A prospect has agreed to do a 30-day POC and asked to integrate with a product that Demisto currently does not have an integration with. How should you respond?
Which technology allows a customer to integrate Cortex Xpanse with third-party applications or services, assets, and IP ranges while leveraging investigation capabilities?
When preparing for a Cortex XSOAR proof of value (POV), which task should be performed before the evaluation is requested?
How does a clear understanding of a customer’s technical expertise assist in a hand off following the close of an opportunity?
Which Cortex XDR license is required for a customer that requests endpoint detection and response (EDR) data collection capabilities?
Which two actions are required to add indicators to the whitelist? (Choose two.)
Which two Cortex XSOAR incident type features can be customized under Settings > Advanced > Incident Types? (Choose two.)
When analyzing logs for indicators, which are used for only BIOC identification'?
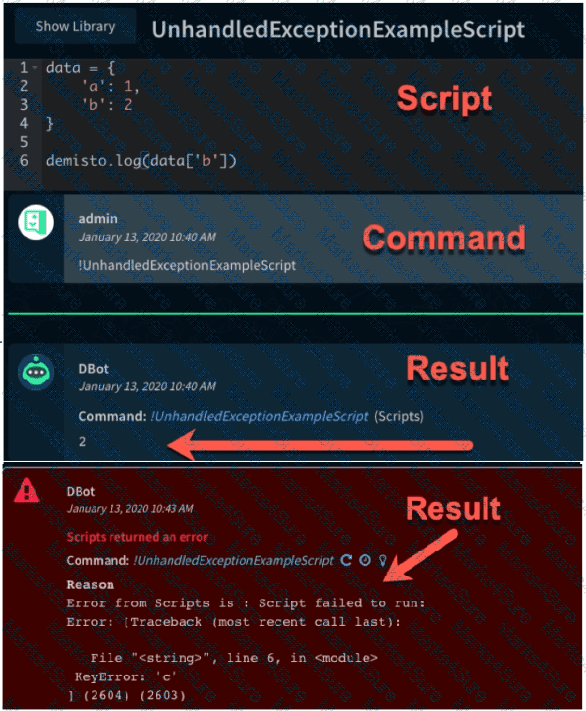
The images show two versions of the same automation script and the results they produce when executed in Demisto. What are two possible causes of the exception thrown in the second Image? (Choose two.)
SUCCESS
Which feature of Cortex XSIAM helps analyst reduce the noise and false positives that often plague traditional SIEM systems?
An adversary is attempting to communicate with malware running on your network for the purpose of controlling malware activities or for ex filtrating data from your network. Which Cortex XDR Analytics alert is this activity most likely to trigger'?
Which task allows the playbook to follow different paths based on specific conditions?
What are two ways a customer can configure user authentication access Cortex Xpanse? (Choose two.)
Which two areas of Cortex XDR are used for threat hunting activities? (Choose two.)
A customer has purchased Cortex Data Lake storage with the following configuration, which requires 2 TB of Cortex Data Lake to order:
support for 300 total Cortex XDR clients all forwarding Cortex XDR data with 30-day retention
storage for higher fidelity logs to support Cortex XDR advanced analytics
The customer now needs 1000 total Cortex XDR clients, but continues with 300 clients forwarding Cortex XDR data with 30-day retention.
What is the new total storage requirement for Cortex Data Lake storage to order?
A customer has 2700 endpoints. There is currently concern about recent attacks in their industry and threat intelligence from a third-party subscription. In an attempt to be proactive, phishing simulations have been prioritized, but the customer wants to gain more visibility and remediation capabilities specific to their network traffic.
Which Cortex product provides these capabilities?
Which two methods does the Cortex XDR agent use to identify malware during a scheduled scan? (Choose two.)
Which playbook functionality allows grouping of tasks to create functional building blocks?
Which statement applies to the differentiation of Cortex XDR from security information and event management (SIEM)?
What is the size of the free Cortex Data Lake instance provided to a customer who has activated a TMS tenant, but has not purchased a Cortex Data Lake instance?
Which process in the causality chain does the Cortex XDR agent identify as triggering an event sequence?
What is a requirement when integrating Cortex XSIAM or Cortex XDR with other Palo Alto Networks products?
When initiated, which Cortex XDR capability allows immediate termination of the process-or entire process tree-on an anomalous process discovered during investigation of a security event?
A test for a Microsoft exploit has been planned. After some research Internet Explorer 11 CVE-2016-0189 has been selected and a module in Metasploit has been identified
(exploit/windows/browser/ms16_051_vbscript)
The description and current configuration of the exploit are as follows;
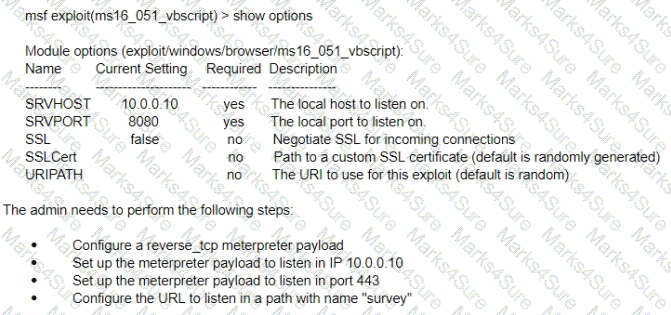
What is the remaining configuration?
A)
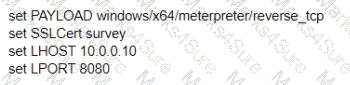
B)
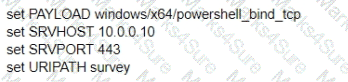
C)
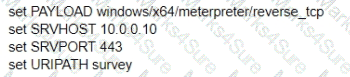
D)

If you have a playbook task that errors out. where could you see the output of the task?
A customer has purchased Cortex XSOAR and has a need to rapidly stand up the product in their environment. The customer has stated that their internal staff are currently occupied with other projects.
Which Palo Alto Networks service offering should be recommended to the customer?
On a multi-tenanted v6.2 Cortex XSOAR server, which path leads to the server.log for "Tenant1"?
In the DBotScore context field, which context key would differentiate between multiple entries for the same indicator in a multi-TIP environment?
What is a benefit of user entity behavior analytics (UEBA) over security information and event management (SIEM)?
What is the requirement for enablement of endpoint and network analytics in Cortex XDR?
Why is Premium Customer Success an important part of any Cortex bill of materials?
In addition to incident volume, which four critical factors must be evaluated to determine effectiveness and ROI on cybersecurity planning and technology?