Which type of security analysis is performed by injecting malformed data into open interfaces of an executable or running application and is most commonly executed during the testing or deployment phases of the SDLC?
Which security assessment deliverable identities unmanaged code that must be kept up to date throughout the life of the product?
Which secure software design principle assumes attackers have the source code and specifications of the product?
Which mitigation technique can be used to fight against a denial of service threat?
Which type of security analysis is limited by the fact that a significant time investment of a highly skilled team member is required?
Credit card numbers are encrypted when stored in the database but are automatically decrypted when data is fetched. The testing tool intercepted the GET response, and testers were able to view credit card numbers as clear text.
How should the organization remediate this vulnerability?
Which secure coding best practice says to use a single application-level authorization component that will lock down the application if it cannot access its configuration information?
A recent security review has identified an aging credential recovery/forgotten password component that emails temporary passwords to users who claim to have forgotten their application password.
How should the organization remediate this vulnerability?
Which secure coding best practice says to use well-vetted algorithms to ensure that the application uses random identifiers, that identifiers are appropriately restricted to the application, and that user processes are fully terminated on logout?
An individual is developing a software application that has a back-end database and is concerned that a malicious user may run the following SOL query to pull information about all accounts from the database:
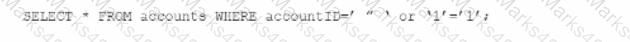
Which technique should be used to detect this vulnerability without running the source codes?
Which secure coding best practice says to require authentication before allowing any files to be uploaded and to limit the types of files to only those needed for the business purpose?
In which step of the PASTA threat modeling methodology will the team capture infrastructure, application, and software dependencies?
The software security group is conducting a maturity assessment using the Building Security in Maturity Model (BSIMM). They are currently focused on reviewing attack models created during recently completed initiatives.
Which BSIMM domain is being assessed?
The security team has a library of recorded presentations that are required viewing tor all new developers in the organization. The video series details organizational security policies and demonstrates how to define, test for. and code tor possible threats.
Which category of secure software best practices does this represent?
Which software control test examines the internal logical structures of a program and steps through the code line by line to analyze the program for potential errors?
Which secure coding practice involves clearing all local storage as soon as a user logs of for the night and will automatically log a user out after an hour of inactivity?
Which threat modeling methodology involves creating or using collections of similar threats?
Which software control test examines an application from a user perspective by providing a wide variety of input scenarios and inspecting the output?
Which type of manual code review technique is being used when the reviewer starts at an input control and traces its value through the application to each of the value's outputs?
Features have been developed and fully tested, the production environment has been created, and leadership has approved the release of the new product. Technicians have scheduled a time and date to make the product available to customers.
Which phase of the software development lifecycle (SDLC) is being described?
Which question reflects the security change management component of the change management process?
Which category classifies identified threats that have some defenses in place and expose the application to limited exploits?
In which step of the PASTA threat modeling methodology is vulnerability and exploit analysis performed?
The security team is reviewing whether changes or open issues exist that would affect requirements for handling personal information documented in earlier phases of the development life cycle.
Which activity of the Ship SDL phase is being performed?
Which secure coding best practice ensures sensitive information is not disclosed in any responses to users, authorized or unauthorized?
Which secure software design principle states that it is always safer to require agreement of more than one entity to make a decision?
The security team has received notice of an insecure direct object reference vulnerability in a third-party component library that could result in remote code execution. The component library was replaced and is no longer being used within the application.
How should the organization remediate this vulnerability?
Company leadership has discovered an untapped revenue stream within its customer base and wants to meet with IT to share its vision for the future and determine whether to move forward.
Which phase of the software development lifecycle (SDLC) is being described?
Using a web-based common vulnerability scoring system (CVSS) calculator, a security response team member performed an assessment on a reported vulnerability in the company's claims intake component. The base score of the vulnerability was 3.5 and changed to 5.9 after adjusting temporal and environmental metrics.
Which rating would CVSS assign this vulnerability?