An API Conned administrator runs the command shown below:
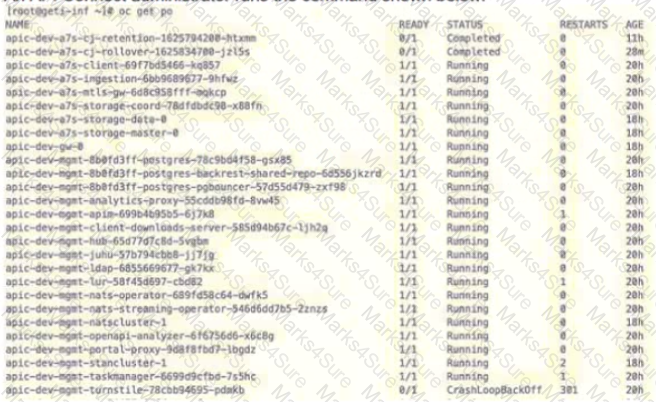
Given the output of the command, what is the state of the API Connect components?
The Analytics subsystem cannot retain historical data.
Developer Portal sites will be unresponsive.
Automated API behavior testing has failed.
New API calls will be rejected by the gateway service.
The command executed is:
sh
CopyEdit
oc get po
This command lists the pods running in an OpenShift (OCP) cluster where IBM API Connect is deployed.
Most API Connect management components (apic-dev-mgmt-xxx) are in a Running state, which indicates that the core API Connect system is operational.
The apic-dev-mgmt-turnstile pod is in a CrashLoopBackOff state, with 301 restarts, indicating that this component has repeatedly failed to start properly.
The Turnstile pod is a critical component of the IBM API Connect Developer Portal.
It manages authentication and access control for the Developer Portal, ensuring that API consumers can access the portal and manage API subscriptions.
When Turnstile is failing, the Developer Portal becomes unresponsive because authentication requests cannot be processed.
Key Observations from the Output:Understanding the Turnstile Component:
Since the Turnstile pod is failing, the Developer Portal will not function properly, preventing users from accessing API documentation and managing API subscriptions.
API providers and consumers will not be able to log in or interact with the Developer Portal.
Why Answer B is Correct?
A. The Analytics subsystem cannot retain historical data. → Incorrect
The Analytics-related pods (e.g., apic-dev-analytics-xxx) are in a Running state.
If the Analytics component were failing, metrics collection and historical API call data would be impacted, but this is not indicated in the output.
C. Automated API behavior testing has failed. → Incorrect
There is no evidence in the pod list that API testing-related components (such as test clients or monitoring tools) have failed.
D. New API calls will be rejected by the gateway service. → Incorrect
The gateway service is not shown as failing in the provided output.
API traffic flows through the Gateway pods (typically apic-gateway-xxx), and they appear to be running fine.
If gateway-related pods were failing, API call processing would be affected, but that is not the case here.
Explanation of Incorrect Answers:
IBM API Connect Deployment on OpenShift
Troubleshooting Developer Portal Issues
Understanding API Connect Components
OpenShift Troubleshooting Pods
IBM Cloud Pak for Integration (CP4I) v2021.2 Administration References:
What ate two ways to add the IBM Cloud Pak tor Integration CatalogSource ob-jects to an OpenShift cluster that has access to the internet?
Copy the resource definition code into a file and use the oc apply -f filename command line option.
Import the catalog project from https://ibm.github.eom/icr-io/cp4int:2.4
Deploy the catalog the Red Hat OpenShift Application Runtimes.
Download the Cloud Pak for Integration driver from partnercentral.ibm.com to a local machine and deploy using the oc new-project command line option
Paste the resource definition code into the import YAML dialog of the OpenShift Admin web console and click Create.
To add the IBM Cloud Pak for Integration (CP4I) CatalogSource objects to an OpenShift cluster that has internet access, there are two primary methods:
Using oc apply -f filename (Option A)
The CatalogSource resource definition can be written in a YAML file and applied using the OpenShift CLI.
This method ensures that the cluster is correctly set up with the required catalog sources for CP4I.
Example command:
sh
CopyEdit
oc apply -f cp4i-catalogsource.yaml
This is a widely used approach for configuring OpenShift resources.
Using the OpenShift Admin Web Console (Option E)
Administrators can manually paste the CatalogSource YAML definition into the OpenShift Admin Web Console.
Navigate to Administrator → Operators → OperatorHub → Create CatalogSource, paste the YAML, and click Create.
This provides a UI-based alternative to using the CLI.
B (Incorrect): There is no valid icr-io/cp4int:2.4 catalog project import method for adding a CatalogSource. IBM’s container images are hosted on IBM Cloud Container Registry (ICR), but this method is not used for adding a CatalogSource.
C (Incorrect): Red Hat OpenShift Application Runtimes (RHOAR) is unrelated to the CatalogSource object creation for CP4I.
D (Incorrect): Downloading the CP4I driver and using oc new-project is not the correct approach for adding a CatalogSource. The oc new-project command is used to create OpenShift projects but does not deploy catalog sources.
Explanation of Incorrect Options:IBM Cloud Pak for Integration (CP4I) v2021.2 Administration References:
IBM Documentation: Managing Operator Lifecycle with OperatorHub
OpenShift Docs: Creating a CatalogSource
IBM Knowledge Center: Installing IBM Cloud Pak for Integration
When using the Platform Navigator, what permission is required to add users and user groups?
root
Super-user
Administrator
User
In IBM Cloud Pak for Integration (CP4I) v2021.2, the Platform Navigator is the central UI for managing integration capabilities, including user and access control. To add users and user groups, the required permission level is Administrator.
User Management Capabilities:
The Administrator role in Platform Navigator has full access to user and group management functions, including:
Adding new users
Assigning roles
Managing access policies
RBAC (Role-Based Access Control) Enforcement:
CP4I enforces RBAC to restrict actions based on roles.
Only Administrators can modify user access, ensuring security compliance.
Access Control via OpenShift and IAM Integration:
User management in CP4I integrates with IBM Cloud IAM or OpenShift User Management.
The Administrator role ensures correct permissions for authentication and authorization.
Why is "Administrator" the Correct Answer?
Why Not the Other Options?Option
Reason for Exclusion
A. root
"root" is a Linux system user and not a role in Platform Navigator. CP4I does not grant UI-based root access.
B. Super-user
No predefined "Super-user" role exists in CP4I. If referring to an elevated user, it still does not match the Administrator role in Platform Navigator.
D. User
Regular "User" roles have view-only or limited permissions and cannot manage users or groups.
Thus, the Administrator role is the correct choice for adding users and user groups in Platform Navigator.
IBM Cloud Pak for Integration - Platform Navigator Overview
Managing Users in Platform Navigator
Role-Based Access Control in CP4I
OpenShift User Management and Authentication
IBM Cloud Pak for Integration (CP4I) v2021.2 Administration References:
What is the License Service's frequency of refreshing data?
1 hour.
30 seconds.
5 minutes.
30 minutes.
In IBM Cloud Pak Foundational Services, the License Service is responsible for collecting, tracking, and reporting license usage data. It ensures compliance by monitoring the consumption of IBM Cloud Pak licenses across the environment.
The License Service refreshes its data every 5 minutes to keep the license usage information up to date.
This frequent update cycle helps organizations maintain accurate tracking of their entitlements and avoid non-compliance issues.
A. 1 hour (Incorrect)
The License Service updates its records more frequently than every hour to provide timely insights.
B. 30 seconds (Incorrect)
A refresh interval of 30 seconds would be too frequent for license tracking, leading to unnecessary overhead.
C. 5 minutes (Correct)
The IBM License Service refreshes its data every 5 minutes, ensuring real-time tracking without excessive system load.
D. 30 minutes (Incorrect)
A 30-minute refresh would delay the reporting of license usage, which is not the actual behavior of the License Service.
Analysis of the Options:
IBM License Service Overview
IBM Cloud Pak License Service Data Collection Interval
IBM Cloud Pak Compliance and License Reporting
IBM Cloud Pak for Integration (CP4I) v2021.2 Administration References:
The following deployment topology has been created for an API Connect deploy-ment by a client.
Which two statements are true about the topology?
A. Regular back-ups of the API Manager and Portal have to be taken and these backups should be replicated
to the second site.
This represents a Active/Passive deployment (or Portal and Management ser-vices.
This represents a distributed Kubernetes cluster across the sites.
In case of Data Center J failing, the Kubernetes service of Data Center 2 will detect and instantiate the portal and management services on Data Center 2.
This represents an Active/Active deployment for Gateway and Analytics services.
IBM API Connect, as part of IBM Cloud Pak for Integration (CP4I), supports various deployment topologies, including Active/Active and Active/Passive configurations across multiple data centers. Let's analyze the provided topology carefully:
Backup Strategy (Option A - Correct)
The API Manager and Developer Portal components are stateful and require regular backups.
Since the topology spans across two sites, these backups should be replicated to the second site to ensure disaster recovery (DR) and high availability (HA).
This aligns with IBM’s best practices for multi-data center deployment of API Connect.
Deployment Mode for API Manager & Portal (Option B - Incorrect)
The question suggests that API Manager and Portal are deployed across two sites.
If it were an Active/Passive deployment, only one site would be actively handling requests, while the second remains idle.
However, in IBM’s recommended architectures, API Manager and Portal are usually deployed in an Active/Active setup with proper failover mechanisms.
Cluster Type (Option C - Incorrect)
A distributed Kubernetes cluster across multiple sites would require an underlying multi-cluster federation or synchronization.
IBM API Connect is usually deployed on separate Kubernetes clusters per data center, rather than a single distributed cluster.
Therefore, this topology does not represent a distributed Kubernetes cluster across sites.
Failover Behavior (Option D - Incorrect)
Kubernetes cannot automatically detect failures in Data Center 1 and migrate services to Data Center 2 unless specifically configured with multi-cluster HA policies and disaster recovery.
Instead, IBM API Connect HA and DR mechanisms would handle failover via manual or automated orchestration, but not via Kubernetes native services.
Gateway and Analytics Deployment (Option E - Correct)
API Gateway and Analytics services are typically deployed in Active/Active mode for high availability and load balancing.
This means that traffic is dynamically routed to the available instance in both sites, ensuring uninterrupted API traffic even if one data center goes down.
Final Answer:✅ A. Regular backups of the API Manager and Portal have to be taken, and these backups should be replicated to the second site.✅ E. This represents an Active/Active deployment for Gateway and Analytics services.
IBM API Connect Deployment Topologies
IBM Documentation – API Connect Deployment Models
High Availability and Disaster Recovery in IBM API Connect
IBM API Connect HA & DR Guide
IBM Cloud Pak for Integration Architecture Guide
IBM Cloud Pak for Integration Docs
References:
What authentication information is provided through Base DN in the LDAP configuration process?
Path to the server containing the Directory.
Distinguished name of the search base.
Name of the database.
Configuration file path.
In Lightweight Directory Access Protocol (LDAP) configuration, the Base Distinguished Name (Base DN) specifies the starting point in the directory tree where searches for user authentication and group information begin. It acts as the root of the LDAP directory structure for queries.
Defines the scope of LDAP searches for user authentication.
Helps locate users, groups, and other directory objects within the directory hierarchy.
Ensures that authentication requests are performed within the correct organizational unit (OU) or domain.
Example: If users are stored in ou=users,dc=example,dc=com, then the Base DN would be:
Key Role of Base DN in Authentication:dc=example,dc=com
When an authentication request is made, LDAP searches for user entries within this Base DN to validate credentials.
A. Path to the server containing the Directory.
Incorrect, because the server path (LDAP URL) is defined separately, usually in the format:
Why Other Options Are Incorrect:ldap://ldap.example.com:389
C. Name of the database.
Incorrect, because LDAP is not a traditional relational database; it uses a hierarchical structure.
D. Configuration file path.
Incorrect, as LDAP configuration files (e.g., slapd.conf for OpenLDAP) are separate from the Base DN and are used for server settings, not authentication scope.
IBM Cloud Pak for Integration (CP4I) v2021.2 Administration References:
IBM Documentation: LDAP Authentication Configuration
IBM Cloud Pak for Integration - Configuring LDAP
Understanding LDAP Distinguished Names (DNs)
What are two ways an Aspera HSTS Instance can be created?
Foundational Services Dashboard
OpenShift console
Platform Navigator
IBM Aspera HSTS Installer
Terraform
IBM Aspera High-Speed Transfer Server (HSTS) is a key component of IBM Cloud Pak for Integration (CP4I) that enables secure, high-speed data transfers. There are two primary methods to create an Aspera HSTS instance in CP4I v2021.2:
OpenShift Console (Option B - Correct):
Aspera HSTS can be deployed within an OpenShift cluster using the OpenShift Console.
Administrators can deploy Aspera HSTS by creating an instance from the IBM Aspera HSTS operator, which is available through the OpenShift OperatorHub.
The deployment is managed using Kubernetes custom resources (CRs) and YAML configurations.
IBM Aspera HSTS Installer (Option D - Correct):
IBM provides an installer for setting up an Aspera HSTS instance on supported platforms.
This installer automates the process of configuring the required services and dependencies.
It is commonly used for standalone or non-OpenShift deployments.
Analysis of Other Options:
Option A (Foundational Services Dashboard) - Incorrect:
The Foundational Services Dashboard is used for managing IBM Cloud Pak foundational services like identity and access management but does not provide direct deployment of Aspera HSTS.
Option C (Platform Navigator) - Incorrect:
Platform Navigator is used to manage cloud-native integrations, but it does not directly create Aspera HSTS instances. Instead, it can be used to access and manage the Aspera HSTS services after deployment.
Option E (Terraform) - Incorrect:
While Terraform can be used to automate infrastructure provisioning, IBM does not provide an official Terraform module for directly creating Aspera HSTS instances in CP4I v2021.2.
IBM Cloud Pak for Integration (CP4I) v2021.2 Administration References:
IBM Documentation: Deploying Aspera HSTS on OpenShift
IBM Aspera Knowledge Center: Aspera HSTS Installation Guide
IBM Redbooks: IBM Cloud Pak for Integration Deployment Guide
What is a prerequisite when configuring foundational services IAM for single-sign-on?
Access to the OpenShift Container Platform console as kubeadmin.
Access to IBM Cloud Pak for Integration as kubeadmin.
Access to OpenShift cluster as root.
Access to IAM service as administrator.
In IBM Cloud Pak for Integration (CP4I) v2021.2, Identity and Access Management (IAM) is part of Foundational Services, which provides authentication and authorization across different modules within CP4I.
When configuring IAM for single sign-on (SSO), the administrator must have administrator access to the IAM service. This is essential for:
Integrating external identity providers (IdPs) such as LDAP, SAML, or OIDC.
Managing user roles and access control policies across the Cloud Pak environment.
Configuring SSO settings for seamless authentication across all IBM Cloud Pak services.
IAM service administrators have full control over authentication and SSO settings.
They can configure and integrate identity providers for authentication.
This level of access is required to modify IAM settings in Cloud Pak for Integration.
Why Answer D (Access to IAM service as administrator) is Correct?
A. Access to the OpenShift Container Platform console as kubeadmin. → Incorrect
While kubeadmin is a cluster-wide OpenShift administrator, this role does not grant IAM administrative privileges in Cloud Pak Foundational Services.
IAM settings are managed within IBM Cloud Pak, not solely through OpenShift.
B. Access to IBM Cloud Pak for Integration as kubeadmin. → Incorrect
kubeadmin can manage OpenShift resources, but IAM requires specific access to the IAM service within Cloud Pak.
IAM administrators are responsible for configuring authentication, SSO, and identity providers.
C. Access to OpenShift cluster as root. → Incorrect
Root access is not relevant here because OpenShift does not use root users for administration.
IAM configurations are done within Cloud Pak, not at the OpenShift OS level.
Explanation of Incorrect Answers:
IBM Cloud Pak Foundational Services - IAM Configuration
Configuring Single Sign-On (SSO) in IBM Cloud Pak
IBM Cloud Pak for Integration Security Overview
OpenShift Authentication and Identity Management
IBM Cloud Pak for Integration (CP4I) v2021.2 Administration References:
Which two authentication types support single sign-on?
2FA
Enterprise LDAP
Plain text over HTTPS
Enterprise SSH
OpenShift authentication
Single Sign-On (SSO) is an authentication mechanism that allows users to log in once and gain access to multiple applications without re-entering credentials. In IBM Cloud Pak for Integration (CP4I), Enterprise LDAP and OpenShift authentication both support SSO.
Enterprise LDAP (B) – ✅ Supports SSO
Lightweight Directory Access Protocol (LDAP) is commonly used in enterprises for centralized authentication.
CP4I can integrate with Enterprise LDAP, allowing users to authenticate once and access multiple cloud services without needing separate logins.
OpenShift Authentication (E) – ✅ Supports SSO
OpenShift provides OAuth-based authentication, enabling SSO across multiple OpenShift-integrated services.
CP4I uses OpenShift’s built-in identity provider to allow seamless user authentication across different Cloud Pak components.
A. 2FA (Incorrect):
Two-Factor Authentication (2FA) enhances security by requiring an additional verification step but does not inherently support SSO.
C. Plain Text over HTTPS (Incorrect):
Plain text authentication is insecure and does not support SSO.
D. Enterprise SSH (Incorrect):
SSH authentication is used for remote access to servers but is not related to SSO.
Analysis of the Incorrect Options:
IBM Cloud Pak for Integration Authentication & SSO Guide
Red Hat OpenShift Authentication and Identity Providers
IBM Cloud Pak - Integrating with Enterprise LDAP
IBM Cloud Pak for Integration (CP4I) v2021.2 Administration References:
Which statement is true about enabling open tracing for API Connect?
Only APIs using API Gateway can be traced in the Operations Dashboard.
API debug data is made available in OpenShift cluster logging.
This feature is only available in non-production deployment profiles
Trace data can be viewed in Analytics dashboards
Open Tracing in IBM API Connect allows for distributed tracing of API calls across the system, helping administrators analyze performance bottlenecks and troubleshoot issues. However, this capability is specifically designed to work with APIs that utilize the API Gateway.
Option A (Correct Answer): IBM API Connect integrates with OpenTracing for API Gateway, allowing the tracing of API requests in the Operations Dashboard. This provides deep visibility into request flows and latencies.
Option B (Incorrect): API debug data is not directly made available in OpenShift cluster logging. Instead, API tracing data is captured using OpenTracing-compatible tools.
Option C (Incorrect): OpenTracing is available for all deployment profiles, including production, not just non-production environments.
Option D (Incorrect): Trace data is not directly visible in Analytics dashboards but rather in the Operations Dashboard where administrators can inspect API request traces.
IBM Cloud Pak for Integration (CP4I) v2021.2 Administration References:
IBM API Connect Documentation – OpenTracing
IBM Cloud Pak for Integration - API Gateway Tracing
IBM API Connect Operations Dashboard Guide
In Cloud Pak for Integration, which user role can replace default Keys and Certificates?
Cluster Manager
Super-user
System user
Cluster Administrator
In IBM Cloud Pak for Integration (CP4I) v2021.2, only a Cluster Administrator has the necessary permissions to replace default keys and certificates. This is because modifying security components such as TLS certificates affects the entire cluster and requires elevated privileges.
Access to OpenShift and Cluster-Wide Resources:
The Cluster Administrator role has full administrative control over the OpenShift cluster where CP4I is deployed.
Replacing keys and certificates often involves interacting with OpenShift secrets and security configurations, which require cluster-wide access.
Management of Certificates and Encryption:
In CP4I, certificates are used for securing communication between integration components and external systems.
Updating or replacing certificates requires privileges to modify security configurations, which only a Cluster Administrator has.
Control Over Security Policies:
CP4I security settings, including certificates, are managed at the cluster level.
Cluster Administrators ensure compliance with security policies, including certificate renewal and management.
Why is "Cluster Administrator" the Correct Answer?
Why Not the Other Options?Option
Reason for Exclusion
A. Cluster Manager
This role is typically responsible for monitoring and managing cluster resources but does not have full administrative control over security settings.
B. Super-user
There is no predefined "Super-user" role in CP4I. If referring to an elevated user, it would still require a Cluster Administrator's permissions to replace certificates.
C. System User
System users often refer to service accounts or application-level users that lack the required cluster-wide security privileges.
Thus, the Cluster Administrator role is the only one with the required access to replace default keys and certificates in Cloud Pak for Integration.
IBM Cloud Pak for Integration Security Overview
Managing Certificates in Cloud Pak for Integration
OpenShift Cluster Administrator Role
IBM Cloud Pak for Integration - Replacing Default Certificates
IBM Cloud Pak for Integration (CP4I) v2021.2 Administration References:
What is an alternative representation of a Kubemetes namespace?
Group
Collaboration
OCP-Namespace
Project
In IBM Cloud Pak for Integration (CP4I) v2021.2, which runs on Red Hat OpenShift Container Platform (OCP), a Kubernetes namespace is alternatively referred to as a Project.
In Kubernetes, a namespace is a logical isolation mechanism that helps organize and manage resources within a cluster.
In OpenShift (OCP), which is built on Kubernetes, a Project is essentially a namespace with additional OpenShift-specific functionalities such as role-based access control (RBAC), quotas, and security policies.
OpenShift extends the standard Kubernetes namespace concept by integrating user and group access controls, making the Project a more feature-rich alternative.
Thus, in the context of IBM Cloud Pak for Integration (CP4I) v2021.2, the correct alternative representation of a Kubernetes namespace is a Project in OpenShift.
IBM Cloud Pak for Integration (CP4I) v2021.2 Administration References:
IBM CP4I Documentation – OpenShift Project Management
Red Hat OpenShift Documentation – Understanding Projects and Namespaces
Kubernetes Documentation – Namespaces
When Instantiating a new capability through the Platform Navigator, what must be done to see distributed tracing data?
Press the 'enable' button In the Operations Dashboard.
Add 'operationsDashboard: true' to the deployment YAML.
Run the oc register command against the capability.
Register the capability with the Operations Dashboard
In IBM Cloud Pak for Integration (CP4I) v2021.2, when instantiating a new capability via the Platform Navigator, distributed tracing data is not automatically available. To enable tracing and observability for a capability, it must be registered with the Operations Dashboard.
The Operations Dashboard in CP4I provides centralized observability, logging, and distributed tracing across integration components.
Capabilities such as IBM API Connect, App Connect, IBM MQ, and Event Streams need to be explicitly registered with the Operations Dashboard to collect and display tracing data.
Registration links the capability with the distributed tracing service, allowing telemetry data to be captured.
Why "Register the capability with the Operations Dashboard" is the correct answer?
Why the Other Options Are Incorrect?Option
Explanation
Correct?
A. Press the 'enable' button in the Operations Dashboard.
❌ Incorrect – There is no single 'enable' button that automatically registers capabilities. Manual registration is required.
❌
B. Add 'operationsDashboard: true' to the deployment YAML.
❌ Incorrect – This setting alone does not enable distributed tracing. The capability still needs to be registered with the Operations Dashboard.
❌
C. Run the oc register command against the capability.
❌ Incorrect – There is no oc register command in OpenShift or CP4I for registering capabilities with the Operations Dashboard.
❌
Final Answer:✅ D. Register the capability with the Operations Dashboard
IBM Cloud Pak for Integration - Operations Dashboard
Enabling Distributed Tracing in IBM CP4I
IBM CP4I - Observability and Monitoring
IBM Cloud Pak for Integration (CP4I) v2021.2 Administration References:
An administrator has just installed the OpenShift cluster as the first step of installing Cloud Pak for Integration.
What is an indication of successful completion of the OpenShift Cluster installation, prior to any other cluster operation?
The command "which oc" shows that the OpenShift Command Line Interface(oc) is successfully installed.
The duster credentials are included at the end of the /.openshifl_install.log file.
The command "oc get nodes" returns the list of nodes in the cluster.
The OpenShift Admin console can be opened with the default user and will display the cluster statistics.
After successfully installing an OpenShift cluster, the most reliable way to confirm that the cluster is up and running is by checking the status of its nodes. This is done using the oc get nodes command.
The command oc get nodes lists all the nodes in the cluster and their current status.
If the installation is successful, the nodes should be in a "Ready" state, indicating that the cluster is functional and prepared for further configuration, including the installation of IBM Cloud Pak for Integration (CP4I).
Option A (Incorrect – which oc): This only verifies that the OpenShift CLI (oc) is installed on the local system, but it does not confirm the cluster installation.
Option B (Incorrect – Checking /.openshift_install.log): While the installation log may indicate a successful install, it does not confirm the operational status of the cluster.
Option C (Correct – oc get nodes): This command confirms that the cluster is running and provides a status check on all nodes. If the nodes are listed and marked as "Ready", it indicates that the OpenShift cluster is successfully installed.
Option D (Incorrect – OpenShift Admin Console Access): While the OpenShift Web Console can be accessed if the cluster is installed, this does not guarantee that the cluster is fully operational. The most definitive check is through the oc get nodes command.
Analysis of the Options:
IBM Cloud Pak for Integration Installation Guide
Red Hat OpenShift Documentation – Cluster Installation
Verifying OpenShift Cluster Readiness (oc get nodes)
IBM Cloud Pak for Integration (CP4I) v2021.2 Administration References:
Which OpenShift component is responsible for checking the OpenShift Update Service for valid updates?
Cluster Update Operator
Cluster Update Manager
Cluster Version Updater
Cluster Version Operator
The Cluster Version Operator (CVO) is responsible for checking the OpenShift Update Service (OSUS) for valid updates in an OpenShift cluster. It continuously monitors for available updates and ensures that the cluster components are updated according to the specified update policy.
Periodically checks the OpenShift Update Service (OSUS) for available updates.
Manages the ClusterVersion resource, which defines the current version and available updates.
Ensures that cluster operators are applied in the correct order.
Handles update rollouts and recovery in case of failures.
A. Cluster Update Operator – No such component exists in OpenShift.
B. Cluster Update Manager – This is not an OpenShift component. The update process is managed by CVO.
C. Cluster Version Updater – Incorrect term; the correct term is Cluster Version Operator (CVO).
IBM Documentation – OpenShift Cluster Version Operator
IBM Cloud Pak for Integration (CP4I) v2021.2 Knowledge Center
Red Hat OpenShift Documentation on Cluster Updates
Key Functions of the Cluster Version Operator (CVO):Why Not the Other Options?IBM Cloud Pak for Integration (CP4I) v2021.2 Administration References.
Which command shows the current cluster version and available updates?
update
adm upgrade
adm update
upgrade
In IBM Cloud Pak for Integration (CP4I) v2021.2, which runs on OpenShift, administrators often need to check the current cluster version and available updates before performing an upgrade.
The correct command to display the current OpenShift cluster version and check for available updates is:
oc adm upgrade
This command provides information about:
The current OpenShift cluster version.
Whether a newer version is available for upgrade.
The channel and upgrade path.
A. update – Incorrect
There is no oc update or update command in OpenShift CLI for checking cluster versions.
C. adm update – Incorrect
oc adm update is not a valid command in OpenShift. The correct subcommand is adm upgrade.
D. upgrade – Incorrect
oc upgrade is not a valid OpenShift CLI command. The correct syntax requires adm upgrade.
Why the other options are incorrect:
Example Output of oc adm upgrade:$ oc adm upgrade
Cluster version is 4.10.16
Updates available:
Version 4.11.0
Version 4.11.1
OpenShift Cluster Upgrade Documentation
IBM Cloud Pak for Integration OpenShift Upgrade Guide
Red Hat OpenShift CLI Reference
IBM Cloud Pak for Integration (CP4I) v2021.2 Administration References:
Which service receives audit data and collects application logs in Cloud Pak Foundational Services?
logging service
audit-syslog-service
systemd journal
fluentd service
In IBM Cloud Pak Foundational Services, the audit-syslog-service is responsible for receiving audit data and collecting application logs. This service ensures that security and compliance-related events are properly recorded and made available for analysis.
The audit-syslog-service is a key component of Cloud Pak's logging and monitoring framework, specifically designed to capture audit logs from various services.
It can forward logs to external SIEM (Security Information and Event Management) systems or centralized log collection tools for further analysis.
It helps organizations meet compliance and governance requirements by maintaining detailed audit trails.
Why is audit-syslog-service the correct answer?
A. logging service (Incorrect)
While Cloud Pak Foundational Services include a logging service, it is primarily for general application logging and does not specifically handle audit data collection.
C. systemd journal (Incorrect)
systemd journal is the default system log manager on Linux but is not the dedicated service for handling Cloud Pak audit logs.
D. fluentd service (Incorrect)
Fluentd is a log forwarding agent used for collecting and transporting logs, but it does not directly receive audit data in Cloud Pak Foundational Services. It can be used in combination with audit-syslog-service for log aggregation.
Analysis of the Incorrect Options:
IBM Cloud Pak Foundational Services - Audit Logging
IBM Cloud Pak for Integration Logging and Monitoring
Configuring Audit Log Forwarding in IBM Cloud Pak
IBM Cloud Pak for Integration (CP4I) v2021.2 Administration References:
What ate the two possible options to upgrade Common Services from the Extended Update Support (EUS) version (3.6.x) to the continuous delivery versions (3.7.x or later)?
Click the Update button on the Details page of the common-services operand.
Select the Update Common Services option from the Cloud Pak Administration Hub console.
Use the OpenShift web console to change the operator channel from stable-v1 to v3.
Run the script provided by IBM using links available in the documentation.
Click the Update button on the Details page of the IBM Cloud Pak Founda-tional Services operator.
IBM Cloud Pak for Integration (CP4I) v2021.2 relies on IBM Cloud Pak Foundational Services, which was previously known as IBM Common Services. Upgrading from the Extended Update Support (EUS) version (3.6.x) to a continuous delivery version (3.7.x or later) requires following IBM's recommended upgrade paths. The two valid options are:
Using IBM's provided script (Option D):
IBM provides a script specifically designed to upgrade Cloud Pak Foundational Services from an EUS version to a later continuous delivery (CD) version.
This script automates the necessary upgrade steps and ensures dependencies are properly handled.
IBM's official documentation includes the script download links and usage instructions.
Using the IBM Cloud Pak Foundational Services operator update button (Option E):
The IBM Cloud Pak Foundational Services operator in the OpenShift web console provides an update button that allows administrators to upgrade services.
This method is recommended by IBM for in-place upgrades, ensuring minimal disruption while moving from 3.6.x to a later version.
The upgrade process includes rolling updates to maintain high availability.
Option A (Click the Update button on the Details page of the common-services operand):
There is no direct update button at the operand level that facilitates the entire upgrade from EUS to CD versions.
The upgrade needs to be performed at the operator level, not just at the operand level.
Option B (Select the Update Common Services option from the Cloud Pak Administration Hub console):
The Cloud Pak Administration Hub does not provide a direct update option for Common Services.
Updates are handled via OpenShift or IBM’s provided scripts.
Option C (Use the OpenShift web console to change the operator channel from stable-v1 to v3):
Simply changing the operator channel does not automatically upgrade from an EUS version to a continuous delivery version.
IBM requires following specific upgrade steps, including running a script or using the update button in the operator.
Incorrect Options and Justification:
IBM Cloud Pak Foundational Services Upgrade Documentation:
IBM Official Documentation
IBM Cloud Pak for Integration v2021.2 Knowledge Center
IBM Redbooks and Technical Articles on CP4I Administration
IBM Cloud Pak for Integration (CP4I) v2021.2 Administration References:
Which statement is true about the removal of individual subsystems of API Connect on OpenShift or Cloud Pak for Integration?
They can be deleted regardless of the deployment methods.
They can be deleted if API Connect was deployed using a single top level CR.
They cannot be deleted if API Connect was deployed using a single top level CR.
They cannot be deleted if API Connect was deployed using a single top level CRM.
In IBM Cloud Pak for Integration (CP4I) v2021.2, when deploying API Connect on OpenShift or within the Cloud Pak for Integration framework, there are different deployment methods:
Single Top-Level Custom Resource (CR) – This method deploys all API Connect subsystems as a single unit, meaning they are managed together. Removing individual subsystems is not supported when using this deployment method. If you need to remove a subsystem, you must delete the entire API Connect instance.
Multiple Independent Custom Resources (CRs) – This method allows more granular control, enabling the deletion of individual subsystems without affecting the entire deployment.
Since the question specifically asks about API Connect deployed using a single top-level CR, it is not possible to delete individual subsystems. The entire deployment must be deleted and reconfigured if changes are required.
IBM Cloud Pak for Integration (CP4I) v2021.2 Administration References:
IBM API Connect v10 Documentation: IBM Docs - API Connect on OpenShift
IBM Cloud Pak for Integration Knowledge Center: IBM CP4I Documentation
API Connect Deployment Guide: Managing API Connect Subsystems
After setting up OpenShift Logging an index pattern in Kibana must be created to retrieve logs for Cloud Pak for Integration (CP4I) applications. What is the correct index for CP4I applications?
cp4i-*
applications*
torn-*
app-*
When configuring OpenShift Logging with Kibana to retrieve logs for Cloud Pak for Integration (CP4I) applications, the correct index pattern to use is applications*.
Here’s why:
IBM Cloud Pak for Integration (CP4I) applications running on OpenShift generate logs that are stored in the Elasticsearch logging stack.
The standard OpenShift logging format organizes logs into different indices based on their source type.
The applications* index pattern is used to capture logs for applications deployed on OpenShift, including CP4I components.
Analysis of the options:
Option A (Incorrect – cp4i-*): There is no specific index pattern named cp4i-* for retrieving CP4I logs in OpenShift Logging.
*Option B (Correct – applications)**: This is the correct index pattern used in Kibana to retrieve logs from OpenShift applications, including CP4I components.
Option C (Incorrect – torn-*): This is not a valid OpenShift logging index pattern.
Option D (Incorrect – app-*): This index does not exist in OpenShift logging by default.
IBM Cloud Pak for Integration (CP4I) v2021.2 Administration References:
IBM Cloud Pak for Integration Logging Guide
OpenShift Logging Documentation
Kibana and Elasticsearch Index Patterns in OpenShift
Which storage type is supported with the App Connect Enterprise (ACE) Dash-board instance?
Ephemeral storage
Flash storage
File storage
Raw block storage
In IBM Cloud Pak for Integration (CP4I) v2021.2, App Connect Enterprise (ACE) Dashboard requires persistent storage to maintain configurations, logs, and runtime data. The supported storage type for the ACE Dashboard instance is file storage because:
It supports ReadWriteMany (RWX) access mode, allowing multiple pods to access shared data.
It ensures data persistence across restarts and upgrades, which is essential for managing ACE integrations.
It is compatible with NFS, IBM Spectrum Scale, and OpenShift Container Storage (OCS), all of which provide file system-based storage.
A. Ephemeral storage – Incorrect
Ephemeral storage is temporary and data is lost when the pod restarts or gets rescheduled.
ACE Dashboard needs persistent storage to retain configuration and logs.
B. Flash storage – Incorrect
Flash storage refers to SSD-based storage and is not specifically required for the ACE Dashboard.
While flash storage can be used for better performance, ACE requires file-based persistence, which is different from flash storage.
D. Raw block storage – Incorrect
Block storage is low-level storage that is used for databases and applications requiring high-performance IOPS.
ACE Dashboard needs a shared file system, which block storage does not provide.
Why the other options are incorrect:
IBM App Connect Enterprise (ACE) Storage Requirements
IBM Cloud Pak for Integration Persistent Storage Guide
OpenShift Persistent Volume Types
IBM Cloud Pak for Integration (CP4I) v2021.2 Administration References:
What needs to be created to allow integration flows in App Connect Designer or App Connect Dashboard to invoke callable flows across a hybrid environment?
Switch server
Mapping assist
Integration agent
Kafka sync
In IBM App Connect, when integrating flows across a hybrid environment (a combination of cloud and on-premises systems), an Integration Agent is required to enable callable flows.
Callable flows allow one integration flow to invoke another flow that may be running in a different environment (on-premises or cloud).
The Integration Agent acts as a bridge between IBM App Connect Designer (cloud-based) or App Connect Dashboard and the on-premises resources.
It ensures secure and reliable communication between different environments.
Option A (Incorrect – Switch server): No such component is needed in App Connect for hybrid integrations.
Option B (Incorrect – Mapping assist): This is used for transformation support but does not enable cross-environment callable flows.
Option C (Correct – Integration agent): The Integration Agent is specifically designed to support callable flows across hybrid environments.
Option D (Incorrect – Kafka): While Kafka is useful for event-driven architectures, it is not required for invoking callable flows between App Connect instances.
Why is the Integration Agent needed?Analysis of the Options:IBM Cloud Pak for Integration (CP4I) v2021.2 Administration References:
IBM App Connect Hybrid Integration Guide
Using Integration Agents for Callable Flows
IBM Cloud Pak for Integration Documentation
Users of the Cloud Pak for Integration topology are noticing that the Integration Runtimes page in the platform navigator is displaying the following message: "Some runtimes cannot be created yet-Assuming that the users have the necessary permissions, what might cause this message to be displayed?
The Aspera. DataPower, or MQ operators have not been deployed.
The platform navigator operator has not been installed cluster-wide
The ibm-entitlement-key has not been added in same namespace as the platform navigator.
The API Connect operator has not been deployed.
In IBM Cloud Pak for Integration (CP4I), the Integration Runtimes page in the Platform Navigator provides an overview of available and deployable runtime components, such as IBM MQ, DataPower, API Connect, and Aspera.
When users see the message:
"Some runtimes cannot be created yet"
It typically indicates that one or more required operators have not been deployed. Each integration runtime requires its respective operator to be installed and running in order to create and manage instances of that runtime.
If the Aspera, DataPower, or MQ operators are missing, then their corresponding runtimes will not be available in the Platform Navigator.
The Platform Navigator relies on these operators to manage the lifecycle of integration components.
Even if users have the necessary permissions, without the required operators, the integration runtimes cannot be provisioned.
B. The platform navigator operator has not been installed cluster-wide
The Platform Navigator does not need to be installed cluster-wide for runtimes to be available.
If the Platform Navigator was missing, users would not even be able to access the Integration Runtimes page.
C. The ibm-entitlement-key has not been added in the same namespace as the platform navigator
The IBM entitlement key is required for pulling images from IBM’s container registry but does not affect the visibility of Integration Runtimes.
If the entitlement key were missing, installation of operators might fail, but this does not directly cause the displayed message.
D. The API Connect operator has not been deployed
While API Connect is a component of CP4I, its operator is not required for all integration runtimes.
The error message suggests multiple runtimes are unavailable, which means the issue is more likely related to multiple missing operators, such as Aspera, DataPower, or MQ.
Key Reasons for This Issue:Why Other Options Are Incorrect:IBM Cloud Pak for Integration (CP4I) v2021.2 Administration References:
IBM Cloud Pak for Integration - Installing and Managing Operators
IBM Platform Navigator and Integration Runtimes
IBM MQ, DataPower, and Aspera Operators in CP4I
When upgrading Cloud Pak (or Integration and switching from Common Services (CS) monitoring to OpenShift monitoring, what command will check whether CS monitoring is enabled?
oc get pods -n ibm-common-services | grep monitoring
oc list pods -A | grep -i monitoring
oc describe pods/ibm-common-services | grep monitoring
oc get containers -A
When upgrading IBM Cloud Pak for Integration (CP4I) and switching from Common Services (CS) monitoring to OpenShift monitoring, it is crucial to determine whether CS monitoring is currently enabled.
The correct command to check this is:
sh
CopyEdit
oc get pods -n ibm-common-services | grep monitoring
This command (oc get pods -n ibm-common-services) lists all pods in the ibm-common-services namespace, which is where IBM Common Services (including monitoring components) are deployed.
Using grep monitoring filters the output to show only the monitoring-related pods.
If monitoring-related pods are running in this namespace, it confirms that CS monitoring is enabled.
B (oc list pods -A | grep -i monitoring) – Incorrect
The oc list pods command does not exist in OpenShift CLI. The correct command to list all pods across all namespaces is oc get pods -A.
C (oc describe pods/ibm-common-services | grep monitoring) – Incorrect
oc describe pods/ibm-common-services is not a valid OpenShift command. The correct syntax would be oc describe pod
D (oc get containers -A) – Incorrect
The oc get containers command is not valid in OpenShift CLI. Instead, oc get pods -A lists all pods, but it does not specifically filter monitoring-related services in the ibm-common-services namespace.
Explanation of Incorrect Options:IBM Cloud Pak for Integration (CP4I) v2021.2 Administration References:
IBM Documentation: Monitoring IBM Cloud Pak foundational services
IBM Cloud Pak for Integration: Disabling foundational services monitoring
OpenShift Documentation: Managing Pods in OpenShift
The OpenShift Logging Elasticsearch instance is optimized and tested for short term storage. Approximately how long will it store data for?
1 day
30 days
7 days
6 months
In IBM Cloud Pak for Integration (CP4I) v2021.2, OpenShift Logging utilizes Elasticsearch as its log storage backend. The default configuration of the OpenShift Logging stack is optimized for short-term storage and is designed to retain logs for approximately 7 days before they are automatically purged.
Performance Optimization: The OpenShift Logging Elasticsearch instance is designed for short-term log retention to balance storage efficiency and performance.
Default Curator Configuration: OpenShift Logging uses Elasticsearch Curator to manage the log retention policy, and by default, it is set to delete logs older than 7 days.
Designed for Operational Logs: The default OpenShift Logging stack is intended for short-term troubleshooting and monitoring, not long-term log archival.
Why is the retention period 7 days?If longer retention is required, organizations can:
Configure a different retention period by modifying the Elasticsearch Curator settings.
Forward logs to an external log storage system like Splunk, IBM Cloud Object Storage, or another long-term logging solution.
A. 1 day – Too short; OpenShift Logging does not delete logs on a daily basis by default.
B. 30 days – The default retention period is 7 days, not 30. A 30-day retention period would require manual configuration changes.
D. 6 months – OpenShift Logging is not optimized for such long-term storage. Long-term log retention should be managed using external storage solutions.
Why Other Options Are Incorrect:IBM Cloud Pak for Integration (CP4I) v2021.2 Administration References:
IBM Cloud Pak for Integration Logging and Monitoring
Red Hat OpenShift Logging Documentation
Configuring OpenShift Logging Retention Policy
What type of authentication uses an XML-based markup language to exchange identity, authentication, and authorization information between an identity provider and a service provider?
Security Assertion Markup Language (SAML)
IAM SSO authentication
lAMviaXML
Enterprise XML
Security Assertion Markup Language (SAML) is an XML-based standard used for exchanging identity, authentication, and authorization information between an Identity Provider (IdP) and a Service Provider (SP).
SAML is widely used for Single Sign-On (SSO) authentication in enterprise environments, allowing users to authenticate once with an identity provider and gain access to multiple applications without needing to log in again.
User Requests Access → The user tries to access a service (Service Provider).
Redirect to Identity Provider (IdP) → If not authenticated, the user is redirected to an IdP (e.g., Okta, Active Directory Federation Services).
User Authenticates with IdP → The IdP verifies user credentials.
SAML Assertion is Sent → The IdP generates a SAML assertion (XML-based token) containing authentication and authorization details.
Service Provider Grants Access → The service provider validates the SAML assertion and grants access.
How SAML Works:SAML is commonly used in IBM Cloud Pak for Integration (CP4I) v2021.2 to integrate with enterprise authentication systems for secure access control.
B. IAM SSO authentication → ❌ Incorrect
IAM (Identity and Access Management) supports SAML for SSO, but "IAM SSO authentication" is not a specific XML-based authentication standard.
C. IAM via XML → ❌ Incorrect
There is no authentication method called "IAM via XML." IBM IAM systems may use XML configurations, but IAM itself is not an XML-based authentication protocol.
D. Enterprise XML → ❌ Incorrect
"Enterprise XML" is not a standard authentication mechanism. While XML is used in many enterprise systems, it is not a dedicated authentication protocol like SAML.
Explanation of Incorrect Answers:
IBM Cloud Pak for Integration - SAML Authentication
Security Assertion Markup Language (SAML) Overview
IBM Identity and Access Management (IAM) Authentication
IBM Cloud Pak for Integration (CP4I) v2021.2 Administration References:
Which capability describes and catalogs the APIs of Kafka event sources and socializes those APIs with application developers?
Gateway Endpoint Management
REST Endpoint Management
Event Endpoint Management
API Endpoint Management
In IBM Cloud Pak for Integration (CP4I) v2021.2, Event Endpoint Management (EEM) is the capability that describes, catalogs, and socializes APIs for Kafka event sources with application developers.
Event Endpoint Management (EEM) allows developers to discover and consume Kafka event sources in a structured way, similar to how REST APIs are managed in an API Gateway.
It provides a developer portal where event-driven APIs can be exposed, documented, and consumed by applications.
It helps organizations share event-driven APIs with internal teams or external consumers, enabling seamless event-driven integrations.
Why "Event Endpoint Management" is the Correct Answer?
Why the Other Options Are Incorrect?Option
Explanation
Correct?
A. Gateway Endpoint Management
❌ Incorrect – Gateway endpoint management refers to managing API Gateway endpoints for routing and securing APIs, but it does not focus on event-driven APIs like Kafka.
❌
B. REST Endpoint Management
❌ Incorrect – REST Endpoint Management deals with traditional RESTful APIs, not event-driven APIs for Kafka.
❌
D. API Endpoint Management
❌ Incorrect – API Endpoint Management is a generic term for managing APIs but does not specifically focus on event-driven APIs for Kafka.
❌
Final Answer:✅ C. Event Endpoint Management
IBM Cloud Pak for Integration – Event Endpoint Management
IBM Event Endpoint Management Documentation
Kafka API Discovery & Management in IBM CP4I
What automates permissions-based workload isolation in Foundational Services?
The Operand Deployment Lifecycle Manager.
The NamespaceScope operator.
Node taints and pod tolerations.
The IAM operator.
The NamespaceScope operator is responsible for managing and automating permissions-based workload isolation in IBM Cloud Pak for Integration (CP4I) Foundational Services. It allows multiple namespaces to share common resources while maintaining controlled access, thereby enforcing isolation between workloads.
Enables namespace scoping, which helps define which namespaces have access to shared services.
Restricts access to specific components within an environment based on namespace policies.
Automates workload isolation by enforcing access permissions across multiple namespaces.
Ensures compliance with IBM Cloud security standards by providing a structured approach to multi-tenant deployments.
A. Operand Deployment Lifecycle Manager: Manages lifecycle and deployment of operands in IBM Cloud Paks but does not specifically handle workload isolation.
C. Node taints and pod tolerations: These are Kubernetes-level mechanisms to control scheduling of pods on nodes but do not directly automate permissions-based workload isolation.
D. The IAM operator: Manages authentication and authorization but does not specifically focus on namespace-based workload isolation.
Key Functions of the NamespaceScope Operator:Why Other Options Are Incorrect:IBM Cloud Pak for Integration (CP4I) v2021.2 Administration References:
IBM Documentation: NamespaceScope Operator
IBM Cloud Pak for Integration Knowledge Center
IBM Cloud Pak for Integration v2021.2 Administration Guide
The OpenShift Logging Operator monitors a particular Custom Resource (CR). What is the name of the Custom Resource used by the OpenShift Logging Opera-tor?
ClusterLogging
DefaultLogging
ElasticsearchLog
LoggingResource
In IBM Cloud Pak for Integration (CP4I) v2021.2, which runs on Red Hat OpenShift, logging is managed through the OpenShift Logging Operator. This operator is responsible for collecting, storing, and forwarding logs within the cluster.
The OpenShift Logging Operator monitors a specific Custom Resource (CR) named ClusterLogging, which defines the logging stack configuration.
The ClusterLogging CR is used to configure and manage the cluster-wide logging stack, including components like:
Fluentd (Log collection and forwarding)
Elasticsearch (Log storage and indexing)
Kibana (Log visualization)
Administrators define log collection, storage, and forwarding settings using this CR.
How the ClusterLogging Custom Resource Works:Example of a ClusterLogging CR Definition:apiVersion: logging.openshift.io/v1
kind: ClusterLogging
metadata:
name: instance
namespace: openshift-logging
spec:
managementState: Managed
logStore:
type: elasticsearch
retentionPolicy:
application:
maxAge: 7d
collection:
type: fluentd
This configuration sets up an Elasticsearch-based log store with Fluentd as the log collector.
The OpenShift Logging Operator monitors the ClusterLogging CR to manage logging settings.
It defines how logs are collected, stored, and forwarded across the cluster.
IBM Cloud Pak for Integration uses this CR when integrating OpenShift’s logging system.
Why Answer A (ClusterLogging) is Correct?
B. DefaultLogging → Incorrect
There is no such resource named DefaultLogging in OpenShift.
The correct resource is ClusterLogging.
C. ElasticsearchLog → Incorrect
Elasticsearch is the default log store, but it is managed within ClusterLogging, not as a separate CR.
D. LoggingResource → Incorrect
This is not an actual OpenShift CR related to logging.
Explanation of Incorrect Answers:
OpenShift Logging Overview
Configuring OpenShift Cluster Logging
IBM Cloud Pak for Integration - Logging and Monitoring
IBM Cloud Pak for Integration (CP4I) v2021.2 Administration References:
What is the result Of issuing the oc extract secret/platform—auth—idp—credentials --to=- command?
Writes the OpenShift Container Platform credentials to the current directory.
Generates Base64 decoded secrets for all Cloud Pak for Integration users.
Displays the credentials of the admin user.
Distributes credentials throughout the Cloud Pak for Integration platform.
The command:
oc extract secret/platform-auth-idp-credentials --to=-
is used to retrieve and display the admin user credentials stored in the platform-auth-idp-credentials secret within an OpenShift-based IBM Cloud Pak for Integration (CP4I) deployment.
In IBM Cloud Pak Foundational Services, the platform-auth-idp-credentials secret contains the admin username and password used to authenticate with OpenShift and Cloud Pak services.
The oc extract command decodes the secret and displays its contents in plaintext in the terminal.
The --to=- flag directs the output to standard output (STDOUT), ensuring that the credentials are immediately visible instead of being written to a file.
This command is commonly used for recovering lost admin credentials or retrieving them for automated processes.
Why Option C (Displays the credentials of the admin user) is Correct:
A. Writes the OpenShift Container Platform credentials to the current directory. → Incorrect
The --to=- option displays the credentials, but it does not write them to a file in the directory.
To save the credentials to a file, the command would need a filename, e.g., --to=admin-creds.txt.
B. Generates Base64 decoded secrets for all Cloud Pak for Integration users. → Incorrect
The command only extracts one specific secret (platform-auth-idp-credentials), which contains the admin credentials only.
It does not generate or decode secrets for all users.
D. Distributes credentials throughout the Cloud Pak for Integration platform. → Incorrect
The command extracts and displays credentials, but it does not distribute or propagate them.
Credentials distribution in Cloud Pak for Integration is handled through Identity and Access Management (IAM) configurations.
Explanation of Incorrect Answers:
IBM Cloud Pak Foundational Services - Retrieving Admin Credentials
OpenShift CLI (oc extract) Documentation
IBM Cloud Pak for Integration Identity and Access Management
IBM Cloud Pak for Integration (CP4I) v2021.2 Administration References:

TESTED 19 Feb 2026

