A company deploys 10 public APIs to CloudHub. Each API has its individual health endpoint defined. The platform operation team wants to configure API Functional Monitoring to monitor the health of the APIs periodically while minimizing operational overhead and cost.
How should API Functional Monitoring be configured?
Refer to the exhibit.
What action must be performed to log all the errors raised by the VM Connector?
Which type of cache invalidation does the Cache scope support without having to write any additional code?
Refer to the exhibit.
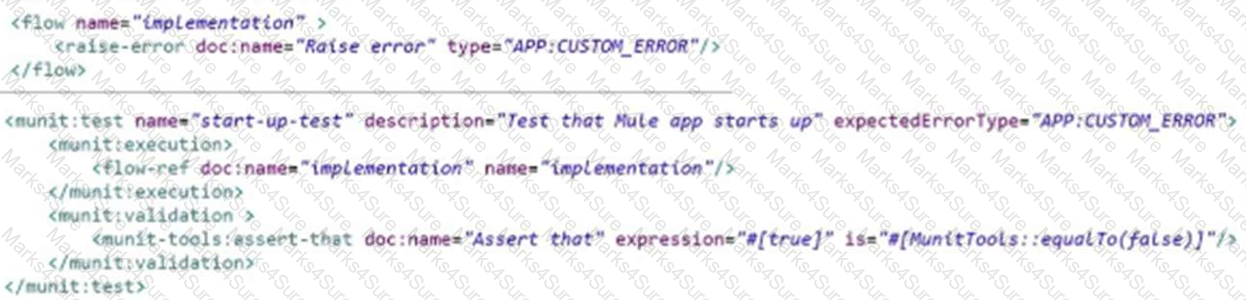
The flow name is ‘’implementation’’ with code for the MUnit test case.
When the MUnit test case is executed,what is the expected result?
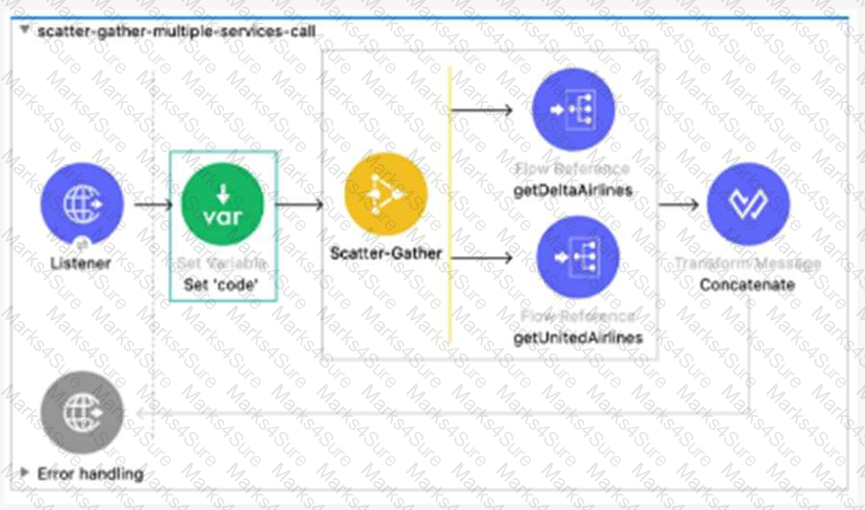
Refer to the exhibit.
What required changes can be made to give a partial successful response in case the United Airlines API returns with a timeout?
Two APIs are deployed to a two-node on-prem cluster. Due to a requirements change, the two APIs must communicate to exchange data asynchronously.
When a client and server are exchanging messages during the mTLS handshake, what is being agreed on during the cipher suite exchange?
The flow is invoicing a target API. The API’s protocol is HTTPS. TheTLS configuration in the HTTP Request Configuration global element is set to None. A web client submits a request to http:localhost:8081/vehicles.
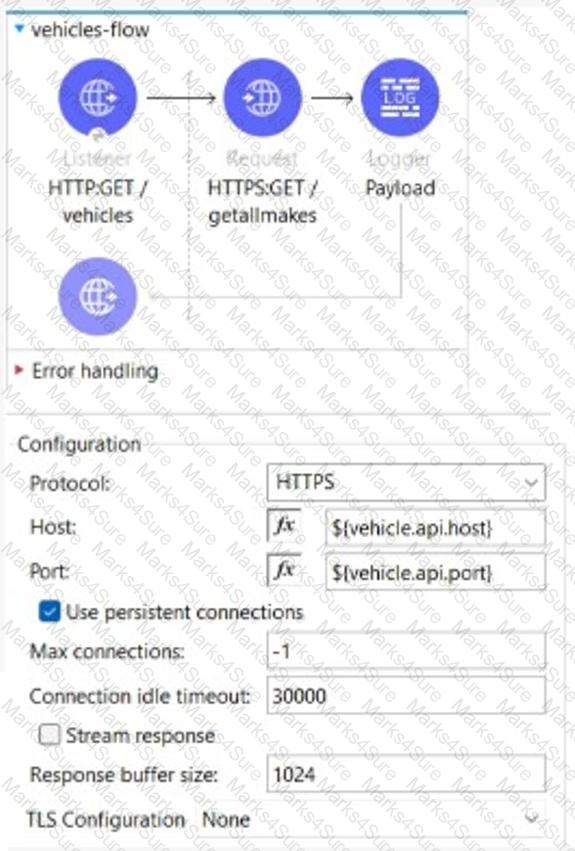
If the certificate of the target API is signed by a certificate authority (CA), what is true about the HTTP Request operation when the flow executes?
A Mule application for processing orders must log the order ID for every log message output.
What is a best practice to enrich every log message with the order ID?
A Mule API receives a JSON payload and updates the target systemwith the payload. The developer uses JSON schemas to ensure the data is valid.
How can the data be validation before posting to the target system?
A company has been using CI/CD. Its developers use Maven to handle build and deployment activities.
What is the correct sequence of activities that takes place during the Maven build and deployment?
Mule application A is deployed to CloudHub and is using Object Store v2. Mute application B is also deployed to CloudHub.
Which approach can Mule application B use to remove values from Mule application A’S Object Store?
A scatter-gather router isconfigured with four routes:Route A, B, C and D.
Route C false.