An administrator would like to apply a more restrictive Security profile to traffic for file sharing applications. The administrator does not want to update the Security policy or object when new applications are released.
Which object should the administrator use as a match condition in the Security policy?
Which Security profile can you apply to protect against malware such as worms and Trojans?
The PowerBall Lottery has reached a high payout amount and a company has decided to help employee morale by allowing employees to check the number, but doesn’t want to unblock the gambling URL category.
Which two methods will allow the employees to get to the PowerBall Lottery site without the company unlocking the gambling URL category? (Choose two.)
Which interface type is part of a Layer 3 zone with a Palo Alto Networks firewall?
Which User Credential Detection method should be applied within a URL Filtering Security profile to check for the submission of a valid corporate username and the associated password?
Which solution is a viable option to capture user identification when Active Directory is not in use?
In which two Security Profiles can an action equal to the block IP feature be configured? (Choose two.)
What allows a security administrator to preview the Security policy rules that match new application signatures?
During the App-ID update process, what should you click on to confirm whether an existing policy rule is affected by an App-ID update?
All users from the internal zone must be allowed only Telnet access to a server in the DMZ zone. Complete the two empty fields in the Security Policy rules that permits only this type of access.

Choose two.
Which two types of profiles are needed to create an authentication sequence? (Choose two.)
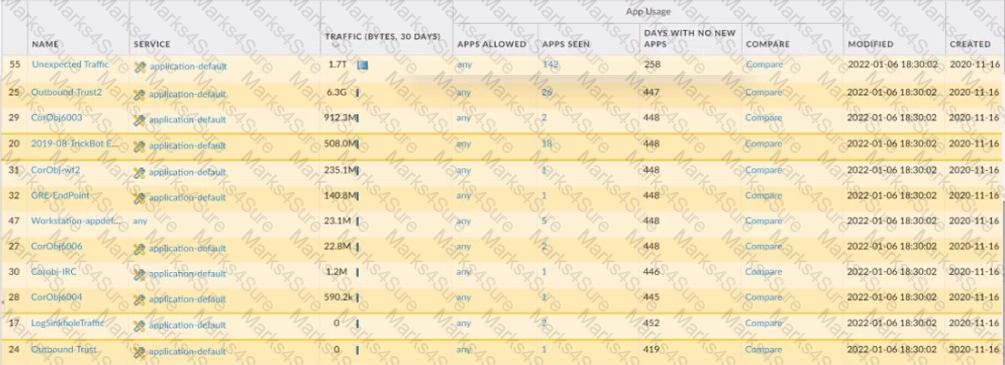
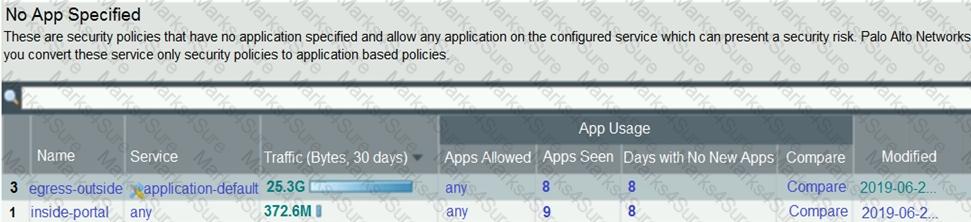
An administrator is updating Security policy to align with best practices.
Which Policy Optimizer feature is shown in the screenshot below?
The PowerBall Lottery has reached an unusually high value this week. Your company has decided to raise morale by allowing employees to access the PowerBall Lottery website (www.powerball.com) for just this week. However, the company does not want employees to access any other websites also listed in the URL filtering “gambling” category.
Which method allows the employees to access the PowerBall Lottery website but without unblocking access to the “gambling” URL category?
An administrator configured a Security policy rule where the matching condition includes a single application and the action is set to deny. What deny action will the firewall perform?
Your company occupies one floor in a single building you have two active directory domain controllers on a single networks the firewall s management plane is only slightly utilized.
Which user-ID agent sufficient in your network?
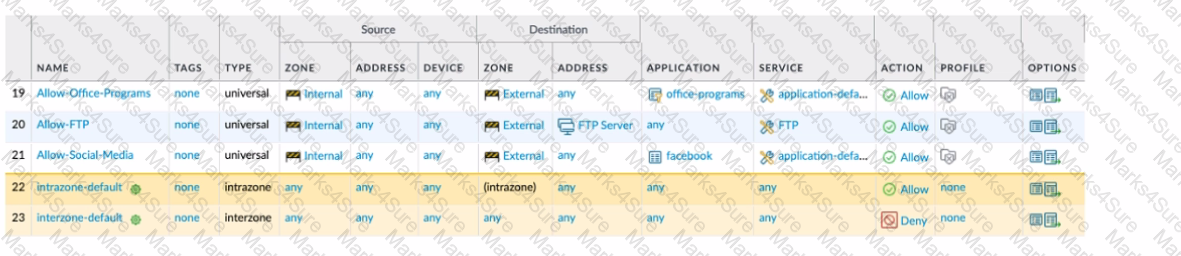
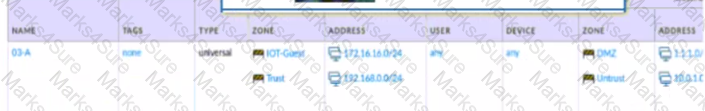
Based on the image provided, which two statements apply to the Security policy rules? (Choose two.)
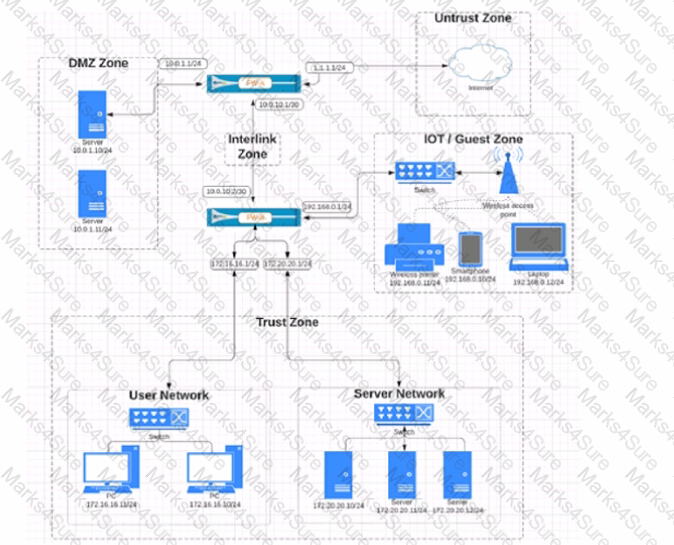
Based on the network diagram provided, which two statements apply to traffic between the User and Server networks? (Choose two.)
You receive notification about new malware that infects hosts through malicious files transferred by FTP.
Which Security profile detects and protects your internal networks from this threat after you update your firewall’s threat signature database?
You receive notification about new malware that is being used to attack hosts The malware exploits a software bug in a common application
Which Security Profile detects and blocks access to this threat after you update the firewall's threat signature database?
Which type of DNS signatures are used by the firewall to identify malicious and command-and-control domains?
You need to allow users to access the office–suite application of their choice. How should you configure the firewall to allow access to any office-suite application?
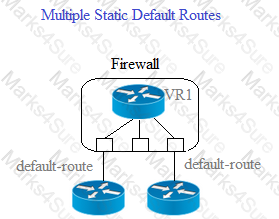
Given the scenario, which two statements are correct regarding multiple static default routes? (Choose two.)
Which two features can be used to tag a username so that it is included in a dynamic user group? (Choose two.)
Which setting is available to edit when a tag is created on the local firewall?
An administrator wants to create a NAT policy to allow multiple source IP addresses to be translated to the same public IP address. What is the most appropriate NAT policy to achieve this?
An administrator is investigating a log entry for a session that is allowed and has the end reason of aged-out. Which two fields could help in determining if this is normal? (Choose two.)
Which three configuration settings are required on a Palo Alto networks firewall management interface?
What must be configured for the firewall to access multiple authentication profiles for external services to authenticate a non-local account?
Assume a custom URL Category Object of "NO-FILES" has been created to identify a specific website
How can file uploading/downloading be restricted for the website while permitting general browsing access to that website?
Based on the screenshot presented which column contains the link that when clicked opens a window to display all applications matched to the policy rule?
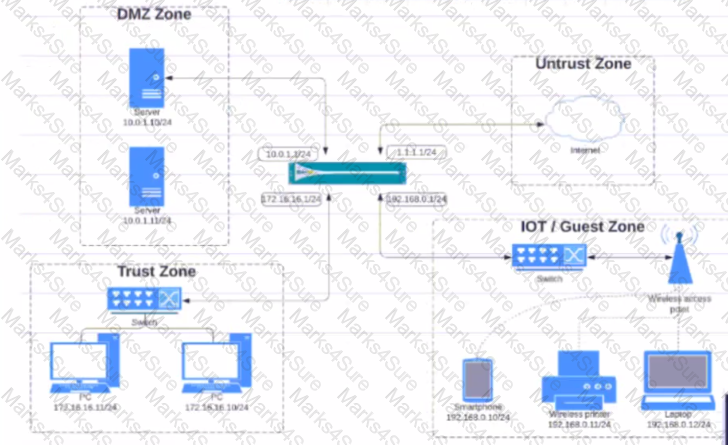
Given the network diagram, traffic should be permitted for both Trusted and Guest users to access general Internet and DMZ servers using SSH. web-browsing and SSL applications
Which policy achieves the desired results?
A)

B)
C)

D)

Which two features can be used to tag a user name so that it is included in a dynamic user group? (Choose two)
An administrator wants to create a No-NAT rule to exempt a flow from the default NAT rule. What is the best way to do this?
What must first be created on the firewall for SAML authentication to be configured?
Given the image, which two options are true about the Security policy rules. (Choose two.)
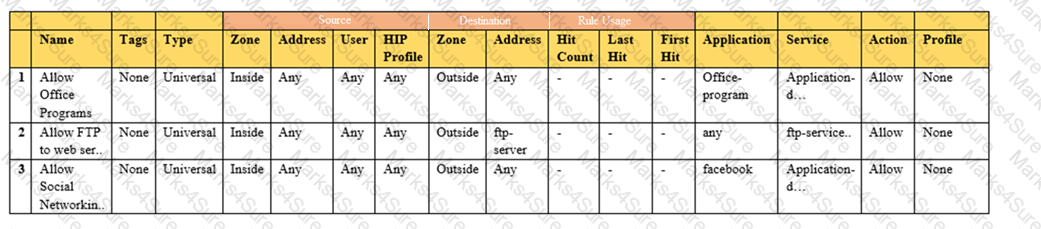
A network administrator creates an intrazone security policy rule on a NGFW. The source zones are set to IT. Finance, and HR.
To which two types of traffic will the rule apply? (Choose two.)
Which security profile will provide the best protection against ICMP floods, based on individual combinations of a packet`s source and destination IP address?
What is a prerequisite before enabling an administrative account which relies on a local firewall user database?
What does an administrator use to validate whether a session is matching an expected NAT policy?
Which policy set should be used to ensure that a policy is applied just before the default security rules?
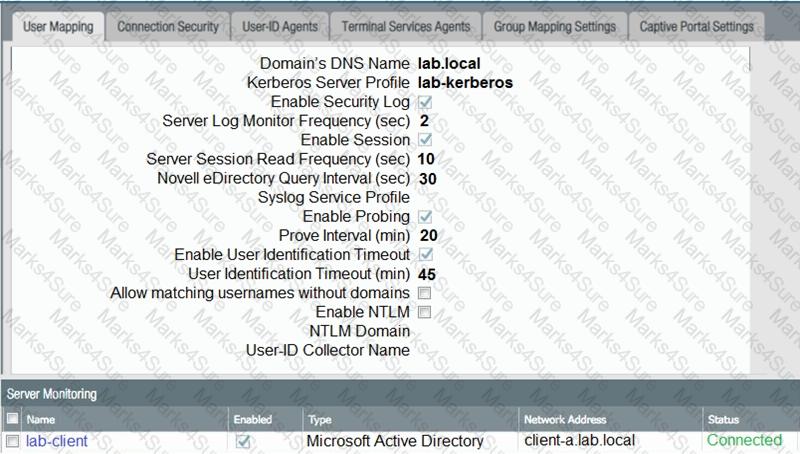
Based on the graphic which statement accurately describes the output shown in the server monitoring panel?
Which action results in the firewall blocking network traffic without notifying the sender?
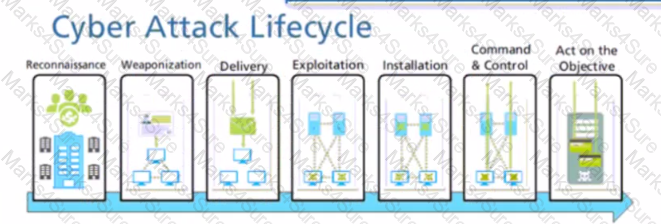
At which stage of the cyber-attack lifecycle would the attacker attach an infected PDF file to an email?
According to the best practices for mission critical devices, what is the recommended interval for antivirus updates?
An administrator would like to create a URL Filtering log entry when users browse to any gambling website. What combination of Security policy and Security profile actions is correct?
In which section of the PAN-OS GUI does an administrator configure URL Filtering profiles?
In which three places on the PAN-OS interface can the application characteristics be found? (Choose three.)
Which firewall plane provides configuration, logging, and reporting functions on a separate processor?
Which path in PAN-OS 10.0 displays the list of port-based security policy rules?
Which three types of Source NAT are available to users inside a NGFW? (Choose three.)
What must be considered with regards to content updates deployed from Panorama?
URL categories can be used as match criteria on which two policy types? (Choose two.)
Which two firewall components enable you to configure SYN flood protection thresholds? (Choose two.)
An administrator needs to create a Security policy rule that matches DNS traffic within the LAN zone, and also needs to match DNS traffic within the DMZ zone The administrator does not want to allow traffic between the DMZ and LAN zones.
Which Security policy rule type should they use?
How would a Security policy need to be written to allow outbound traffic using Secure Shell (SSH) to destination ports tcp/22 and tcp/4422?
Which user mapping method could be used to discover user IDs in an environment with multiple Windows domain controllers?
An administrator is trying to enforce policy on some (but not all) of the entries in an external dynamic list. What is the maximum number of entries that they can be exclude?
Which interface type requires no routing or switching but applies Security or NAT policy rules before passing allowed traffic?
A systems administrator momentarily loses track of which is the test environment firewall and which is the production firewall. The administrator makes changes to the candidate configuration of the production firewall, but does not commit the changes. In addition, the configuration was not saved prior to
making the changes.
Which action will allow the administrator to undo the changes?
Starting with PAN_OS version 9.1 which new type of object is supported for use within the user field of a security policy rule?
Which attribute can a dynamic address group use as a filtering condition to determine its membership?
Which service protects cloud-based applications such as Dropbox and Salesforce by administering permissions and scanning files for sensitive information?
An administrator is implementing an exception to an external dynamic list by adding an entry to the list manually. The administrator wants to save the changes, but the OK button is grayed out.
What are two possible reasons the OK button is grayed out? (Choose two.)
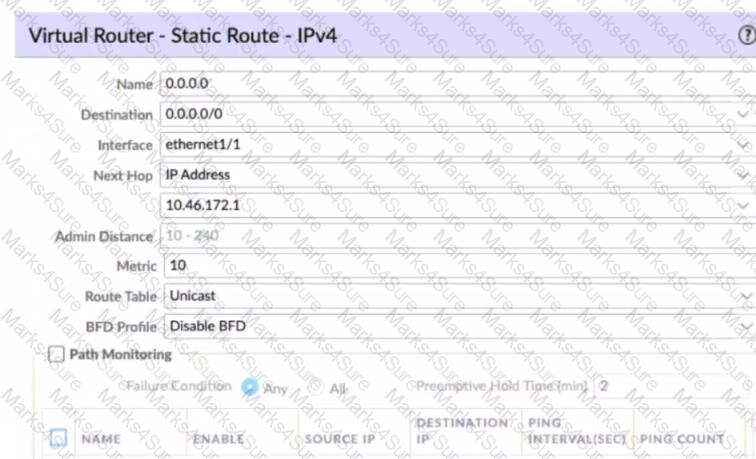
Given the screenshot what two types of route is the administrator configuring? (Choose two )
An administrator receives a global notification for a new malware that infects hosts. The infection will result in the infected host attempting to contact a command-and-control (C2) server. Which two security profile components will detect and prevent this threat after the firewall’s signature database has been updated? (Choose two.)
What can be achieved by selecting a policy target prior to pushing policy rules from Panorama?
An administrator is configuring a NAT rule
At a minimum, which three forms of information are required? (Choose three.)
Which administrator type utilizes predefined roles for a local administrator account?
Choose the option that correctly completes this statement. A Security Profile can block or allow traffic ____________.
Which administrative management services can be configured to access a management interface?
Within a WildFire Analysis Profile, what match criteria can be defined to forward samples for analysis?
If using group mapping with Active Directory Universal Groups, what must you do when configuring the User-ID?
An administrator has an IP address range in the external dynamic list and wants to create an exception for one specific IP address in this address range.
Which steps should the administrator take?
Which table for NAT and NPTv6 (IPv6-to-IPv6 Network Prefix Translation) settings is available only on Panorama?
What is the best-practice approach to logging traffic that traverses the firewall?
In a security policy what is the quickest way to rest all policy rule hit counters to zero?
An administrator wants to prevent users from submitting corporate credentials in a phishing attack.
Which Security profile should be applied?
What in the minimum frequency for which you can configure the firewall too check for new wildfire antivirus signatures?
Which the app-ID application will you need to allow in your security policy to use facebook-chat?
Which System log severity level would be displayed as a result of a user password change?