A systems engineer has been tasked by management to provide a recommendation with a prioritized, focused set of actions to help the organization stop high-risk cyber attacks and ensure data security. What should the systems engineer recommend the organization use to accomplish this?
When considering Defense in Depth (DiD) as part of a network’s architectural design, what is the FIRST layer in a multi-layered defensive strategy?
A software development vendor wants to test the Application Programming Interface (API). The testers use and manipulate data to identify the various states of the application behavior. What is the kind of testing that is being used?
An organization has hired a consultant to establish their Identity and Access Management (IAM) system. One of the consultant’s main priorities will be to understand the current state and establish visibility across the environment. How can the consultant start to establish an IAM governance process?
What is the BEST protection method to ensure that an unauthorized entry attempt would fail when securing highly sensitive areas?
An organization is concerned that if an employee’s mobile device is lost or stolen and does not reconnect to the carrier network, the data on the device may still be at risk. Consequently, the organization has implemented a control on all mobile devices to require an eight-character passcode for unlock and login. What should happen after multiple incorrect passcode attempts?
A hot Disaster Recovery (DR) data center is the victim of a data breach. The hackers are able to access and copy 10GB of clear text confidential information. Which of the following could have decreased the amount of exposure from this data breach?
A part is sold as a service part, and It is also used as a component In another part. Which of the following statements about the planning for this part is true?
A company implementing a localized multi-country strategy to increase market share should engage in which of the following actions?
Which security audit phase is MOST important to ensure correct controls are applied to classified data in a production environment?
A low-cost provider strategy works best when which of the following conditions are met?
An organizations is developing a new software package for a financial institution. What is the FIRST step when modeling threats to this new software package?
Which of the following documents is the BEST reference to describe application functionality?
An attacker wants to decrypt a message and has no knowledge of what may have been in the original message. The attacker chooses to use an attack that will exhaust the keyspace in order to decrypt the message. What type of cryptanalytic attack is the attacker using?
The costs provided in the table below are associated with buying a quantity larger than immediately needed. What Is the total landed cost based on this table?
Cost CategoryCost
Custom fees$125
Freight$700
Warehouse rent$200
Matenal cost$500
Which of the following tools is used to evaluate the impact that a production plan has on capacity?
After a recent cybersecurity incident, a manufacturing organization is interested in further hardening its Identity and Access Management (IAM) solution. Knowing that the organization limits the use of personal devices in the facility, which could BEST be implemented to enhance the manufacturing organization's IAM solution?
Health information stored in paper form may be destroyed using which of the following methods?
An agency has the requirement to establish a direct data connection with another organization for the purpose of exchanging data between the agency and organization systems. There is a requirement for a formal agreement between the agency and organization. Which source of standards can the system owners use to define the roles and responsibilities along with details for the technical and security requirements?
An organization implemented a threat modeling program focusing on key assets. However, after a short time it became clear that the organization was having difficulty executing the threat modeling program.
Which approach will MOST likely have been easier to execute?
A security officer has been tasked with performing security assessments on the organization’s in the current calendar year. While collecting data, the officer realizes that more than one business until will be engaged in the assessment. What activity MUST be included in the data collection phase?
Which of the following criteria is used to determine safety stock in a distribution center (DC)?
An organization’s computer incident responses team PRIMARY responds to which type of control?
A security analyst has been asked to build a data retention policy for a hospital. What is the FIRST action that needs to be performed in building this policy?
A health care organization's new cloud-based customer-facing application is constantly receiving security events from dubious sources. What BEST describes a security event that compromises the confidentiality, integrity or availability of the application and data?
An organization wishes to utilize a managed Domain Name System (DNS) provider to reduce the risk of users accessing known malicious sites when web browsing. The organization operates DNS forwarders that forward queries for all external domains to the DNS provider. Which of the following techniques could enable the organization to identify client systems that have attempted to access known malicious domains?
In preparing for a facility location decision, proximity to suppliers would be classified as which kind of criteria?
Additional requirements that are outside the original design are being added to a project, increasing the timeline and cost of the project.
What BEST describes the requirement changes that are happening?
In conducting a new corporate payroll system security review, which of the following individuals should answer questions regarding the data classification?
An organization discovered that malicious software was installed on an employee’s work laptop and allowed a competing vendor to access confidential files. The employee was fully aware of the policy not to install unauthorized software on the organization laptop. What is the BEST automated security practice for an organization to implement to avoid this situation?
In times of monetary inflation, which of the following methods of inventory valuation results in the greatest cost of sales for the early years of a particular product?
A manufacturer has a forecasted annual demand of 1,000,000 units for a new product. They have to choose 1 of 4 new pieces of equipment to produce this product. Assume that revenue will be $10 per unit for all 4 options.
Which machine will maximize their profit if the manufacturer anticipates market demand will be steady for 3 years and there is no residual value for any of the equipment choices?
MachineFixed CostVariable Cost per UnitAnnual Capacity
AS100.000$6 00800,000 units
B$200,000$5 501.000,000 units
C$250,000$5 001,200,000 units
D$1 000.000$4 501 400.000 units
The Data Loss Prevention (DLP) team in a major financial institution discovered network traffic that involved movement of sensitive material to a Cloud Service Provider (CSP). What action should be taken FIRST in this situation?
A security engineer needs to perform threat modeling on a microprocessor design for an Internet of Things (IoT) application. Using the MITRE Common Weakness Enumeration (CWE) catalog for hardware, a risk analysis is performed. What kind of threat modeling approach would be BEST to identify entry points into the system based on motivation?
After a data loss event, an organization is reviewing its Identity and Access Management (IAM) governance process. The organization determines that the process is not operating effectively. What should be the FIRST step to effectively manage the IAM governance process?
A forecasting method that responds slowly to changes in demand would be most appropriate when the historical demand pattern shows a:
The demand for an item has increasing forecast error, whereas all other factors remain constant. Which of the following remains constant while maintaining the same customer service level?
Which is the MOST valid statement around the relationship of security and privacy?
Company A has acquired Company B. Company A has decided to start a project to convert Company B's enterprise resource planning (ERP) software to the same ERP software that Company A uses. What is a likely reason for this decision?
Which of the following is the MOST effective practice for tracking organizational assets when removed from the premises?
Which of the following BEST describes the responsibility of an information System Security Officer?
A security specialist is responsible to improve the security awareness program of a medium-sized organization and is tasked to track blocked targeted attacks. Which of the following BEST describes the outcome of the security specialist’s use of metrics for this task?
Which of the below represents the GREATEST cloud-specific policy and organizational risk?
Which of the following is the GREATEST threat for a Border Gateway Protocol (BGP) deployment on the internet?
Which of the following is MOST accurate when comparing patch management and vulnerability management?
A cybersecurity analyst is reviewing a recent incident in which the adversaries were able to move vertically within the network. Which attack phase MOST clearly represents this scenario?
Which of the following should be done FIRST when implementing an Identity and Access Management (IAM) solution?
Which of the following BEST defines whether an organization can consider an alternate location during a contingency?
A logistics manager Is faced with delivering an order via rail or truck. Shipping via rail costs S300 and takes 14 days. Shipping via truck costs $600 and takes 3 days. If the holding cost is $40 per day, what is the cost to deliver the order?
Which of the following techniques is BEST suited to preserve the confidentiality of a system’s data?
Which of the following mechanisms should a practitioner focus on for the MOST effective information security continuous monitoring?
Which of the following is a core subset of The Open Group Architecture Framework (TOGAF) enterprise architecture model?
A company selling seasonal products is preparing their sales and operations plan for the coming year. Their current labor staffing is at the maximum for their production facility and cannot meet the forecasted demand. The business plan shows they do not have the financial capability to add to the production facility. Which of the following actions would be most appropriate?
A security team leader needs to communicate the value of the security program. As the security team leader determines the return on security investments, what is the MOST important aspect to incorporate?
Which of the following tactics can be employed effectively to reduce appraisal quality costs?
While doing a penetration test, auditors found an old credential hash for a privileged user. To prevent a privileged user's hash from being cached, what is the MOST appropriate policy to mandate?
What is a strategic process that is aimed at considering possible attack scenarios and vulnerabilities within a proposed or existing application environment for the purpose of clearly identifying risk and impact levels?
A large organization is planning to lay off half of its staff. From an information security point of view, what is the BEST way of approaching affected staff?
A newer automotive supplier has not fully developed its information technology (IT) systems. The supplier has Just received a contract from a large automotive manufacturer which requires the supplier to use electronic data interchange (EDI) transactions for receiving orders, sending advance ship notices (ASNs), and receiving invoice payments. What strategy can the supplier adopt to immediately meet the EDI requirements?
A security engineer has determined the need to implement preventative controls into their Wireless Local Area Network (WLAN) for added protection. Which preventative control provides the MOST security?
An organization’s external auditors have issued a management letter identifying significant deficiencies related to the effectiveness of the previous year’s global access certification. The organization wants to move from a department-based access control system to a Role-Based Access Control (RBAC) system. In addition to quickly and securely provisioning users by granting membership into predefined and approved roles, which of these presents the BEST reason to do so?
Which of the following controls should a financial Institution have in place in order to prevent a trader from both entering and executing a trade?
Which of the following states of data becomes MOST important to protect as organizations continue to transition toward Application Programming Interface (API)-based solutions?
Objective security metrics tend to be easier to gather, easier to interpret, and easier to include in reports to management.
What is the BEST objective metric for the effectiveness of a security awareness training?
Which of the following planning modules considers the shortest-range planning goals?
The development team wants new commercial software to integrate into the current system. What steps can the security office take to ensure the software has no vulnerabilities?
Which of the following ports needs to be open for Kerberos Key Distribution Center (KDC) to function properly?
A security engineer is responsible for verifying software reliability prior to commercial deployment. Which of the following factor would BEST be verified to ensure that the software stays reliable?
An organization is retiring an old server out of the data center. This server was used to store and process sensitive information. The server is being sent off-site to a recycling center. Which declassification method should be performed prior to it being sent off-site?
An organization wants to ensure the security of communications across its environment. What is the BEST way to provide confidentiality of data from handheld wireless devices to the internal network?
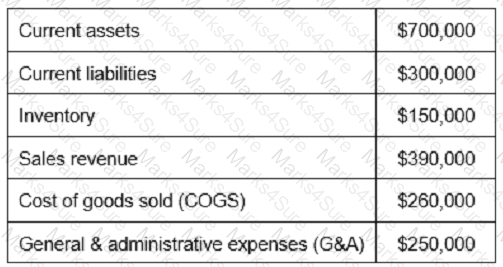
Based on the values reported in the table below, what is the inventory turnover?
A lengthy power outage led to unavailability of time critical services resulting in considerable losses. It was determined that a backup electrical generator did not work as intended at the time of the incident due to lack of fuel. What should the security consultant FIRST Investigate?
An organization wants to ensure a risk does not occur. The action taken is to eliminate the attack surface by uninstalling vulnerable software. Which risk response strategy did the organization take?
Which of the following BEST characterizes the operational benefit of using immutable workloads when working on a cloud-based project?
The project manager for a new application development is building a test framework. It has been agreed that the framework will Include penetration testing; however, the project manager is keen to identify any flaws prior to the code being ready for execution. Which of the following techniques BEST supports this requirement?
Which of the following may authorize an organization to monitor an employee’s company computer and phone usage?
After a recent threat modeling workshop, the organization has requested that the Chief Information Security Officer (CISO) implement zero trust (ZT) policies. What was the MOST likely threat identified in the workshop?
A warehouse manager assigns orders to warehouse personnel grouped by where the goods are stored. This type of picking is called a(n):
An organization co-locates three divisions and merges them into one network infrastructure. Prior to the merge, the network manager issued devices to employees for remote login. What security concept should be observed to provide security when a device joins the network or when a client makes an Application Programming Interface (API) call?
A security specialist is responsible to improve the security awareness program of a medium-sized organization and tasked to track blocked targeted attacks. Which of the following BEST describes the outcome of the security specialist’s use of metrics for this task?
A security engineer is reviewing Incident Response (IR) roles and responsibilities. Several roles have static elevated privileges in case an incident occurs. Instead of static access, what is the BEST access method to manage elevated privileges?
Which of the following BEST describes web service security conformance testing as it relates to web services security testing?
A web application is found to have SQL injection (SQLI) vulnerabilities. What is the BEST option to remediate?
Which security concept applies if an architecture diagram illustrates a particular user/role combination with access to an asset or applicaton?
A security practitioner has been asked to investigate the presence of customer Personally Identifiable Information (PII) on a social media website. Where does the practitioner begin?
An organization processes healthcare data, stores credit card data, and must provide audited financial statements, each of which is controlled by a separate compliance standard. To support compliance against multiple standards and the testing of the greatest number of controls with a limited budget, how would the internal audit team BEST audit the organization?
Remote sensors have been deployed at a utility site to reduce overall response times for maintenance staff supporting critical infrastructure. Wireless communications are used to communicate with the remote sensors, as it is the most cost-effective method and minimizes risk to public health and safety. The utility organization has deployed a Host-Based Intrusion Prevention System (HIPS) to monitor and protect the sensors. Which statement BEST describes the risk that is mitigated by utilizing this security tool?
An organization recently created a new accounting department, and that department is critical in the event of a disaster for the operations to continue. Which steps should the organization take to create a Business Continuity Plan (BCP)?
Which of the following methods places a replenishment order when the quantity on hand falls below a predetermined level?
Capacity requirements planning (CRP) is applicable primarily In companies operating In an environment where:
Plans are being made to move an organization’s software systems to the cloud in order to utilize the flexibility and scalability of the cloud. Some of these software systems process highly sensitive data. The organization must follow strict legal requirements regarding the location of the highly sensitive data processed by the software systems. Which cloud model will BEST fit the organization’s requirements?
A multinational organization acquires a subsidiary. The acquisition results in the need to integrate a large population of new users into the organization's corporate cloud. What is the MAIN benefit of the organization's Federated Identity Management (FIM) system to address the need?
The trade-off of increasing safety stock to improve customer fill rate would be a decrease in:
Which of the following BEST effective when protecting against insider threats?
Which technology is BEST suited to establish a secure communications link between an individual’s home office and the organization’s Local Area Network (LAN)?
The time spent In queue by a specific manufacturing job is determined by which of the following factors related to the order?
When conducting a vulnerability test using a scanner tool, which unintended consequence can occur?
The question below is based on the following standard and actual data of a production order
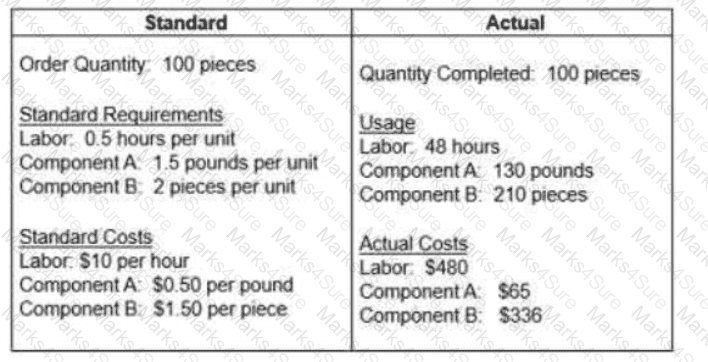
Which of the following statements about variances is true?
An organization’s security team is looking at ways to minimize the security risk of the container infrastructure. The lead engineer needs to select a suite of remediation actions to minimize risks. Which programmatic approach will result in preventing, detecting , and responding to the GREATEST number of threats aimed at container operations?
In order to meet retention requirements, it may be necessary to migrate digital records to different media because of which of the following issues?
An effective approach to projecting requirements for materials with long lead times Includes which of the following options?
Which of the following provides for continuous improvement of the change control process?
A newly hired Chief Information Security Officer (CISO) is now responsible to build a third-party assurance for their organization. When assessing a third-party, which of the following questions needs to be answered?
A third-party vendor is procured to conduct a non-financial audit. Which report evaluates the effectiveness of the controls?
In a make-to-stock (MTS) environment, the master production schedule (MPS) Is usually a schedule of which of the following types of items?
During an investigation, a forensic analyst executed a task to allow for the authentication of all documents, data, and objects collected, if required. Which of the options below BEST describes this task?
An organization is designing a new Disaster Recovery (DR) site. What is the BEST option to harden security of the site?
What FIRST step should a newly appointed Data Protection Officer (DPO) take to develop an organization's regulatory compliance policy?
Which of the following sampling techniques is BEST suited for comprehensive risk assessments?
The Chief Information Security Officer (CISO) defined a requirement to install a network security solution that will have the ability to inspect and block data flowing over network in real time. What network deployment scenario will be MOST suitable?
When performing threat modeling using Spoofing, Tampering, Repudiation, Information Disclosure, Denial Of Service, And Elevation of Privilege (STRIDE), which of the following is an example of a repudiation threat?
When a third-party needs to receive privileged information, which of the following would be the BEST to
transport the data?
Following the go-live of a new financial software, an organization allowed the Information Technology (IT) officer to maintain all rights and access permissions to help the organization staff should they have challenges in their day-to-day work. What is the BEST way to categorize the situation?
During a threat modeling exercise using the Spoofing, Tampering, Repudiation, Information Disclosure, Denial of Service, and Elevation of Privilege (STRIDE) framework, it was identified that a web server allocates a socket and forks each time it receives a request from a user without limiting the number of connections or requests.
Which of the following security objectives is MOST likely absent in the web server?
In a large organization, the average time for a new user to receive access is seven days. Which of the following is the BEST enabler to shorten this time?
Which of the following is a threat modeling methodology used for accessing threats against applications and Operating Systems (OS)?
A manufacturer begins production of an item when a customer order is placed. This is an example of a(n):
As the organization requires user friendly access to a new web-based application, a software developer decides to implement Single Sign-On (SSO). The developer uses the de-facto standard for web-based applications and the implementation includes the use of a JavaScript Object Notation (JSON) web token. With this information, which is the BEST way for the software developer to establish SSO capability?
An organization is implementing Zero Trust Network Access (ZTNA) and needs a strategy to measure device trust for employee laptops. Which measurement strategy is BEST suited and why?
A cybersecurity professional has been tasked with instituting a risk management function at a new organization. Which of the following is the MOST important step the professional should take in this endeavor?
The development team wants new commercial software to Integrate into the current systems. What steps can the security office take to ensure the software has no vulnerabilities?
An infrastructure team is setting up a wireless network for employees at a new location of the organization that is located near a very busy city transport hub. Which should be the MOST important antenna consideration with regard to securing the wireless network for the infrastructure team?
An organization is opening a new data center and is looking for a facilities security officer to provide best practices for the site and facility design. The two major requirements for this organization are not to attract undue attention and avoid proximity to potentially hazardous sites.
What site selection considerations do these requirements BEST fall under when deciding on the location for a facility?
For a company that uses first in, first out (FIFO) inventory accounting, the actual use in production of a recently arrived shipment of more expensive components rather than lower-cost components
previously received will have which of the following results?
Network Access Control (NAC) is used to perform what function for computers joining the network?
The question below is based on the following alternative schedules for a lot of 1,200.
A company works 8-hour, single-shift days. Setups are 4 hours for Operation 20 and 4 hours for Operation 40. Each operation has multiple machines available.
Which of the following statements is correct?
An information security professional is tasked with configuring full disk encryption on new hardware equipped with a Trusted Platform Module (TPM). How does TPM further enhance the security posture of full disk encryption if configured properly?
An organization has a legacy application used in production. Security updates are no longer provided, which makes the legacy application vulnerable. The legacy application stores Social Security numbers and credit card numbers. Which actions will BEST reduce the risk?
Which of the following actions best supports a company's strategic focus on delivery speed to improve competitive advantage?
A company has the following production conditions:
Batch size: 1,000 items
Processing time: 4 minutes per item
Setup time: 2 hours
Utilization: 80%
Efficiency: 80%
Which of the following actions would result in the work being done in the least amount of time?
A potentially life-threatening vulnerability is found in vendor software that is used to manage critical systems. Which of the following is generally considered the BEST method to disclose the vulnerability from an ethical hacking perspective?
What is the process when a security assessor compiles potential targets from the attacker’s perspective, such as data flows, and interactions with users?
Who is responsible for ensuring compliance when an organization uses a cloud provider to host its Virtual Machine (VM) instances?
Labor3 people
Work hours10 hours per day
Days4 days per week
Meetings with work area employees1/2 hour per day
Work area efficiency85%
Given the information above, what is the weekly theoretical capacity of this work area in hours?
Which of the physiological biometric scanning methods is considered the MOST invasive?
Which of the following MUST be checked during the validation of software verification capabilities?
A security consultant is working with an organization to help evaluate a proposal received from a new managed security service provider. There are questions about the confidentiality and effectiveness of the provider's system over a period of time. Which of the following System And Organization Controls (SOC) report types should the consultant request from the provider?
If the total part failure rate of a machine is 0.00055 failures per hour, what would be the mean time between failures (MTBF) in hours?
An organization has a call center that uses a Voice Over Internet Protocol (VoIP) system. The conversations are sensitive, and the organization is concerned about employees other than the call agents accessing these conversations. What is the MOST effective additional security measure to make?
The question below is based on the following information:
Beginning inventory = 43Week 1Week 2Week 3
Forecast202020
Customer orders221710
Projected on-hand
Master production schedule (MPS)80
Available-to-promise (ATP)
What is the largest customer order that could be accepted for delivery at the end of week 3 without making changes to the master production schedule (MPS)?
Which of the following production activity control (PAC) techniques focuses on optimizing output?
We have observed the inventory system does not handle plastic parts well." What should be added to the problem statement to make it more useful?
A company confirms a customer order based on available capacity and inventory, even though the current production plan does not cover the entire order quantity. This situation is an example of what type of order fulfillment policy?
An organization decides to conduct penetration testing. Senior management is concerned about the potential loss of information through data exfiltration. The organization is currently preparing a major product launch that is time-sensitive. Which of the following methods of testing is MOST appropriate?
Which of the following statements is an advantage of a fourth-party logistics (4PL) provider?
Which of the following is an access control method that organizations can use to prevent unauthorized access?
Which of the following Internet Protocol Security (IPSec) components provides the MOST confidentiality for the information that is being transmitted?
An organization needs a firewall that maps packets to connections and uses Transmission Control Protocol/Internet Protocol (TCP/IP) header fields to keep track of connections. Which type of firewall will be recommended?
What is the BEST way to plan for power disruptions when implementing a Disaster Recovery Plan (DRP)?
Which of the following provides that redundancy and failover capabilities are built into a system to maximize its uptime?
Price negotiation is most appropriate when purchasing which of the following product categories?
Payment Card Industry Data Security Standard (PCI DSS) allows for scanning a statistical sample of the environment without scanning the full environment. Scanning a statistical sample has many advantages and disadvantages.
Which of the following is the MOST accurate set of advantages and disadvantages?