Refer to the exhibit showing a debug flow output.
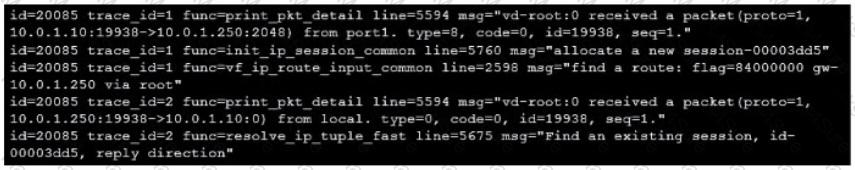
Which two statements about the debug flow output are correct? (Choose two.)
Which timeout setting can be responsible for deleting SSL VPN associated sessions?
Refer to the exhibits.
Exhibit A shows the application sensor configuration. Exhibit B shows the Excessive-Bandwidth and Apple filter details.
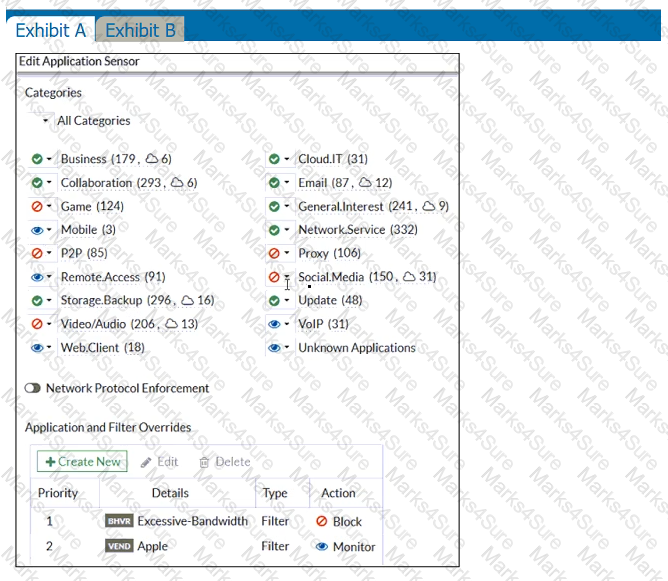
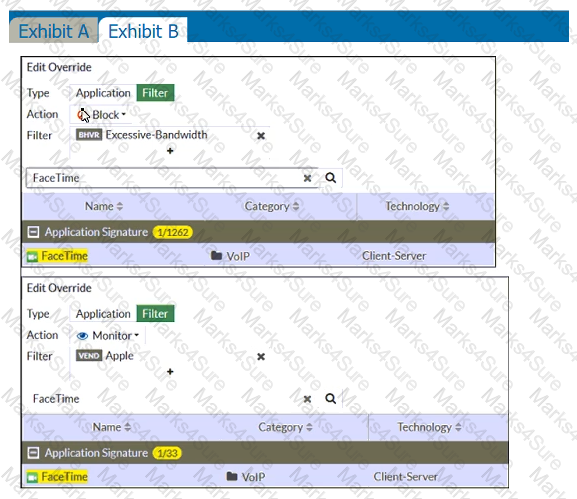
Based on the configuration, what will happen to Apple FaceTime if there are only a few calls originating or incoming?
Refer to the exhibit.
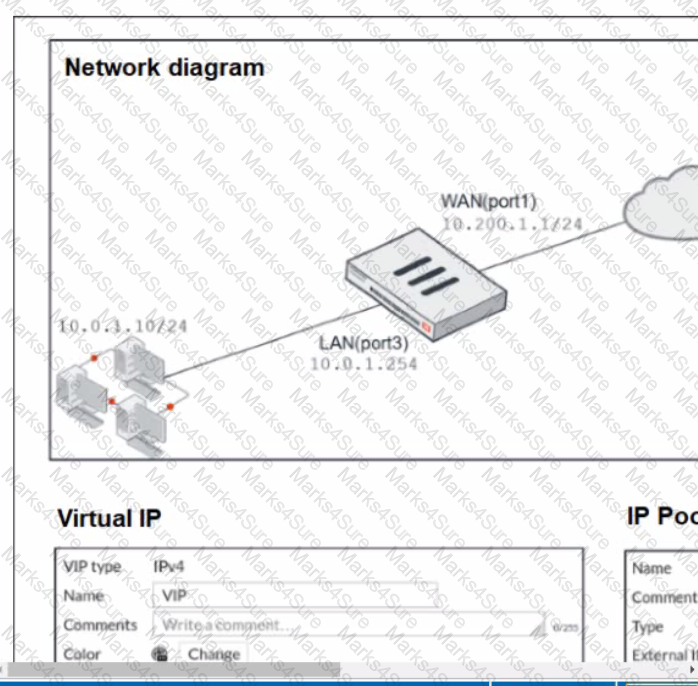
The exhibit contains a network diagram, virtual IP, IP pool, and firewall policies configuration.
The WAN (port1) interface has the IP address 10.200. 1. 1/24.
The LAN (port3) interface has the IP address 10 .0.1.254. /24.
The first firewall policy has NAT enabled using IP Pool.
The second firewall policy is configured with a VIP as the destination address.
Which IP address will be used to source NAT the internet traffic coming from a workstation with the IP address 10.0. 1. 10?
Refer to the exhibit.
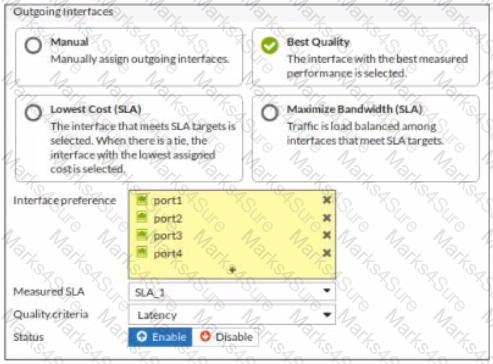
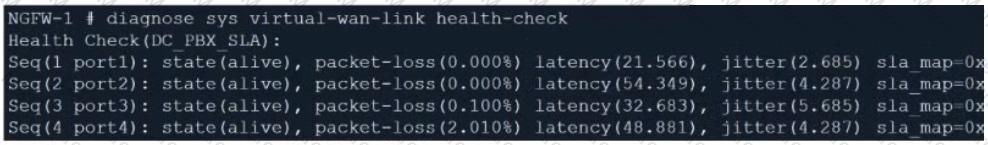
The exhibit contains the configuration for an SD-WAN Performance SLA, as well as the output of diagnose sys virtual-wan-link health-check . Which interface will be selected as an outgoing interface?
84
Which certificate value can FortiGate use to determine the relationship between the issuer and the certificate?
Refer to the exhibit.
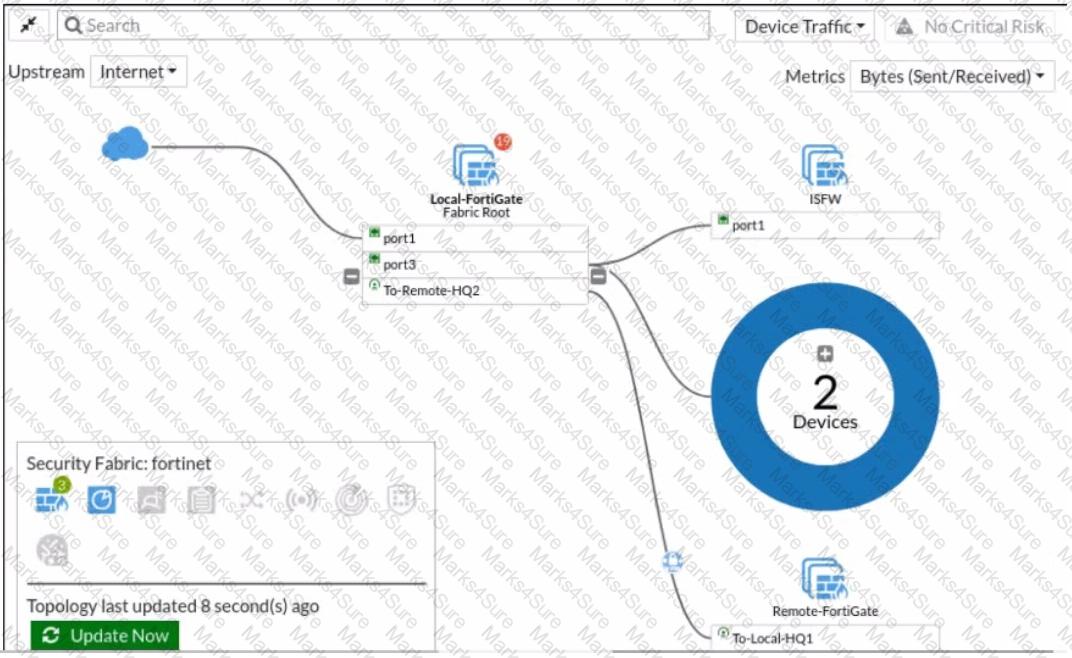
Given the security fabric topology shown in the exhibit, which two statements are true? (Choose two.)
A network administrator has enabled full SSL inspection and web filtering on FortiGate. When visiting any HTTPS websites, the browser reports certificate warning errors. When visiting HTTP websites, the browser does not report errors.
What is the reason for the certificate warning errors?
Refer to the exhibit showing a debug flow output.
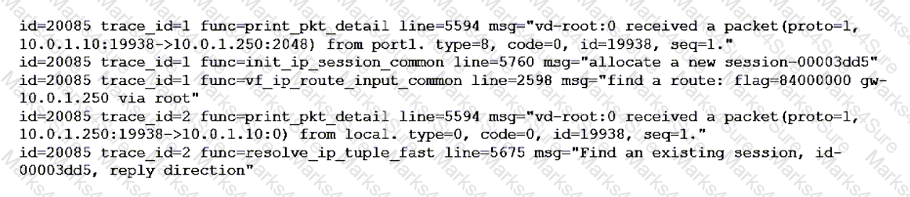
What two conclusions can you make from the debug flow output? (Choose two.)
An administrator wants to simplify remote access without asking users to provide user credentials.
Which access control method provides this solution?
Refer to the exhibit, which contains a static route configuration.
An administrator created a static route for Amazon Web Services.
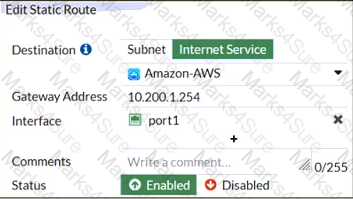
Which CLI command must the administrator use to view the route?
40
Which CLI command will display sessions both from client to the proxy and from the proxy to the servers?
An employee needs to connect to the office through a high-latency internet connection.
Which SSL VPN setting should the administrator adjust to prevent SSL VPN negotiation failure?
When a firewall policy is created, which attribute is added to the policy to support recording logs to a FortiAnalyzer or a FortiManager and improves functionality when a FortiGate is integrated with these devices?
Refer to the exhibits to view the firewall policy (Exhibit A) and the antivirus profile (Exhibit B).
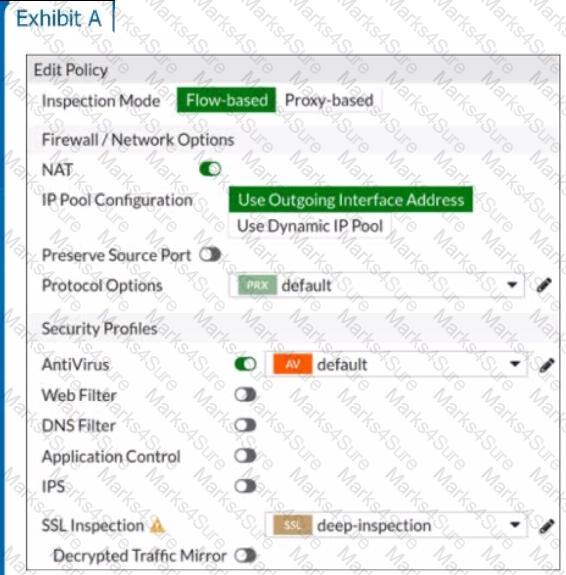
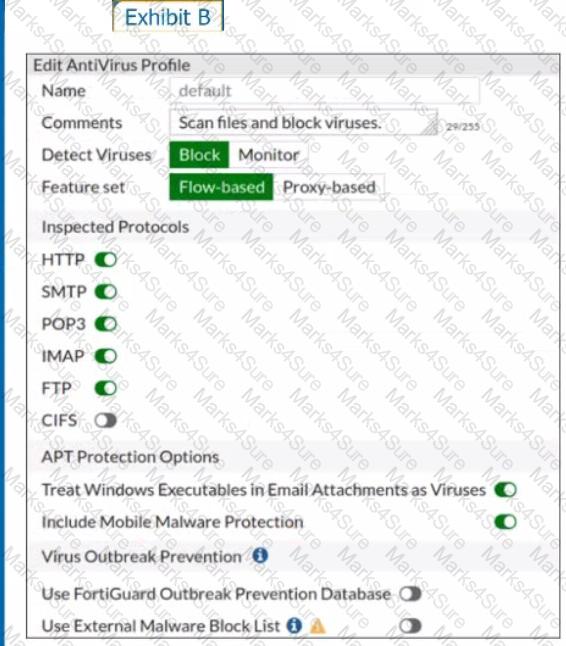
Which statement is correct if a user is unable to receive a block replacement message when downloading an infected file for the first time?
Examine the exhibit, which contains a virtual IP and firewall policy configuration.
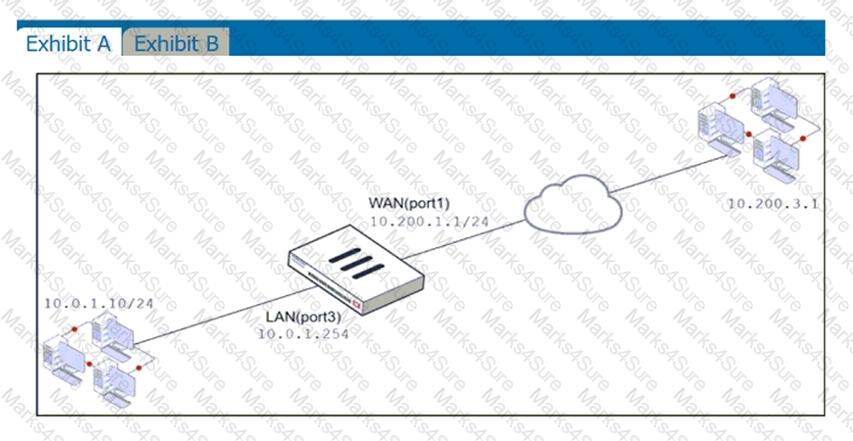
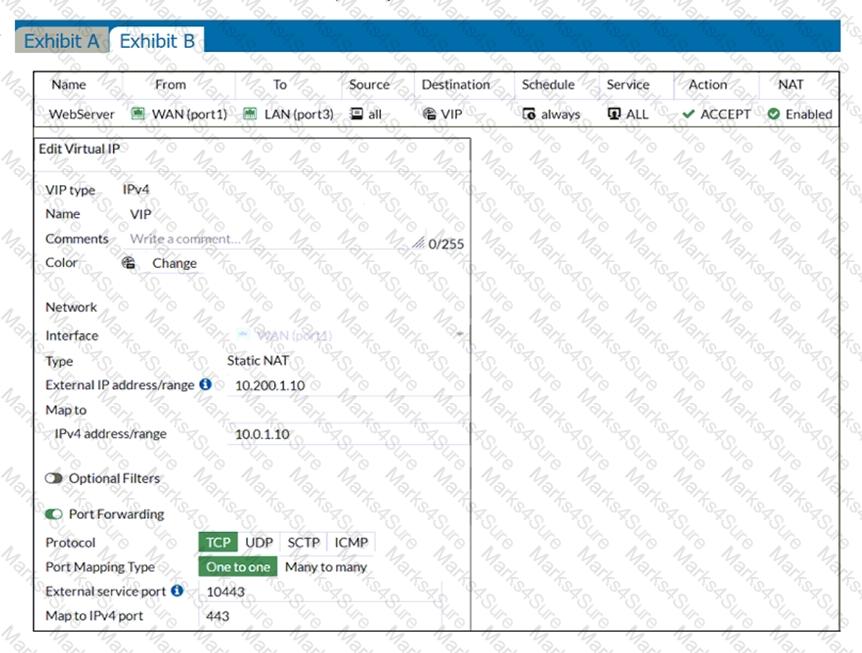
The WAN (port1) interface has the IP address 10.200. 1. 1/24. The LAN (port2) interface has the IP address 10.0. 1.254/24.
The first firewall policy has NAT enabled on the outgoing interface address. The second firewall policy is configured with a VIP as the destination address. Which IP address will be used to source NAT the Internet traffic coming from a workstation with the IP address 10.0. 1. 10/24?
Which three criteria can a FortiGate use to look for a matching firewall policy to process traffic? (Choose three.)
Refer to the exhibit.
A network administrator is troubleshooting an IPsec tunnel between two FortiGate devices. The administrator has determined that phase 1 status is up, but phase 2 fails to come up.
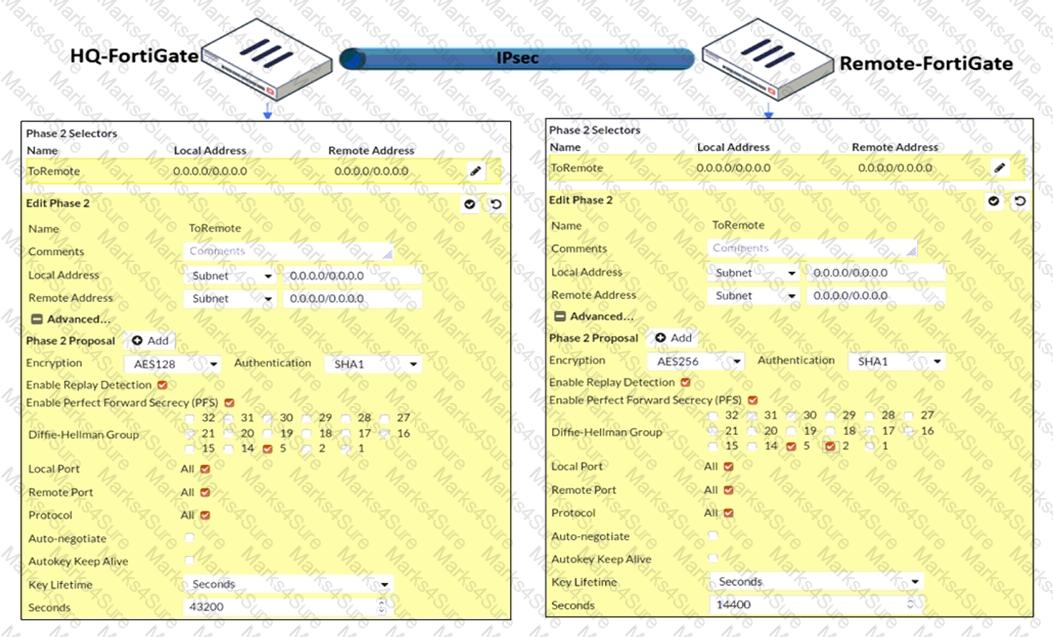
Based on the phase 2 configuration shown in the exhibit, which configuration change will bring phase 2 up?
29
Which two statements are correct about a software switch on FortiGate? (Choose two.)
56
Which two protocol options are available on the CLI but not on the GUI when configuring an SD-WAN Performance SLA? (Choose two.)
31
Which CLI command allows administrators to troubleshoot Layer 2 issues, such as an IP address conflict?
Refer to the exhibits.
Exhibit A shows a topology for a FortiGate HA cluster that performs proxy-based inspection on traffic. Exhibit B shows the HA configuration and the partial output of the get system ha status command.
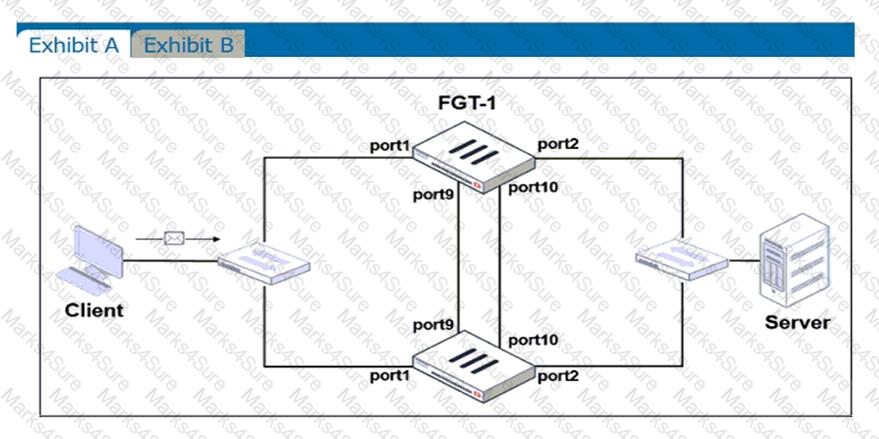
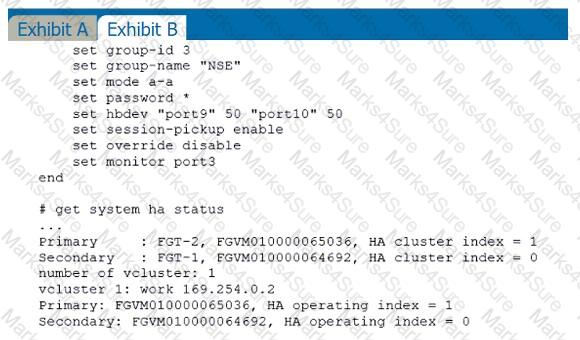
Based on the exhibits, which two statements about the traffic passing through the cluster are true? (Choose two.)
Which of the following SD-WAN load balancing method use interface weight value to distribute traffic? (Choose two.)
A network administrator wants to set up redundant IPsec VPN tunnels on FortiGate by using two IPsec VPN tunnels and static routes.
* All traffic must be routed through the primary tunnel when both tunnels are up
* The secondary tunnel must be used only if the primary tunnel goes down
* In addition, FortiGate should be able to detect a dead tunnel to speed up tunnel failover
Which two key configuration changes are needed on FortiGate to meet the design requirements? (Choose two,)
Which statement is correct regarding the use of application control for inspecting web applications?
Refer to the exhibit.
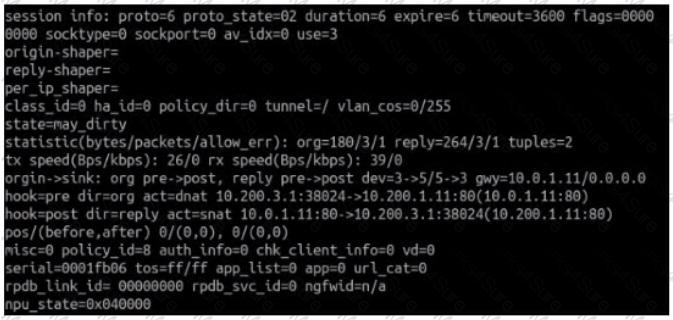
Which contains a session diagnostic output. Which statement is true about the session diagnostic output?
Refer to the exhibits.
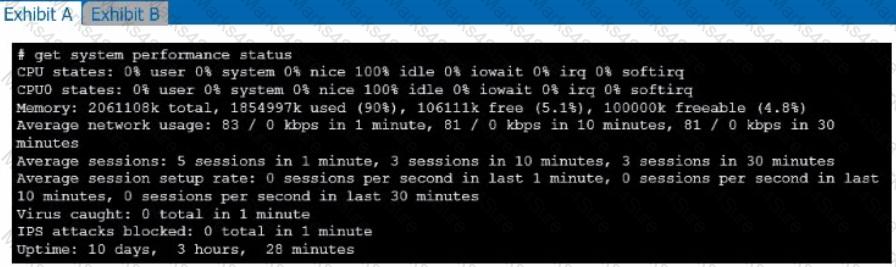
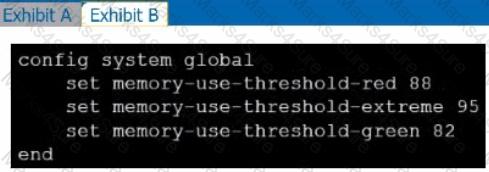
Exhibit A shows system performance output. Exhibit B shows a FortiGate configured with the default configuration of high memory usage thresholds. Based on the system performance output, which two statements are correct? (Choose two.)
An administrator has configured outgoing Interface any in a firewall policy. Which statement is true about the policy list view?
40
Which CLI command will display sessions both from client to the proxy and from the proxy to the servers?
An administrator needs to increase network bandwidth and provide redundancy.
What interface type must the administrator select to bind multiple FortiGate interfaces?
Which two types of traffic are managed only by the management VDOM? (Choose two.)
2
Which two statements are true when FortiGate is in transparent mode? (Choose two.)
85
Which statement regarding the firewall policy authentication timeout is true?
49
A network administrator is configuring a new IPsec VPN tunnel on FortiGate. The remote peer IP address is dynamic. In addition, the remote peer does not support a dynamic DNS update service.
What type of remote gateway should the administrator configure on FortiGate for the new IPsec VPN tunnel to work?
46
Which two types of traffic are managed only by the management VDOM? (Choose two.)
Refer to the exhibit.
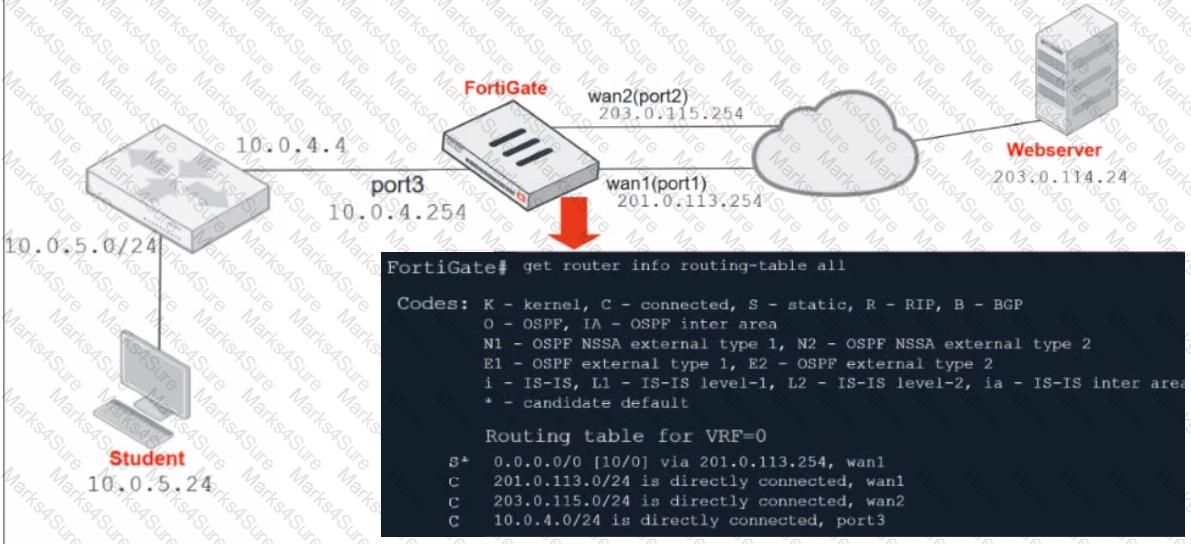
Which contains a network diagram and routing table output.
The Student is unable to access Webserver.
What is the cause of the problem and what is the solution for the problem?
Refer to the exhibit.
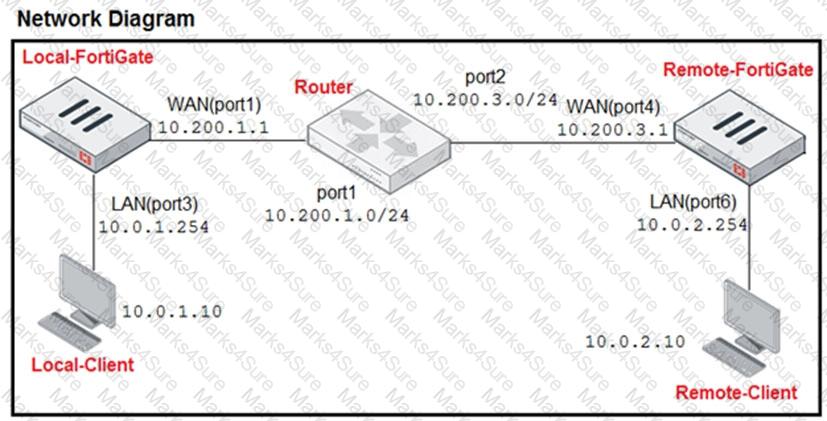
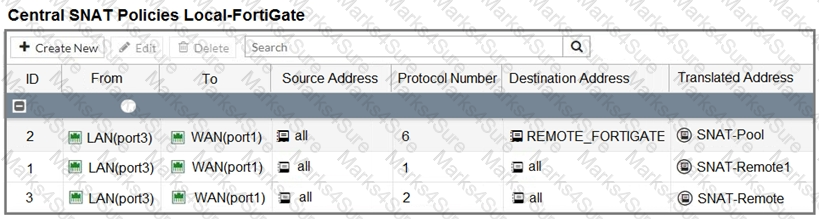
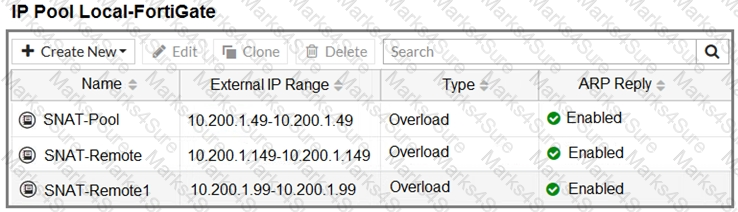
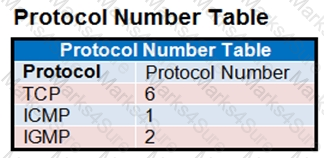
The exhibit contains a network diagram, central SNAT policy, and IP pool configuration.
The WAN (port1) interface has the IP address 10.200. 1. 1/24.
The LAN (port3) interface has the IP address 10.0. 1.254/24.
A firewall policy is configured to allow to destinations from LAN (port3) to WAN (port1).
Central NAT is enabled, so NAT settings from matching Central SNAT policies will be applied.
Which IP address will be used to source NAT the traffic, if the user on Local-Client (10.0. 1. 10) pings the IP address of Remote-FortiGate (10.200.3. 1)?
An administrator configures FortiGuard servers as DNS servers on FortiGate using default settings.
What is true about the DNS connection to a FortiGuard server?