An industrial facility wants to ensure that only authorized systems reach its PLCs while minimizing disruption to time-sensitive control processes. Which type of firewall would BEST suit this need?
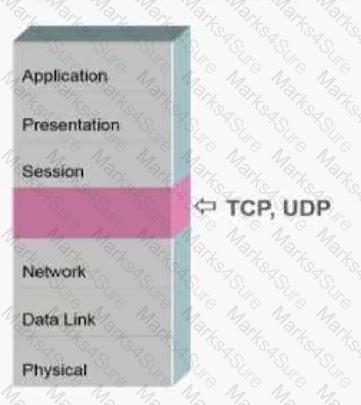
What is the name of the missing layer in the Open Systems Interconnection (OSI) model shown below?
What are the four main categories for documents in the ISA-62443 (IEC 62443) series?
Available Choices (select all choices that are correct)
ISA/IEC 62443 - Part 4-2 covers technical security requirements for which types of IACS components?
Which of the following can be employed as a barrier device in a segmented network?
Available Choices (select all choices that are correct)
Which is a reason for
and physical security regulations meeting a mixed resistance?
Available Choices (select all choices that are correct)
An industrial control system requires strong protection against intentional violations using sophisticated means and moderate skills. According to the Security Level (SL) definitions, which SL should be targeted?
Which is the PRIMARY objective when defining a security zone?
Available Choices (select all choices that are correct)
What is the PRIMARY goal of the IACS Security Program (SP) requirements according to ISA/IEC 62443-2-1?
A national standards body wants to represent its country’s interests at an international level and adopt global standards locally. What role does this organization fulfill?
What is recommended to use between the plant floor and the rest of the company networks?
What is a commonly used protocol for managing secure data transmission over a Virtual Private Network (VPN)?
Available Choices (select all choices that are correct)
Safety management staff are stakeholders of what security program development?
Available Choices (select all choices that are correct)
After receiving an approved patch from the IACS vendor, what is BEST practice for the asset owner to follow?
When selecting a risk assessment methodology for a complex industrial automation system, which approach aligns BEST with ISA/IEC 62443 guidance?
Which organization manages the ISASecure conformance certification program?
Available Choices (select all choices that are correct)
According to the scheme for cybersecurity profiles, which of the following is true about ISA/IEC 62443 security requirements when creating a security profile?
What is one of the primary causes of cyber-related production losses in process control systems?
At Layer 4 of the Open Systems Interconnection (OSI) model, what identifies the application that will handle a packet inside a host?
Available Choices (select all choices that are correct)
Which type of cryptographic algorithms requires more than one key?
Available Choices (select all choices that are correct)
Which of the following is NOT listed under Organizational Security Measures (SP Element 1)?
What are the three main components of the ISASecure Integrated Threat Analysis (ITA) Program?
Available Choices (select all choices that are correct)
Which U.S. Department is responsible for the Chemical Facility Anti-Terrorism Standards (CFATS)?
Who is responsible for defining the tolerable residual cybersecurity risk as an input requirement for all activities?
If an industrial control system experiences frequent unexpected shutdowns causing downtime, which SP Element activities should be reviewed to improve system availability?
As related to IACS Maintenance Service Providers, when do maintenance activities generally start?
What is a key aspect of the relationship between physical security measures and cybersecurity?
What change was introduced in the second edition (2024) of ISA-62443-2-1 compared to the first edition (2010)?
A company needs to create a standardized interface for exchanging real-time plant data between heterogeneous control devices while maintaining a structured organization of data elements such as folders, classes, and methods. Which feature of OPC supports this requirement?
Which is the PRIMARY reason why Modbus over Ethernet is easy to manaqe in a firewall?
Available Choices (select all choices that are correct)
Which of the following attacks relies on a human weakness to succeed?
Available Choices (select all choices that are correct)
Which communications system covers a large geographic area?
Available Choices (select all choices that are correct)
Which of the following is an element of security policy, organization, and awareness?
Available Choices (select all choices that are correct)
Which is a commonly used protocol for managing secure data transmission on the Internet?
Available Choices (select all choices that are correct)
Which of the following is the underlying protocol for Ethernet/IP?
Available Choices (select all choices that are correct)
Which factor drives the selection of countermeasures?
Available Choices (select all choices that are correct)
Which steps are part of implementing countermeasures?
Available Choices (select all choices that are correct)
How should CSMS organizational responsibilities or training be handled over time?
Which is the PRIMARY responsibility of the network layer of the Open Systems Interconnection (OSI) model?
Available Choices (select all choices that are correct)
Which is an important difference between IT systems and IACS?
Available Choices (select all choices that are correct)
Within the National Institute of Standards and Technoloqv Cybersecuritv Framework v1.0 (NIST CSF), what is the status of the ISA 62443 standards?
Available Choices (select all choices that are correct)
Which of the following PRIMARILY determines access privileges for user accounts?
Available Choices (select all choices that are correct)
Which of the following activities is NOT listed under the “Patch Testing” phase in the asset owner requirements?
If an asset owner wants to improve their organization's ability to respond during a cyberattack, which of the following activities would be MOST appropriate to implement?
Which of the following ISA-99 (IEC 62443) Reference Model levels is named correctly?
Which of the following is NOT listed as a potential consequence of compromising IACS according to the ISA99 Committee scope?
Which is one of the PRIMARY goals of providing a framework addressing secure product development life-cycle requirements?
What type of malware disrupted an emergency shutdown capability in safety systems?
As related to technical security requirements for IACS components, what does CCSC stand for?
A national standards body wants to represent its country’s interests at an international level and adopt global standards locally. What role does this organization fulfill?