Refer to the exhibits.
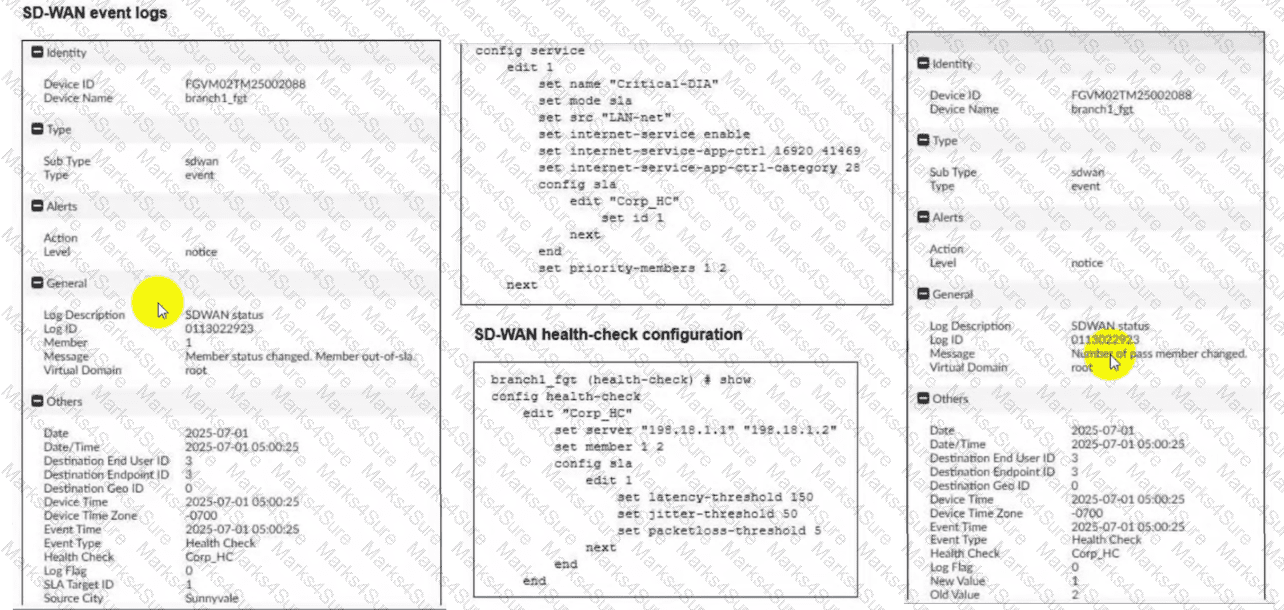
Two SD-WAN event logs, the member status, the SD-WAN rule configuration, and the health-check configuration for a FortiGate device are shown. Immediately after the log messages are displayed, how will the FortiGate steer the traffic based on the information shown in the exhibits? (Choose one answer)
SD-WAN interacts with many other FortiGate features. Some of them are required to allow SD-WAN to steer the traffic.
Which three configuration elements must you configure before FortiGate can steer traffic according to SD-WAN rules? (Choose three.)
How does the FortiSASE security dashboard facilitate vulnerability management for FortiClient endpoints? (Choose one answer)
A FortiGate device is in production. To optimize WAN link use and improve redundancy, you enable and configure SD-WAN.
What must you do as part of this configuration update process? (Choose one answer)
Which FortiSASE feature monitors SaaS application performance and connectivity to points of presence (POPs)?
Which two statements correctly describe what happens when traffic matches the implicit SD-WAN rule? (Choose two answers)
Refer to the exhibit.
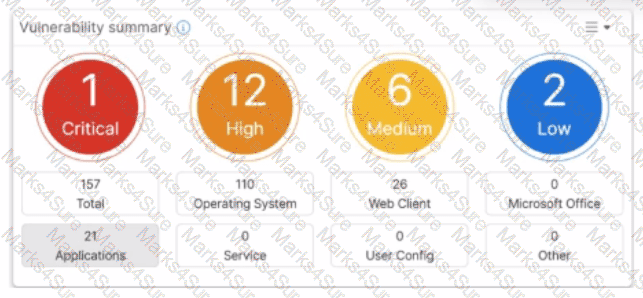
Which two statements about the Vulnerability summary dashboard in FortiSASE are correct? (Choose two.)