A government entity wants to implement technology that can block websites based on country code. Which of the following will best enable this requirement?
Which of the following protocols is used to route traffic on the public internet?
Which of the following layers of the OSI model is responsible for end-to-end encryption?
A user connects to a corporate VPN via a web browser and is able to use TLS to access the internal financial system to input a time card. Which of the following best describes how the VPN is being used?
A company implements a video streaming solution that will play on all computers that have joined a particular group, but router ACLs are blocking the traffic. Which of the following is the most appropriate IP address that will be allowed in the ACL?
Which of the following steps in the troubleshooting methodology comes after using a top-to-top buttom examination of the OSI model to determine cause?
An administrator is setting up an SNMP server for use in the enterprise network and needs to create device IDs within a MIB. Which of the following describes the function of a MIB?
An attacker gained access to the hosts file on an endpoint and modified it. Now, a user is redirected from the company’s home page to a fraudulent website. Which of the following most likely happened?
Which of the following network traffic types is sent to all nodes on the network?
Users report latency with a SaaS application. Which of the following should a technician adjust to fix the issue?
A customer wants to cache commonly used content to reduce the number of full page downloads from the internet. Which of the following should the network administrator recommend?
Which of the following is created to illustrate the effectiveness of wireless networking coverage in a building?
An organization recently connected a new computer to the LAN. The user is unable to ping the default gateway. The technician examines the configuration and sees a self-assigned IP address. Which of the following is the most likely cause?
A new SQL server is identified as allowing FTP access to all users. Which of the following would a systems administrator most likely do to ensure only the required services are allowed?
A company is hosting a secure that requires all connections to the server to be encrypted. A junior administrator needs to harded the web server. The following ports on the web server. The following ports on the web server are open:

Which of the following ports should be disabled?
Which of the following, in addition to a password, can be asked of a user for MFA?
An attack on an internal server is traced to an isolated guest network. Which of the following best describes the attack?
A network administrator needs to create a way to redirect a network resource that has been on the local network but is now hosted as a SaaS solution. Which of the following records should be used to accomplish the task?
Which of the following would be violated if an employee accidentally deleted a customer's data?
A network administrator is deploying a new switch and wants to make sure that the default priority value was set for a spanning tree. Which of the following values would the network administrator expect to see?
An organization is struggling to get effective coverage using the wireless network. The organization wants to implement a solution that allows for continuous connectivity anywhere in the facility. Which of the following should the network administrator suggest to ensure the best coverage?
Which of the following disaster recovery concepts is calculated by dividing the total hours of operation by the total number of units?
A network technician is designing a LAN for a new facility. The company is expecting more than 300 devices to connect to the network. Which of the following masks will provide the most efficient subnet?
A network administrator is configuring a wireless network with an ESSID. Which of the following is a user benefit of ESSID compared to SSID?
A small business is choosing between static and dynamic routing for its network. Which of the following is the best reason to use dynamic routing in a growing network?
A network technician is requesting a fiber patch cord with a connector that is round and twists to install. Which of the following is the proper name of this connector type?
Which of the following physical installation factors is the most important when a network switch is installed in a sealed enclosure?
A technician needs to set up a wireless connection that utilizes MIMO on non-overlapping channels. Which of the following would be the best choice?
A network administrator needs to implement a solution to filter access to the internet. Which of the following should the administrator most likely implement?
Which of the following allows a network administrator to analyze attacks coming from the internet without affecting latency?
Which of the following is a type of NAC that uses a set of policies to allow or deny access to the network based on the user’s identity?
Which of the following is used to redistribute traffic between one source and multiple servers that run the same service?
Which of the following connection methods allows a network engineer to automate configuration deployment for network devices across the environment?
A network administrator is implementing security zones for each department. Which of the following should the administrator use to accomplish this task?
A network administrator is setting up a firewall to protect the organization’s network from external threats. Which of the following should the administrator consider first when configuring the firewall?
Which of the following devices functions mainly at the data link layer of the OSI model and is used to connect a fiber-optic cable to a network interface?
A junior network technician at a large company needs to create networks from a Class C address with 14 hosts per subnet. Which of the following numbers of host bits is required?
Which of the following is most closely associated with a dedicated link to a cloud environment and may not include encryption?
A network administrator performed upgrades on a server and installed a new NIC to improve performance. Following the upgrades, usera are unable to reach the server. Which of the following is the most likely reason.
Which of the following enables an organization to leverage an identity provider to manage access across SaaS applications?
A data center interconnect using a VXLAN was recently implemented. A network engineer observes slow performance and fragmentation on the interconnect. Which of the following technologies will resolve the issue?
Which of the following is used to describe the average duration of an outage for a specific service?
A network engineer is designing a secure communication link between two sites. The entire data stream needs to remain confidential. Which of the following will achieve this goal?
Which of the following ports should a network administrator enable for encrypted login to a network switch?
A network administrator is planning to implement device monitoring to enhance network visibility. The security that the solution provides authentication and encryption. Which of the following meets these requirements?
A network administrator configured a router interface as 10.0.0.95 255.255.255.240. The administrator discovers that the router is not routing packets to a web server with IP 10.0.0.81/28. Which of the following is the best explanation?
A user submits an escalated ticket regarding failed logins on their laptop. The user states that the time displayed on the laptop is incorrect. An administrator thinks the issue is related to the NTP. Which of the following should the administrator do next?
A customer needs six usable IP addresses. Which of the following best meets this requirement?
Which of the following is associated with avoidance, acceptance, mitigation, and transfer?
Which of the following devices can operate in multiple layers of the OSI model?
Which of the following should be configured so users can authenticate to a wireless network using company credentials?
A network administrator configures a new network discovery tool and is concerned that it might disrupt business operations. Which of the following scan types should the administrator configure?
Which of the following network devices converts wireless signals to electronic signals?
A technician is deploying new networking hardware for company branch offices. The bridge priority must be properly set. Which of the following should the technician configure?
A server administrator needs to add a record to the company's DNS server to verify ownership of a web domain. The administrator has the record's name and value. Which of the following record types should the administrator use to add the record to the DNS server?
A network administrator needs to divide 192.168.1.0/24 into two equal halves. Which of the following subnet masks should the administrator use?
After a recent security awareness phishing campaign, the cybersecurity team discovers that additional security measures need to be set up when users access potentially malicious websites. Which of the following security measures will best address this concern?
A network administrator needs to assign IP addresses to a newly installed network. They choose 192.168.1.0/24 as their network address and need to create three subnets with 30 hosts on each subnet. Which of the following is a valid subnet mask that will meet the requirements?
Which of the following is a company most likely enacting if an accountant for the company can only see the financial department's shared folders?
After installing a series of Cat 8 keystones, a data center architect notices higher than normal interference during tests. Which of the following steps should the architect take to troubleshoot the issue?
A network manager wants to implement a SIEM system to correlate system events. Which of the following protocols should the network manager verify?
A network technician was recently onboarded to a company. A manager has
tasked the technician with documenting the network and has provided the technician With partial information from previous documentation.
Instructions:
Click on each switch to perform a network discovery by entering commands into the terminal. Fill in the missing information using drop-down menus provided.
Which of the following types of attacks is most likely to occur after an attacker sets up an evil twin?
A network engineer needs to deploy an access point at a remote office so that it will not communicate back to the wireless LAN controller. Which of the following deployment methods must the engineer use to accomplish this task?
A network engineer is installing new PoE wireless APs. The first five APs deploy successfully, but the sixth one fails to start. Which of the following should the engineer investigate first?
A network administrator is unable to ping a remote server from a newly connected workstation that has been added to the network. Ping to 127.0.0.1 on the workstation is failing. Which of the following should the administrator perform to diagnose the problem?
Which of the following attacks utilizes a network packet that contains multiple network tags?
A company has been added to an unapproved list because of spam. The network administrator confirmed that a workstation was infected by malware. Which of the following processes did the administrator use to identify the root cause?
Which of the following should a company implement in order to share a single IP address among all the employees in the office?
Which of the following OSI model layers can utilize a connectionless protocol for data transmission?
A network engineer is configuring network ports in a public office. To increase security, the engineer wants the ports to allow network connections only after authentication. Which of the following security features should the engineer use?
A VoIP phone is plugged in to a port but cannot receive calls. Which of the following needs to be done on the port to address the issue?
A network engineer needs to correlate findings and receive alerts if there are brute force attacks, DDoS attacks, or port scanning happening within their network. Which of the following network monitoring technologies should the engineer implement?
Which of the following best describes a group of devices that is used to lure unsuspecting attackers and to study the attackers' activities?
Which of the following is used to stage copies of a website closer to geographically dispersed users?
Which of the following is the best way to reduce the likelihood of electrostatic discharge?
Which of the following is the most closely associated with segmenting compute resources within a single cloud account?
A customer calls the help desk to report that resources are no longer reachable. The resources were available before network changes were made. The technician verifies the report, investigates, and discovers that a new logical layout is segmenting the network using tagging. Which of the following appliances most likely needs to be reviewed to restore the connections?
A network engineer is now in charge of all SNMP management in the organization. The engineer must use a SNMP version that does not utilize plaintext data. Which of the following is the minimum version of SNMP that supports this requirement?
A network administrator is looking for a solution to extend Layer 2 capabilities and replicate backups between sites. Which of the following is the best solution?
A technician is troubleshooting a computer issue for a user who works in a new annex of an office building. The user is reporting slow speeds and intermittent connectivity. The computer is connected via a Cat 6 cable to a distribution switch that is 492ft (150m) away. Which of the following should the technician implement to correct the issue?
A network administrator upgrades the wireless access points and wants to implement a configuration that gives users higher speed and less channel overlap based on device compatibility. Which of the following accomplishes this goal?
A network engineer configures a new switch and connects it to an existing switch for expansion and redundancy. Users immediately lose connectivity to the network. The network engineer notes the following spanning tree information from both switches:
Switch 1
Port State Cost
1 Forward 2
2 Forward 2
Switch 2
Port State Cost
1 Forward 2
2 Forward 2
Which of the following best describes the issue?
A network engineer needs to add a boundary network to isolate and separate the internal network from the public-facing internet. Which of the following security defense solutions would best accomplish this task?
Which of the following is most likely responsible for the security and handling of personal data in Europe?
A network administrator wants to update a geofencing policy to limit remote access to the corporate network based on country location. Which of the following would the administrator most likely leverage?
A network administrator is configuring a network for a new site that will have 150 users. Within the next year, the site is expected to grow by ten users. Each user will have two IP addresses, one for a computer and one for a phone connected to the network. Which of the following classful IPv4 address ranges will be best-suited for the network?
A company experiences an incident involving a user who connects an unmanaged switch to the network. Which of the following technologies should the company implement to help avoid similar incidents without conducting an asset inventory?
Which of the following is the next step to take after successfully testing a root cause theory?
Which of the following attacks forces a switch to send all traffic out of all ports?
A company is concerned that the public can use network wall jacks in publicly available conference rooms to access company servers. Which of the following is the best way to mitigate the vulnerability?
Which of the following allows a user to authenticate to multiple resources without requiring additional passwords?
Which of the following cloud deployment models is most commonly associated with multitenancy and is generally offered by a service provider?
Which of the following is the most likely reason an insurance brokerage would enforce VPN usage?
A network administrator deployed wireless networking in the office area. When users visit the outdoor patio and try to download emails with large attachments or stream training videos, they notice buffering issues. Which of the following is the most likely cause?
An organization has a security requirement that all network connections can be traced back to a user. A network administrator needs to identify a solution to implement on the wireless network. Which of the following is the best solution?
Which of the following should an installer orient a port-side exhaust to when installing equipment?
Which of the following is the most cost-effective way to safely expand outlet capacity in an IDF?
Users cannot connect to an internal website with an IP address 10.249.3.76. A network administrator runs a command and receives the following output:
1 3ms 2ms 3ms 192.168.25.234
2 2ms 3ms 1ms 192.168.3.100
3 4ms 5ms 2ms 10.249.3.1
4 *
5 ’
6 *
7 •
Which of the following command-line tools is the network administrator using?
A systems administrator needs to connect two laptops to a printer via Wi-Fi. The office does not have access points and cannot purchase any. Which of the following wireless network types best fulfills this requirement?
A company upgrades its network and PCs to gigabit speeds. After the upgrade, users are not getting the expected performance. Technicians discover that the speeds of the endpoint NICs are inconsistent. Which of the following should be checked first to troubleshoot the issue?
A network technician is configuring the company’s network of 100 Mbps Layer 2 switches. The technician wants increased throughput for the uplinks between switches. The technician connects multiple redundant links between the switches. Which of the following should the technician configure?
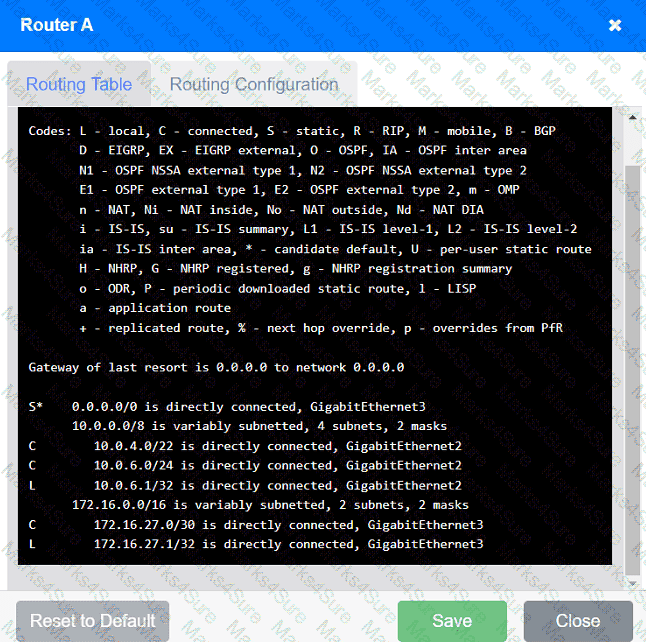
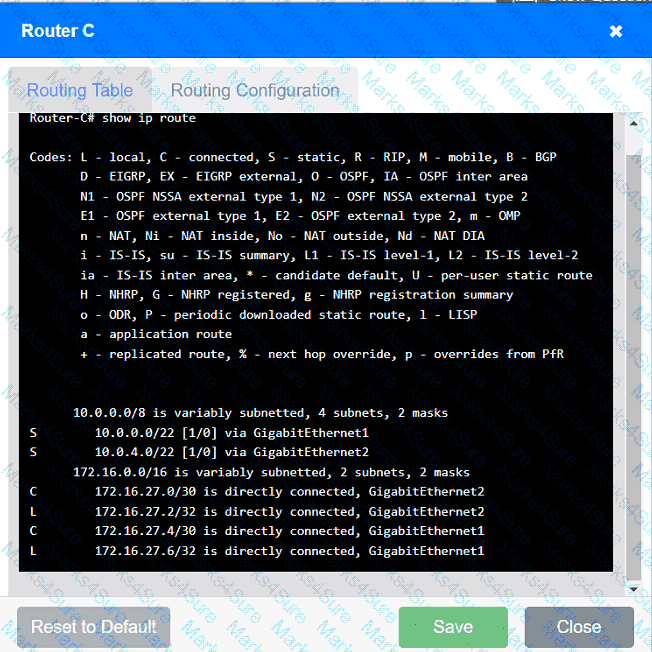
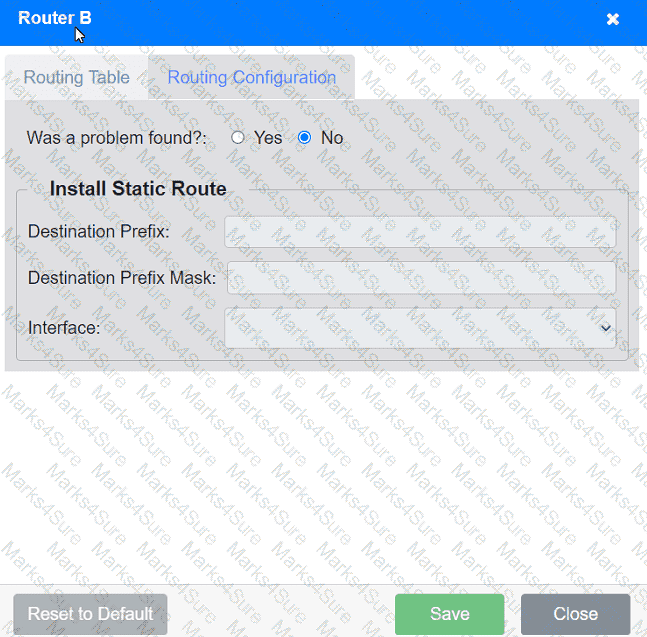
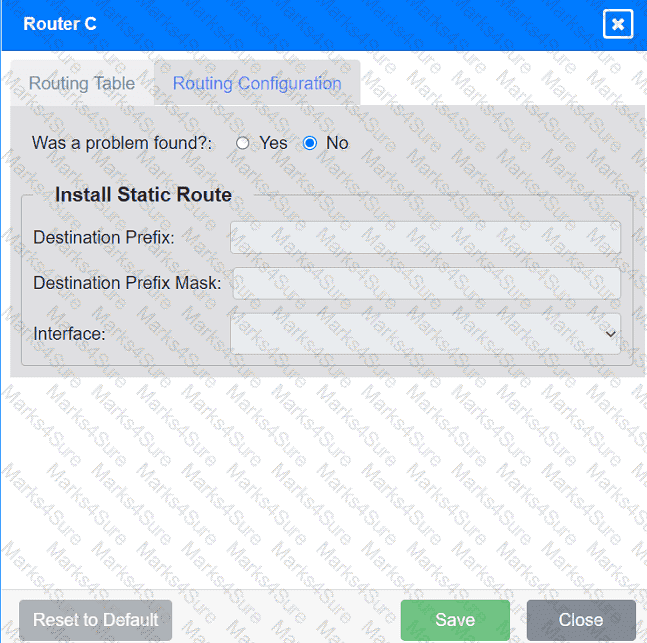
Users are unable to access files on their department share located on file server 2.
The network administrator has been tasked with validating routing between networks
hosting workstation A and file server 2.
INSTRUCTIONS
Click on each router to review output, identify any issues, and configure the appropriate solution.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
A network administrator wants to restrict inbound traffic to allow only HTTPS to the company website, denying all other inbound traffic from the internet. Which of the following would best accomplish this goal?
A user notifies a network administrator about losing access to a remote file server. The network administrator is able to ping the server and verifies the current firewall rules do not block access to the network fileshare. Which of the following tools wold help identify which ports are open on the remote file server?
A company wants to implement a disaster recovery site or non-critical applicance, which can tolerance a short period of downltime. Which of the followig type of sites should the company impelement to achive this goal?
Which of the following uses the longest prefix match to determine an exit interface?
As part of an attack, a threat actor purposefully overflows the content-addressable memory (CAM) table on a switch. Which of the following types of attacks is this scenario an example of?
A network administrator is troubleshooting issues with a DHCP server at a university. More students have recently arrived on campus, and the users are unable to obtain an IP address. Which of the following should the administrator do to address the issue?
Which of the following allows a user to connect to an isolated device on a stand-alone network?
A user is unable to navigate to a website because the provided URL is not resolving to the correct IP address. Other users are able to navigate to the intended website without issue. Which of the following is most likely causing this issue?
A Linux server is running a log collector that needs to be hardened. A network administrator executes netstat to find open ports on the server. Which of the following ports should be disabled?
Which of the following cable types allows the use of QSFP ports without requiring transceivers?
A network administrator installed a new VLAN to the network after a company added an additional floor to the office. Users are unable to obtain an IP address on the new VLAN, but ports on existing VLANs are working properly. Which of the following configurations should the administrator update?
Which of the following attacks can cause users who are attempting to access a company website to be directed to an entirely different website?
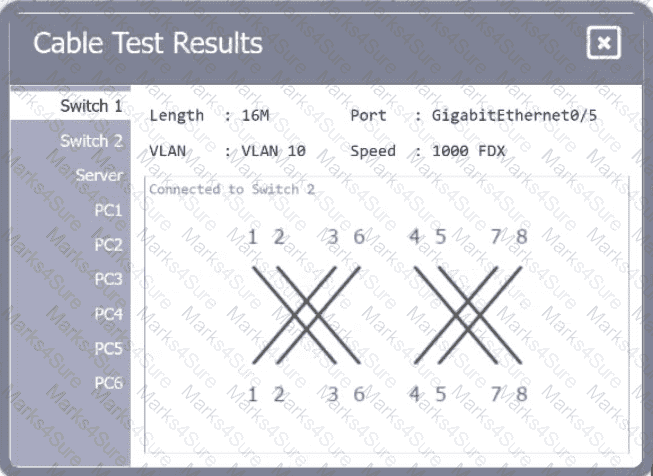
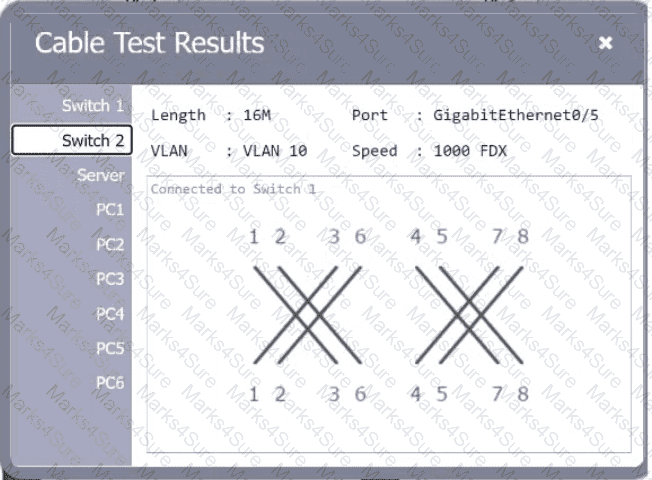
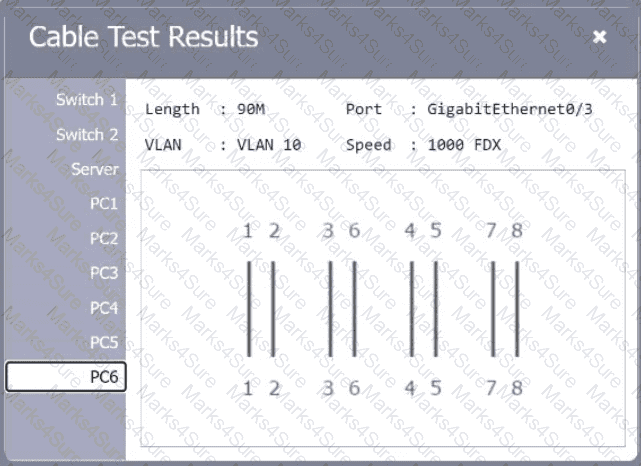
A network technician needs to resolve some issues with a customer's SOHO network. The
customer reports that some of the PCs are not connecting to the network, while others
appear to be working as intended.
INSTRUCTIONS
Troubleshoot all the network components.
Review the cable test results first, then diagnose by clicking on the appropriate PC,
server, and Layer 2 switch.
Identify any components with a problem and recommend a solution to correct each
problem.
If at any time you would like to bring back
the initial state of the simulation, please
click the Reset All button.
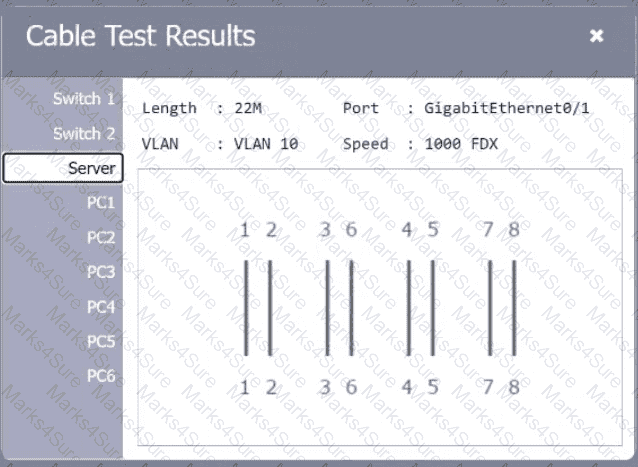
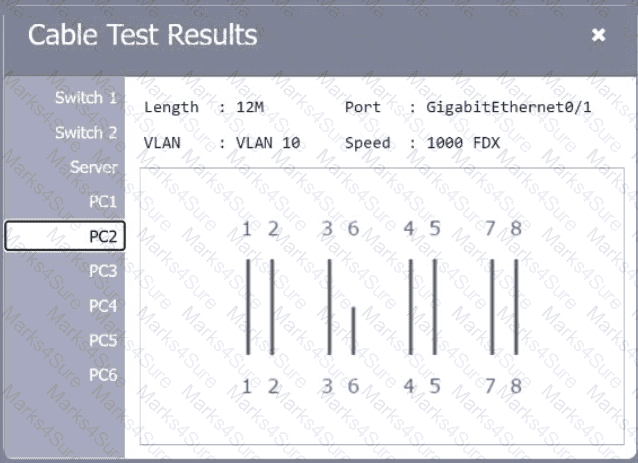
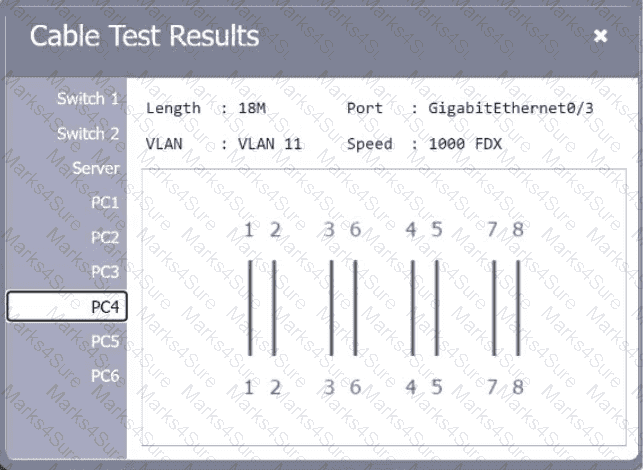
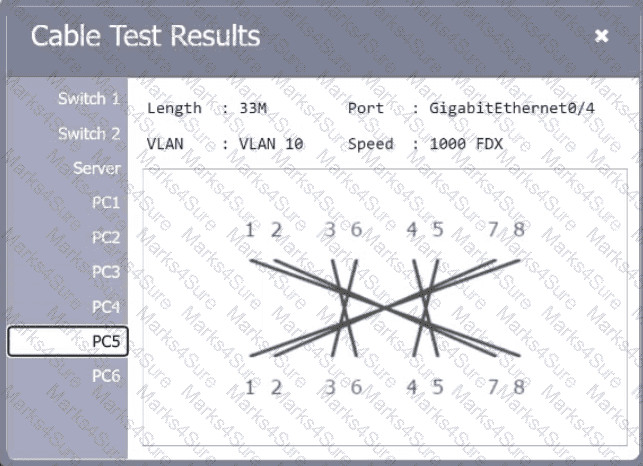
A network technician is examining the configuration on an access port and notices more than one VLAN has been set. Which of the following best describes how the port is configured?
A network engineer queries a hostname using dig, and a valid IP address is returned. However, when the engineer queries that same IP address using dig, no hostname is returned. Which of the following DNS records is missing?
After running a Cat 8 cable using passthrough plugs, an electrician notices that connected cables are experiencing a lot of cross talk. Which of the following troubleshooting steps should the electrician take first?
Which of the following protocols is used to send networking status messages between clients and servers?
Which of the following is an XML-based security concept that works by passing sensitive information about users, such as login information and attributes, to providers?
Which of the following routing technologies uses an attribute list for path selection?
A network administrator upgraded the wireless access points and wants to implement a configuration that will give users higher speed and less channel overlap based on device compatibility. Which of the following will accomplish this goal?
Voice traffic is experiencing excessive jitter. A network engineer wants to improve call performance and clarity. Which of the following features should the engineer configure?