Exhibit
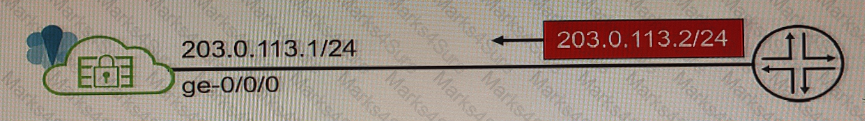
You configure Source NAT using a pool of addresses that are in the same subnet range as the external ge-0/0/0 interface on your vSRX device. Traffic that is exiting the internal network can reach external destinations, but the return traffic is being dropped by the service provider router.
Referring to the exhibit, what must be enabled on the vSRX device to solve this problem?
Exhibit
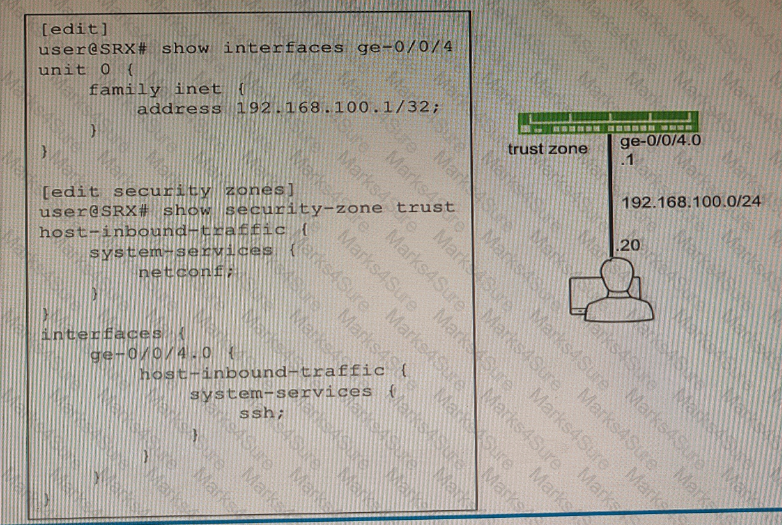
You are not able to ping the default gateway of 192.168 100 1 (or your network that is located on your SRX Series firewall.
Referring to the exhibit, which two commands would correct the configuration of your SRX Series device? (Choose two.)
A)

B)
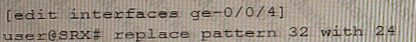
C)

D)

you are connecting two remote sites to your corporate headquarters site. You must ensure that traffic
passes corporate headquarter.
In this scenario, which VPN should be used?
Exhibit
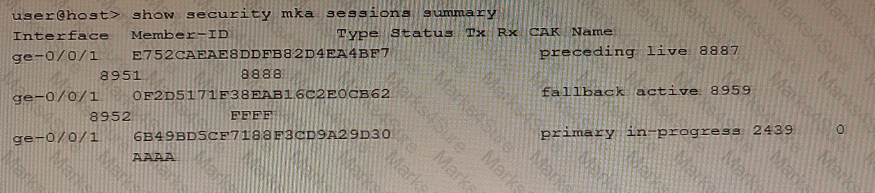
Referring to the exhibit, which two statements are true about the CAK status for the CAK named "FFFP"? (Choose two.)
Exhibit
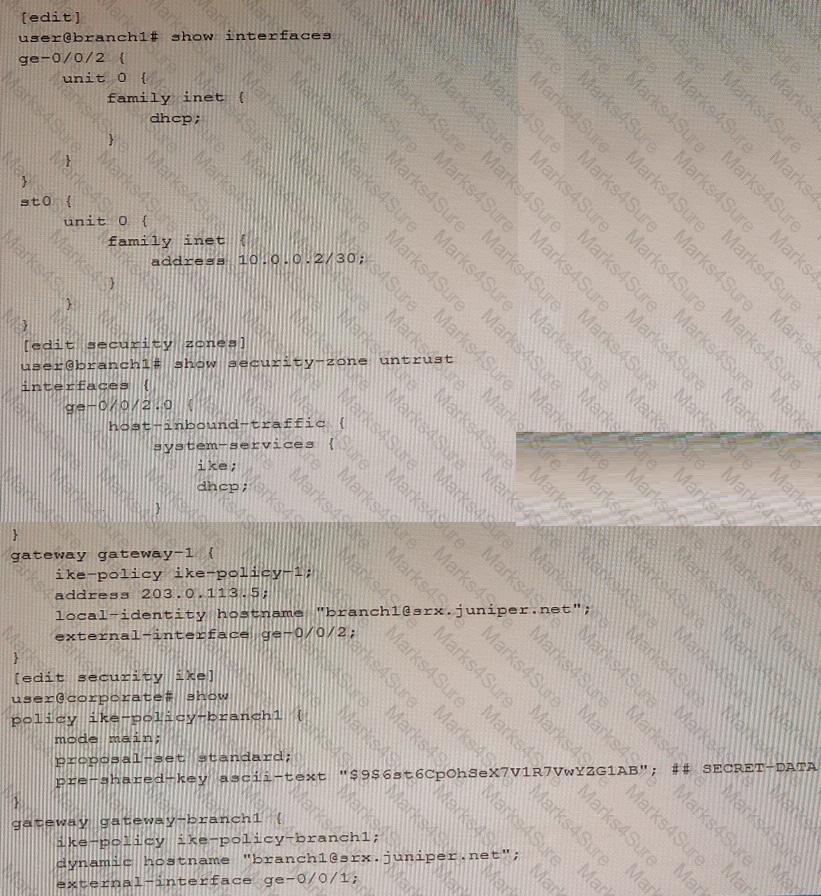
You are trying to configure an IPsec tunnel between SRX Series devices in the corporate office and branch1. You have committed the configuration shown in the exhibit, but the IPsec tunnel is not establishing.
In this scenario, what would solve this problem.
Your company wants to use the Juniper Seclntel feeds to block access to known command and control servers, but they do not want to use Security Director to manage the feeds.
Which two Juniper devices work in this situation? (Choose two)
What are two important function of the Juniper Networks ATP appliance solution? (Choose two.).
You are asked to determine if the 203.0.113.5 IP address has been added to the third-party security feed, DS hield, from Juniper Seclnte1. You have an SRX Series device that is using Seclnte1 feeds from Juniper ATP Cloud
Which command will return this information?
You have noticed a high number of TCP-based attacks directed toward your primary edge device. You are asked to
configure the IDP feature on your SRX Series device to block this attack.
Which two IDP attack objects would you configure to solve this problem? (Choose two.)
Exhibit
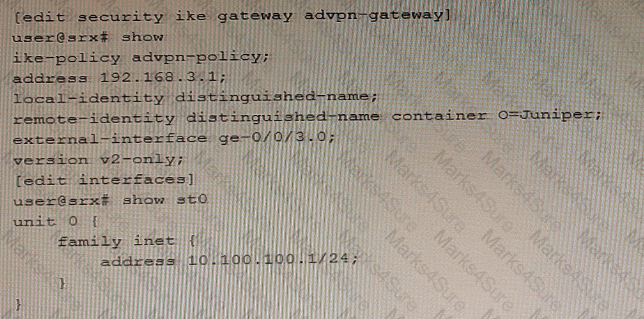
Referring to the exhibit, a spoke member of an ADVPN is not functioning correctly.
Which two commands will solve this problem? (Choose two.)
A)
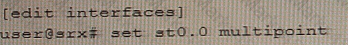
B)
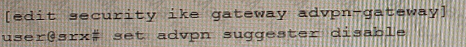
C)

D)

Click the Exhibit button.
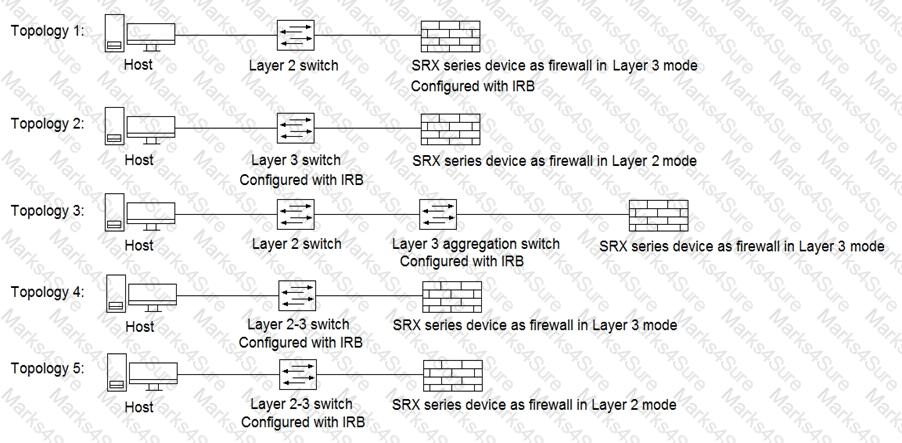
Referring to the exhibit, which three topologies are supported by Policy Enforcer? (Choose three.)
You issue the command shown in the exhibit.
Which policy will be active for the identified traffic?
Which two features would be used for DNS doctoring on an SRX Series firewall? (Choose two.)
You are asked to deploy Juniper atp appliance in your network. You must ensure that incidents and
alerts are sent to your SIEM.
In this scenario, which logging output format is supported?
You have a webserver and a DNS server residing in the same internal DMZ subnet. The public Static NAT addresses for
the servers are in the same subnet as the SRX Series devices internet-facing interface. You implement DNS doctoring to
ensure remote users can access the webserver.Which two statements are true in this scenario? (Choose two.)
Exhibit:

You are troubleshooting a firewall filter shown in the exhibit that is intended to log all traffic and block
only inbound telnet traffic on interface ge-0/0/3.
How should you modify the configuration to fulfill the requirements?
Exhibit
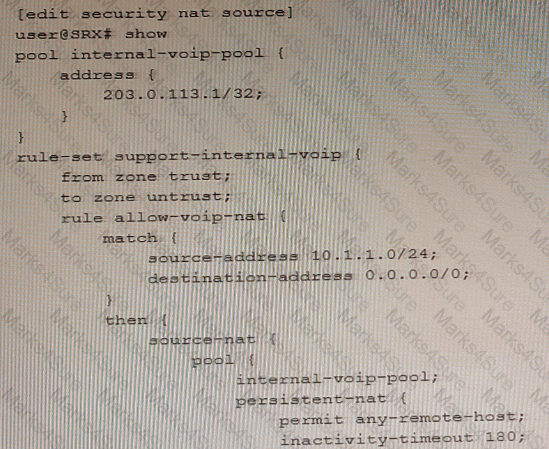
Referring to the exhibit, an internal host is sending traffic to an Internet host using the 203.0.113.1 reflexive address with source port 54311.
Which statement is correct in this situation?
Click the Exhibit button.
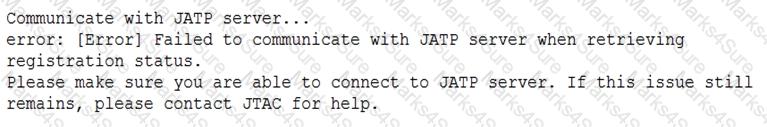
When attempting to enroll an SRX Series device to JATP, you receive the error shown in the exhibit. What is the cause of the error?
Exhibit
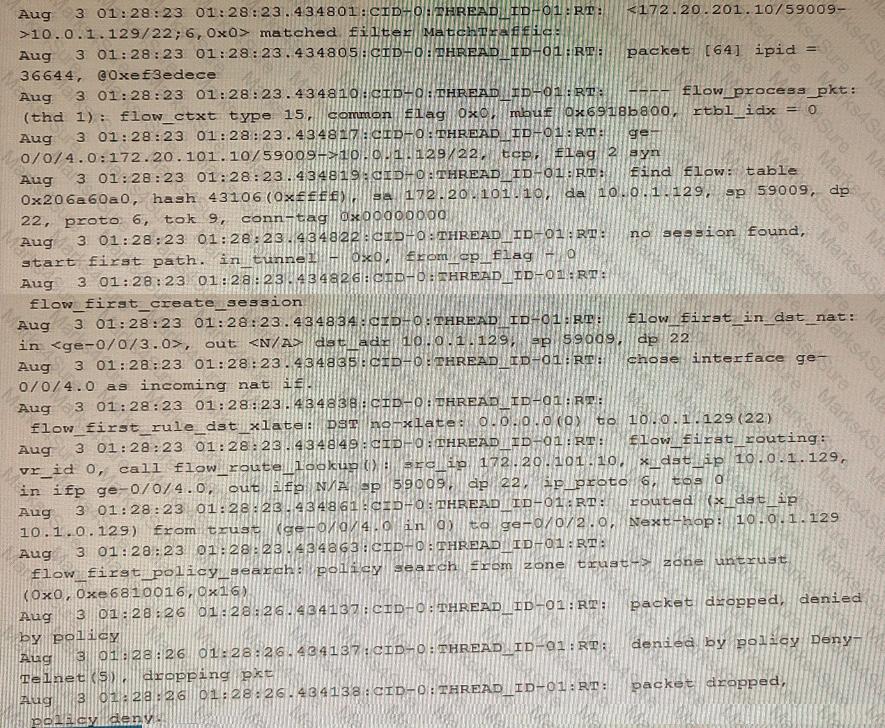
Which two statements are correct about the output shown in the exhibit. (Choose two.)
You are requested to enroll an SRX Series device with Juniper ATP Cloud.
Which statement is correct in this scenario?
The monitor traffic interface command is being used to capture the packets destined to and the from the SRX Series device.
In this scenario, which two statements related to the feature are true? (Choose two.)
Exhibit
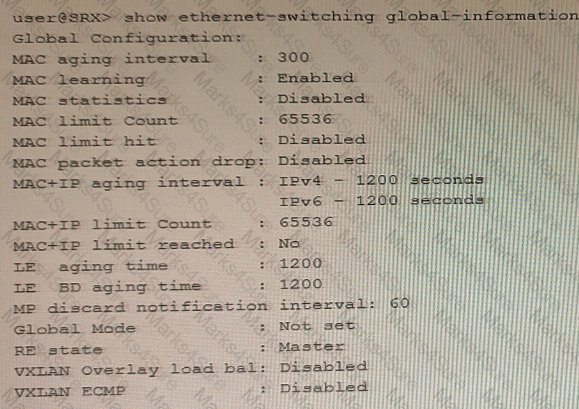
You have configured the SRX Series device to switch packets for multiple directly connected hosts that are within the same broadcast domain However, the traffic between two hosts in the same broadcast domain are not matching any security policies
Referring to the exhibit, what should you do to solve this problem?