Will this command ensure that overlay traffic between service tasks is encrypted?
Solution.docker network create -d overlay --secure
Is this statement correct?
Solution.A Dockerfile stores persistent data between deployments of a container
Two development teams in your organization use Kubernetes and want to deploy their applications while ensuring that Kubernetes-specific resources, such as secrets, are grouped together for each application.
Is this a way to accomplish this?
Solution: Add all the resources to the default namespace.
Your organization has a centralized logging solution, such as Splunk.
Will this configure a Docker container to export container logs to the logging solution?
Solution: docker logs
Will this Linux kernel facility limit a Docker container's access to host resources, such as CPU or memory?
Solution: namespaces
Does this command display all the pods in the cluster that are labeled as 'env: development'?
Solution: 'kubectl get pods --all-namespaces -label env=development'
Will this Linux kernel facility limit a Docker container's access to host resources, such as CPU or memory?
Solution: cgroups
Are these conditions sufficient for Kubernetes to dynamically provision a persistentVolume, assuming there are no limitations on the amount and type of available external storage?
Solution: A persistentVolumeClaim is created that specifies a pre-defined storageClass.
Which networking drivers allow you to enable multi-host network connectivity
between containers?
Does this command display all the pods in the cluster that are labeled as env; development'?
Solution. ‘kubectl gel pods --all-namespaces -I 'env in (development)''
One of several containers in a pod is marked as unhealthy after failing its livenessProbe many times. Is this the action taken by the orchestrator to fix the unhealthy container?
Solution: Kubernetes automatically triggers a user-defined script to attempt to fix the unhealthy container.
In Docker Trusted Registry, is this how a user can prevent an image, such as 'nginx:latest’, from being overwritten by another user with push access to the repository?
Solution: Keep a backup copy of the image on another repository.
A company's security policy specifies that development and production containers must run on separate nodes in a given Swarm cluster.
Can this be used to schedule containers to meet the security policy requirements?
Solution: node affinities
You are troubleshooting a Kubernetes deployment called api, and want to see the events table for this object. Does this command display it?
Solution: kubectl events deployment api
The Kubernetes yaml shown below describes a clusterIP service.
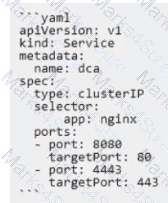
Is this a correct statement about how this service routes requests?
Solution: Traffic sent to the IP of this service on port 80 will be routed to port 8080 in a random pod with the label app:
nginx.
Will this command mount the host's '/data' directory to the ubuntu container in read-only mode?
Solution: 'docker run --add-volume /data /mydata -read-only ubuntu'
The following Docker Compose file is deployed as a stack:
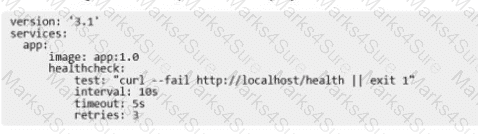
Is this statement correct about this health check definition?
Solution: Health checks test for app health five seconds apart. If the test fails, the container will be restarted three times before it gets rescheduled.
Will a DTR security scan detect this?
Solution.image configuration poor practices, such as exposed ports or inclusion of compilers in production images
An application image runs in multiple environments, with each environment using different certificates and ports.
Is this a way to provision configuration to containers at runtime?
Solution: Create a Dockerfile for each environment, specifying ports and ENV variables for certificates.
Does this command create a swarm service that only listens on port 53 using the UDP protocol?
Solution. ‘docker service create -name dns-cache -p 53:53/udp dns-cache"
Will this Linux kernel facility limit a Docker container's access to host resources, such as CPU or memory?
Solution.capabilities
A company's security policy specifies that development and production containers must run on separate nodes in a given Swarm cluster. Can this be used to schedule containers to meet the security policy requirements?
Solution.label constraints
Will This command list all nodes in a swarm cluster from the command line?
Solution. ‘docker swarm nodes'
Will this sequence of steps completely delete an image from disk in the Docker Trusted Registry?
Solution: Manually delete all layers used by the image on the disk from the Docker Trusted Registry.
Two development teams in your organization use Kubernetes and want to deploy their applications while ensuring that Kubernetes-specific resources, such as secrets, are grouped together for each application.
Is this a way to accomplish this?
Solution: Create one namespace for each application and add all the resources to it.
Is this the purpose of Docker Content Trust?
Solution.Indicate an image on Docker Hub is an official image.
The Kubernetes yaml shown below describes a networkPolicy.
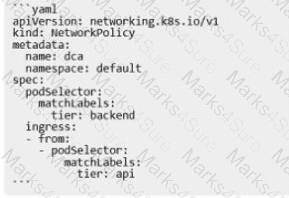
Will the networkPolicy BLOCK this trafftc?
Solution. a request issued from a pod bearing only the tier: frontend label, to a pod bearing the tier: backend label
Your organization has a centralized logging solution, such as Sptunk.
Will this configure a Docker container to export container logs to the logging solution?
Solution.docker system events- -filter splunk
Will this command list all nodes in a swarm cluster from the command line?
Solution. ‘docker inspect nodes
Will this configuration achieve fault tolerance for managers in a swarm?
Solution: one manager node for two worker nodes
Is this a type of Linux kernel namespace that provides container isolation?
Solution: Network
Is this an advantage of multi-stage builds?
Solution: better caching when building Docker images
You want to provide a configuration file to a container at runtime. Does this set of Kubernetes tools and steps accomplish this?
Solution: Turn the configuration file into a configMap object, use it to populate a volume associated with the pod, and mount that file from the volume to the appropriate container and path.
Will this configuration achieve fault tolerance for managers in a swarm?
Solution: only two managers, one active and one passive.
Will this Linux kernel facility limit a Docker container's access to host resources, such as CPU or memory?
Solution: seccomp
Is this a type of Linux kernel namespace that provides container isolation?
Solution: Storage
Does this command create a swarm service that only listens on port 53 using the UDP protocol?
Solution: ‘docker service create -name dns-cache -p 53:53 -service udp dns-cache'
Is this a type of Linux kernel namespace that provides container isolation?
Solution.Process ID
Some Docker images take time to build through a Continuous Integration environment. You want to speed up builds and take advantage of build caching.
Where should the most frequently changed part of a Docker image be placed in a Dockerfile?
Is this a Linux kernel namespace that is disabled by default and must be enabled at Docker engine runtime to be used?
Solution.pid
In the context of a swarm mode cluster, does this describe a node?
Solution: an instance of the Docker engine participating in the swarm
An application image runs in multiple environments, with each environment using different certificates and ports. Is this a way to provision configuration to containers at runtime?
Solution.Create a Dockerfile for each environment, specifying ports and Docker secrets for certificates.
Is this a way to configure the Docker engine to use a registry without a trusted TLS certificate?
Solution: Set IGNORE_TLS in the 'daemon.json' configuration file.
Is this an advantage of multi-stage builds?
Solution.better logical separation of Dockerfile instructions for increased readability
The Kubernetes yaml shown below describes a clusterIP service.
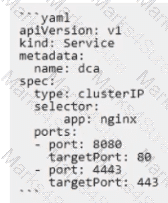
Is this a correct statement about how this service routes requests?
Solution: Traffic sent to the IP of any pod with the label app: nginx on port 8080 will be forwarded to port 80 in that pod.
You configure a local Docker engine to enforce content trust by setting the environment variable
DOCKER_CONTENT_TRUST=1.
If myorg/myimage: 1.0 is unsigned, does Docker block this command?
Solution: docker container run myorg/myimage:1.0
Will this sequence of steps completely delete an image from disk in the Docker Trusted Registry?
Solution: Delete the image and delete the image repository from Docker Trusted Registry
You want to create a container that is reachable from its host's network.
Does this action accomplish this?
Solution.Use either EXPOSE or -publish to access the container on the bridge network.