An administrator is configuring FortiNAC to manage FortiGate VPN users. As part of the configuration, the administrator must configure a few FortiGate firewall policies.
What is the purpose of the FortiGate firewall policy that applies to unauthorized VPN clients?
Which two of the following are required for endpoint compliance monitors? (Choose two.)
When FortiNAC passes a firewall tag to FortiGate, what determines the value that is passed?
Which system group will force at-risk hosts into the quarantine network, based on point of connection?
Refer to the exhibit.
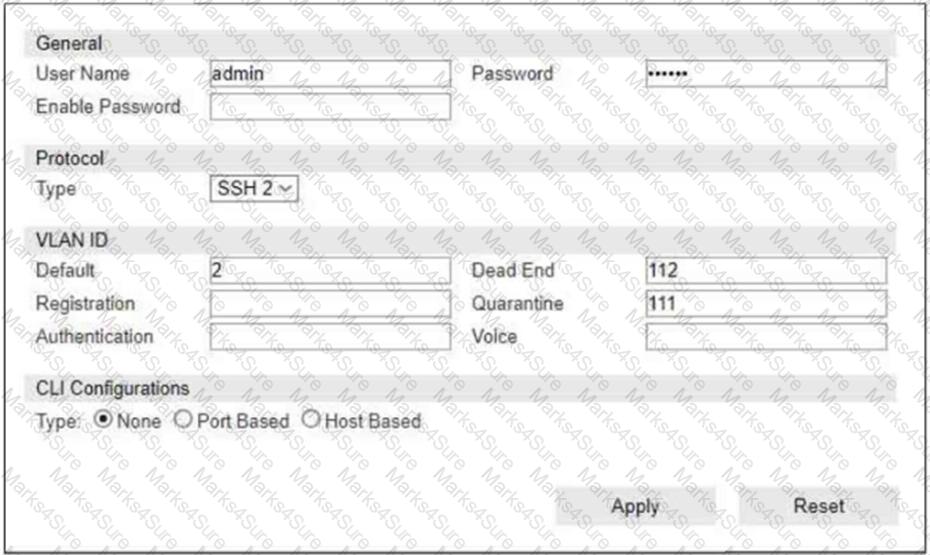
If you are forcing the registration of unknown (rogue) hosts, and an unknown (rogue) host connects to a port on the switch, what occurs?
With enforcement for network access policies and at-risk hosts enabled, what will happen if a host matches a network access policy and has a state of "at risk"?
Which two agents can validate endpoint compliance transparently to the end user? (Choose two.)