You have a Microsoft 365 IS subscription and use Microsoft Defender for Cloud Apps. You register a cloud app named App1 in Microsoft Entra 10. You need to create an access policy for Appl. What should you do first?
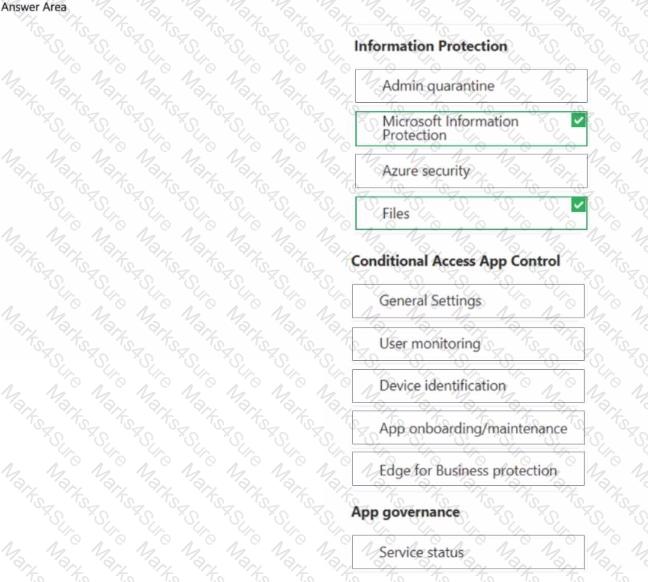
You have a Microsoft 365 E5 subscription and use Microsoft Defender for Cloud Apps. You need to create a file policy named Policy1 that meets the following requirements:
• Inspects files in connected software as a service (SaaS) apps
* Inspects protected files
Which two settings should you configure? To answer, select the appropriate settings in the answer area. NOTE: Each correct selection is worth one point.
You have a Microsoft 365 E5 subscription.
You plan to implement Microsoft 365 compliance policies to meet the following requirements:
Identify documents that are stored in Microsoft Teams and SharePoint Online that contain Personally Identifiable Information (PII).
Report on shared documents that contain PII.
What should you create?
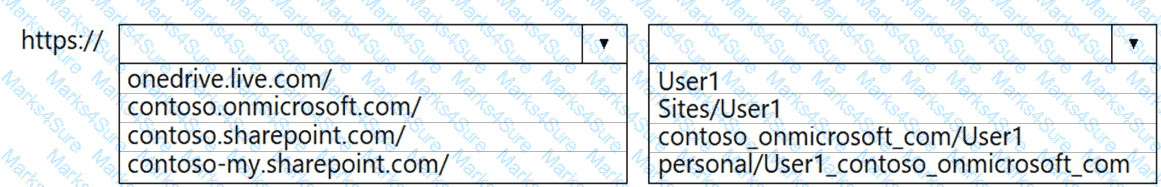
You have a Microsoft 365 subscription that links to an Azure Active Directory (Azure AD) tenant named contoso.onmicrosoft.com.
A user named User1 stores documents in Microsoft OneDrive.
You need to place the contents of User1’s OneDrive account on an eDiscovery hold.
Which URL should you use for the eDiscovery hold? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You have a Microsoft 365 E5 subscription that contains the users shown in the following table.
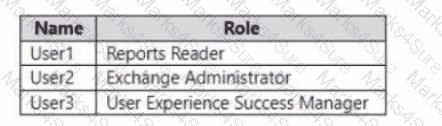
Which users can review the Adoption Score in the Microsoft 365 admin center?
You have a Microsoft 365 tenant.
Company policy requires that all Windows 10 devices meet the following minimum requirements:
Require complex passwords.
Require the encryption of data storage devices.
Have Microsoft Defender Antivirus real-time protection enabled.
You need to prevent devices that do not meet the requirements from accessing resources in the tenant.
Which two components should you create? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
You have a Microsoft 365 E5 subscription. You need to create a mail-enabled contact. Which portal should you use?
You have a Microsoft 365 E5 subscription that contains the users shown in the following table.
You have labels in Microsoft 365 as shown in the following table.
The content in Microsoft 365 is assigned labels as shown in the following table.
You have labels In Microsoft 365 as shown in the following table.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
Your network contains an Active Directory domain and a Microsoft Entra tenant.
The network uses a firewall that contains a list of allowed outbound domains.
You begin to implement directory synchronization, but it fails.
The firewall currently allows only:
microsoft.com
office.com
You need to ensure that directory synchronization completes successfully.
What is the best approach to achieve the goal?
You have a Microsoft 365 E5 subscription and use Microsoft Purview. The subscription contains the devices shown in the following table.
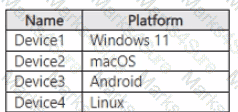
All the devices are onboarded to Microsoft Defender for Endpoint. You plan to deploy Endpoint data loss prevention (Endpoint DLP) policies. Which devices can be protected by using the DLP policies?
You configure an anti-phishing policy as shown in the following exhibit.
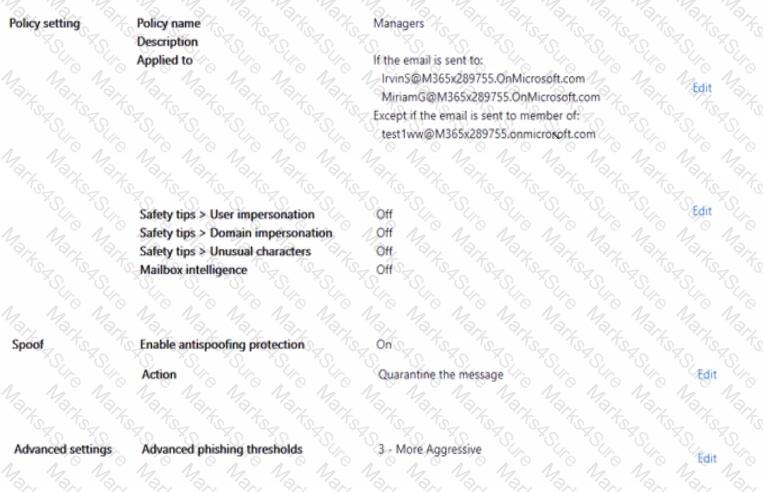
Use the drop-down menus to select the answer choke that completes each statement based on the information presented in the graphic.
NOTE: Each correct selection is worth one point.
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
Your network contains an Active Directory domain named contoso.com that is synced to Microsoft Azure Active Directory (Azure AD).
You manage Windows 10 devices by using Microsoft System Center Configuration Manager (Current Branch).
You configure a pilot for co-management.
You add a new device named Device1 to the domain. You install the Configuration Manager client on Device1.
You need to ensure that you can manage Device1 by using Microsoft Intune and Configuration Manager.
Solution: Define a Configuration Manager device collection as the pilot collection. Add Device1 to the collection.
Does this meet the goal?
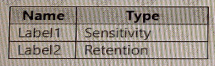
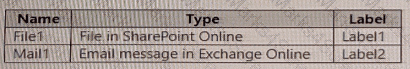
You have a Microsoft 365 E5 subscription that contains two sensitivity labels named Label1 and Label2. The subscription contains a Windows device named Device1 that is onboarded to Microsoft Purview. Device1 contains the files shown in the following table.
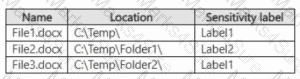
You create a data loss prevention (DLP) policy named Policy1 that has the following configurations:
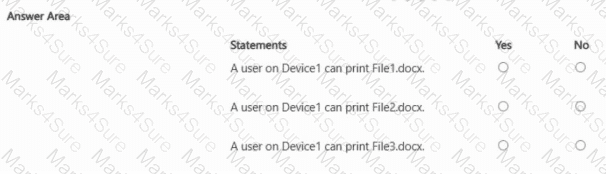
You have a Microsoft 365 E5 subscription.
You have an Azure AD tenant named contoso.com that contains the following users:
• Admin1
• Admin2
• User1
Contoso.com contains an administrative unit named AIM that has no role assignments. User1 is a member of AU1. You create an administrative unit named AU2 that does NOT have any members or role assignments. For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.

You have a Microsoft 365 E5 tenant that contains 100 Windows 10 devices.
You plan to deploy a Windows 10 Security Baseline profile that will protect secrets stored in memory.
What should you configure in the profile?
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
Your network contains an on-premises Active Directory domain named contoso.com. The domain contains the users shown in the following table.
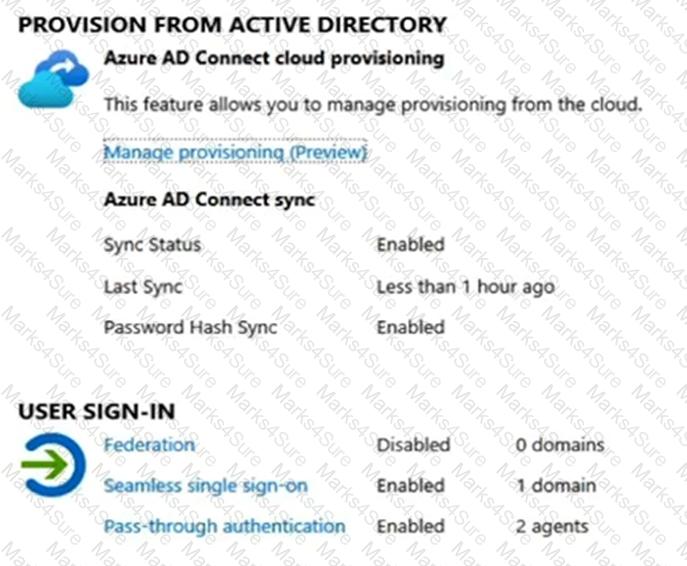
The domain syncs to an Azure AD tenant named contoso.com as shown in the exhibit. (Click the Exhibit tab.)
User2 fails to authenticate to Azure AD when signing in as user2@fabrikam.com.
You need to ensure that User2 can access the resources in Azure AD.
Solution: From the on-premises Active Directory domain, you set the UPN suffix for User2 to @contoso.com. You instruct User2 to sign in as user2@contoso.com.
Does this meet the goal?
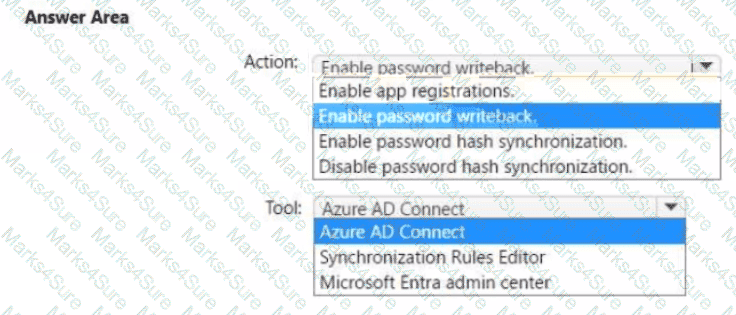
You need to ensure that Admin4 can use SSPR.
Which tool should you use. and which action should you perform? To answer, select the appropriate options m the answer area.
NOTE: Each correct selection is worth one point.
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a Microsoft 365 E5 subscription.
You create an account for a new security administrator named SecAdmin1.
You need to ensure that SecAdmin1 can manage Microsoft Defender for Office 365 settings and policies for Microsoft Teams, SharePoint, and OneDrive.
Solution: From the Microsoft Entra admin center, you assign SecAdmin1 the Security Administrator role.
Does this meet the goal?
You have a Microsoft 365 subscription.
You integrate Microsoft Defender for Cloud Apps with Microsoft Defender for Endpoint.
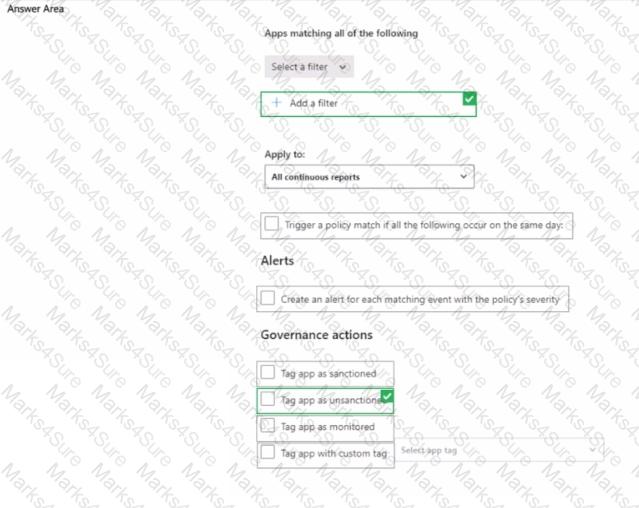
You need to create a policy to block users from accessing discovered apps that have a risk score of 4 or lower.
Which two settings should you configure? To answer, select the appropriate settings in the answer area.
NOTE: Each correct selection is worth one point.
You need to ensure that all the sales department users can authenticate successfully during Project1 and Project2.
Which authentication strategy should you implement for the pilot projects?
HOTSPOT
You create the Microsoft 365 tenant.
You implement Azure AD Connect as shown in the following exhibit.
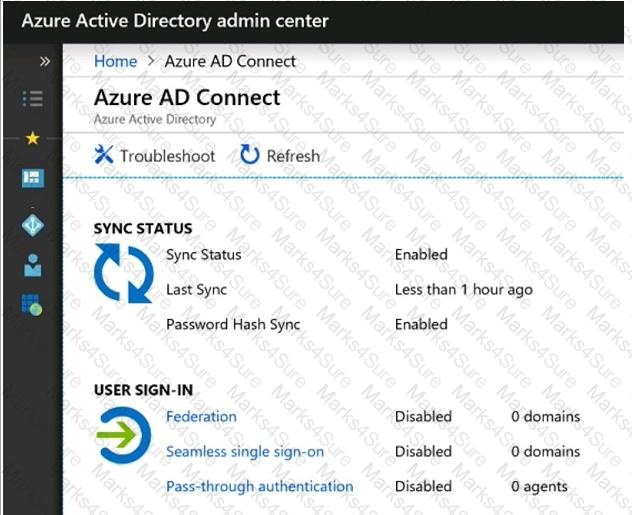
Use the drop-down menus to select the answer choice that completes each statement based on the information presented in the graphic.
NOTE: Each correct selection is worth one point.

Which role should you assign to User1?
Available Choices (select all choices that are correct)
You are evaluating the required processes for Project1.
You need to recommend which DNS record must be created while adding a domain name for the project.
Which DNS record should you recommend?
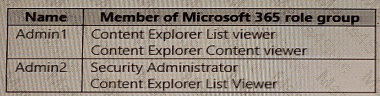
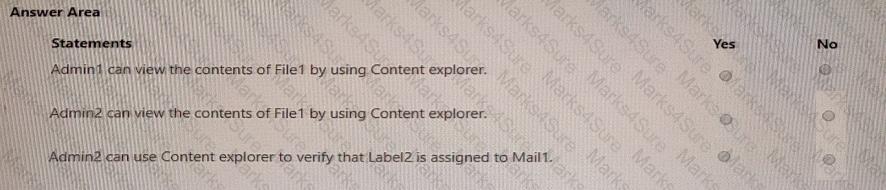
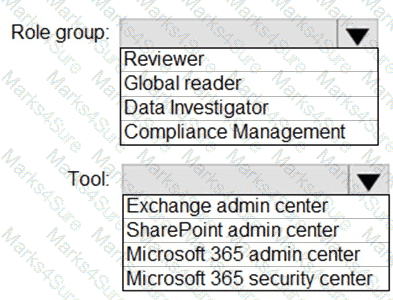
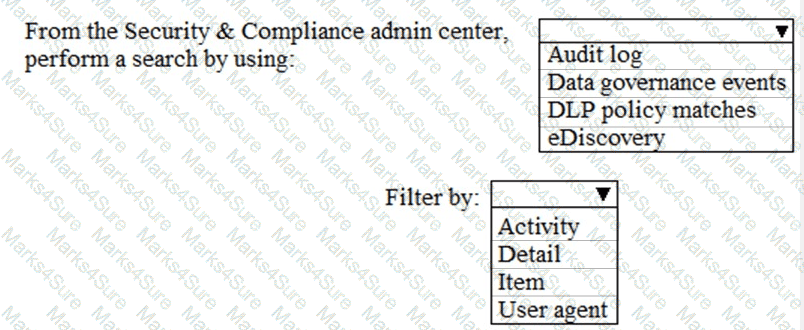
You need to ensure that User2 can review the audit logs. The solutions must meet the technical requirements.
To which role group should you add User2, and what should you use? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You are evaluating the use of multi-factor authentication (MFA).
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.

You need to configure Azure AD Connect to support the planned changes for the Montreal Users and Seattle Users OUs.
What should you do?
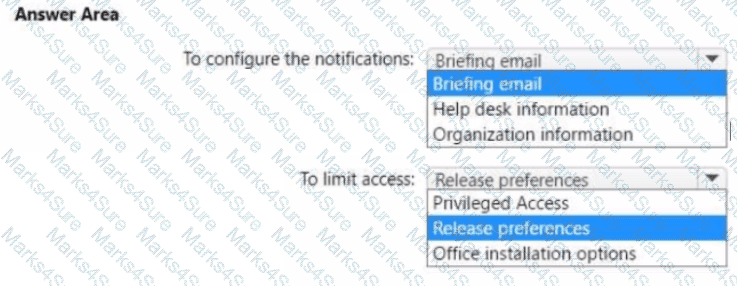
You need to configure the Office 365 service status notifications and limit access to the service and feature updates. The solution must meet the technical requirements.
What should you configure in the Microsoft 365 admin center? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You need to configure just in time access to meet the technical requirements.
What should you use?
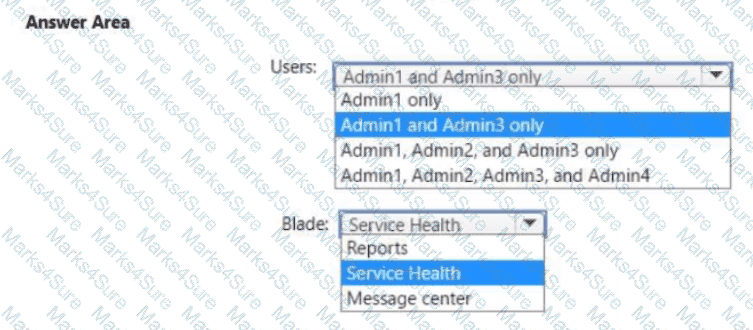
You need to ensure that the Microsoft 365 incidents and advisories are reviewed monthly.
Which users can review the incidents and advisories, and which blade should the users use? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You need to meet the technical requirement for the SharePoint administrator. What should you do? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
You need to meet the technical requirement for large-volume document retrieval. What should you create?
You need to protect the U.S. PII data to meet the technical requirements.
What should you create?
You need to recommend a solution for the security administrator. The solution must meet the technical requirements.
What should you include in the recommendation?
You need to meet the technical requirement for the EU PII data.
What should you create?
You need to ensure that User1 can enroll the devices to meet the technical requirements. What should you do?
You need to meet the technical requirement for log analysis.
What is the minimum number of data sources and log collectors you should create from Microsoft Cloud App Security? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

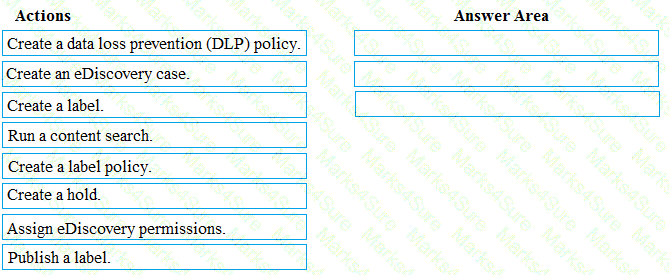
You need to meet the requirement for the legal department.
Which three actions should you perform in sequence from the Security & Compliance admin center? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.
As of March, how long will the computers in each office remain supported by Microsoft? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

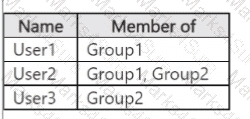
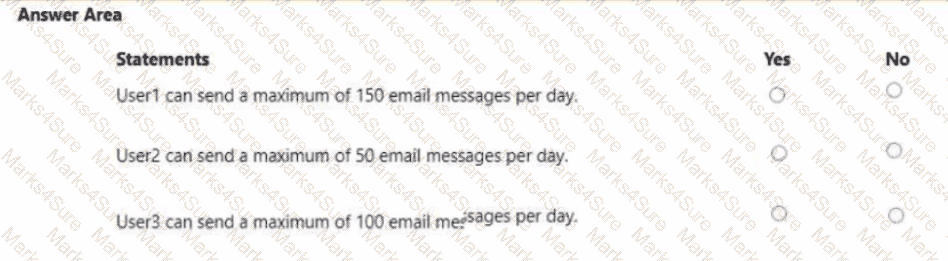
You have a Microsoft 365 E5 subscription that contains the users shown in the following table.
The subscription has the following two anti-spam policies:
• Name: AntiSpam1
• Priority: 0
• Induce these users, groups and domains
o Users: User3
o Groups: Group1
• Exclude these users, groups and domains
o Groups: Group2
• Message limits
o Set a daily message limit 100
• Name: AntiSpam2
• Priority: 1
• Include these users, groups and domains
o Users: User! o Groups: Group2
• Exclude these users, groups and domains
o Users: User3
• Message limits
o Set a daily message limit 50
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Your network contains an on-premises Active Directory domain. The domain contains 2,000 computers that run Windows 10.
You purchase a Microsoft 365 subscription.
You implement password hash synchronization and Azure AD Seamless Single Sign-On (Seamless SSO).
You need to ensure that users can use Seamless SSO from the Windows 10 computers.
What should you do?
: 225
You implement Microsoft Azure Advanced Threat Protection (Azure ATP).
You have an Azure ATP sensor configured as shown in the following exhibit.

How long after the Azure ATP cloud service is updated will the sensor update?
You need to ensure that the support technicians can meet the technical requirement for the Montreal office mobile devices.
What is the minimum of dedicated support technicians required?
You need to meet the compliance requirements for the Windows 10 devices.
What should you create from the Intune admin center?
You need to create the Microsoft Store for Business. Which user can create the store?
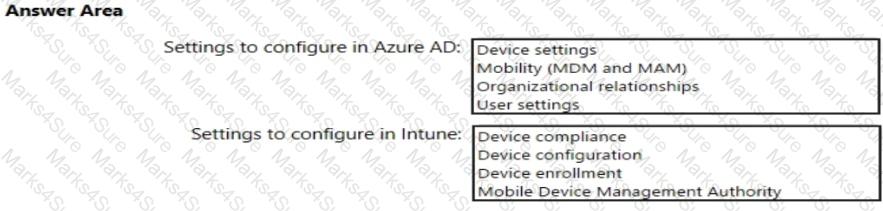
You need to meet the Intune requirements for the Windows 10 devices.
What should you do? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
Your network contains an Active Directory domain named contoso.com that is synced to Microsoft Azure Active Directory (Azure AD).
You manage Windows 10 devices by using Microsoft System Center Configuration Manager (Current Branch).
You configure a pilot for co-management.
You add a new device named Device1 to the domain. You install the Configuration Manager client on Device1.
You need to ensure that you can manage Device1 by using Microsoft Intune and Configuration Manager.
Solution: You create a device configuration profile from the Device Management admin center.
Does this meet the goal?
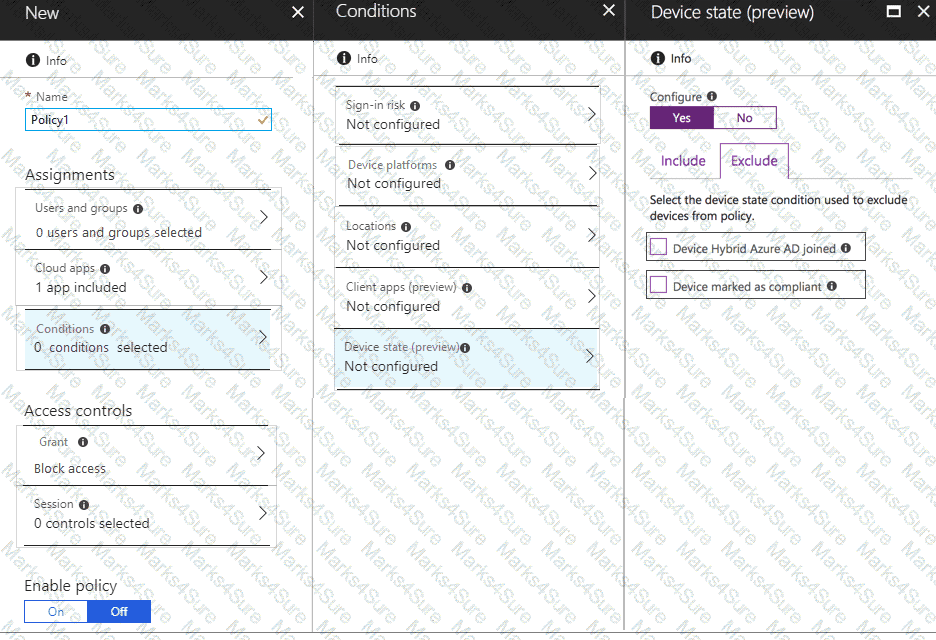
You need to configure a conditional access policy to meet the compliance requirements.
You add Exchange Online as a cloud app.
Which two additional settings should you configure in Policy1? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You need to meet the technical requirements and planned changes for Intune.
What should you do? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.