Which of the following best describes a use case for playbooks in a Linux system?
Which of the following commands should a Linux administrator use to determine the version of a kernel module?
Which of the following utilities supports the automation of security compliance and vulnerability management?
A systems administrator manages multiple Linux servers and needs to set up a reliable and secure way to handle the complexity of managing event records on the OS and application levels. Which of the following should the administrator do?
A systems administrator needs to open the DNS TCP port on a Linux system from network 10.0.0.0/24. Which of the following commands should the administrator use for this task?
While hardening a system, an administrator runs a port scan with Nmap, which returned the following output:
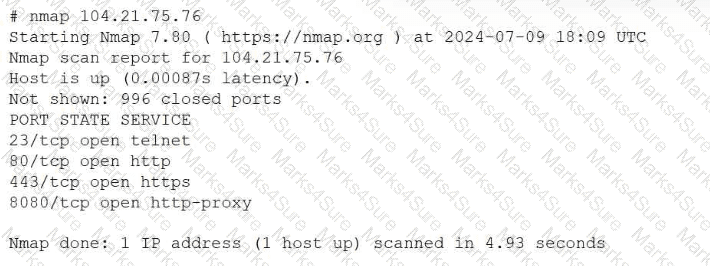
Which of the following is the best way to address this security issue?
An administrator is investigating the reason a Linux workstation is not resolving the website http://www.comptia.org. The administrator executes some commands and receives the following output:
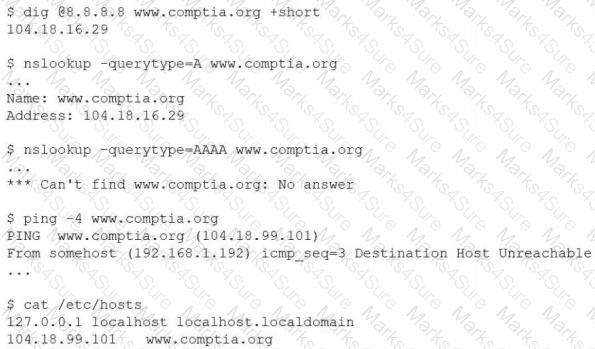
Which of the following is the most likely cause?
Which of the following is the main reason for setting up password expiry policies?
A systems administrator attempts to edit a file as root, but receives the following error:

Which of the following commands allows the administrator to edit the file?
An administrator added a new disk to expand the current storage. Which of the following commands should the administrator run first to add the new disk to the LVM?
A Linux administrator receives reports about MySQL service availability issues. The administrator observes the following information:
uptime -p shows the system has been up for only 2 minutes
journalctl shows messages indicating:mysqld invoked oom-killermysqld cpuset=/ mems_allowed=0
Which of the following explains why the server was offline?
A Linux systems administrator is running an important maintenance task that consumes a large amount of CPU, causing other applications to slow. Which of the following actions should the administrator take to help alleviate the issue?
An administrator needs to verify the user ID, home directory, and assigned shell for the user named "accounting." Which of the following commands should the administrator use to retrieve this information?
A systems administrator wants to review the amount of time the NetworkManager service took to start. Which of the following commands accomplishes this goal?
An administrator must secure an account for a user who is going on extended leave. Which of the following steps should the administrator take? (Choose two)
A Linux administrator tries to install Ansible in a Linux environment. One of the steps is to change the owner and the group of the directory /opt/Ansible and its contents. Which of the following commands will accomplish this task?
An administrator updates the network configuration on a server but wants to ensure the change will not cause an outage if something goes wrong. Which of the following commands allows the administrator to accomplish this goal?
A Linux administrator is making changes to local files that are part of a Git repository. The administrator needs to retrieve changes from the remote Git repository. Which of the following commands should the administrator use to save the local modifications for later review?
An administrator is trying to terminate a process that is not responding. Which of the following commands should the administrator use in order to force the termination of the process?
On a Kubernetes cluster, which of the following resources should be created in order to expose a port so it is publicly accessible on the internet?
In the echo "profile-$num-$name" line of a shell script, the variable $num seems to not be expanding during execution. Which of the following notations ensures the value is expanded?