Which role must be assigned to DevOps users who need access to deploy Container and Host Defenders in Compute?
How does assigning an account group to an administrative user on Prisma Cloud help restrict access to resources?
Which two proper agentless scanning modes are supported with Prisma Cloud? (Choose two).
Which three fields are mandatory when authenticating the Prisma Cloud plugin in the IntelliJ application? (Choose three.)
Which action would be applicable after enabling anomalous compute provisioning?
An administrator wants to enforce a rate limit for users not being able to post five (5) .tar.gz files within five (5) seconds.
What does the administrator need to configure?
Console is running in a Kubernetes cluster, and Defenders need to be deployed on nodes within this cluster.
How should the Defenders in Kubernetes be deployed using the default Console service name?
Which three Orchestrator types are supported when deploying Defender? (Choose three.)
Which of the following is not a supported external integration for receiving Prisma Cloud Code Security notifications?
Which type of query is used for scanning Infrastructure as Code (laC) templates?
An administrator has deployed Console into a Kubernetes cluster running in AWS. The administrator also has configured a load balancer in TCP passthrough mode to listen on the same ports as the default Prisma Compute Console configuration.
In the build pipeline, the administrator wants twistcli to talk to Console over HTTPS. Which port will twistcli need to use to access the Prisma Compute APIs?
The compliance team needs to associate Prisma Cloud policies with compliance frameworks. Which option should the team select to perform this task?
Which report includes an executive summary and a list of policy violations, including a page with details for each policy?
While writing a custom RQL with array objects in the investigate page, which type of auto-suggestion a user can leverage?
Which two bot categories belong to unknown bots under Web-Application and API Security (WAAS) bot protection? (Choose two.)
Which three AWS policy types and identities are used to calculate the net effective permissions? (Choose three).
Which two actions are required in order to use the automated method within Amazon Web Services (AWS) Cloud to streamline the process of using remediation in the identity and access management (IAM) module? (Choose two.)
Given the following JSON query:
$.resource[*].aws_s3_bucket exists
Which tab is the correct place to add the JSON query when creating a Config policy?
Which two integrated development environment (IDE) plugins are supported by Prisma Cloud as part of its Code Security? (Choose two.)
A customer wants to monitor the company’s AWS accounts via Prisma Cloud, but only needs the resource configuration to be monitored for now.
Which two pieces of information do you need to onboard this account? (Choose two.)
A business unit has acquired a company that has a very large AWS account footprint. The plan is to immediately start onboarding the new company’s AWS accounts into Prisma Cloud Enterprise tenant immediately. The current company is currently not using AWS Organizations and will require each account to be onboarded individually.
The business unit has decided to cover the scope of this action and determined that a script should be written to onboard each of these accounts with general settings to gain immediate posture visibility across the accounts.
Which API endpoint will specifically add these accounts into the Prisma Cloud Enterprise tenant?
A customer wants to harden its environment from misconfiguration.
Prisma Cloud Compute Compliance enforcement for hosts covers which three options? (Choose three.)
A customer has multiple violations in the environment including:
User namespace is enabled
An LDAP server is enabled
SSH root is enabled
Which section of Console should the administrator use to review these findings?
What factor is not used in calculating the net effective permissions for a resource in AWS?
Which three options for hardening a customer environment against misconfiguration are included in Prisma Cloud Compute compliance enforcement for hosts? (Choose three.)
A customer has configured the JIT, and the user created by the process is trying to log in to the Prisma Cloud console. The user encounters the following error message:
What is the reason for the error message?
The security team wants to protect a web application container from an SQLi attack. Which type of policy should the administrator create to protect the container?
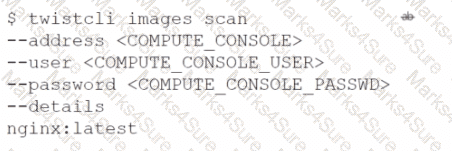
Which command should be used in the Prisma Cloud twistcli tool to scan the nginx:latest image for vulnerabilities and compliance issues?
A)
B)

C)
D)
An administrator of Prisma Cloud wants to enable role-based access control for Docker engine.
Which configuration step is needed first to accomplish this task?
Which three steps are involved in onboarding an account for Data Security? (Choose three.)
Which two bot types are part of Web Application and API Security (WAAS) bot protection? (Choose two.)
A customer wants to scan a serverless function as part of a build process. Which twistcli command can be used to scan serverless functions?
You have onboarded a public cloud account into Prisma Cloud Enterprise. Configuration Resource ingestion is visible in the Asset Inventory for the onboarded account, but no alerts are being generated for the configuration assets in the account.
Config policies are enabled in the Prisma Cloud Enterprise tenant, with those policies associated to existing alert rules. ROL statements on the investigate matching those policies return config resource results successfully.
Why are no alerts being generated?
In which two ways can Prisma Cloud images be retrieved in Prisma Cloud Compute Self-Hosted Edition? (Choose two.)
The security team wants to target a CNAF policy for specific running Containers. How should the administrator scope the policy to target the Containers?
A customer has serverless functions that are deployed in multiple clouds.
Which serverless cloud provider is covered be “overly permissive service access” compliance check?
A customer is interested in PCI requirements and needs to ensure that no privilege containers can start in the environment.
Which action needs to be set for “do not use privileged containers”?
Per security requirements, an administrator needs to provide a list of people who are receiving e-mails for Prisma Cloud alerts.
Where can the administrator locate this list of e-mail recipients?
Which intensity setting for anomaly alerts is used for the measurement of 100 events over 30 days?
A customer has a requirement to restrict any container from resolving the name www.evil-url.com.
How should the administrator configure Prisma Cloud Compute to satisfy this requirement?
Which IAM Azure RQL query would correctly generate an output to view users who have sufficient permissions to create security groups within Azure AD and create applications?
Prisma Cloud Compute has been installed on Onebox. After Prisma Cloud Console has been accessed. Defender is disconnected and keeps returning the error "No console connectivity" in the logs.
What could be causing the disconnection between Console and Defender in this scenario?
Which type of compliance check is available for rules under Defend > Compliance > Containers and Images > CI?
On which cloud service providers can you receive new API release information for Prisma Cloud?
Which of the below actions would indicate – “The timestamp on the compliance dashboard?
A security team has been asked to create a custom policy.
Which two methods can the team use to accomplish this goal? (Choose two.)
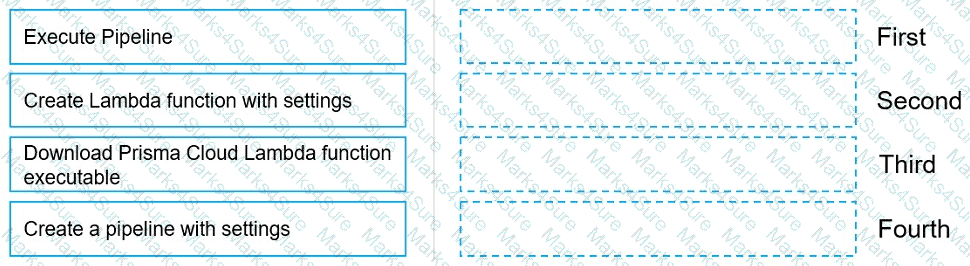
Move the steps to the correct order to set up and execute a serverless scan using AWS DevOps.
Which three serverless runtimes are supported by Prisma Cloud for vulnerability and compliance scans? (Choose three.)
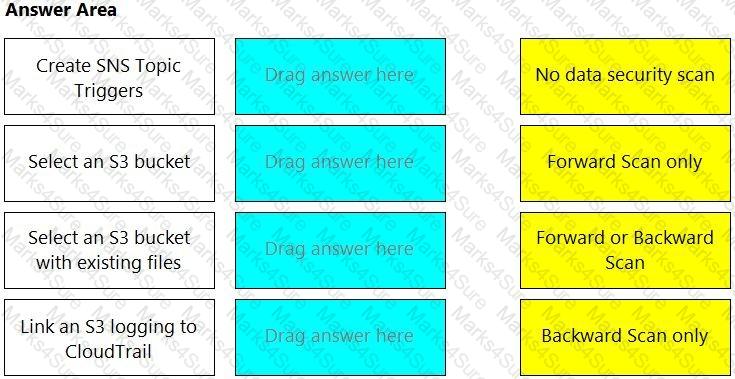
Match the correct scanning mode for each given operation.
(Select your answer from the pull-down list. Answers may be used more than once or not at all.)
An S3 bucket within AWS has generated an alert by violating the Prisma Cloud Default policy “AWS S3 buckets are accessible to public”. The policy definition follows:
config where cloud.type = 'aws' AND api.name='aws-s3api-get-bucket-acl' AND json.rule="((((acl.grants[? (@.grantee=='AllUsers')] size > 0) or policyStatus.isPublic is true) and publicAccessBlockConfiguration does not exist) or ((acl.grants[?(@.grantee=='AllUsers')] size > 0) and publicAccessBlockConfiguration.ignorePublicAcis is false) or (policyStatus.isPublic is true and publicAccessBlockConfiguration.restrictPublicBuckets is false)) and websiteConfiguration does not exist"
Why did this alert get generated?
When configuring SSO how many IdP providers can be enabled for all the cloud accounts monitored by Prisma Cloud?
An administrator has access to a Prisma Cloud Enterprise.
What are the steps to deploy a single container Defender on an ec2 node?
The InfoSec team wants to be notified via email each time a Security Group is misconfigured. Which Prisma Cloud tab should you choose to complete this request?
A Systems Engineer is the administrator of a self-hosted Prisma Cloud console. They upgraded the console to the latest version. However, after the upgrade, the console does not show all the policies configured. Before they upgraded the console, they created a backup manually and exported it to a local drive. Now they have to install a Prisma Cloud to restore from the backup that they manually created. Which Prisma Cloud version can they can restore with the backup?
What will happen when a Prisma Cloud Administrator has configured agentless scanning in an environment that also has Host and Container Defenders deployed?
An administrator has been tasked with a requirement by your DevSecOps team to write a script to continuously query programmatically the existing users, and the user’s associated permission levels, in a Prisma Cloud Enterprise tenant.
Which public documentation location should be reviewed to help determine the required attributes to carry out this step?
In Azure, what permissions need to be added to Management Groups to allow Prisma Cloud to calculate net effective permissions?
Which three options are selectable in a CI policy for image scanning with Jenkins or twistcli? (Choose three.)
Which three types of classifications are available in the Data Security module? (Choose three.)