switch(config)# interface 1/1/1
Switch(config-if)# client device-fingerprint profile myprofile
This ensures that the switch collects DHCP and LLDP data from clients connected to the specified ports.
Option A, "Configure the switch as a DHCP relay," is incorrect. While a DHCP relay (using the ip helper-address command) is needed if the DHCP server is on a different subnet, it is not a requirement for the switch to collect DHCP information for fingerprinting. The switch can snoop DHCP traffic on the local VLAN without being a relay, as long as the profile is applied to the ports.
Option B, "Add at least one LLDP option to the policy," is incorrect. The lldp command in the fingerprinting profile already enables the collection of LLDP information. There is no need to specify individual LLDP options (e.g., system name, description) in the profile; the switch collects all available LLDP data by default.
Option D, "Add at least one DHCP option to the policy," is incorrect. The dhcp command in the fingerprinting profile already enables the collection of DHCP information, including options like Option 55 (Parameter Request List), which is commonly used for fingerprinting. There is no need to specify individual DHCP options in the profile.
The HPE Aruba Networking AOS-CX 10.12 Security Guide states:
"To enable device fingerprinting on an AOS-CX switch, create a device fingerprinting profile using the client device-fingerprint profile
Additionally, the HPE Aruba Networking AOS-CX 10.12 System Management Guide notes:
"The device fingerprinting profile must be applied to the ports where clients are connected to collect DHCP and LLDP information. The dhcp and lldp commands in the profile enable the collection of all relevant data for those protocols, such as DHCP Option 55 for fingerprinting, without requiring additional options to be specified." (Page 95, Device Fingerprinting Setup Section)
What role does the Aruba ClearPass Device Insight Analyzer play in the Device Insight architecture?
It resides in the cloud and manages licensing and configuration for Collectors
It resides on-prem and provides the span port to which traffic is mirrored for deep analytics.
It resides on-prem and is responsible for running active SNMP and Nmap scans
It resides In the cloud and applies machine learning and supervised crowdsourcing to metadata sent by Collectors
The Aruba ClearPass Device Insight Analyzer plays a crucial role within the Device Insight architecture by residing in the cloud and applying machine learning and supervised crowdsourcing to the metadata sent by Collectors. This component of the architecture is responsible for analyzing vast amounts of data collected from the network to identify and classify devices accurately. By utilizing machine learning algorithms and crowdsourced input, the Device Insight Analyzer enhances the accuracy of device detection and classification, thereby improving the overall security and management of the network.
Refer to the exhibit.
Device A is establishing an HTTPS session with the Arubapedia web sue using Chrome. The Arubapedia web server sends the certificate shown in the exhibit
What does the browser do as part of vacating the web server certificate?
It uses the public key in the DigCen SHA2 Secure Server CA certificate to check the certificate's signature.
It uses the public key in the DigCert root CA certificate to check the certificate signature
It uses the private key in the DigiCert SHA2 Secure Server CA to check the certificate's signature.
It uses the private key in the Arubapedia web site's certificate to check that certificate's signature
When a browser, like Chrome, is validating a web server's certificate, it uses the public key in the certificate's signing authority to verify the certificate's digital signature. In the case of the exhibit, the browser would use the public key in the DigiCert SHA2 Secure Server CA certificate to check the signature of the Arubapedia web server's certificate. This process ensures that the certificate was indeed issued by the claimed Certificate Authority (CA) and has not been tampered with.
Refer to the exhibit.
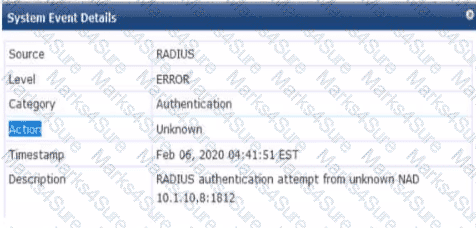
You are deploying a new ArubaOS Mobility Controller (MC), which is enforcing authentication to Aruba ClearPass Policy Manager (CPPM). The authentication is not working correctly, and you find the error shown In the exhibit in the CPPM Event Viewer.
What should you check?
that the MC has been added as a domain machine on the Active Directory domain with which CPPM is synchronized
that the snared secret configured for the CPPM authentication server matches the one defined for the device on CPPM
that the IP address that the MC is using to reach CPPM matches the one defined for the device on CPPM
that the MC has valid admin credentials configured on it for logging into the CPPM
Given the error message from the ClearPass Policy Manager (CPPM) Event Viewer, indicating a RADIUS authentication attempt from an unknown Network Access Device (NAD), you should check that the IP address the Mobility Controller (MC) is using to communicate with CPPM matches the IP address defined for the MC in the CPPM's device inventory. If there is a mismatch in IP addresses, CPPM will not recognize the MC as a known device and will not process the authentication request, leading to the error observed.
Which correctly describes a way to deploy certificates to end-user devices?
ClearPass Onboard can help to deploy certificates to end-user devices, whether or not they are members of a Windows domain
ClearPass Device Insight can automatically discover end-user devices and deploy the proper certificates to them
ClearPass OnGuard can help to deploy certificates to end-user devices, whether or not they are members of a Windows domain
in a Windows domain, domain group policy objects (GPOs) can automatically install computer, but not user certificates
ClearPass Onboard is part of the Aruba ClearPass suite and it provides a mechanism to deploy certificates to end-user devices, regardless of whether or not they are members of a Windows domain. ClearPass Onboard facilitates the configuration and provisioning of network settings and security, including the delivery and installation of certificates to ensure secure network access. This capability enables a bring-your-own-device (BYOD) environment where devices can be securely managed and provided with the necessary certificates for network authentication.

TESTED 24 Feb 2026

