Which three statements accurately describe the guiding principles of Zero Trust? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point.
What can you use to provision Azure resources across multiple subscriptions in a consistent manner?
Which three authentication methods does Windows Hello for Business support? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.

For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.
What should you create to search and export content preserved in an eDiscovery hold?
To which three locations can a data loss prevention (DLP) policy be applied? Each correct answer presents a complete solution.
NOTE: Each correct answer is worth one point.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Which Microsoft 365 compliance feature can you use to encrypt content automatically based on specific conditions?
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.

For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.

Which two types of devices can be managed by using Endpoint data loss prevention (Endpoint DLP)? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point.
Which security feature is available in the free mode of Microsoft Defender for Cloud?
For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.

What can you use to deploy Azure resources across multiple subscriptions in a consistent manner?
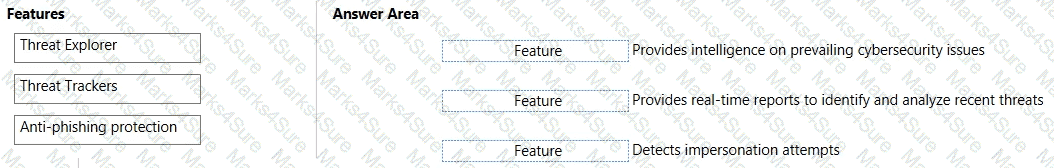
Match the Microsoft Defender for Office 365 feature to the correct description.
To answer, drag the appropriate feature from the column on the left to its description on the right. Each feature may be used once, more than once, or not at all.
NOTE: Each correct match is worth one point.
Which Microsoft 365 feature can you use to restrict communication and the sharing of information between members of two departments at your organization?
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.

For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.

For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.

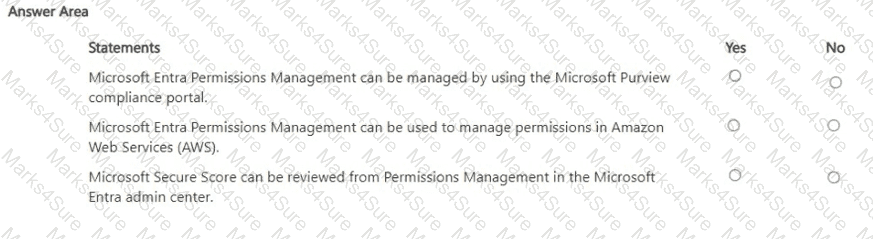
Which Azure Active Directory (Azure AD) feature can you use to evaluate group membership and automatically remove users that no longer require membership in a group?
Which Microsoft Defender for Cloud metric displays the overall security health of an Azure subscription?
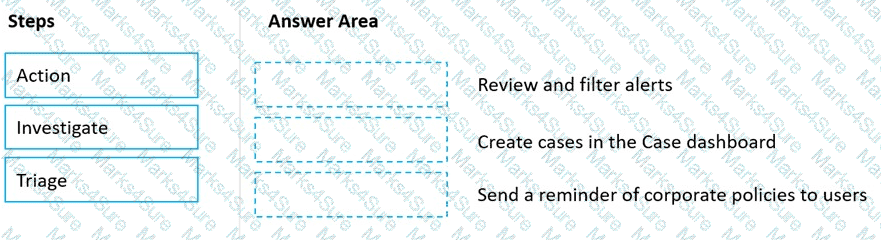
Match the Microsoft 365 insider risk management workflow step to the appropriate task.
To answer, drag the appropriate step from the column on the left to its task on the right. Each step may be used once, more than once, or not at all.
NOTE: Each correct match is worth one point.
Which solution performs security assessments and automatically generates alerts when a vulnerability is found?
You have an Azure subscription.
You need to implement approval-based, tiProme-bound role activation.
What should you use?
What Microsoft Purview feature can use machine learning algorithms to detect and automatically protect sensitive items?
What can you use to scan email attachments and forward the attachments to recipients only if the attachments are free from malware?
Which three authentication methods can be used by Azure Multi-Factor Authentication (MFA)? Each correct answer presents a complete solution. NOTE: Each correct selection is worth one point.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point
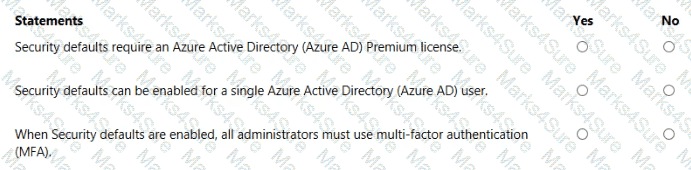
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.

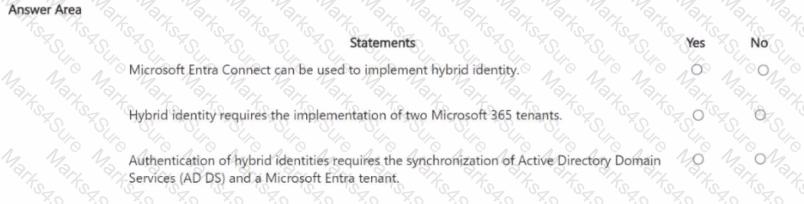
In a hybrid identity model, what can you use to sync identities between Active Directory Domain Services (AD DS) and Azure Active Directory (Azure AD)?
Match the types of Conditional Access signals to the appropriate definitions.
To answer, drag the appropriate Conditional Access signal type from the column on the left to its definition on the right. Each signal type may be used once, more than once, or not at all.
NOTE: Each correct match is worth one point.

What is a use case for implementing information barrier policies in Microsoft 365?
You are evaluating the compliance score in Microsoft Purview Compliance Manager.
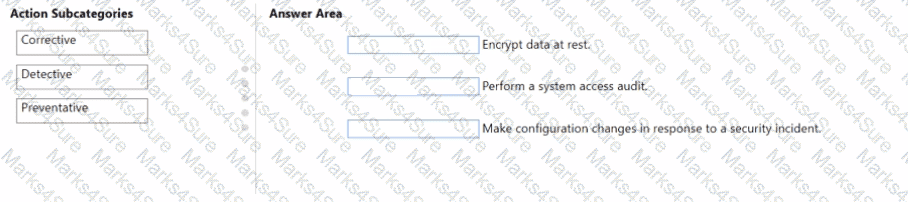
Match the compliance score action subcategories to the appropriate actions.
To answer, drag the appropriate action subcategory from the column on the left to its action on the right. Each action subcategory may be used once, more than once, or not at all.
NOTE: Each correct match is worth one point.
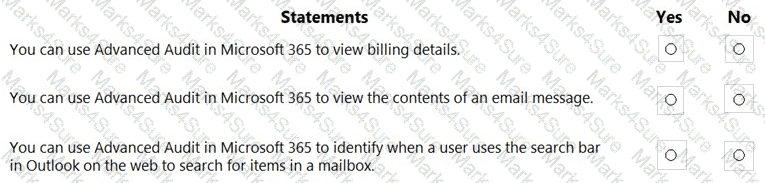
Which Microsoft 365 compliance center feature can you use to identify all the documents on a Microsoft SharePoint Online site that contain a specific key word?
Which Microsoft Purview data classification type supports the use of regular expressions?