You are configuring a data loss prevention (DLP) policy to report when credit card data is found on a Microsoft Entra joined Windows device.
You plan to use information from the policy to restrict the ability to copy the sensitive data to the clipboard.
What should you configure in the policy advanced DLP rule?
You have a Microsoft 365 E5 subscription that uses Microsoft Purview.
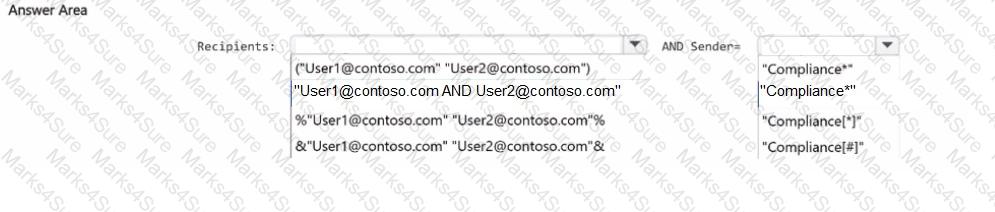
You need to perform a content search for email messages that meet the following requirements:
• Are delivered to both user1@contoso.com and user2@contoso.com
• Are sent from a user account that has a name that starts with the word Compliance
How should you complete the query in the KQL editor? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You need to create a retention policy to delete content after seven years from the following locations:
• Exchange Online email
• SharePoint Online sites
• OneDrive accounts
• Microsoft 365 Groups
• Teams channel messages
• Teams chats
What is the minimum number of retention policies that you should create?
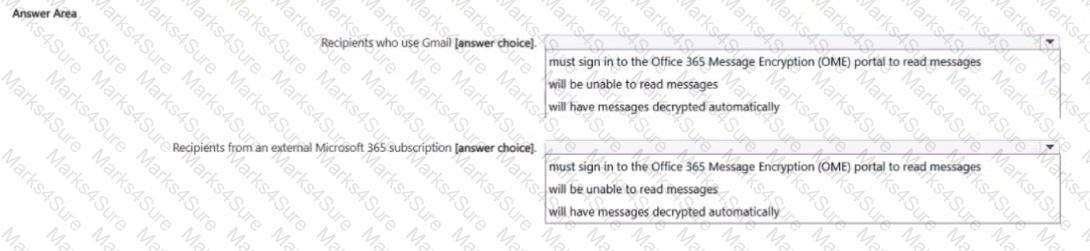
You are implementing Microsoft Purview Advanced Message Encryption for a Microsoft 365 tenant named contoso.com You need to meet the following requirements:
• All email to a domain named (abrikam.com must be encrypted automatically.
• Encrypted emails must expire seven days after they are sent
What should you configure for each requirement? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

You have a Microsoft 365 subscription.
You identify the following data loss prevention (DLP) requirements:
• Send notifications to users if they attempt to send attachments that contain an EU Social Security Number (SSN) or Equivalent ID.
• Prevent any email messages that contain credit card numbers from being sent outside your organization.
• Block the external sharing of Microsoft OneDrive content that contains EU passport numbers.
• Send administrators email alerts if any rule matches occur.
What is the minimum number of DLP policies and rules you must create to meet the requirements? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

You are creating a DLP policy named Policy1 that will be applied to the locations as shown in the following exhibit.

Policy1 contains an advanced data loss prevention (DLP) rule named Rule1.
Which two conditions can you use in Rule1? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point.
You have a Microsoft 365 E5 subscription.
Users access their mailbox by using the following apps.
• Outlook for Microsoft 365
• Outlook on the web
• Outlook Mobile fiOS. Android)
You create a data loss prevention (DLP) policy named DLP1 that has the following settings:
• Location; Exchange email
• Status: On
• User notifications: On
• Notify users with a policy tip: Enabled
Which apps display a policy tip when content is matched by using DIP1 ?
You have a Microsoft 365 E5 subscription that uses Microsoft Defender for Cloud Apps.
You need to ensure that you receive an alert when a user uploads a document to a third-party cloud storage service.
What should you use?
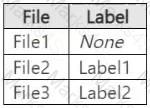
You have a Microsoft 365 E5 subscription that contains three DOCX files named File1, File2, and File3.
You create the sensitivity labels shown in the following table.

You apply the labels to the files as shown in the following table.
You ask Microsoft 365 Copilot to summarize the files, and you receive the results shown in the following table.
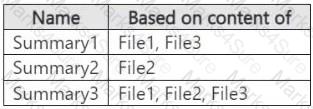
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.

You have a Microsoft 36S subscription.
In Microsoft Exchange Online, you configure the mail flow rule shown in the following exhibit.

Use the drop-down menus to select the answer choice that completes each statement based on the information presented in the graphic.
NOTE: Each correct selection is worth one point.
You have a Microsoft 365 subscription. You create a retention policy and apply the policy to Exchange Online mailboxes.
You need to ensure that the retention policy tags can be assigned to mailbox items as soon as possible.
What should you do?
You have a Microsoft SharePoint Online site named Site! that contains the files shown in the following table.

You have a data loss prevention (DLP) policy named DLP1 that has the advanced DLP rules shown in the following table.
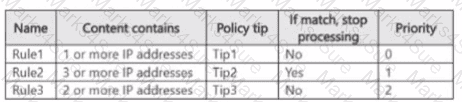
You apply DLP1 toSite1.
Which policy tips will appear for File2?
At the end of a project, you upload project documents to a Microsoft SharePoint Online library that contains many files. The following is a sample of the project document file names:
• aei_AA989.docx
• bd_WS098.docx
• cei_DF112.docx
• ebc_QQ454.docx
• ecc_BB565.docx
All documents that use this naming format must be labeled as Project Documents:
You need to create an auto-apply retention label policy.
What should you use to identify the files?
You have a Microsoft J65 E5 subscription. You plan to implement retention policies for Microsoft Teams. Which item types can be retained?
You have a Microsoft 365 E5 subscription that contains a device named Device1.
You need to enable Endpoint data loss prevention (Endpoint DLP) for Device1.
What should you do first in the Microsoft Purview portal?
You need to test Microsoft Purview Advanced Message Encryption capabilities for your company. The test must verify the following information:
• The acquired default template names
• The encryption and decryption verification status
Which PowerShell cmdlet should you run?
You have a Microsoft 365 E5 tenant.
You need to add a new keyword dictionary.
What should you create?
You have a Microsoft SharePoint Online site named Site1 that contains a document library. The library contains more than 1,000 documents. Some of the documents are job applicant resumes. All the documents are in the English language.
You plan to apply a sensitivity label automatically to any document identified as a resume. Only documents that contain work experience, education, and accomplishments must be labeled automatically.
You need to identify and categorize the resumes. The solution must minimize administrative effort.
What should you include in the solution?
You need to meet the retention requirement for the users' Microsoft 365 data.
What is the minimum number of retention policies required to achieve the goal?
HOTSPOT
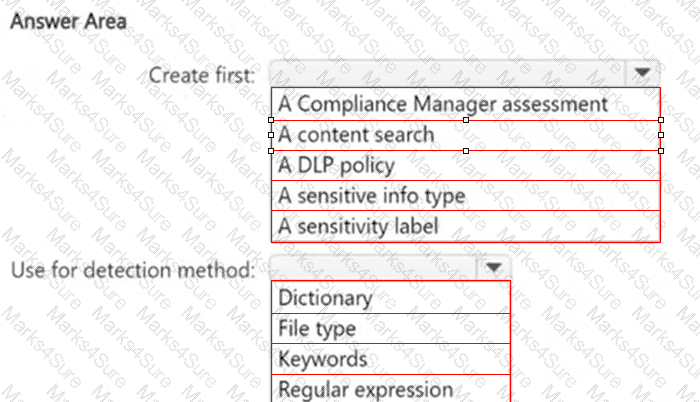
You need to meet the technical requirements for the confidential documents.
What should you create first, and what should you use for the detection method? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
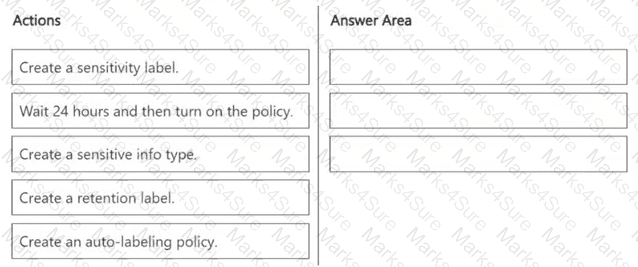
You need to meet the technical requirements for the Site1 documents.
Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.
HOTSPOT
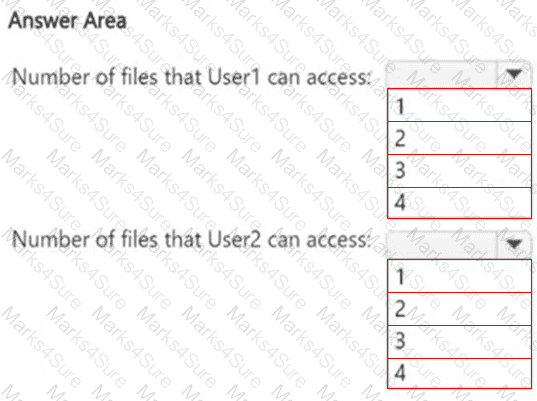
How many files in Site2 can User1 and User2 access after you turn on DLPpolicy1? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You need to meet the technical requirements for the creation of the sensitivity labels.
To which user or users must you assign the Sensitivity Label Administrator role?
HOTSPOT
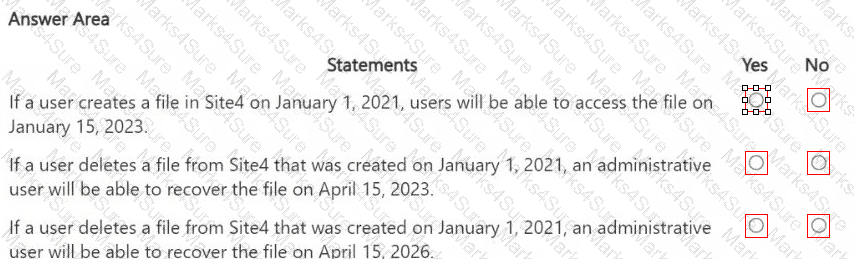
You are reviewing policies for the SharePoint Online environment.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.