The vulnerability protection profile of an on-premises Palo Alto Networks firewall is triggering on a common Threat ID, and it has been determined to be a false positive. The issue causes an outage of a critical service. When the vulnerability protection profile is opened to add the exception, the Threat ID is missing. Which action will most efficiently find and implement the exception?
You are auditing the work of a co-worker and need to verify that they have matched the Palo Alto Networks Best Practices for Anti-Spyware Profiles.
For which three severity levels should single-packet captures be enabled to meet the Best Practice standard? (Choose three.)
An administrator is configuring a Panorama device group. Which two objects are configurable? (Choose two.)
A firewall administrator has configured User-ID and deployed GlobalProtect, but there is no User-ID showing in the traffic logs.
How can the administrator ensure that User-IDs are populated in the traffic logs?
A company wants to use GlobalProtect as its remote access VPN solution.
Which GlobalProtect features require a Gateway license?
An administrator notices that an interface configuration has been overridden locally on a firewall. They require all configuration to be managed from Panorama and overrides are not allowed. What is one way the administrator can meet this requirement?
If a URL is in multiple custom URL categories with different actions, which action will take priority?
When backing up and saving configuration files, what is achieved using only the firewall and is not available in Panorama?
A security engineer needs to mitigate packet floods that occur on a RSF servers behind the internet facing interface of the firewall. Which Security Profile should be applied to a policy to prevent these packet floods?
An administrator is informed that the engineer who previously managed all the VPNs has left the company. According to company policies the administrator must update all the IPSec VPNs with new pre-shared keys Where are the pre-shared keys located on the firewall?
Which GlobalProtect gateway selling is required to enable split-tunneling by access route, destination domain, and application?
Review the screenshot of the Certificates page.
An administrator for a small LLC has created a series of certificates as shown, to use for a planned Decryption roll out. The administrator has also installed the self-signed root certificate in all client systems.
When testing, they noticed that every time a user visited an SSL site, they received unsecured website warnings.
What is the cause of the unsecured website warnings?
An engineer needs to collect User-ID mappings from the company's existing proxies.
What two methods can be used to pull this data from third party proxies? (Choose two.)
An engineer is designing a deployment of multi-vsys firewalls.
What must be taken into consideration when designing the device group structure?
Users are intermittently being cut off from local resources whenever they connect to GlobalProtect. After researching, it is determined that this is caused by an incorrect setting on one of the NGFWs. Which action will resolve this issue?
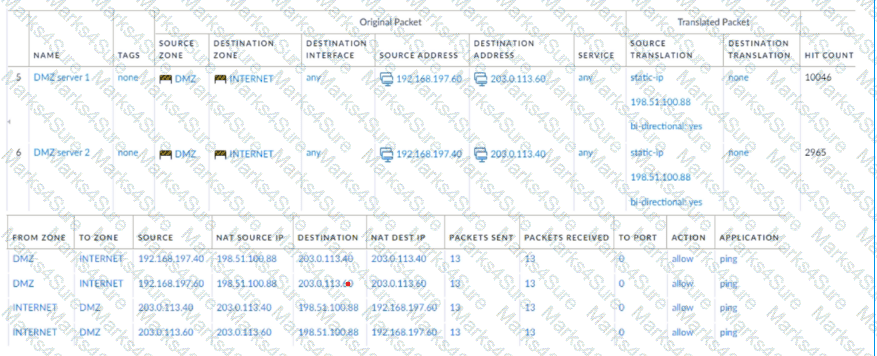
A new application server 192.168.197.40 has been deployed in the DMZ. There are no public IP addresses available resulting in the server sharing MAT IP 198 51 100 B8 with another OMZ serve that uses IP address 192 168 19? 60 Firewall security and NAT rules have been configured The application team has confirmed mat the new server is able to establish a secure connection to an external database with IP address 203.0.113.40. The database team reports that they are unable to establish a secure connection to 196 51 100 88 from 203.0.113.40 However it confirm a successful prig test to 198 51 100 88 Referring to the MAT configuration and traffic logs provided how can the firewall engineer resolve the situation and ensure inbound and outbound connections work concurrently for both DMZ servers?
A network engineer has discovered that asymmetric routing is causing a Palo Alto Networks firewall to drop traffic. The network architecture cannot be changed to correct this.
Which two actions can be taken on the firewall to allow the dropped traffic permanently? (Choose two.)
Which GloDalProtecI gateway setting is required to enable split-tunneting by access route, destination domain and application?
After implementing a new NGFW, a firewall engineer sees a VoIP traffic issue going through the firewall After troubleshooting the engineer finds that the firewall performs NAT on the voice packets payload and opens dynamic pinholes for media ports
What can the engineer do to solve the VoIP traffic issue?
A firewall administrator wants to be able at to see all NAT sessions that are going ‘through a firewall with source NAT. Which CLI command can the administrator use?
Which three items must be configured to implement application override? (Choose three )
For company compliance purposes, three new contractors will be working with different device-groups in their hierarchy to deploy policies and objects.
Which type of role-based access is most appropriate for this project?
What action does a firewall take when a Decryption profile allows unsupported modes and unsupported traffic with TLS 1.2 protocol traverses the firewall?
An engineer configures SSL decryption in order to have more visibility to the internal users' traffic when it is regressing the firewall.
Which three types of interfaces support SSL Forward Proxy? (Choose three.)
A network administrator is troubleshooting an issue with Phase 2 of an IPSec VPN tunnel The administrator determines that the lifetime needs to be changed to match the peer. Where should this change be made?
A firewall engineer is configuring quality of service (OoS) policy for the IP address of a specific server in an effort to limit the bandwidth consumed by frequent downloads of large files from the internet.
Which combination of pre-NAT and / or post-NAT information should be used in the QoS rule?
An existing log forwarding profile is currently configured to forward all threat logs to Panorama. The firewall engineer wants to add syslog as an additional log forwarding method. The requirement is to forward only medium or higher severity threat logs to syslog. Forwarding to Panorama must not be changed.
Which set of actions should the engineer take to achieve this goal?
Which tool can gather information about the application patterns when defining a signature for a custom application?
An administrator wants to enable WildFire inline machine learning. Which three file types does WildFire inline ML analyze? (Choose three.)
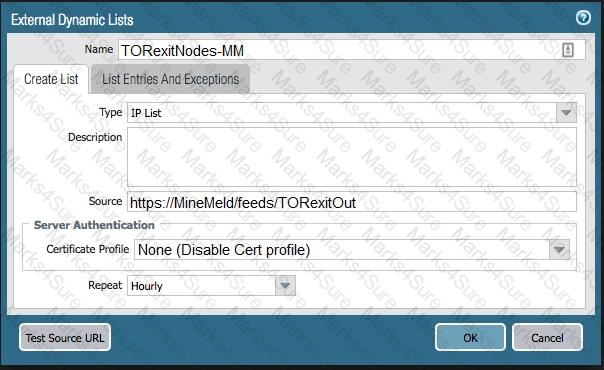
The firewall is not downloading IP addresses from MineMeld. Based, on the image, what most likely is wrong?
A firewall engineer is migrating port-based rules to application-based rules by using the Policy Optimizer. The engineer needs to ensure that the new application-based rules are future-proofed, and that they will continue to match if the existing signatures for a specific application are expanded with new child applications. Which action will meet the requirement while ensuring that traffic unrelated to the specific application is not matched?
Which type of policy in Palo Alto Networks firewalls can use Device-ID as a match condition?
Which statement explains the difference between using the PAN-OS integrated User-ID agent and the standalone User-ID agent when using Active Directory for user-to-IP mapping?
Which server platforms can be monitored when a company is deploying User-ID through server monitoring in an environment with diverse directory services?
If an administrator wants to apply QoS to traffic based on source, what must be specified in a QoS policy rule?
An administrator pushes a new configuration from Panorama to a pair of firewalls that are configured as an active/passive HA pair. Which NGFW receives the configuration from Panorama?
Certain services in a customer implementation are not working, including Palo Alto Networks Dynamic version updates.
Which CLI command can the firewall administrator use to verify if the service routes were correctly installed and that they are active in the Management Plane?
A network security administrator wants to enable Packet-Based Attack Protection in a Zone Protection profile. What are two valid ways to enable Packet-Based Attack Protection? (Choose two.)
What would allow a network security administrator to authenticate and identify a user with a new BYOD-type device that is not joined to the corporate domain?
A security team has enabled real-time WildFire signature lookup on all its firewalls. Which additional action will further reduce the likelihood of newly discovered malware being allowed through the firewalls?
An administrator troubleshoots an issue that causes packet drops.
Which log type will help the engineer verify whether packet buffer protection was activated?
An administrator receives the following error message:
"IKE phase-2 negotiation failed when processing Proxy ID. Received local id 192.168 33 33/24 type IPv4 address protocol 0 port 0, received remote id 172.16 33.33/24 type IPv4 address protocol 0 port 0."
How should the administrator identify the root cause of this error message?
An administrator has been asked to configure active/active HA for a pair of Palo Alto Networks NGFWs. The firewall use Layer 3 interfaces to send traffic to a single gateway IP for the pair.
Which configuration will enable this HA scenario?
How is Perfect Forward Secrecy (PFS) enabled when troubleshooting a VPN Phase 2 mismatch?
A company is deploying User-ID in their network. The firewall team needs to have the ability to see and choose from a list of usernames and user groups directly inside the Panorama policies when creating new security rules.
How can this be achieved?
An administrator would like to determine which action the firewall will take for a specific CVE. Given the screenshot below, where should the administrator navigate to view this information?
A firewall administrator has been tasked with ensuring that all firewalls forward System logs to Panorama. In which section is this configured?
An administrator notices that an interface configuration has been overridden locally on a firewall. They require all configuration to be managed from Panorama and overrides are not allowed.
What is one way the administrator can meet this requirement?
A firewall administrator is changing a packet capture filter to troubleshoot a specific traffic flow Upon opening the newly created packet capture, the administrator still sees traffic for the previous fitter What can the administrator do to limit the captured traffic to the newly configured filter?
A firewall engineer is managing a Palo Alto Networks NGFW that does not have the DHCP server on DHCP agent configuration. Which interface mode can the broadcast DHCP traffic?
A security engineer wants to upgrade the company's deployed firewalls from PAN-OS 10.1 to 11.0.x to take advantage of the new TLSvl.3 support for management access.
What is the recommended upgrade path procedure from PAN-OS 10.1 to 11.0.x?
A firewall engineer creates a NAT rule to translate IP address 1.1.1.10 to 192.168.1.10. The engineer also plans to enable DNS rewrite so that the firewall rewrites the IPv4 address in a DNS response based on the original destination IP address and translated destination IP address configured for the rule. The engineer wants the firewall to rewrite a DNS response of 1.1.1.10 to 192.168.1.10.
What should the engineer do to complete the configuration?
Which interface type should a firewall administrator configure as an upstream to the ingress trusted interface when configuring transparent web proxy on a Palo Alto Networks firewall?
Which Panorama mode should be used so that all logs are sent to. and only stored in. Cortex Data Lake?
How can a firewall be set up to automatically block users as soon as they are found to exhibit malicious behavior via a threat log?
An administrator plans to deploy 15 firewalls to act as GlobalProtect gateways around the world. Panorama will manage the firewalls.
The firewalls will provide access to mobile users and act as edge locations to on-premises infrastructure. The administrator wants to scale the configuration out quickly and wants all of the firewalls to use the same template configuration.
Which two solutions can the administrator use to scale this configuration? (Choose two.)
A security engineer needs firewall management access on a trusted interface.
Which three settings are required on an SSL/TLS Service Profile to provide secure Web UI authentication? (Choose three.)
A customer wants to deploy User-ID on a Palo Alto Network NGFW with multiple vsys. One of the vsys will support a GlobalProtect portal and gateway. the customer uses Windows
After configuring an IPSec tunnel, how should a firewall administrator initiate the IKE phase 1 to see if it will come up?
When configuring a GlobalProtect Portal, what is the purpose of specifying an Authentication Profile?
An engineer is configuring secure web access (HTTPS) to a Palo Alto Networks firewall for management.
Which profile should be configured to ensure that management access via web browsers is encrypted with a trusted certificate?
Which two actions must an engineer take to configure SSL Forward Proxy decryption? (Choose two.)
An administrator needs to identify which NAT policy is being used for internet traffic.
From the Monitor tab of the firewall GUI, how can the administrator identify which NAT policy is in use for a traffic flow?
An engineer needs to collect User-ID mappings from the company’s existing proxies. What two methods can be used to pull this data from third-party proxies? (Choose two)
An administrator needs to gather information about the CPU utilization on both the management plane and the data plane. Where does the administrator view the desired data?
Review the screenshots.
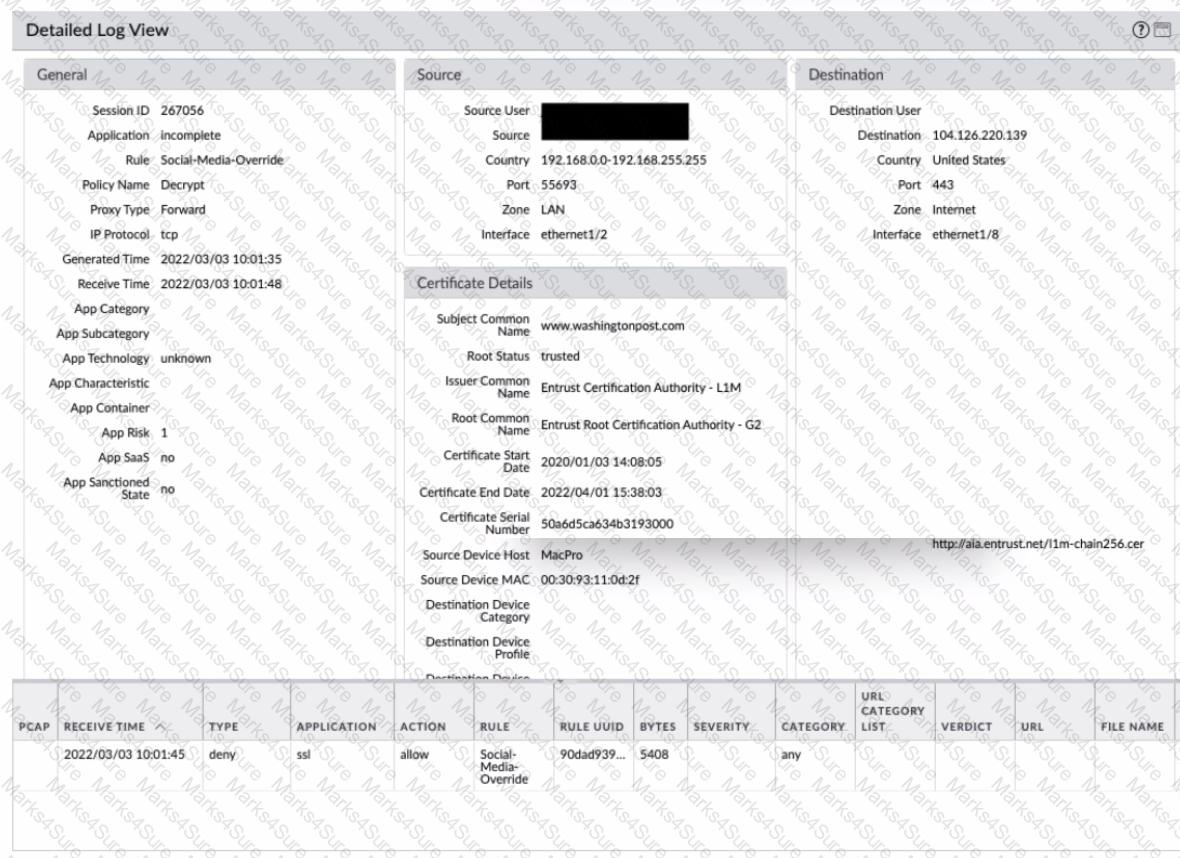
What is the most likely reason for this decryption error log?
An administrator wants to configure the Palo Alto Networks Windows User-D agent to map IP addresses to u: ‘The company uses four Microsoft Active ‘servers and two Microsoft Exchange servers, which can provide logs for login events. All six servers have IP addresses assigned from the following subnet: 192.168.28.32/27. The Microsoft Active Directory in 192.168.28.22/128, and the Microsoft Exchange reside in 192,168.28 48/28. What the 0 the User
Which CLI command is used to simulate traffic going through the firewall and determine which Security policy rule, NAT translation, static route, or PBF rule will be triggered by the traffic?
An administrator has two pairs of firewalls within the same subnet. Both pairs of firewalls have been configured to use High Availability mode with Active/Passive. The ARP tables for upstream routes display the same MAC address being shared for some of these firewalls.
What can be configured on one pair of firewalls to modify the MAC addresses so they are no longer in conflict?
An administrator is tasked to provide secure access to applications running on a server in the company's on-premises datacenter.
What must the administrator consider as they prepare to configure the decryption policy?
A firewall engineer needs to update a company's Panorama-managed firewalls to the latest version of PAN-OS. Strict security requirements are blocking internet access to Panorama and to the firewalls. The PAN-OS images have previously been downloaded to a secure host on the network.
Which path should the engineer follow to deploy the PAN-OS images to the firewalls?
Which three methods are supported for split tunneling in the GlobalProtect Gateway? (Choose three.)
When creating a Policy-Based Forwarding (PBF) rule, which two components can be used? (Choose two.)
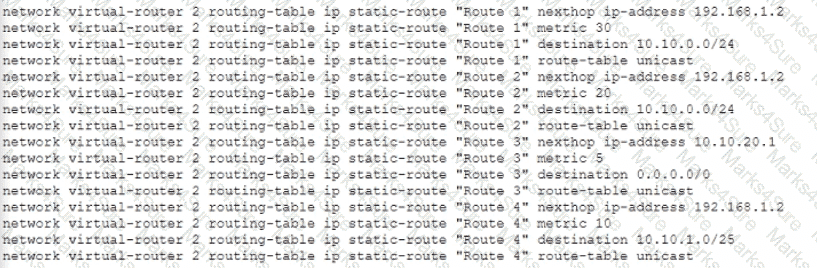
Given the following configuration, which route is used for destination 10 10 0 4?
What are three prerequisites for credential phishing prevention to function? (Choose three.)
Refer to the diagram. Users at an internal system want to ssh to the SSH server. The server is configured to respond only to the ssh requests coming from IP 172.16.16.1.
In order to reach the SSH server only from the Trust zone, which Security rule and NAT rule must be configured on the firewall?
An administrator has been asked to configure a Palo Alto Networks NGFW to provide protection against worms and trojans. Which Security Profile type will protect against worms and trojans?
A network security engineer is attempting to peer a virtual router on a PAN-OS firewall with an external router using the BGP protocol. The peer relationship is not establishing. What command could the engineer run to see the current state of the BGP state between the two devices?
Which User-ID mapping method should be used in a high-security environment where all IP address-to-user mappings should always be explicitly known?
View the screenshots
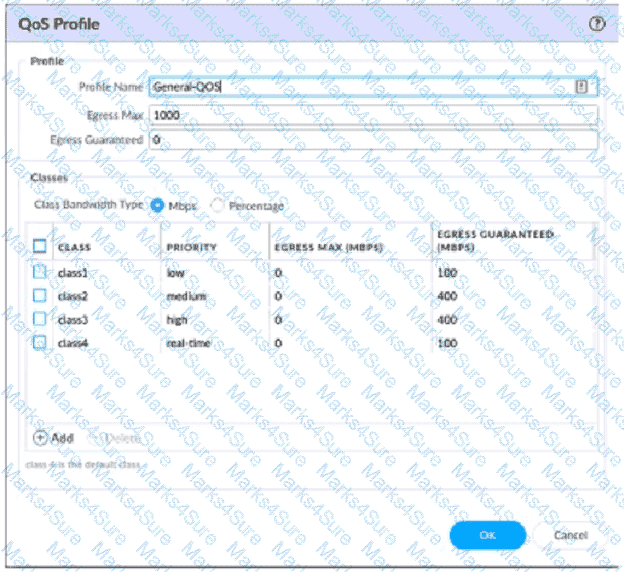
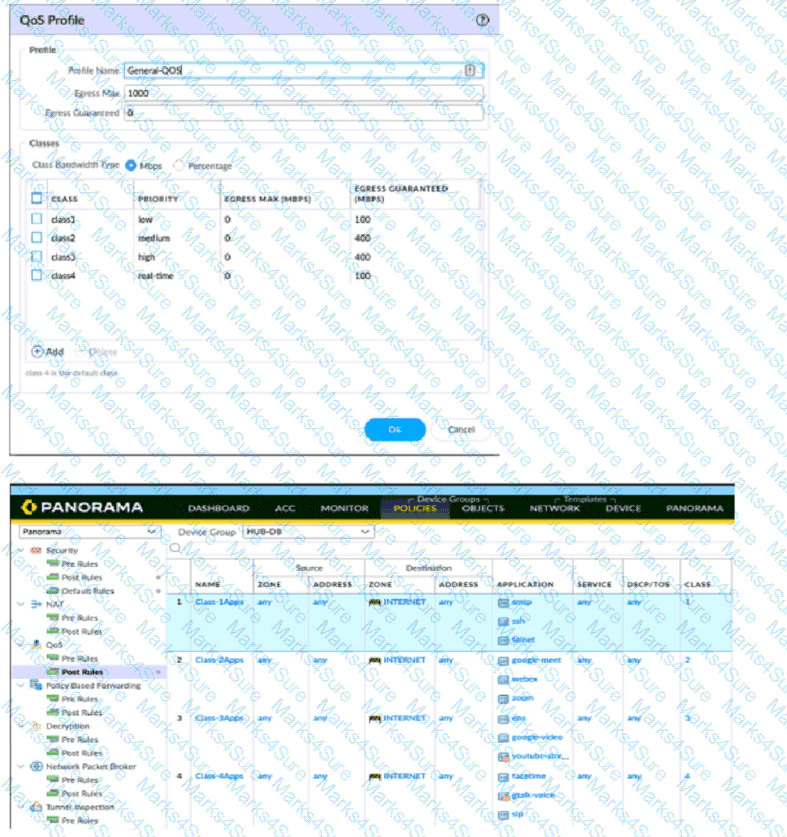
A QoS profile and policy rules are configured as shown. Based on this information which two statements are correct?
A company CISO updates the business Security policy to identify vulnerable assets and services and deploy protection for quantum-related attacks. As a part of this update, the firewall team is reviewing the cryptography used by any devices they manage. The firewall architect is reviewing the Palo Alto Networks NGFWs for their VPN tunnel configurations. It is noted in the review that the NGFWs are running PAN-OS 11.2. Which two NGFW settings could the firewall architect recommend to deploy protections per the new policy? (Choose two)
A firewall administrator is investigating high packet buffer utilization in the company firewall. After looking at the threat logs and seeing many flood attacks coming from a single source that are dropped by the firewall, the administrator decides to enable packet buffer protection to protect against similar attacks.
The administrator enables packet buffer protection globally in the firewall but still sees a high packet buffer utilization rate.
What else should the administrator do to stop packet buffers from being overflowed?
Which three firewall multi-factor authentication factors are supported by PAN-OS? (Choose three.)
An administrator connects a new fiber cable and transceiver Ethernet1/1 on a Palo Alto Networks firewall. However, the link does not come up. How can the administrator troubleshoot to confirm the transceiver type, tx-power, rxpower, vendor name, and part number by using the CLI?
If a template stack is assigned to a device and the stack includes three templates with overlapping settings, which settings are published to the device when the template stack is pushed?
An administrator is receiving complaints about application performance degradation. After checking the ACC, the administrator observes that there is an excessive amount of VoIP traffic.
Which three elements should the administrator configure to address this issue? (Choose three.)
An administrator is assisting a security engineering team with a decryption rollout for inbound and forward proxy traffic. Incorrect firewall sizing is preventing the team from decrypting all of the traffic they want to decrypt. Which three items should be prioritized for decryption? (Choose three.)
A company is expanding its existing log storage and alerting solutions All company Palo Alto Networks firewalls currently forward logs to Panorama. Which two additional log forwarding methods will PAN-OS support? (Choose two)
A firewall administrator is changing a packet capture filter to troubleshoot a specific traffic flow. Upon opening the newly created packet capture, the administrator still sees traffic for the previous filter.
What can the administrator do to limit the captured traffic to the newly configured filter?
An engineer configures a destination NAT policy to allow inbound access to an internal server in the DMZ. The NAT policy is configured with the following values:
- Source zone: Outside and source IP address 1.2.2.2
- Destination zone: Outside and destination IP address 2.2.2.1
The destination NAT policy translates IP address 2.2.2.1 to the real IP address 10.10.10.1 in the DMZ zone.
Which destination IP address and zone should the engineer use to configure the security policy?
An organization wants to begin decrypting guest and BYOD traffic.
Which NGFW feature can be used to identify guests and BYOD users, instruct them how to download and install the CA certificate, and clearly notify them that their traffic will be decrypted?
What happens, by default, when the GlobalProtect app fails to establish an IPSec tunnel to the GlobalProtect gateway?
An organization is interested in migrating from their existing web proxy architecture to the Web Proxy feature of their PAN-OS 11.0 firewalls. Currently. HTTP and SSL requests contain the c IP address of the web server and the client browser is redirected to the proxy
Which PAN-OS proxy method should be configured to maintain this type of traffic flow?
An administrator configures a preemptive active-passive high availability (HA) pair of firewalls and configures the HA election settings on firewall-02 with a device priority value of 100, and firewall-01 with a device priority value of 90.
When firewall-01 is rebooted, is there any action taken by the firewalls?
A firewall engineer at a company is researching the Device Telemetry feature of PAN-OS. Which two aspects of the feature require further action for the company to remain compliant with local laws regarding privacy and data storage? (Choose two.)
An engineer reviews high availability (HA) settings to understand a recent HA failover event Review the screenshot below.
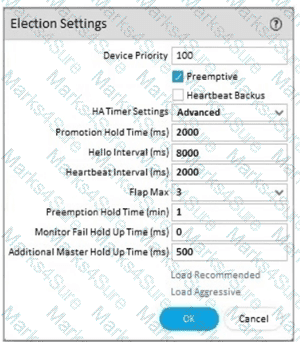
Which tuner determines how long the passive firewall will wart before taking over as the active firewall after losing communications with the HA peer?
Which DoS Protection Profile detects and prevents session exhaustion attacks against specific destinations?
A system administrator runs a port scan using the company tool as part of vulnerability check. The administrator finds that the scan is identified as a threat and is dropped by the firewall. After further investigating the logs, the administrator finds that the scan is dropped in the Threat Logs.
What should an administrator consider when planning to revert Panorama to a pre-PAN-OS 10.1 version?
Which three options does Panorama offer for deploying dynamic updates to its managed devices? (Choose three.)