A healthcare organization wants to provide a web application that allows individuals to digitally report health emergencies.
Which of the following is the most important consideration during development?
During a penetration test in a hypervisor, the security engineer is able to inject a malicious payload and access the host filesystem. Which of the following best describes this vulnerability?
A security analyst discovers that a large number of employee credentials had been stolen and were being sold on the dark web. The analyst investigates and discovers that some hourly employee credentials were compromised, but salaried employee credentials were not affected.
Most employees clocked in and out while they were Inside the building using one of the kiosks connected to the network. However, some clocked out and recorded their time after leaving to go home. Only those who clocked in and out while Inside the building had credentials stolen. Each of the kiosks are on different floors, and there are multiple routers, since the business segments environments for certain business functions.
Hourly employees are required to use a website called acmetimekeeping.com to clock in and out. This website is accessible from the internet. Which of the following Is the most likely reason for this compromise?
After an audit, an administrator discovers all users have access to confidential data on a file server. Which of the following should the administrator use to restrict access to the data quickly?
Which of the following control types involves restricting IP connectivity to a router's web management interface to protect it from being exploited by a vulnerability?
Which of the following types of identification methods can be performed on a deployed application during runtime?
A vendor needs to remotely and securely transfer files from one server to another using the command line. Which of the following protocols should be Implemented to allow for this type of access? (Select two).
Which of the following would be best suited for constantly changing environments?
A penetration test identifies that an SMBvl Is enabled on multiple servers across an organization. The organization wants to remediate this vulnerability in the most efficient way possible. Which of the following should the organization use for this purpose?
A new security regulation was announced that will take effect in the coming year. A company must comply with it to remain in business. Which of the following activities should the company perform next?
Which of the following should be used to ensure that a new software release has not been modified before reaching the user?
Which of the following actions could a security engineer take to ensure workstations and servers are properly monitored for unauthorized changes and software?
An administrator is creating a secure method for a contractor to access a test environment. Which of the following would provide the contractor with the best access to the test environment?
A company's online shopping website became unusable shortly after midnight on January 30, 2023. When a security analyst reviewed the database server, the analyst noticed the following code used for backing up data:
Which of the following should the analyst do next?
A company with a high-availability website is looking to harden its controls at any cost. The company wants to ensure that the site is secure by finding any possible issues. Which of the following would most likely achieve this goal?
An important patch for a critical application has just been released, and a systems administrator is identifying all of the systems requiring the patch. Which of the following must be maintained in order to ensure that all systems requiring the patch are updated?
Which of the following describes the understanding between a company and a client about what will be provided and the accepted time needed to provide the company with the resources?
A company wants to improve the availability of its application with a solution that requires minimal effort in the event a server needs to be replaced or added. Which of the following would be the best solution to meet these objectives?
A security architect wants to prevent employees from receiving malicious attachments by email. Which of the following functions should the chosen solution do?
Which of the following data types best describes an AI tool developed by a company to automate the ticketing system under a specific contract?
Which of the following hardening techniques must be applied on a container image before deploying it to a production environment? (Select two).
Which of the following would be the best way to test resiliency in the event of a primary power failure?
An IT team rolls out a new management application that uses a randomly generated MFA token sent to the administrator’s phone. Despite this new MFA precaution, there is a security breach of the same software. Which of the following describes this kind of attack?
An incident response specialist must stop a malicious attack from expanding to other parts of an organization. Which of the following should the incident response specialist perform first?
Which of the following activities is the first stage in the incident response process?
An organization’s internet-facing website was compromised when an attacker exploited a buffer overflow. Which of the following should the organization deploy to best protect against similar attacks in the future?
A company makes a change during the appropriate change window, but the unsuccessful change extends beyond the scheduled time and impacts customers. Which of the following would prevent this from reoccurring?
Which of the following explains why an attacker cannot easily decrypt passwords using a rainbow table attack?
A security officer observes that a software development team is not complying with its corporate security policy on encrypting confidential data. Which of the following categories refers to this type of non-compliance?
An administrator wants to perform a risk assessment without using proprietary company information. Which of the following methods should the administrator use to gather information?
A systems administrator needs to ensure the secure communication of sensitive data within the organization's private cloud. Which of the following is the best choice for the administrator to implement?
Which of the following actions must an organization take to comply with a person's request for the right to be forgotten?
A security analyst is reviewing logs and discovers the following:

Which of the following should be used lo best mitigate this type of attack?
A company wants to ensure secure remote access to its internal network. The company has only one public IP and would like to avoid making any changes to the current network setup. Which of the following solutions would best accomplish this goal?
Which of the following would best prepare a security team for a specific incident response scenario?
An administrator is estimating the cost associated with an attack that could result in the replacement of a physical server. Which of the following processes is the administrator performing?
Which of the following is the most likely outcome if a large bank fails an internal PCI DSS compliance assessment?
Which of the following types of vulnerabilities is primarily caused by improper use and management of cryptographic certificates?
A systems administrator wants to prevent users from being able to access data based on their responsibilities. The administrator also wants to apply the required access structure via a simplified format. Which of the following should the administrator apply to the site recovery resource group?
Which of the following threat actors would most likely deface the website of a high-profile music group?
An organization is struggling with scaling issues on its VPN concentrator and internet circuit due to remote work. The organization is looking for a software solution that will allow it to reduce traffic on the VPN and internet circuit, while still providing encrypted tunnel access to the data center and monitoring of remote employee internet traffic. Which of the following will help achieve these objectives?
An employee from the accounting department logs in to the website used for processing the company's payments. After logging in, a new desktop application automatically downloads on the employee's computer and causes the computer to restart. Which of the following attacks has occurred?
A program manager wants to ensure contract employees can only use the company’s computers Monday through Friday from 9 a.m. to 5 p.m. Which of the following would best enforce this access control?
An employee clicked a malicious link in an email and downloaded malware onto the company's computer network. The malicious program exfiltrated thousands of customer records. Which of the following should the company implement to prevent this in the future?
A company is working with a vendor to perform a penetration test Which of the following includes an estimate about the number of hours required to complete the engagement?
Which of the following is used to add extra complexity before using a one-way data transformation algorithm?
An employee decides to collect PII data from the company's system for personal use. The employee compresses the data into a single encrypted file before sending the file to their personal email. The security department becomes aware of the attempted misuse and blocks the attachment from leaving the corporate environment. Which of the following types of employee training would most likely reduce the occurrence of this type of issue?
(Select two).
The analyst wants to move data from production to the UAT server for testing the latest release. Which of the following strategies to protect data should the analyst use?
In order to strengthen a password and prevent a hacker from cracking it, a random string of 36 characters was added to the password. Which of the following best describes this technique?
Which of the following techniques can be used to sanitize the data contained on a hard drive while allowing for the hard drive to be repurposed?
A systems administrator is concerned users are accessing emails through a duplicate site that is not run by the company. Which of the following is used in this scenario?
A company is implementing a vendor's security tool in the cloud. The security director does not want to manage users and passwords specific to this tool but would rather utilize the company's standard user directory. Which of the following should the company implement?
A company wants to verify that the software the company is deploying came from the vendor the company purchased the software from. Which of the following is the best way for the company to confirm this information?
An administrator learns that users are receiving large quantities of unsolicited messages. The administrator checks the content filter and sees hundreds of messages sent to multiple users. Which of the following best describes this kind of attack?
Which of the following involves an attempt to take advantage of database misconfigurations?
The local administrator account for a company's VPN appliance was unexpectedly used to log in to the remote management interface. Which of the following would have most likely prevented this from happening'?
An administrator discovers a cross-site scripting vulnerability on a company website. Which of the following will most likely remediate the issue?
As part of new compliance audit requirements, multiple servers need to be segmented on different networks and should be reachable only from authorized internal systems. Which of the following would meet the requirements?
Which of the following is the best way to validate the integrity and availability of a disaster recovery site?
Which of the following allows an exploit to go undetected by the operating system?
A business needs a recovery site but does not require immediate failover. The business also wants to reduce the workload required to recover from an outage. Which of the following recovery sites is the best option?
A new vulnerability enables a type of malware that allows the unauthorized movement of data from a system. Which of the following would detect this behavior?
Which of the following is the most common data loss path for an air-gapped network?
A security manager wants to reduce the number of steps required to identify and contain basic threats. Which of the following will help achieve this goal?
A company is experiencing issues with employees leaving the company for a competitor and taking customer contact information with them. Which of the following tools will help prevent this from reoccurring?
A security analyst is investigating an alert that was produced by endpoint protection software. The analyst determines this event was a false positive triggered by an employee who attempted to download a file. Which of the following is the most likely reason the download was blocked?
A company is in the process of cutting jobs to manage costs. The Chief Information Security Officer is concerned about the increased risk of an insider threat. Which of the following would most likely help the security awareness team address this potential threat?
After failing an audit twice, an organization has been ordered by a government regulatory agency to pay fines. Which of the following caused this action?
A security administrator recently reset local passwords and the following values were recorded in the system:
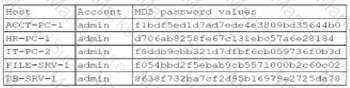
Which of the following in the security administrator most likely protecting against?
Which of the following can be used to identify potential attacker activities without affecting production servers?
Which of the following considerations is the most important for an organization to evaluate as it establishes and maintains a data privacy program?
A network administrator wants to ensure that network traffic is highly secure while in transit. Which of the following actions best describes the actions the network administrator should take?
A security analyst receives an alert that there was an attempt to download known malware. Which of the following actions would allow the best chance to analyze the malware?
Which of the following is the most effective way to protect an application server running software that is no longer supported from network threats?
An external vendor recently visited a company's headquarters tor a presentation. Following the visit a member of the hosting team found a file that the external vendor left behind on a server. The file contained detailed architecture information and code snippets. Which of the following data types best describes this file?
A legal department must maintain a backup from all devices that have been shredded and recycled by a third party. Which of the following best describes this requirement?
Which of the following makes Infrastructure as Code (IaC) a preferred security architecture over traditional infrastructure models?
Security controls in a data center are being reviewed to ensure data is properly protected and that human life considerations are included. Which of the following best describes how the controls should be set up?
Which of the following best protects sensitive data in transit across a geographically dispersed Infrastructure?
The physical security team at a company receives reports that employees are not displaying their badges. The team also observes employees tailgating at controlled entrances. Which of the following topics will the security team most likely emphasize in upcoming security training?
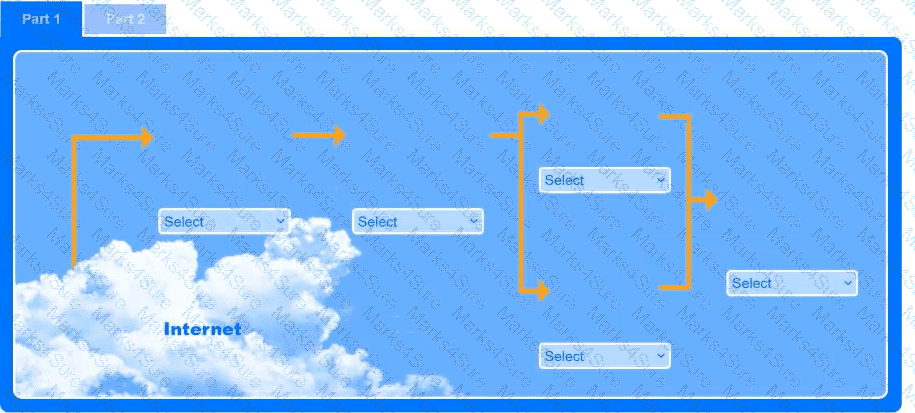
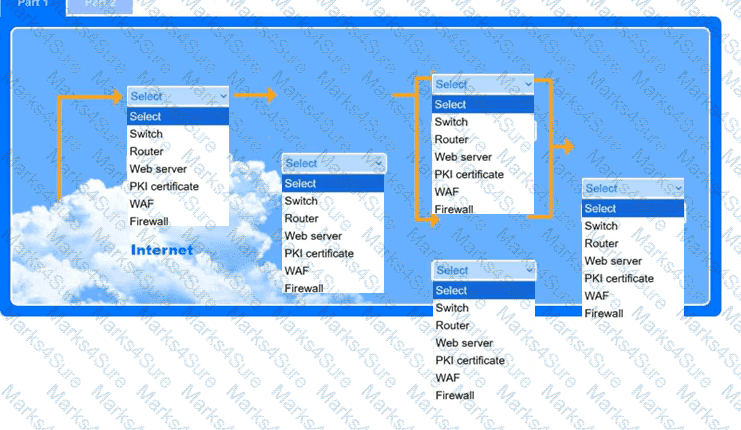
A recent black-box penetration test of http://example.com discovered that external
website vulnerabilities exist, such as directory traversals, cross-site scripting, cross-site forgery, and insecure protocols.
You are tasked with reducing the attack space and enabling secure protocols.
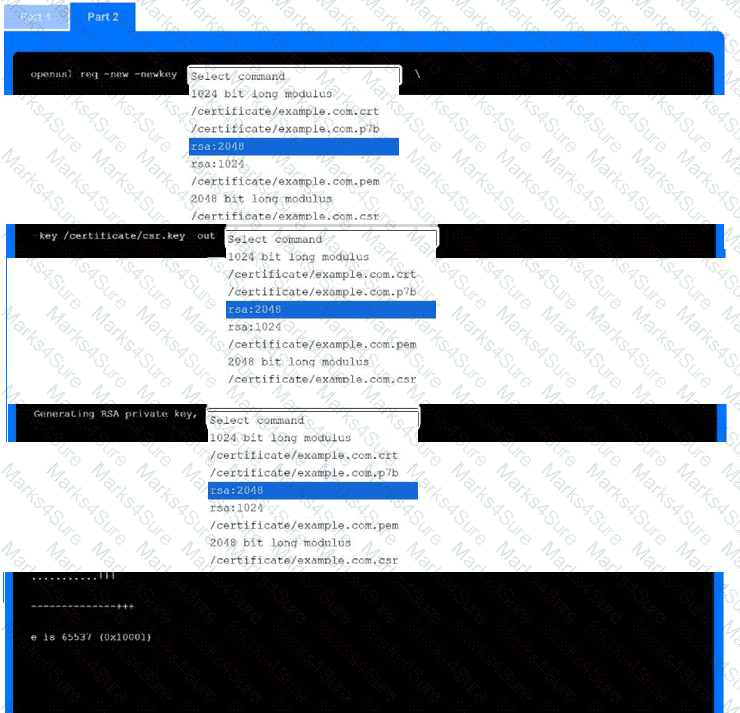
INSTRUCTIONS
Part 1
Use the drop-down menus to select the appropriate technologies for each location to implement a secure and resilient web architecture. Not all technologies will be used, and technologies may be used multiple times.
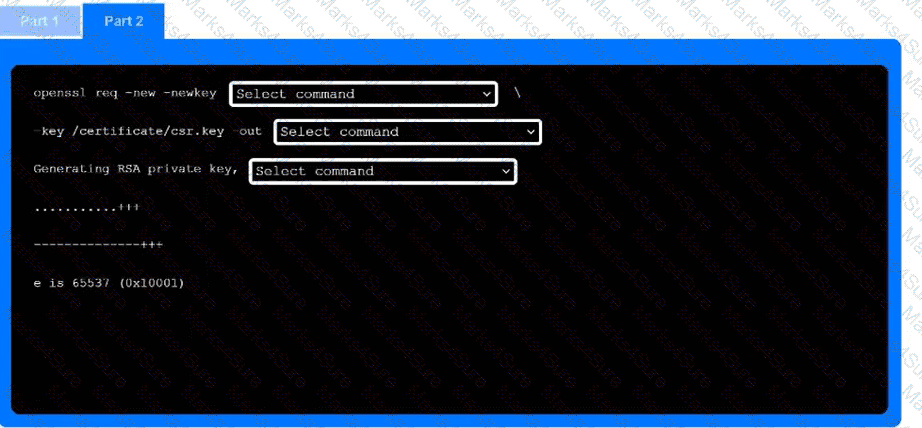
Part 2
Use the drop-down menus to select the appropriate command snippets from the drop-down menus. Each command section must be filled.
Sine© a recent upgrade (o a WLAN infrastructure, several mobile users have been unable to access the internet from the lobby. The networking team performs a heat map survey of the building and finds several WAPs in the area. The WAPs are using similar frequencies with high power settings. Which of the following installation considerations should the security team evaluate next?
Which of the following is an algorithm performed to verify that data has not been modified?
A company expects its provider to ensure servers and networks maintain 97% uptime. Which of the following would most likely list this expectation?
During the onboarding process, an employee needs to create a password for an intranet account. The password must include ten characters, numbers, and letters, and two special characters. Oncethe password is created, the company will grant the employee access to other company-owned websites based on the intranet profile. Which of the following access management concepts is the company most likely using to safeguard intranet accounts and grant access to multiple sites based on a user's intranet account? (Select two).
The help desk receives multiple calls that machines with an outdated OS version are running slowly. Several users are seeing virus detection alerts. Which of the following mitigation techniques should be reviewed first?
An analyst is evaluating the implementation of Zero Trust principles within the data plane. Which of the following would be most relevant for the analyst to evaluate?
A company is concerned about the theft of client data from decommissioned laptops. Which of the following is the most cost-effective method to decrease this risk?
An organization failed to account for the right-to-be-forgotten regulations. Which of the following impacts might this action have on the company?
A company asks a vendor to help its internal red team with a penetration test without providing too much detail about the infrastructure. Which of the following penetration testing methods does this scenario describe?
During a SQL update of a database, a temporary field that was created was replaced by an attacker in order to allow access to the system. Which of the following best describes this type of vulnerability?
A database administrator is updating the company's SQL database, which stores credit card information for pending purchases. Which of the following is the best method to secure the data against a potential breach?
A technician is opening ports on a firewall for a new system being deployed and supported by a SaaS provider. Which of the following is a risk in the new system?
Which of the following should be used to ensure that a device is inaccessible to a network-connected resource?
For which of the following reasons would a systems administrator leverage a 3DES hash from an installer file that is posted on a vendor's website?
Which of the following would most likely prevent exploitation of an end-of-life, business-critical system?
A company wants to ensure employees are allowed to copy files from a virtual desktop during the workday but are restricted during non-working hours. Which of the following security measures should the company set up?
A security administrator is addressing an issue with a legacy system that communicates data using an unencrypted protocol to transfer sensitive data to a third party. No software updates that use an encrypted protocol are available, so a compensating control is needed. Which of the following are the most appropriate for the administrator to suggest? (Select two.)
One of a company's vendors sent an analyst a security bulletin that recommends a BIOS update. Which of the following vulnerability types is being addressed by the patch?
While updating the security awareness training, a security analyst wants to address issues created if vendors' email accounts are compromised. Which of the following recommendations should the security analyst include in the training?
Which of the following are the best methods for hardening end user devices? (Select two)
An employee emailed a new systems administrator a malicious web link and convinced the administrator to change the email server's password. The employee used this access to remove the mailboxes of key personnel. Which of the following security awareness concepts would help prevent this threat in the future?
A company purchased cyber insurance to address items listed on the risk register. Which of the following strategies does this represent?
A site reliability engineer is designing a recovery strategy that requires quick failover to an identical site if the primary facility goes down. Which of the following types of sites should the engineer consider?
Which of the following is the most likely to be used to document risks, responsible parties, and thresholds?
A software developer would like to ensure. The source code cannot be reverse engineered or debugged. Which of the following should the developer consider?
A cybersecurity incident response team at a large company receives notification that malware is present on several corporate desktops No known Indicators of compromise have been found on the network. Which of the following should the team do first to secure the environment?
Which of the following definitions best describes the concept of log co-relation?
A company needs to determine whether authentication weaknesses in a customer-facing web application exist. Which of the following is the best technique to use?
Which of the following should a company use to provide proof of external network security testing?
In which of the following will unencrypted PLC management traffic most likely be found?
A newly identified network access vulnerability has been found in the OS of legacy loT devices. Which of the following would best mitigate this vulnerability quickly?
A company is currently utilizing usernames and passwords, and it wants to integrate an MFA method that is seamless, can Integrate easily into a user's workflow, and can utilize employee-owned devices. Which of the following will meet these requirements?
Which of the following describes the process of concealing code or text inside a graphical image?
A user sends an email that includes a digital signature for validation. Which of the following security concepts would ensure that a user cannot deny that they sent the email?
Which of the following would best allow a company to prevent access to systems from the Internet?
An organization maintains intellectual property that it wants to protect. Which of the following concepts would be most beneficial to add to the company's security awareness training program?
A penetration tester is testing the security of a building’s alarm system. Which type of penetration test is being conducted?
A company wants to update its disaster recovery plan to include a dedicated location for immediate continued operations if a catastrophic event occurs. Which of the following options is best to include in the disaster recovery plan?
A customer has a contract with a CSP and wants to identify which controls should be implemented in the IaaS enclave. Which of the following is most likely to contain this information?
Two companies are in the process of merging. The companies need to decide how to standardize their information security programs. Which of the following would best align the security programs?
A company's marketing department collects, modifies, and stores sensitive customer data. The infrastructure team is responsible for securing the data while in transit and at rest. Which of the following data roles describes the customer?
Which solution is most likely used in the financial industry to mask sensitive data?
Which of the following best describes why me SMS DIP authentication method is more risky to implement than the TOTP method?
A security consultant needs secure, remote access to a client environment. Which of the following should the security consultant most likely use to gain access?
A malicious update was distributed to a common software platform and disabled services at many organizations. Which of the following best describes this type of vulnerability?
A security analyst receives alerts about an internal system sending a large amount of unusual DNS queries to systems on the internet over short periods of time during non-business hours. Which of the following is most likely occurring?
A business received a small grant to migrate its infrastructure to an off-premises solution. Which of the following should be considered first?
An administrator finds that all user workstations and servers are displaying a message that is associated with files containing an extension of .ryk. Which of the following types of infections is present on the systems?
Which of the following provides resilience by hosting critical VMs within different IaaS providers while being maintained by internal application owners?
Which of the following can be used to mitigate attacks from high-risk regions?
A security analyst is reviewing logs to identify the destination of command-and-control traffic originating from a compromised device within the on-premises network. Which of the following is the best log to review?
In which of the following scenarios is tokenization the best privacy technique 10 use?
An employee receives a text message that appears to have been sent by the payroll department and is asking for credential verification. Which of the following social engineering techniques are being attempted? (Choose two.)
Which of the following activities is included in the post-incident review phase?
Which of the following is the most likely benefit of conducting an internal audit?
An organization would like to store customer data on a separate part of the network that is not accessible to users on the main corporate network. Which of the following should the administrator use to accomplish this goal?
A company plans to secure its systems by:
Preventing users from sending sensitive data over corporate email
Restricting access to potentially harmful websites
Which of the following features should the company set up? (Select two).
The security team at a large global company needs to reduce the cost of storing data used for performing investigations. Which of the following types of data should have its retention length reduced?
While conducting a business continuity tabletop exercise, the security team becomes concerned by potential impacts if a generator fails during failover. Which of the following is the team most likely to consider in regard to risk management activities?
Which of the following should be used to ensure an attacker is unable to read the contents of a mobile device's drive if the device is lost?
A company is implementing a policy to allow employees to use their personal equipment for work. However, the company wants to ensure that only company-approved applications can be installed. Which of the following addresses this concern?
Which of the following factors are the most important to address when formulating a training curriculum plan for a security awareness program? (Select two).
A security administrator needs a method to secure data in an environment that includes some form of checks so that the administrator can track any changes. Which of the following should the administrator set up to achieve this goal?
A newly appointed board member with cybersecurity knowledge wants the board of directors to receive a quarterly report detailing the number of incidents that impacted the organization. The systems administrator is creating a way to present the data to the board of directors. Which of the following should the systems administrator use?
A company is in the process of migrating to cloud-based services. The company's IT department has limited resources for migration and ongoing support. Which of the following best meets the company's needs?
Which of the following strategies most effectively protects sensitive data at rest in a database?
A U.S.-based cloud-hosting provider wants to expand its data centers to new international locations. Which of the following should the hosting provider consider first?
Which of the following techniques would identify whether data has been modified in transit?
Which of the following strategies should an organization use to efficiently manage and analyze multiple types of logs?
An administrator must replace an expired SSL certificate. Which of the following does the administrator need to create the new SSL certificate?
Which of the following is die most important security concern when using legacy systems to provide production service?
Which of the following roles, according to the shared responsibility model, is responsible for securing the company’s database in an IaaS model for a cloud environment?
An analyst identifies that multiple users have the same passwords, but the hashes appear to be completely different. Which of the following most likely explains this issue?
An organization is looking to optimize its environment and reduce the number of patches necessary for operating systems. Which of the following will best help to achieve this objective?
Which of the following provides the best protection against unwanted or insecure communications to and from a device?
During a SQL update of a database, a temporary field used as part of the update sequence was modified by an attacker before the update completed in order to allow access to the system. Which of the following best describes this type of vulnerability?
Which of the following mitigation techniques would a security analyst most likely use to avoid bloatware on devices?
Which of the following is the best way to prevent data from being leaked from a secure network that does not need to communicate externally?
A Chief Information Security Officer (CISO) has developed information security policies that relate to the software development methodology. Which of the following would the CISO most likely include in the organization's documentation?
Which of the following would best explain why a security analyst is running daily vulnerability scans on all corporate endpoints?
A systems administrator is looking for a low-cost application-hosting solution that is cloud-based. Which of the following meets these requirements?
Which of the following activities should be performed first to compile a list of vulnerabilities in an environment?
A security analyst learns that an attack vector, used as part of a recent incident, was a well-known IoT device exploit. The analyst needs to review logs to identify the time of the initial exploit. Which of the following logs should the analyst review first?
A company plans to secure its systems by:
Preventing users from sending sensitive data over corporate email
Restricting access to potentially harmful websites
Which of the following features should the company set up? (Select two).
Cadets speaking a foreign language are using company phone numbers to make unsolicited phone calls lo a partner organization. A security analyst validates through phone system logs that the calls are occurring and the numbers are not being spoofed. Which of the following is the most likely explanation?
A security team is reviewing the findings in a report that was delivered after a third party performed a penetration test. One of the findings indicated that a web application form field is vulnerable to cross-site scripting. Which of the following application security techniques should the security analyst recommend the developer implement to prevent this vulnerability?
Prior to implementing a design change, the change must go through multiple steps to ensure that it does not cause any security issues. Which of the following is most likely to be one of those steps?
Which of the following can be used to compromise a system that is running an RTOS?
Which of the following allows a systems administrator to tune permissions for a file?
A user would like to install software and features that are not available with a smartphone's default software. Which of the following would allow the user to install unauthorized software and enable new features?
A growing organization, which hosts an externally accessible application, adds multiple virtual servers to improve application performance and decrease the resource usage on individual servers Which of the following solutions is the organization most likely to employ to further increase performance and availability?
An organization experiences a cybersecurity incident involving a command-and-control server. Which of the following logs should be analyzed to identify the impacted host? (Select two).
Which of the following should a security administrator adhere to when setting up a new set of firewall rules?
A security analyst must prevent remote users from accessing malicious URLs. The sites need to be checked inline for reputation, content, or categorization. Which of the following technologies will help secure the enterprise?
Which of the following is the best way to secure an on-site data center against intrusion from an insider?
Which of the following is a common source of unintentional corporate credential leakage in cloud environments?
A company's antivirus solution is effective in blocking malware but often has false positives. The security team has spent a significant amount of time on investigations but cannot determine a root cause. The company is looking for a heuristic solution. Which of the following should replace the antivirus solution?
Which of the following must be considered when designing a high-availability network? (Select two).
An employee clicks a malicious link in an email that appears to be from the company's Chief Executive Officer. The employee's computer is infected with ransomware that encrypts the company's files. Which of the following is the most effective way for the company to prevent similar incidents in the future?
A software developer wishes to implement an application security technique that will provide assurance of the application's integrity. Which of the following techniques will achieve this?
Which of the following is the most relevant reason a DPO would develop a data inventory?
Which of the following is an example of a false negative vulnerability detection in a scan report?
A recent penetration test identified that an attacker could flood the MAC address table of network switches. Which of the following would best mitigate this type of attack?
A company is considering an expansion of access controls for an application that contractors and internal employees use to reduce costs. Which of the following risk elements should the implementation team understand before granting access to the application?
An organization is evaluating new regulatory requirements associated with the implementation of corrective controls on a group of interconnected financial systems. Which of the following is the most likely reason for the new requirement?
An organization discovers that its cold site does not have enough storage and computers available. Which of the following was most likely the cause of this failure?
A security engineer at a large company needs to enhance IAM to ensure that employees can only access corporate systems during their shifts. Which of the following access controls should the security engineer implement?
Which of the following threat actors is the most likely to be hired by a foreign government to attack critical systems located in other countries?
A systems administrator set up a perimeter firewall but continues to notice suspicious connections between internal endpoints. Which of the following should be set up in order to mitigate the threat posed by the suspicious activity?
Which of the following best describes the practice of researching laws and regulations related to information security operations within a specific industry?
A security analyst scans a company's public network and discovers a host is running a remote desktop that can be used to access the production network. Which of the following changes should the security analyst recommend?
An organization is implementing a COPE mobile device management policy. Which of the following should the organization include in the COPE policy? (Select two).
An enterprise is trying to limit outbound DNS traffic originating from its internal network. Outbound DNS requests will only be allowed from one device with the IP address 10.50.10.25. Which of the following firewall ACLs will accomplish this goal?
Which of the following is the act of proving to a customer that software developers are trained on secure coding?
An employee recently resigned from a company. The employee was responsible for managing and supporting weekly batch jobs over the past five years. A few weeks after the employee resigned. one of the batch jobs talked and caused a major disruption. Which of the following would work best to prevent this type of incident from reoccurring?
Which of the following activities are associated with vulnerability management? (Select two).
Which of the following organizational documents is most often used to establish and communicate expectations associated with integrity and ethical behavior within an organization?
Which of the following would be the best ways to ensure only authorized personnel can access a secure facility? (Select two).
During a routine audit, an analyst discovers that a department at a high school uses a simulation program that was not properly vetted before deployment.
Which of the following threats is this an example of?
During an investigation, a security analyst discovers traffic going out to a command-and-control server. The analyst must find out if any data exfiltration has occurred. Which of the following would best help the analyst determine this?