A third party who provides payroll services to the organization was asked to create audit or “read-only 1 functionalities in their systems. Which of the following statements is true regarding this request?
Which of these instances accurately describes the responsibilities for big data governance?
The chief audit executive (CAE) has embraced a total quality management approach to improving the internal audit activity's (lAArs) processes. He would like to reduce the time to complete audits and improve client ratings of the IAA. Which of the following staffing approaches is the CAE most likely lo select?
Which of the following statements describes the typical benefit of using a flat organizational structure for the internal audit activity, compared to a hierarchical structure?
An IT auditor is evaluating IT controls of a newly purchased information system. The auditor discovers that logging is not configured al database and application levels. Operational management explains that they do not have enough personnel to manage the logs and they see no benefit in keeping logs. Which of the fallowing responses best explains risks associated with insufficient or absent logging practices?
An internal auditor considers the financial statement of an organization as part of a financial assurance engagement. The auditor expresses the organization's electricity and depreciation expenses as a percentage of revenue to be 10% and 7% respectively. Which of the following techniques was used by the internal auditor In this calculation?
According to I1A guidance on IT. which of the following activities regarding information security Is most likely to be the responsibility of line management as opposed to executive management, internal auditors, or the board?
An organization has an immediate need for servers, but no time to complete capital acquisitions. Which of the following cloud services would assist with this situation?
An organization prepares a statement of privacy to protect customers' personal information. Which of the following might violate the privacy principles?
Which of the following should internal auditors be attentive of when reviewing personal data consent and opt-in/opt-out management process?
At an organization that uses a periodic inventory system, the accountant accidentally understated the organization s beginning inventory. How would the accountant's accident impact the income statement?
Focus An organization has decided to have all employees work from home. Which of the following network types would securely enable this approach?
Which of the following performance measures includes both profits and investment base?
According to 11A guidance on IT, which of the following spreadsheets is most likely to be considered a high-risk user-developed application?
During the process of setting the annual audit plan, the chief audit executive receives a request from senior management to conduct an assurance engagement on the cybersecurity controls of the organization. Which of the following is a reason cybersecurity should be included in the annual internal audit plan?
A restaurant decided to expand its business to include delivery services, rather than relying on third-party food delivery services. Which of the following best describes the restaurants strategy?
To achieve conformance with the Global Internal Audit Standards, the chief audit executive must include which of the following activities in the quality assurance and improvement program (QAIP)?
Which of the following inventory costing methods requires the organization to account for the actual cost paid for the unit being sold?
An internal audit team performed an assurance engagement of the organization's IT security. The audit team found significant flaws in the design and implementation of the internal control framework. IT department managers often disagreed with the audit team on the significance of the findings, claiming that the controls in place partly mitigated the risks. Which of the following should be included when communicating the engagement results to senior management?
Which of the following would best contribute to the success of a guest auditor program that allows people from other areas of the organization to serve as subject matter experts?
The internal audit function of a manufacturing organization is conducting an advisory engagement. The engagement team identifies a gap in procedures: there is no documentation for the activities that take place when new site construction projects are completed. In practice, these activities include the transfer of assets from the development department to the production department. What is the most appropriate action for the engagement team?
Management has decided to change the organizational structure from one that was previously decentralized to one that is now highly centralized. As such: which of the
following would be a characteristic of the now highly centralized organization?
An internal audit uncovered high-risk issues that needed to be addressed by the organization. During the exit conference, the audit team discussed the high-risk issues with the manager responsible for addressing them. How should the chief audit executive respond if the manager agrees to correct the issues identified during the audit?
Which of the following is a sound network configuration practice to enhance information security?
Which of the following describes a third-party network that connects an organization specifically with its trading partners?
Which of the following parties is most likely to be responsible for maintaining the infrastructure required to prevent the failure of a real-time backup of a database?
An internal auditor uses a risk and control questionnaire as part of the preliminary survey for an audit of the organization's anti-bribery and corruption program. What is the primary purpose of using this approach?
Which of the following best describes the chief audit executive's responsibility for assessing the organization's residual risk?
Which of the following best describes the purpose of fixed manufacturing costs?
An IT auditor tested management of access rights and uncovered 48 instances where employees moved to a new position within the organization, but their former access rights were not revoked. System administrators explained that they did not receive information regarding employees’ new positions. Which of the following would be the best recommendation to address the root causes of the audit observation?
The internal auditor concluded there was a high likelihood that a significant wind farm development, worth $200 million, would be delayed from its approved schedule. As a result, electricity production would not start on time, leading to considerable financial penalties. Which of the following should be added to the observation to support its clarity and completeness?
Employees of an organization noticed that an exterior surface of the office building was deteriorating. Upon investigation, it was found that the deterioration was caused by harsh cleaning chemicals used to remove excessive bird droppings, and that the birds were drawn to the building to feed from a spider infestation. Which of the following best represents a root cause-based recommendation for this situation?
Which of the following disaster recovery plans includes recovery resources available at the site, but they may need to be configured to support the production system?
After identifying and reporting a control deficiency, which of the following actions should an internal auditor perform next?
Which of the following is a necessary action for an internal audit function if senior management chooses not to take action to remediate the finding and accepts the risk?
During an internal audit engagement, numerous deficiencies in the organization's management of customer data were discovered, entailing the risk of breaching personal data protection legislation. An improvement plan was approved by senior management. Which of the following conditions observed during the periodic follow-up process best justifies the chief audit executive's decision to escalate the issue to the board?
Which of the following actions would senior management need to consider as part of new IT guidelines regarding the organization's cybersecurity policies?
Which of the following IT disaster recovery plans includes a remote site dessgnated for recovery with available space for basic services, such as internet and
telecommunications, but does not have servers or infrastructure equipment?
Which of the following is a key performance indicator of the efficiency of the internal audit function?
Which of the following actions is likely to reduce the risk of violating transfer pricing regulations?
Which of the following statements is true regarding user-developed applications (UDAs)?
An internal auditor reviews a data population and calculates the mean, median, and range. What is the most likely purpose of performing this analytic technique?
When should the results of internal quality assessments be communicated to senior management and the board?
Which of the following data privacy concerns can be attributed specifically to blockchain technologies?
Which of the following would be most likely found in an internal audit procedures manual?
According to 11A guidance on IT, which of the following are indicators of poor change management?
1. Inadequate control design.
2. Unplanned downtime.
3. Excessive troubleshooting .
4. Unavailability of critical services.
According to IIA guidance, which of the following statements is true regarding communication of engagement results?
An internal audit engagement team found that the risk register of the project under review did not include significant risks identified by the internal audit function. The project manager explained that risk register preparations are facilitated by risk managers and that each project’s risk review follows the same set of questions. Which of the following recommendations will likely add the greatest value to the project management process of the organization?
An internal auditor is assigned to perform data analytics. Which of the following is the next step the auditor should undertake after she has ascertained the value expected from the review?
Which of the following is an example of a smart device security control intended to prevent unauthorized users from gaining access to a device’s data or applications?
Which of the following is a security feature that involves the use of hardware and software to filter or prevent specific information from moving between the inside network and the outside network?
Which of the following security controls would be appropriate to protect the exchange of information?
During a payroll audit, the internal auditor is assessing the security of the local area network of the payroll department computers. Which of the following IT controls should the auditor test?
Which of the following is the best example of a compliance risk that is likely to arise when adopting a bring-your-own-device (BYOD) policy?
An organization has 1,000 units of a defective item in stock. Per unit, market price is $10; production cost is $4; and the defect selling price is $5. What is the carrying amount (inventory value) of defects at year-end?
Which of the following statements is true regarding the management-by-objectives (MBO) approach?
Which of the following network types should an organization choose if it wants to allow access only to its own personnel?
Which of the following best explains why an organization would enter into a capital lease contract?
A large retail customer made an offer to buy 10,000 units at a special price of $7 per unit. The manufacturer usually sells each unit for $10. Variable manufacturing costs are $5 per unit and fixed manufacturing costs are $3 per unit. For the manufacturer to accept the offer, which of the following assumptions needs to be true?
Which of the following authentication controls combines what a user knows with the unique characteristics of the user, respectively?
According to IIA guidance, which of the following are typical physical and environmental IT controls?
Which of the following bring-your-own-device (BYOD) practices is likely to increase the risk of infringement on local regulations, such as copyright or privacy laws?
Given the information below, which organization is in the weakest position to pay short-term debts?
Organization A: Current assets constitute $1,200,000; Current liabilities are $400,000
Organization B: Current assets constitute $1,000,000; Current liabilities are $1,000,000
Organization C: Current assets constitute $900,000; Current liabilities are $300,000
Organization D: Current assets constitute $1,000,000; Current liabilities are $250,000
An internal auditor was asked to review an equal equity partnership. In one sampled transaction, Partner A transferred equipment into the partnership with a self-declared value of $10,000, and Partner B contributed equipment with a self-declared value of $15,000. The capital accounts of each partner were subsequently credited with $12,500. Which of the following statements is true regarding this transaction?
An organization with global headquarters in the United States has subsidiaries in eight other nations. If the organization operates with an ethnocentric attitude, which of the following statements is true?
Which of the following statements is true regarding the capital budgeting procedure known as the discounted payback period?
The IT department maintains logs of user identification and authentication for all requests for access to the network. What is the primary purpose of these logs?
Based on test results, an IT auditor concluded that the organization would suffer unacceptable loss of data if there was a disaster at its data center. Which of the following test results would likely lead the auditor to this conclusion?
Which of the following types of data analytics would be used by a hospital to determine which patients are likely to require readmittance for additional treatment?
According to IIA guidance, which of the following would be the best first step to manage risk when a third party is overseeing the organization’s network and data?
Which of the following risks would involve individuals attacking an oil company’s IT system as a sign of solidarity against drilling in a local area?
Which of the following responsibilities would ordinarily fall under the help desk function of an organization?
Which of the following statements is true regarding cost-volume-profit analysis?
Which of the following is a primary driver behind the creation and prioritization of new strategic initiatives established by an organization?
An internal auditor observed that the organization's disaster recovery solution will make use of a cold site in a town several miles away. Which of the following is likely to be a characteristic of this disaster recovery solution?
Which of the following purchasing scenarios would gain the greatest benefit from implementing electronic data interchange (EDI)?
The head of the research and development department at a manufacturing organization believes that his team lacks expertise in some areas and decides to hire more experienced researchers to assist in the development of a new product. Which of the following variances are likely to occur as the result of this decision?
Favorable labor efficiency variance
Adverse labor rate variance
Adverse labor efficiency variance
Favorable labor rate variance
Which of the following statements is most accurate concerning the management and audit of a web server?
A newly appointed chief audit executive (CAE) reviews current reporting practices. The CAE notices that exit meetings tend to be unproductive. When internal auditors present summaries of observations, engagement clients consistently complain that they do not understand where the observations come from. Which of the following could improve this situation?
When using data analytics during a review of the procurement process, what is the first step in the analysis process?
Which of the following describes the most appropriate set of tests for auditing a workstation’s logical access controls?
According to IIA guidance on IT, which of the following best describes a situation where data backup plans exist to ensure that critical data can be restored at some point in the future, but recovery and restore processes have not been defined?
An organization has instituted a bring-your-own-device (BYOD) work environment. Which of the following policies best addresses the increased risk to the organization's network incurred by this environment?
Which of the following risks would Involve individuals attacking an oil company's IT system as a sign of solidarity against drilling in a local area?
Which of the following statements is true regarding cost-volume-profit analysis?
According to Maslow's hierarchy of needs theory, which of the following best describes a strategy where a manager offers an assignment to a subordinate specifically to support his professional growth and future advancement?
According to IIA guidance, which of the following statements is true regarding analytical procedures?
Which of the following bring-your-own-device (BYOD) practices is likely to increase the risk of Infringement on local regulations, such as copyright or privacy laws?
An investor has acquired an organization that has a dominant position in a mature. slew-growth Industry and consistently creates positive financial income.
Which of the following terms would the investor most likely label this investment in her portfolio?
An organization has 10,000 units of a defect item in stock, per unit, market price is $10$; production cost is $4; and defect selling price is $5. What is the carrying amount (inventory value) of defects at your end?
A retail organization mistakenly did have include $10,000 of Inventory in the physical count at the end of the year. What was the impact to the organization's financial statements?
Which of the following statements. Is most accurate concerning the management and audit of a web server?
Which of the following IT-related activities is most commonly performed by the second line of defense?
According to lIA guidance on IT, which of the following plans would pair the identification of critical business processes with recovery time objectives?
Which of the following is a security feature that Involves the use of hardware and software to filter or prevent specific Information from moving between the inside network and the outs de network?
Which of the following would most likely be found in an organization that uses a decentralized organizational structure?
An internal auditor found the following information while reviewing the monthly financial siatements for a wholesaler of safety
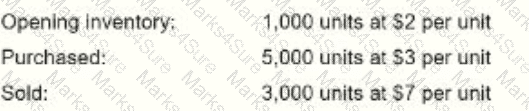
The cost of goods sold was reported at $8,500. Which of the following inventory methods was used to derive this value?
An organization uses the management-by-objectives method whereby employee performance is based on defined goals. Which of the following statements is true regarding this approach?
A one-time password would most likely be generated in which of the following situations?
The head of the research arid development department at a manufacturing organization believes that his team lacks expertise in some areas, and he decides to hire more experienced researchers to assist in the development of a new product. Which of the following variances are likely to occur as the result of this decision?
1. Favorable labor efficiency variance.
2. Adverse labor rate variance.
3. Adverse labor efficiency variance.
4. Favorable labor rate variance.
Which of the following network types should an organization choose if it wants to allow access only to its own personnel?
Which of the following physical access control is most likely to be based on ’’something you have" concept?
Which of the following responsibilities would ordinary fall under the help desk function of an organization?
Which of the following is the most appropriate way lo record each partner's initial Investment in a partnership?
Which of the following items represents the first thing that should be done with obtained dote in the data analytics process?
Which of the following is a primary driver behind the creation and prloritteation of new strategic Initiatives established by an organization?
During which phase of the contracting process ere contracts drafted for a proposed business activity?
Which of the following should be included in a data privacy poky?
1. Stipulations for deleting certain data after a specified period of time.
2. Guidance on acceptable methods for collecting personal data.
3. A requirement to retain personal data indefinitely to ensure a complete audit trail,
4. A description of what constitutes appropriate use of personal data.
Which of the following types of date analytics would be used by a hospital to determine which patients are likely to require remittance for additional treatment?
Which of the following is on example of a smart device security control intended to prevent unauthorized users from gaining access to a device's data or applications?
Which of the following best explains why an organization would enter into a capital lease contract?
Which of the following practices impacts copyright issues related to the manufacturer of a smart device?
When management uses the absorption costing approach, fixed manufacturing overhead costs are classified as which of the following types of costs?
An Internal auditor is using data analytics to focus on high-risk areas during an engagement. The auditor has obtained data and is working to eliminate redundancies in the data. Which of the following statements is true regarding this scenario?
An organization's account for office supplies on hand had a balance of $9,000 at the end of year one. During year two. The organization recorded an expense of $45,000 for purchasing office supplies. At the end of year two. a physical count determined that the organization has $11 ,500 in office supplies on hand. Based on this Information, what would he recorded in the adjusting entry an the end of year two?
Which of the following controls would be the most effective in preventing the disclosure of an organization's confidential electronic information?
An internal auditor observed that the organization's disaster recovery solution will make use of a cold site in a town several miles away. Which of the following is likely to be a characteristic of this disaster recover/ solution?
Which of the following is an indicator of liquidity that is more dependable than working capital?
Which of the following security controls would be me most effective in preventing security breaches?
Management has established a performance measurement focused on the accuracy of disbursements. The disbursement statistics, provided daily to ail accounts payable and audit staff, include details of payments stratified by amount and frequency. Which of the following is likely to be the greatest concern regarding this performance measurement?
The chief audit executive (CAE) has been asked to evaluate the chief technology officer's proposal to outsource several key functions in the organization's IT department. Which of the following would be the most appropriate action for the CAE to determine whether the proposal aligns with the organization's strategy?
According to IIA guidance on IT, which of the following best describes a logical access control?
Which of the following analytical techniques would an internal auditor use to verify that none of an organization's employees are receiving fraudulent invoice payments?
Which of the following can be viewed as a potential benefit of an enterprisewide resource planning system?
Which of the following cost of capital methods identifies the time period required to recover She cost of the capital investment from the annual inflow produced?
According to IIA guidance, which of the following statements is true regarding penetration testing?
Which of the following would be the strongest control to prevent unauthorized wireless network access?
An organization had a gross profit margin of 40 percent in year one and in year two. The net profit margin was 18 percent in year one and 13 percent in year two. Which of the following could be the reason for the decline in the net profit margin for year two?
How can the concept of relevant cost help management with behavioral analyses?
An organization produces products X and Y. The materials used for the production of both products are limited to 500 Kilograms

(kg ) per month. All other resources are unlimited and their costs are fixed. Individual product details are as follows in order to maximize profit, how much of product Y should the organization produce each month?
$10 $13
2 kg
70 units
6 kg
120 units
An organization contracted a third-party service provider to plan, design, and build a new facility. Senior management would like to transfer all of the risk to the builder. Which type of procurement contract would the organization use?
Which of the following best describes the type of control provided by a firewall?
Which of the following statements is true regarding activity-based costing (ABC)?
In accounting, which of the following statements is true regarding the terms debit and credit?