Which of the following are the types of access controls?
Each correct answer represents a complete solution. Choose three.
You have reason to believe someone with a domain user account has been accessing and modifying sensitive spreadsheets on one of your application servers. You decide to enable auditing for the files to see who is accessing and changing them. You enable the Audit Object Access policy on the files via Group Policy. Two weeks later, when you check on the audit logs, you see they are empty. What is the most likely reason this has happened?
Which of the following would be used to explicitly deny the traffic from a foreign IP address scanning the EC2 Instances in a VPC?
Use PowerShell ISE to
examineC:\Windows\security\templates\WorkstationSecureTemplate.inf. Which setting is configured in the template?

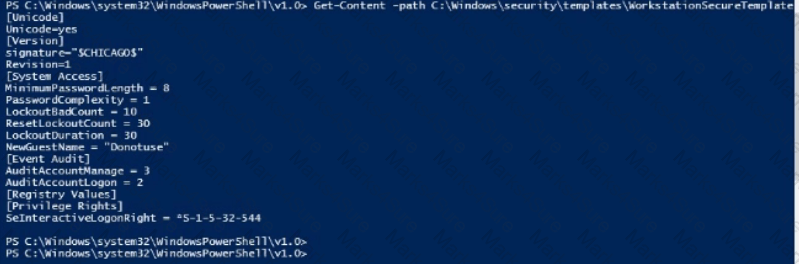
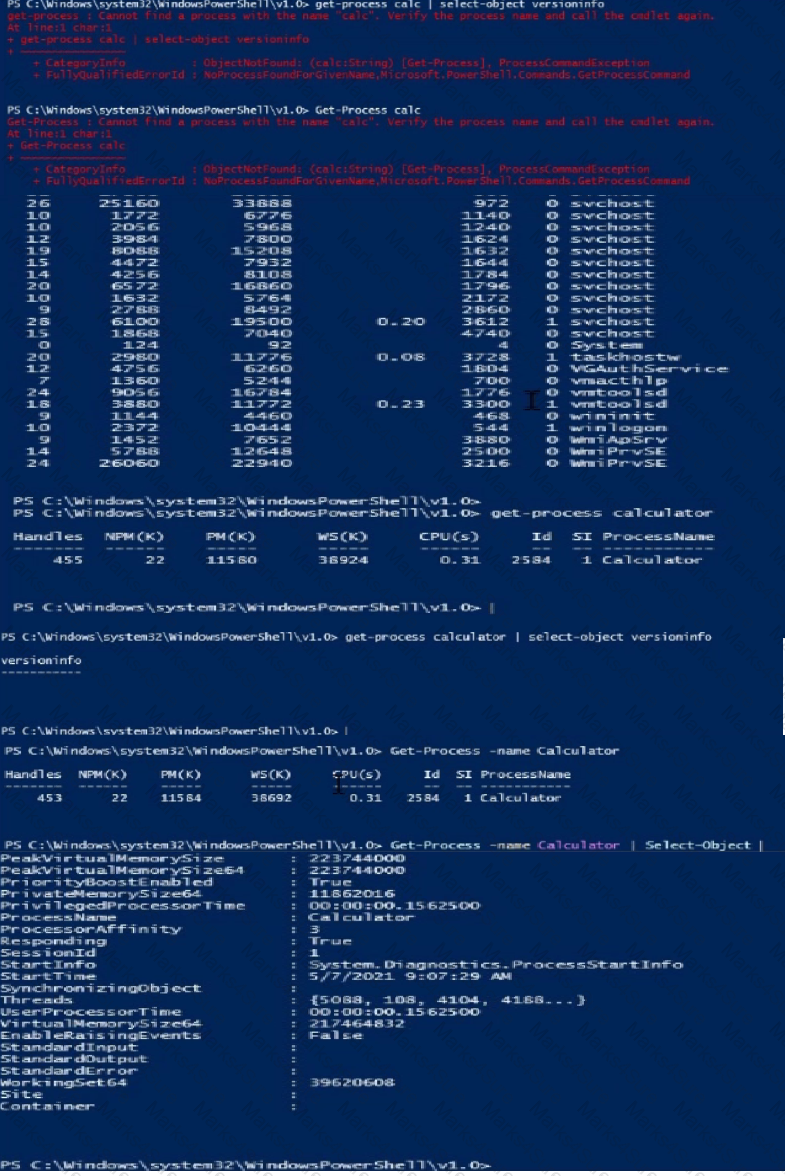
Launch Calculator (calc.exe). Using PowerShell, retrieve the Calculator Process Information. What is the value of the File Version property?
Hint: The process name of Calculator is calculator

A company disables cd drives for users; what defense strategy is this a part of?
What is the term for a game in which for every win there must be an equivalent loss?
What method do Unix-type systems use to prevent attackers from cracking passwords using pre-computed hashes?
Which of the following fields CANNOT be hashed by Authentication Header (AH) in transport mode?
Mark works as a Network Administrator for NetTech Inc. The company has a Windows 2003 domain- based network. The network contains ten Windows 2003 member servers, 150 Windows XP Professional client computers. According to the company's security policy, Mark needs to check whether all the computers in the network have all available security updates and shared folders. He also needs to check the file system type on each computer's hard disk. Mark installs and runs MBSACLI.EXE with the appropriate switches on a server. Which of the following tasks will he accomplish?
How is a Distributed Denial of Service (DDOS) attack distinguished from a regular DOS attack?
An attacker gained physical access to an internal computer to access company proprietary data. The facility is protected by a fingerprint biometric system that records both failed and successful entry attempts. No failures were logged during the time periods of the recent breach. The account used when the attacker entered the facility shortly before each incident belongs to an employee who was out of the area. With respect to the biometric entry system, which of the following actions will help mitigate unauthorized physical access to the facility?
John works as a Network Administrator for Perfect Solutions Inc. The company has a Linux-based network. John is working as a root user on the Linux operating system. He is currently working on his C based new traceroute program. Since, many processes are running together on the system, he wants to give the highest priority to the cc command process so that he can test his program, remove bugs, and submit it to the office in time. Which of the following commands will John use to give the highest priority to the cc command process?
What technique makes it difficult for attackers to predict the memory address space location for code execution?
Against policy, employees have installed Peer-to-Peer applications on their workstations and they are using them over TCP port 80 to download files via the company network from other Peer-to-Peer users on the Internet. Which of the following describes this threat?
Dilbert wants to have a script run on his Windows server every time Wally logs into it. Where should he place this script?
Jonny Is an IT Project Manager. He cannot access the folder called "IT Projects" but can access a folder called "Sales Data" even though he's not on the sales team. Which information security principle has failed?
Two clients connecting from the same public IP address (for example - behind the same NAT firewall) can connect simultaneously to the same web server on the Internet, provided what condition is TRUE?
Your IT security team is responding to a denial of service attack against your server. They have taken measures to block offending IP addresses. Which type of threat control is this?
Which of the following describes software technologies that improve portability, manageability, and compatibility of applications by encapsulating them from the underlying operating system on which they are executed?
Which of the following is a type of countermeasure that can be deployed to ensure that a threat vector does not meet a vulnerability?
Which of the following statements best describes where a border router is normally placed?
Which of the below choices should an organization start with when implementing an effective risk management process?
Which of the following are used to suppress gasoline and oil fires? Each correct answer represents a complete solution. Choose three.
When Net Stumbler is initially launched, it sends wireless frames to which of the following addresses?
Which of the following quantifies the effects of a potential disaster over a period of time?
During which of the following steps is the public/private key-pair generated for Public Key Infrastructure (PKI)?
Your software developer comes to you with an application that controls a user device. The application monitors its own behavior and that of the device and creates log files. The log files are expected to grow steadily and rapidly. Your developer currently has the log files stored in the /bin folder with the application binary. Where would you suggest that the developer store the log files?
During a scheduled evacuation training session the following events took place in this order:
1. Evacuation process began by triggering the building fire alarm.
2a. The meeting point leader arrived first at the designated meeting point and immediately began making note of who was and was not accounted for.
2b. Stairwell and door monitors made it to their designated position to leave behind a box of flashlights and prop the stairway doors open with a garbage can so employees can find exits and dispose of food and beverages.
2c. Special needs assistants performed their assigned responsibility to help employees out that require special assistance.
3. The safety warden communicated with the meeting point leader via walkie talkie to collect a list of missing personnel and communicated this information back to the searchers.
4. Searchers began checking each room and placing stick-it notes on the bottom of searched doors to designate which areas were cleared.
5. All special need assistants and their designated wards exited the building.
6. Searchers complete their assigned search pattern and exit with the Stairwell/door monitors.
Given this sequence of events, which role is in violation of its expected evacuation tasks?
Which of the following is a benefit of using John the Ripper for auditing passwords?
A system administrator sees the following URL in the webserver logs:
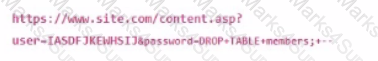
Which action will mitigate against this attack?
Which of the following is a required component for successful 802.lx network authentication?
Which choice best describes the line below?
alert tcp any any -> 192.168.1.0/24 80 (content: /cgi-bin/test.cgi"; msg: "Attempted
CGI-BIN Access!!";)
Which of the following attacks can be mitigated by avoiding making system calls from within a web application?
Which of the following is a new Windows Server 2008 feature for the Remote Desktop Protocol (RDP)?
Which of the following should be implemented to protect an organization from spam?
When trace route fails to get a timely response for a packet after three tries, which action will it take?
When you log into your Windows desktop what information does your Security Access Token (SAT) contain?
Which of the following authentication methods are used by Wired Equivalent Privacy (WEP)? Each correct answer represents a complete solution. Choose two.
Analyze the file below. When will the program /home/sink/utils/remove temp hies.py run?
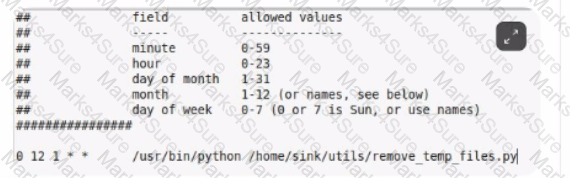
If a Linux administrator wanted to quickly filter out extraneous data and find a running process named RootKit, which command could he use?
Which access control mechanism requires a high amount of maintenance since all data must be classified, and all users granted appropriate clearance?
You work as a Network Administrator for Secure World Inc. The company has a Linux-based network. You want to run a command with the changed root directory. Which of the following commands will you use?
What are the two actions the receiver of a PGP email message can perform that allows establishment of trust between sender and receiver?
Which of the following protocols is used by a host that knows its own MAC (Media Access Control) address to query a server for its own IP address?
How is confidentiality disabled in the IPSec Encapsulated Security Payload protocol?
It is possible to sniff traffic from other hosts on a switched Ethernet network by impersonating which type of network device?
Which of the following works at the network layer and hides the local area network IP address and topology?
You work as a Network Administrator for McNeil Inc. The company has a Linux-based network. David, a Sales Manager, wants to know the name of the shell that he is currently using. Which of the following commands will he use to accomplish the task?
Which of the following statements about Microsoft's VPN client software is FALSE?
An employee is currently logged into the corporate web server, without permission. You log into the web server as 'admin" and look for the employee's username: "dmaul" using the "who" command. This is what you get back:
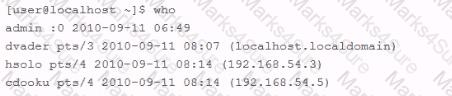
Which Windows event log would you look in if you wanted information about whether or not a specific diver was running at start up?
A VPC is created with a CIDR block of 10.22.0.0/16, which of the following private subnets could be Included?
Which of the following SIP INVITE lines indicates to the remote registrar the VoIP phone that initiated the call?
When no anomaly is present in an Intrusion Detection, but an alarm is generated, the response is known as.
Which of the following TCP dump output lines indicates the first step in the TCP 3-way handshake?
You are responsible for a Microsoft based network. Your servers are all clustered. Which of the following are the likely reasons for the clustering?
Each correct answer represents a complete solution. Choose two.
What would the following IP tables command do?
IP tables -I INPUT -s 99.23.45.1/32 -j DROP
There is not universal agreement on the names of the layers in the TCP/IP networking model. Which of the following is one of the functions of the bottom layer which is sometimes called the Network Access or Link Layer?
How many clients Is a single WSUS server designed to support when the minimum system requirements are met?
Which attack stage mirrors the Information Gathering phase used in penetration testing methodology?
What technical control provides the most critical layer of defense if an intruder is able to bypass all physical security controls and obtain tapes containing critical data?
You work as a Network Administrator for Perfect Solutions Inc. The company has a Linux-based network. You are required to search for the error messages in the /var/log/messages log file. Which of the following commands will you use to accomplish this?
Which of the following languages enable programmers to store cookies on client computers? Each correct answer represents a complete solution. Choose two.
Which of the following statements would describe the term "incident" when used in the branch of security known as Incident Handling?
You work as a Network Administrator for NetTech Inc. To ensure the security of files, you encrypt data files using Encrypting File System (EFS).
You want to make a backup copy of the files and maintain security settings. You can backup the files either to a network share or a floppy disk. What will you do to accomplish this?
You work as a Network Administrator for Tech Perfect Inc. The company has a Linux-based network. You want to kill a process running on a Linux server. Which of the following commands will you use to know the process identification number (PID) of the process?
When file integrity checking is enabled, what feature is used to determine if a monitored file has been modified?
Which of the following Microsoft services integrates SSO into Microsoft 365 by syncing with on-premises servers?
Which of the following statements about Network Address Translation (NAT) are true? Each correct answer represents a complete solution. Choose two.
John works as a Network Administrator for Perfect Solutions Inc. The company has a Linux-based network. He is working as a root user on the Linux operating system. He wants to delete his private.txt file from his operating system. He knows that the deleted file can be recovered easily. Hence, he wants to delete the file securely. He wants to hide the shredding, and so he desires to add a final overwrite of the file private.txt with zero. Which of the following commands will John use to accomplish his task?
When using Pretty Good Privacy (PGP) to digitally sign a message, the signature is created in a two-step process. First, the message to be signed is submitted to PGP's cryptographic hash algorithm. What is one of the hash algorithms used by PGP for this process?
What would the file permission example "rwsr-sr-x" translate to in absolute mode?
In preparation to do a vulnerability scan against your company's systems. You've taken the steps below:
You've notified users that there will be a system test.
You've priontized and selected your targets and subnets.
You've configured the system to do a deep scan.
You have a member of your team on call to answer questions.
Which of the following is a necessary step to take prior to starting the scan?
What type of malware is a self-contained program that has the ability to copy itself without parasitically infecting other host code?
Which of the four basic transformations in the AES algorithm involves the leftward circular movement of state data?
Which of the following is a private, RFC 1918 compliant IP address that would be assigned to a DHCP scope on a private LAN?
Which Defense-in-Depth principle starts with an awareness of the value of each section of information within an organization?
Your system has been infected by malware. Upon investigation, you discover that the malware propagated primarily via email. The malware attacked known vulnerabilities for which patches are available, but due to problems with your configuration management system you have no way to know which systems have been patched and which haven't, slowing your progress in patching your network. Of the following, which solution would you use to protect against this propagation vector?
What is the maximum number of connections a normal Bluetooth device can handle at one time?
Which of the following is a Layer 3 device that will typically drop directed broadcast traffic?
Analyze the screenshot below. In what order should the vulnerabilities be remediated?
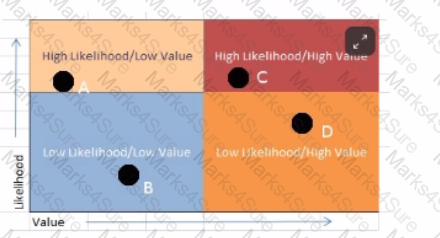
You are the security director for an off-shore banking site. From a business perspective, what is a major factor to consider before running your new vulnerability scanner against the company's business systems?
You work as an Administrator for McRoberts Inc. The company has a Linux-based network. You are logged in as a non-root user on your client computer. You want to delete all files from the /garbage directory. You want that the command you will use should prompt for the root user password. Which of the following commands will you use to accomplish the task?