What are three core components for enabling advanced policy-based routing? (Choose three.)
Referring to the exhibit, you are attempting to set up a remote access VPN on your SRX series devices.
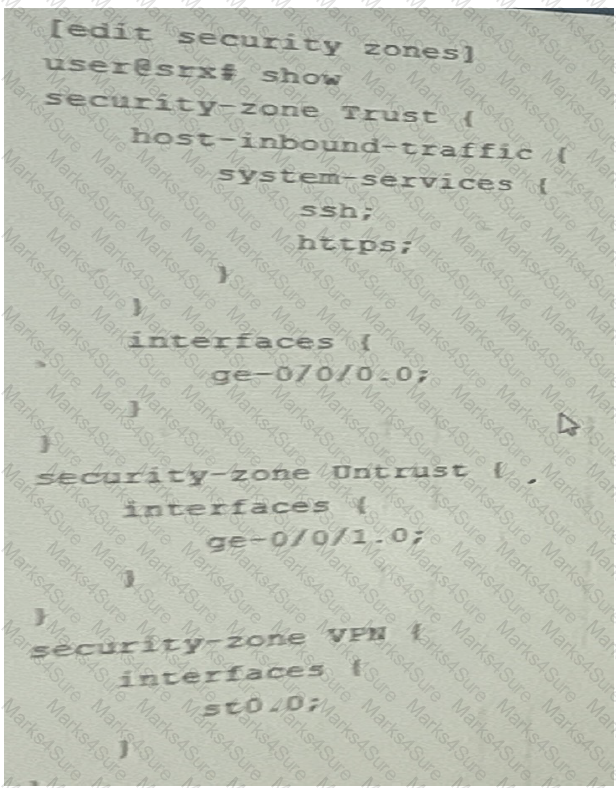
However you are unsure of which system services you should allow and in which zones they should be allowed to correctly finish the remote access VPN configuration
Which two statements are correct? (Choose two.)
In a multinode HA environment, which service must be configured to synchronize between nodes?
You have deployed automated threat mitigation using Security Director with Policy Enforcer, Juniper ATP Cloud, SRX Series devices, and EX Series switches.
In this scenario, which device is responsible for blocking the infected hosts?
Which encapsulation type must be configured on the lt-0/0/0 logical units for an interconnect
logical systems VPLS switch?
Which two statements are correct about automated threat mitigation with Security Director? (Choose two.)
An ADVPN configuration has been verified on both the hub and spoke devices and it seems fine. However, OSPF is not functioning as expected.
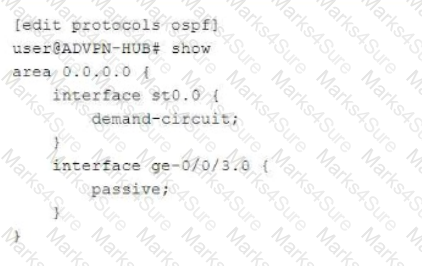
Referring to the exhibit, which two statements under interface st0.0 on both the hub and spoke devices would solve this problem? (Choose two.)
You are asked to connect two hosts that are directly connected to an SRX Series device. The traffic should flow unchanged as it passes through the SRX, and routing or switch lookups should not be performed. However, the traffic should still be subjected to security policy checks.
What will provide this functionality?
The exhibit shows part of the flow session logs.
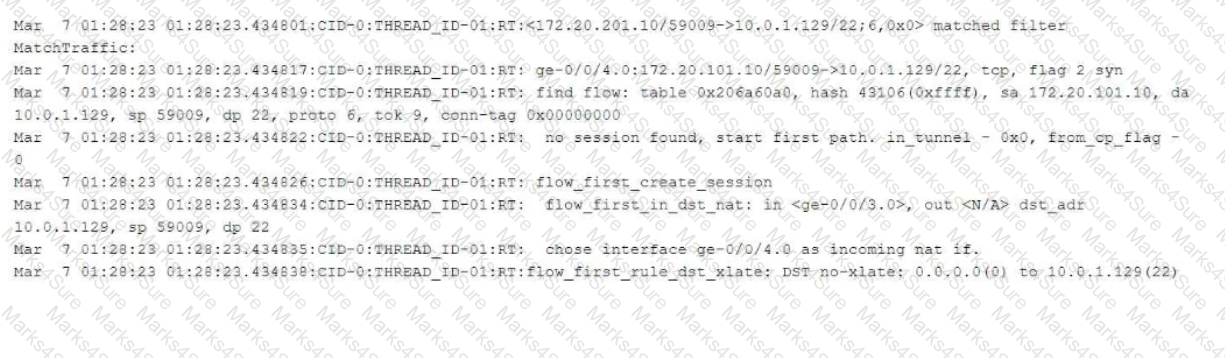
Which two statements are true in this scenario? (Choose two.)
Referring to the exhibit,
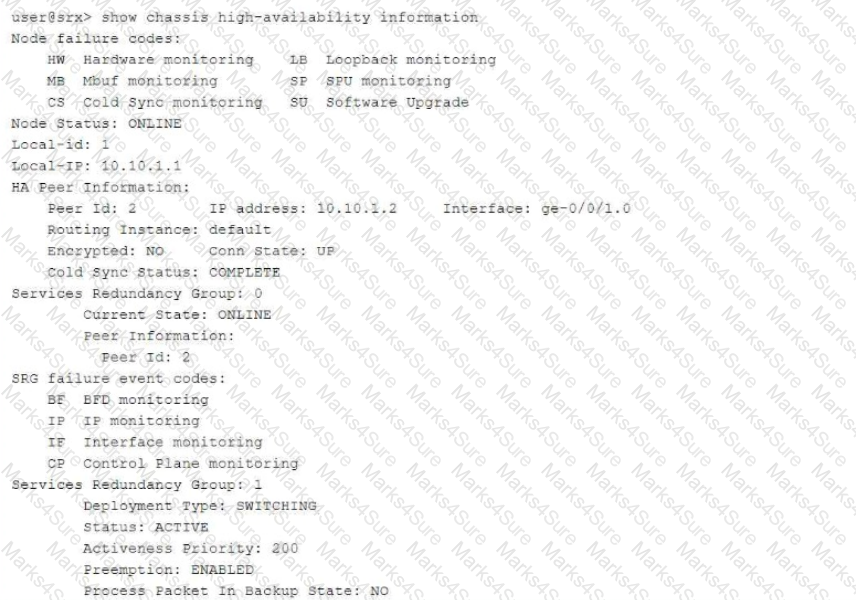
which three statements about the multinode HA environment are true? (Choose three.)
You want to create a connection for communication between tenant systems without using physical revenue ports on the SRX Series device.
What are two ways to accomplish this task? (Choose two.)
You are deploying IPsec VPNs to securely connect several enterprise sites with ospf for dynamic
routing. Some of these sites are secured by third-party devices not running Junos.
Which two statements are true for this deployment? (Choose two.)
You are asked to see if your persistent NAT binding table is exhausted.
Which show command would you use to accomplish this task?
Which two statements about policy enforcer and the forescout integration are true? (Choose two)
You want to bypass IDP for traffic destined to social media sites using APBR, but it is not working and IDP is dropping the session.
What are two reasons for this problem? (Choose two.)
Your IPsec tunnel is configured with multiple security associations (SAs). Your SRX Series device supports the CoS-based IPsec VPNs with multiple IPsec SAs feature. You are asked to configure CoS for this tunnel.
Which two statements are true in this scenario? (Choose two.)
You want to test how the device handles a theoretical session without generating traffic on the Junos security device.
Which command is used in this scenario?
A company has acquired a new branch office that has the same address space as one of its local networks, 192.168.100.0/24. The offices need to communicate with each other.
Which two NAT configurations will satisfy this requirement? (Choose two.)
Which two statements are true about the procedures the Junos security device uses when handling traffic destined for the device itself? (Choose two.)
You are configuring advanced policy-based routing. You have created a static route with next
hop of an interface in your inet.0 routing table
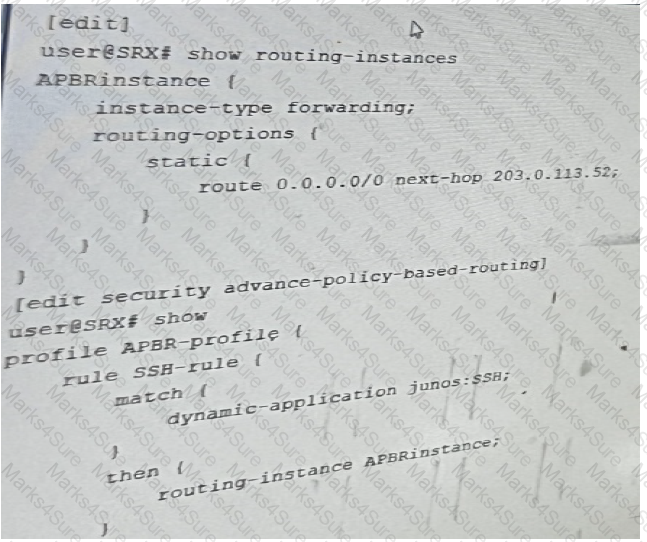

Referring to the exhibit, what should be changed to solve this issue?
You are deploying threat remediation to endpoints connected through third-party devices.
In this scenario, which three statements are correct? (Choose three.)
Exhibit:
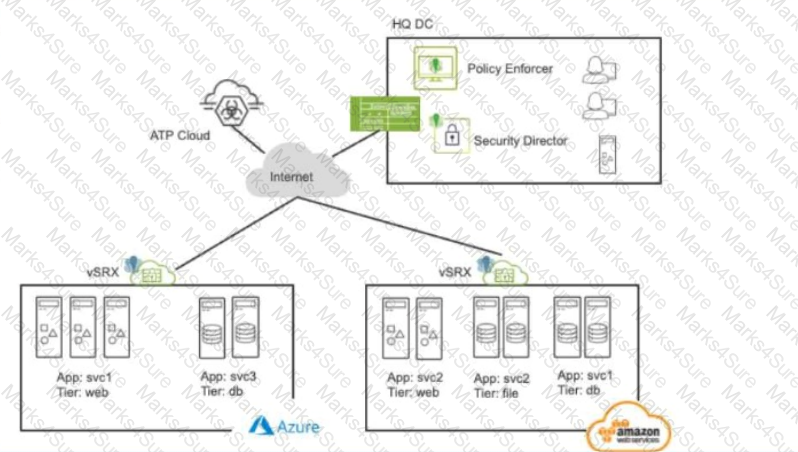
Referring to the exhibit, what do you use to dynamically secure traffic between the Azure and AWS clouds?
Click the Exhibit button.
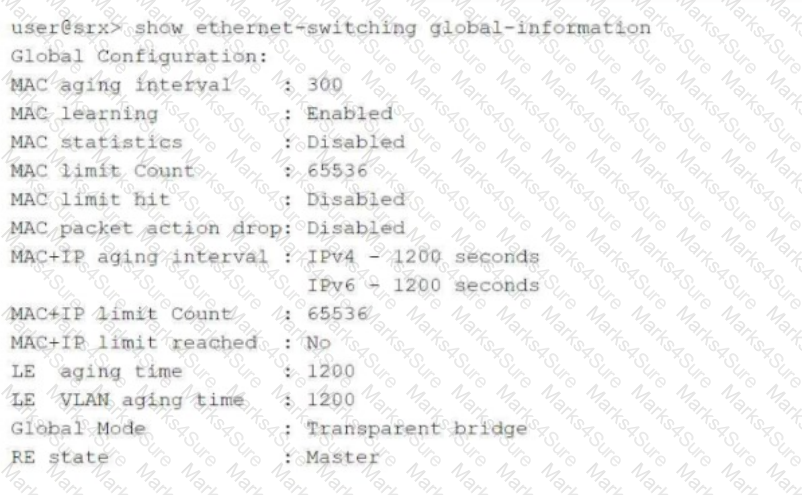
Referring to the exhibit, which two statements are correct? (Choose two.)
You are setting up multinode HA for redundancy.
Which two statements are correct in this scenario? (Choose two.)
You have deployed automated threat mitigation using Security Director with Policy Enforcer, Juniper ATP Cloud, SRX Series devices, Forescout, and third-party switches.
In this scenario, which device is responsible for communicating directly to the third-party switches when infected hosts need to be blocked?