Which two statements are correct when FortiGate enters conserve mode? (Choose two answers)
What are two characteristics of HA cluster heartbeat IP addresses in a FortiGate device? (Choose two.)
A new administrator is configuring FSSO authentication on FortiGate using DC Agent Mode. Which step is not part of the expected process?
Refer to the exhibit
A firewall policy to enable active authentication is shown.
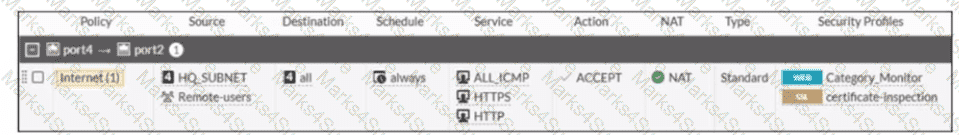
When attempting to access an external website using an active authentication method, the user is not presented with a login prompt. What is the most likely reason for this situation?
Which three statements explain a flow-based antivirus profile? (Choose three answers)
FortiGate is integrated with FortiAnalyzer and FortiManager.
When creating a firewall policy, which attribute must an administrator include to enhance functionality and enable log recording on FortiAnalyzer and FortiManager?
Which statement correctly describes NetAPI polling mode for the FSSO collector agent?
Which two components are part of the secure internet access (SIA) agent-based mode on FortiSASE? (Choose two.)
Refer to the exhibit.
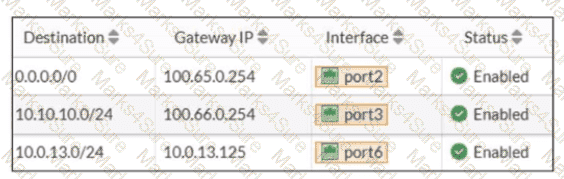
Based on the routing table shown in the exhibit, which two statements are true? (Choose two.)
Refer to the exhibit.
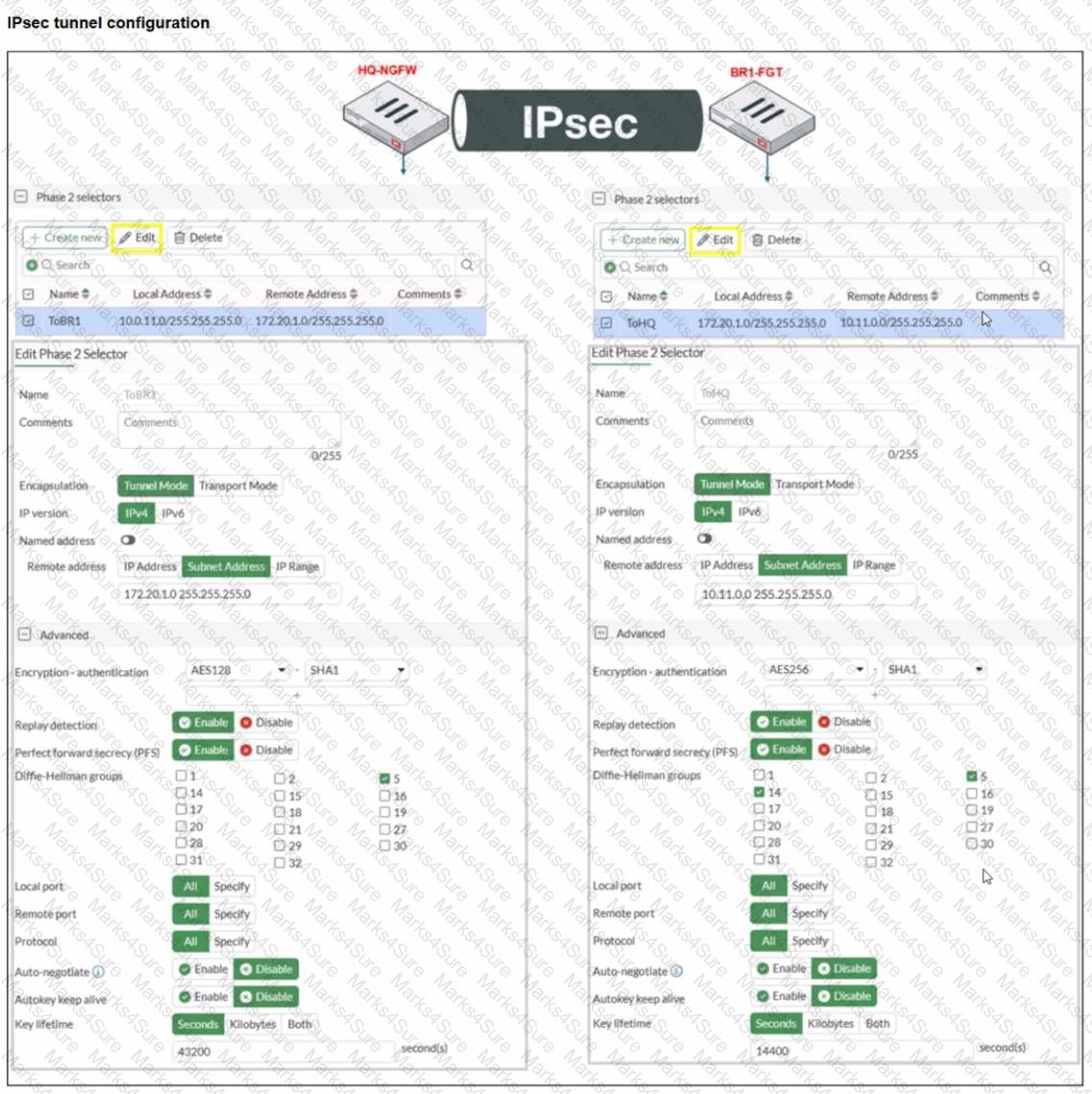
A network administrator is troubleshooting an IPsec tunnel between two FortiGate devices. The administrator has determined that phase 1 status is up, but phase 2 fails to come up.
Based on the phase 2 configuration shown in the exhibit, which two configuration changes will bring phase 2 up? (Choose two.)
Refer to the exhibit.
A RADIUS server configuration is shown.
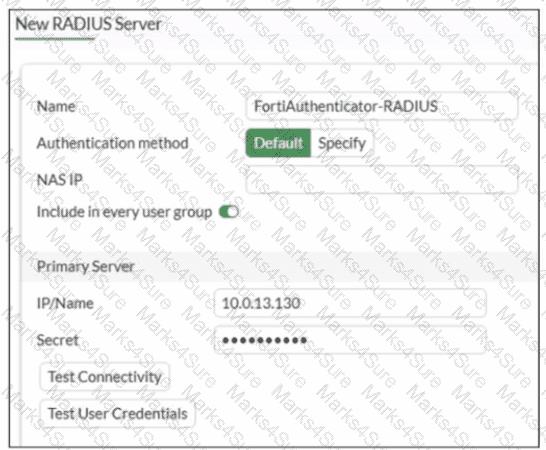
An administrator added a configuration for a new RADIUS server While configuring, the administrator enabled Include in every user group What is the impact of enabling Include in every user group in a RADIUS configuration?
An administrator wanted to configure an IPS sensor to block traffic that triggers the signature set number of times during a specific time period. How can the administrator achieve the objective?
Refer to the exhibit.

The NOC team connects to the FortiGate GUI with the NOC_Access admin profile. They request that their GUI sessions do not disconnect too early during inactivity. What must the administrator configure to answer this specific request from the NOC team?
Refer to the exhibit.
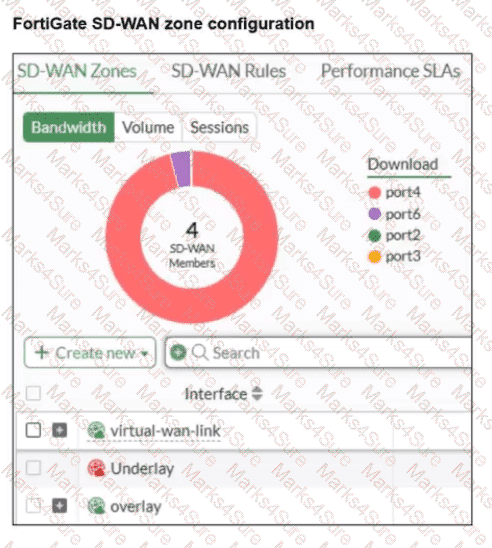
An SD-WAN zone configuration on the FortiGate GUI is shown. Based on the exhibit, which statement is true?