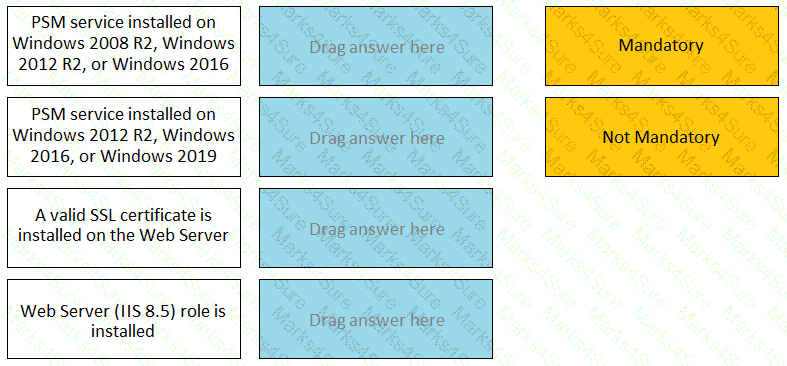
For each listed prerequisite, identify if it is mandatory or not mandatory to run the PSM Health Check.
In a default CyberArk installation, which group must a user be a member of to view the “reports” page in PVWA?
If a customer has one data center and requires high availability, how many PVWA's should be deployed.
A user requested access to view a password secured by dual-control and is unsure who to contact to expedite the approval process. The Vault Admin has been asked to look at the account and identify who can approve their request.
What is the correct location to identify users or groups who can approve?
Via Password Vault Web Access (PVWA), a user initiates a PSM connection to the target Linux machine using RemoteApp. When the client’s machine makes an RDP connection to the PSM server, which user will be utilized?
Which Cyber Are components or products can be used to discover Windows Services or Scheduled Tasks that use privileged accounts? Select all that apply.
You need to move a platform from using PMTerminal to using Terminal Plugin Controller (TPC) What must you do?
You are installing HTML5 gateway on a Linux host using the RPM provided. After installing the Tomcat webapp, what is the next step in the installation process?
It is possible to restrict the time of day, or day of week that a [b]reconcile[/b] process can occur
Which of the following are secure options for storing the contents of the Operator CD, while still allowing the contents to be accessible upon a planned Vault restart? (Choose three.)
Which component must be installed on the Vault if Distributed Vaults is used with PSM?
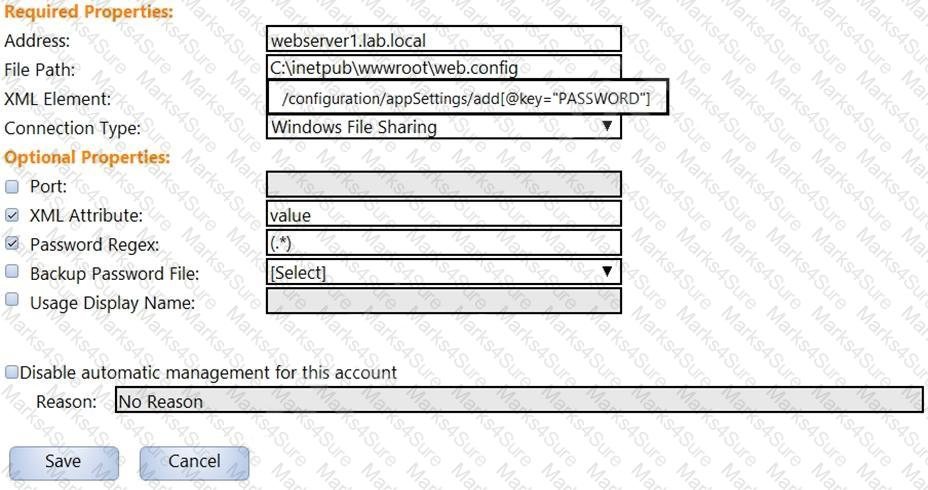
In the screenshot displayed, you just configured the usage in CyberArk and want to update its password.
What is the least intrusive way to accomplish this?
Which components can connect to a satellite Vault in distributed Vault architecture?
When Dual Control is enabled a user must first submit a request in the Password Vault Web Access (PVWA) and receive approval before being able to launch a secure connection via PSM for Windows (previously known as RDP Proxy).
You have been asked to identify the up or down status of Vault services.
Which CyberArk utility can you use to accomplish this task?
In a rule using “Privileged Session Analysis and Response” in PTA, which session options are available to configure as responses to activities?
You are creating a new Rest API user that utilizes CyberArk Authentication.
What is a correct process to provision this user?
When running a “Privileged Accounts Inventory” Report through the Reports page in PVWA on a specific safe, which permission/s are required on that safe to show complete account inventory information?
Which of the following properties are mandatory when adding accounts from a file? (Choose three.)
As vault Admin you have been asked to configure LDAP authentication for your organization's CyberArk users. Which permissions do you need to complete this task?
Which configuration file and Vault utility are used to migrate the server key to an HSM?
Users can be resulted to using certain CyberArk interfaces (e.g.PVWA or PACLI).
You are onboarding an account that is not supported out of the box.
What should you do first to obtain a platform to import?
What is the configuration file used by the CPM scanner when scanning UNIX/Linux devices?
Which of the following files must be created or configured m order to run Password Upload Utility? Select all that apply.
Arrange the steps to restore a Vault using PARestore for a Backup in the correct sequence.

Which Master Policy Setting must be active in order to have an account checked-out by one user for a pre-determined amount of time?
When a group is granted the 'Authorize Account Requests' permission on a safe Dual Control requests must be approved by
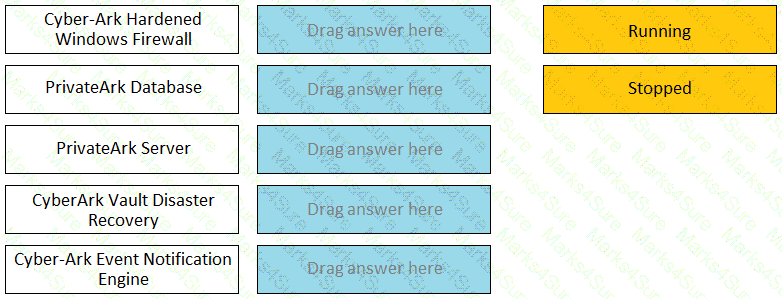
Match the Status of Service on a DR Vault to what is displayed when it is operating normally in Replication mode.
What is a prerequisite step betore CyberArk can be configured to support RADIUS authentication?
You have been asked to configure SNMP remote monitoring for your organization's Vault servers. In the PARAgent.ini, which parameter specifies the destination of the Vault SNMP Traps?
If a user is a member of more than one group that has authorizations on a safe, by default that user is granted________.
Customers who have the ‘Access Safe without confirmation’ safe permission on a safe where accounts are configured for Dual control, still need to request approval to use the account.
You are configuring the vault to send syslog audit data to your organization's SIEM solution. What is a valid value for the SyslogServerProtocol parameter in DBPARM.ini file?
PTA can automatically suspend sessions if suspicious activities are detected in a privileged session, but only if the session is made via the CyberArk PSM.
An auditor needs to login to the PSM in order to live monitor an active session. Which user ID is used to establish the RDP connection to the PSM server?
A customer's environment three data centers, consisting of 5,000 servers in Germany, 10,000 servers in Canada, 1,500 servers in Singapore. You want to manage target servers and avoid complex firewall rules. How many CPM's should you deploy?